FIREWALL BASICS
状态检测防火墙 FWaaS
五元组
源目安全区域
时间段
用户
应用
安全配置文件(Anti-virus等)
高级别安全区域到低级别安全区域的流量称作outbound流量
常见攻击
保密性 完整性 源验证
应用层 缓冲区溢出攻击、XSS、SQL注入
传输层 TCP欺骗、SYN Flood攻击、UDP Flood攻击、端口扫描
网络层 IP欺骗、Smurf攻击、IP扫描攻击
链路层 MAC欺骗、MAC泛洪、ARP欺骗
物理层 设备破坏、线路侦听
ASPF Application Specific Packet Filtering
创建Server-map表项
dis firewall server-map (nat aspf)
dis firewall session table verbose
STUN
转发流程
白名单 黑名单
见HUAWEI USG6000, USG9500, NGFW Module V500R005C20 产品文档
NAT
PAT, Bidirectional NAT
LB
GSLB LSLB L4 proxy L7 proxy (LVS, HAproxy, Nginx)
DNS Transparent Proxy
Firewall as a DNS server, resolving to Servers on different ISPs according to requesting addresses.
Exit Selection
is there a firewall session?
- longest match first (as per the routing table), default route last.
choose exits according to ISP public addresses stored in FW. This will generate detailed routes in the routing table.
- policy routing (src/dst add, src zone, service, user, time, etc.), preferred to fib.
source in source out.
intelligent routing (link bandwidth, link weight, link active-standby, link quanity)
USG FW HA
MTBF MTTR
inspection technology: BFD, IP-LINK(icmp), NQA(icmp, tcp, udp)
redundancy techonolgy: Eth-Trunk, Link-Group(vgmp), Hot Backup
BFD
can converge in microseconds.
universal, media independent, protocol independent
asynchronous mode, echo assistance mode
where ip-link applies, bfd works too. BFD even supports OSPF (more commonly used).
BFD control packets using UDP, dst port 3784
disadvantages: it cosumes more resources; it must be configured on both peers.
bfd
quit
bfd b1 bind peer-ip 10.1.1.254 interface G1/0/1
discriminator local 10
discriminator remote 20
commit
quit
ip route-static 0.0.0.0 0 10.1.1.254 track bfd-session b1 ## ip-link more common
ip route-static 0.0.0.0 0 10.2.1.254 preference 50
dis bfd session all
ospf 1
bfd all-interfaces enable
inter g1/0/0
ospf bfd enable
ospf bfd min-rx-interval 500 min-tx-interval 500 detect-multiplier 3
By-Pass
Power Supply Redundancy, Fan Redundancy, By-Pass Card
By-Passs Card has 4 ports. to up-stream, to down-stream, to firewall in, to firewall out.
By-Pass function is only supported on some USG6000 devices.
Eth-Trunk
Huawei devices support a max of 16 cables.
Mode can be manual or LACP.
LACP is generic.
display eth-trunk
display trunkmembership
Firewall loadbalance in flows by default. When using iperf to do stream test, it should initiate multple streams with different pairs of source and destination addresses. So that all phisical links can share the streams.
VRRP/VGMP/HRP (Dual FW Active Standby)
HRP is used for synchronizing configuration and state information like policies, objects, some network items, some system items, etc.
VRRP manges virutal interfaces. protocol no 112. Gratuitous arp sent on switchover.
VGMP synchronizes states of upstream and downstream interfaces on the same FW. VGMP state (active or standby) can be seen as FW state. Or VGMP manages VRRP backup groups.
dis hrp
hrp ospf-cost adjust-enable [standby-cost]
dis mac-address
dis arp
dis ip routing-table
#R1
inter g0/0/0
ip add 10.1.1.1 24
vrrp vrid 10 veritual-ip 10.1.1.254
vrrp vrid 10 priority 105
vrrp vrid 10 track interface int g0/0/1 reduced 10
inter g0/0/1
ip add 20.1.1.1 24
vrrp vrid 20 veritual-ip 20.1.1.254
vrrp vrid 20 priority 105
dis vrrp
#R2
int g0/0/0
ip add 10.1.1.2 24
vrrp vrid 10 virtual-ip 10.1.1.254
int g0/0/1
ip add 20.1.1.2 24
vrrp vrid 20 virtual-ip 20.1.1.254
dis vrrp brief
dis hrp interface # 查看心跳接口
hrp mirror session enable # while using loadbalance.
