第一章
THE BIG PICTURE
这一部分内容为非重点,不做表述。
第二章:这一部分主要内容在于进制的转换。
data base convert
熟悉不同进制的转换:
binary / octal / decimal /hexadecimal
以二进制为桥梁:
base 2->base 8: 3位并1位
base 2->base 16: 4位并1位
base 16(0~9,A-F)
题:
- Why are binary numbers important in computing?
ANS:Data and instructions are represented in binary inside the computer.
第三章:主要了解两个知识点
Analog data A continuous representation of data(连续)
Digital data A discrete representation of data(离散)
What is the main difference between the ASCII and Unicode character sets?
Unicode is a superset of ASCII, and the numbers 0–127 have the same meaning in ASCII as they have in Unicode.
第四章:
gate:
NOT/AND/OR/NOR/NAND/XOR/XNOR
非 / 与 /或 /或非/与非 /异或 /同或
question:
- Give the three representations of an AND gate and say in words what AND means.?
ANS:
A and B are the input signals and X is the output signal.
Boolean expression: A B (A AND B)
Logic Diagram:
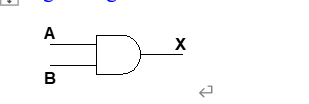
Truth Table:
A B X
0 0 0
0 1 0
1 0 0
1 1 1
If both input values are 1, AND returns a 1; otherwise AND returns a 0.
2.Draw a circuit diagram corresponding to the following Boolean expression:
(AB)’ + (CD)’
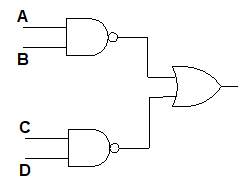
3.What is a multiplexer?
A multiplexer is a circuit that uses input control signals to determine which of several data input lines is to be routed to the output.
4.A multiplexer adds all of the bits on its input lines to produce its output.
FALSE
5.ADDER:
Differentiate between a half adder and a full adder.?
A half adder is a circuit that computes the sum of two bits and produces the appropriate carry bit. A full adder is a circuit that computes the sum of two bits, taking into account the carry bit.
What is the Boolean expression for a full adder and half adder?
C is the carry in.(进位)
Sum is (A B) C)
Carry out is (A AND B) OR ((A B) AND C) " "为异或
Sum is(A B)
Carry out is A AND B
第五章
1.Name the components of a von Neumann machine.
memory, arithmetic/logic unit, input/output units, the control unit
2.Which component in the von Neumann architecture would you say acts as the stage manager. Explain.
The computer component that acts as the state manager is the control unit. It controls the actions of the other components in order to execute instructions in sequence.
3.List the steps in the fetch-execute cycle.
Fetch the next instruction from the address in the program counter.
Decode the instruction.
Execute the instruction.
4.Explain what is meant by "fetch an instruction."
The control unit goes to the address named in the program counter, makes a copy of the contents of that address, puts the copy into the instruction register
Explain what is meant by "decode and instruction."
The control unit determines what the instruction is and accesses any memory locations that contain operands for the instruction.
Explain what is meant by "execute an instruction."
Signals are sent to the arithmetic/logic unit to carry out the processing.
5.Compare and contrast RAM and ROM memory.
RAM is an acronym for Random Access Memory;
ROM is an acronym for Read Only Memory. Both RAM and ROM are random access;
1.The cells in RAM can be both read from and written to. But the ROM can only be read from. 2.Another major difference is that RAM is volatile and ROM is not. This means that ROM maintain its bit patterns when the power is turned off.
6.What is a secondary storage device, and why are such devices important?
Because RAM is volatile and ROM cannot be changed, there must be places to store data and programs outside of the computer’s main memory. Such places are called secondary storage devices.
7.What is the common name for the disk that is a secondary storage device?
Although there are a variety of disks that are secondary storage devices, the hard disk drive is the one that comes with the machine.