#R5
ospf
a 0
network 1.1.1.5 0.0.0.0
network 2.2.2.5 0.0.0.0
netowrk 3.3.3.5 0.0.0.0
#FW3
ospf
area 0
network 10.1.1.10 0.0.0.0
network 1.1.1.3 0.0.0.0
hrp enable
hrp int g1/0/2 remote 172.16.1.4
int g1/0/1
ip add 10.1.1.10 24
vrrp vrid 10 virtual-ip 10.1.1.254 24 active
it g1/0/2
ip add 172.16.1.3 24
int g1/0/0
ip add 1.1.1.3 24
firewall zone trust
add inter g1/0/1
firewall zone untrust
add inter g1/0/0
firewall zone hb
add inter g1/0/2
dis hrp state verbose
#FW4
ospf
area 0
network 10.1.1.10 0.0.0.0
network 2.2.2.4 0.0.0.0
hrp enable
hrp standby config enable # from loadbalance to master-backup
hrp int g1/0/2 remote 172.16.1.3
int g1/0/1
ip add 10.1.1.20 24
vrrp vrid 10 virtual-ip 10.1.1.254 24 standby
it g1/0/2
ip add 172.16.1.4 24
int g1/0/0
ip add 2.2.2.4 24
firewall zone trust
add inter g1/0/1
firewall zone untrust
add inter g1/0/0
firewall zone hb
add inter g1/0/2
VRRP virtual ip doesn’t have to be in the same subnet as real IPs. This feature can save public network IPs.
VPN
GRE
Can encapsulate IP, IPX, AppleTalk, etc.
Tunnel interface should also be put in an area.
ip route-static 172.16.0.0 16 Tunnel1
inter Tunnel 1
tunnel-protocol gre
source 1.1.1.3
destination 2.2.2.4
ip add 192.168.3.3 24 # the interface won't be up without an IP.
firewall zone dmz
add int Tun 1
security-policy
rule name 1-2
source-zone trust
destination-zone dmz
source-address 10.1.1.0 mask 255.255.255.0
destination-address 172.16.1.0 mask 255.255.255.0
service icmp
action permit
rule name 2-1.1
srouce-zone untrust
destination-zone local
srouce-add 2.2.2.4 32
dest 1.1.1.3 32
action permit
rule name 2-1.2
source-zone dmz
destination-zone trust
source-add 172.16.1.0 24
dest 10.1.1.0 24
action permit
rule name default
action deny
After encapsulation, security-policy won’t check packets any more. But after decapsulation, security-policy will check packets again if there is no corrsponding session.
Firstly configure default action permit. After checking sessions with command dis firewall session table, then consider how to write security policies.
This command firewall packet-filter basic-protocol enable can permit OSPF packets by default. Some deivces permit self-related OSPF packets by default.
IPSec
Peer, SA, Security Protocol, Mode
New IP Header | ESP Header | IP Header TCP Header Data | ESP Trailer | ESP Auth
IKEv1 main mode (6 packets)/ aggressive mode (3 packets), IPSec quick mode(3 packets)
SKEYID = prf(pre-shared-key, Ni_b | Nr_b) 或 SKEYID = prf(K,Ni_b | Nr_b)
SKEYID_d = prf(SKEYID, K | Ci | Cr | 0) # used in IPSec service
SKEYID_a = prf(SKEYID, SKEYID_d | K | Ci | Cr | 1) # used in HMAC for IPSec SA
SKEYID_e = prf(SKEYID, SKEYID_a | K | Ci | Cr | 2) # used in encryption for IPSec SA
prf (psudo random function)
PFS (perfect forward secrecy) will initiate another DH exchange.
SPI in ESP header is used to find what algorithm and key are to used to decapsulate the packet.
ike proposal 1
encryption-algorithm sm4
authentication-algorithm sm3 | sha2-256
authentication-method pre-share | rsa-signature
dh group10
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike peer 2
undo version 2 # both versions are supported by default.
remote-add 2.2.2.2
ike-proposal 1
exchange-mode main | aggressive | auto
pre-shared-key azen123
acl 3001
rule permit ip source 10.1.1.0 0.0.0.255 dest 192.168.1.0 0.0.0.255
ipsec proposal 3
encapsulation-mode tunnel
transform esp # security protocol
esp encryption-algorithm aes-256
esp authentication-algorithm sha2-256
ipsec policy 4 10 isakmp # ike port number: udp 500
proposal 3
ike-peer 2
security acl 3001
int g1/0/1
ipsec policy 4
ip add 1.1.1.1 24
int g1/0/0
ip add 10.1.1.254 24
ospf 5
router-id
a 0
net 1.1.1.1 0.0.0.0
ip route-static 192.168.1.0.24 1.1.1.11
firewall zone untrust
add int g1/0/1
security-policy
rule name 1
source-zone trust
destination-zone untrust
source 10.1.1.0 mask 24
desti 10.1.2.0 mask 24
service icmp
action permit
rule name 2
source-zone local
dest untrust
source-add 1.1.1.1 32
dest 2.2.2.2 32
service isakmp
action permit
rule name 3
srouce-zone untrust
destination-zone local
source-address 2.2.2.2 mask 32
dest 1.1.1.1 mask 32
service esp
action permit
dis ipsec sa
reset ipsec sa
# with ipsec policy templates, you don't have to configure acl or remote address. the applying scenario is when the other end doesn't have a static IP.
ike peer 8
undo version 2
pre-shared-key azen123
ike-proposal 1
ipsec policy-template 10 100
proposal 3
ike peer 8
route inject dynamic
ipsec policy 4 20 isakmp template 10
NAT Travesal
SNAT and IPSec enabled on the same device: After SNAT, source address is changed and ipsec policy acl can’t match the packet so the packet won’t be encapsulated as expected. One workaround is add paticular acls on both peers in a mirrored manner. Another way is to insert a nat-policy for packets going to and coming from two vpn sites with action no-nat.
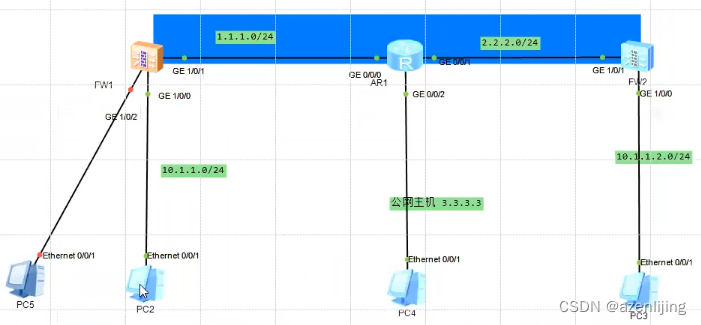
SNAT device behind IPsec device (nat travesal): during IKE SA negotiation, if nat is detected, nat-t is launched and a udp header with port 4500 will be inserted between the outer ip header and esp header. IKE v1 can use nat-t but it must be configured manually. IKE v2 supports nat-t by itself.
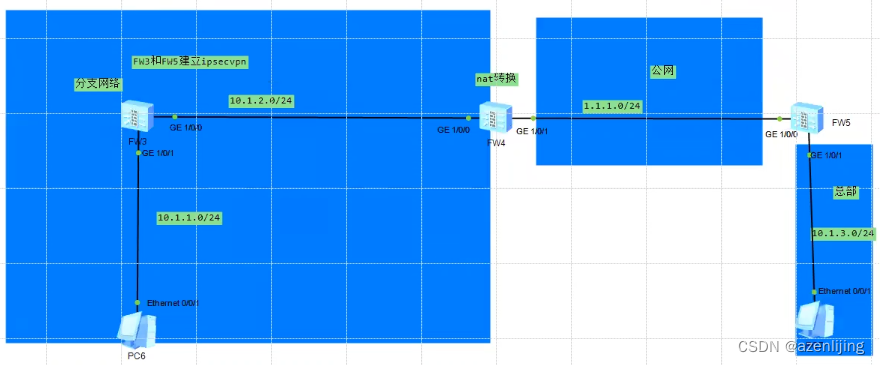
IKE v2
Better than IKE v1 in efficiency and security. 4 packets in total to negotiate IKE SA and the first pair of IPSec SAs.























 7097
7097











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