第七章
1.binary research:出题的关键在于写出比较的次数
int binary_research(int array[n],int value)
{
low = array[0],high=array[n-1];
mid = low +(high – low)/2;
while(low<high)
{ mid = low +(high – low)/2;
if(array[mid]==valve) return mid;
else if(array[mid]<valve) low = mid+1;
else if(array[mid]>valve) high = mid -1;
}
}
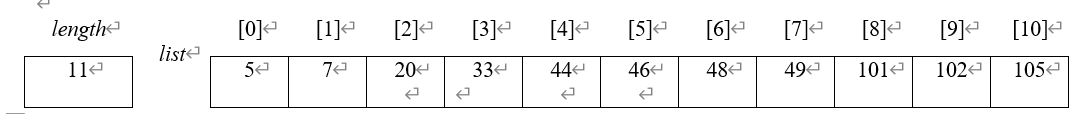
How many comparisons does it take using a sequential search to find the following values or determine that the item is not in the list?
A. 4
11
B. 44
5
C. 45
11
D. 105
11
E. 10
11
67. How many comparisons does it take using a binary search to find the following values or determine that the item is not in the list?
A. 4
4
B. 44
4
C. 46
1
D. 105
4
E. 106
4
选择排序:每一趟从待排序的数据元素中选出最小(或最大)的一个元素,顺序放在已排好序的数列的最后,直到全部待排序的数据元素排完。
Bubble sort (冒泡排序):
for(int i=1;i< length;i++) {
for(int j=0;j<length-i;j++) {
if(ages[j]>ages[j+1]) {
int tmp=0;
tmp=ages[j];
ages[j]=ages[j+1];
ages[j+1]=tmp;}}
插入排序从第二个数开始,拿出第二个数进行向前插入排序,一直到最后一个数向前做插入排序。
快速排序:
Show the state of the list when the first recursive call is made in Quicksort using list[0] as split value.
Array when first recursive call is made.
6 1 2 7 3 4 5 10 8
首先将[0]作为哨兵6第一次3 1 2 5 4 6 9 7 10 8
binary search tree:
Draw the binary search tree whose elements are inserted in the following order:
50 72 96 94 107 26 12 11 9 2 10 25 51 16 17 95
Timesharing allows multiple users to interact with a computer at the same time. √
Define timesharing.
Timesharing is a technique by which CPU time is shared among multiple interactive users at the same times.
因为在复习过程中是为了效率,一下内容不区分章节
Memory management(需要注意的是介绍以及地址的计算)
Memory management is keeping track of how and where programs are loaded into main memory。
If a logical address in a paged memory management system is <2, 133>, what do the values mean?
This address means the 133 byte on page 2.
If, in a fixed partition memory management system, the current value of the base register is 42993 and the current value of the bounds register is 2031, compute the physical addresses that correspond to the following logical addresses:
A. 104
43097
B. 1755
44748
C. 3041
Address out of bounds of partition.(不能超过2031)
Name and describe three CPU scheduling algorithms.
First-come, first-served: The processes are moved into the running state in the order in which they arrive in the ready.
Shortest job next: When the CPU is ready for anther job, the process in the ready state that takes the shortest time is moved into the running state. The estimated length of time that a process needs the CPU may or may not be accurate.
Round robin: Each process stays in the running state for a predetermined amount of time, called a time slice. When a process’s time slice is over, it is moved back into the ready state, where it stays until it is its turn again for the CPU.
What is a file protection mechanism?
A file protection mechanism is one that an operating system implements that ensures the only valid users can access a particular file.
What is a computer network?
A computer network is a collection of computing devices connected so that they can communicate and share resources.
Name and describe two key issues related to computer networks.
Data transfer rate: The speed with which data is moved across the network
Protocol: The set of rules that define how data is formatted and processed across a network
What is a domain name?
A domain name is that part of the hostname that specifies the organization or group to which the host belongs.
What is a top-level domain name?
The last part of a domain name that specifies the type of organization or its country of origin.
Why was the IPv6 protocol created for IP addresses?
IPv4 is limited in the number of unique computers it could identify, and was used up by 2011. IPv6 was created as the successor to IPv4, providing many more addresses.
























 185
185











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








