IAT Hook通过修改输入表的地址使应用调用函数的时候跳转到恶意代码区域
这里我们获取到了指定进程的指定dll中导入的指定函数的地址和该IAT的地址,只要把该IAT修改了就可以达到hook的目的
文章目录
远程进程IAT Hook
大概步骤
获取IMAGE_BASE
获取IAT
找到需要修改的IAT位置,保存原始的函数地址,修改为自己定义的函数位置
困难
上述过程看起来很简单,但有需要困难的地方,比如说我们想hook MessageBoxA,hwnd就设置为0,uType设置为数字,但对应的字符串我们需要再远程进程里面分配,这个就比较麻烦,我们不能说一遍下断点一边获取返回值
代码
#include<windows.h>
#include<iostream>
#include<TlHelp32.h>
using namespace std;
DWORD GetProcessIdByName(WCHAR* FileName) {
if (!FileName) {
return 0;
}
HANDLE hSnapShot = CreateToolhelp32Snapshot(TH32CS_SNAPPROCESS, NULL);
if (INVALID_HANDLE_VALUE == hSnapShot) {
return 0;
}
PROCESSENTRY32 p32;
p32.dwSize = sizeof(p32);
DWORD ProcessId = 0;
Process32First(hSnapShot, &p32);
do {
if (!wcscmp(p32.szExeFile, FileName)) {
ProcessId = p32.th32ProcessID;
break;
}
} while (Process32Next(hSnapShot, &p32));
CloseHandle(hSnapShot);
return ProcessId;
}
HANDLE GetProcessHandleById(DWORD ProcessId) {
if (!ProcessId) {
return 0;
}
return OpenProcess(PROCESS_ALL_ACCESS, FALSE, ProcessId);
}
HANDLE GetProcessHandleByName(WCHAR* FileName) {
return GetProcessHandleById(GetProcessIdByName(FileName));
}
WCHAR EXE_NAME[] = L"1.exe";
CHAR WantToHookDllName[] = "USER32.dll";
CHAR WantToHookFunName[] = "MessageBoxA";
DWORD OriginalHookedFunAddress = 0;
LPVOID HookedIATAddress = 0;
HANDLE hProcess = NULL;
DWORD ImageBase = 0;
VOID GetImageBase() {
BYTE SHELLCODE[] = "\x64\xA1\x30\x00\x00\x00\x8b\x40\x08\xc2\x04\x00";
LPVOID base_address = VirtualAllocEx(hProcess, NULL, sizeof(SHELLCODE), MEM_COMMIT, PAGE_EXECUTE_READWRITE);
if (!base_address) {
cout << "分配失败";
CloseHandle(hProcess);
}
if (!WriteProcessMemory(hProcess, base_address, SHELLCODE, sizeof(SHELLCODE), NULL)) {
cout << "写入失败";
CloseHandle(hProcess);
}
HANDLE hThread = CreateRemoteThread(hProcess, NULL, 0, (LPTHREAD_START_ROUTINE)base_address, NULL, 0, NULL);
if (!hThread) {
cout << "线程创建失败";
CloseHandle(hProcess);
}
WaitForSingleObject(hThread, INFINITE);
GetExitCodeThread(hThread, &ImageBase);
CloseHandle(hThread);
}
DWORD GetImageImportDescriptorRVA() {
GetImageBase();
if (!ImageBase) {
return 0;
}
char header[1000];
if (!ReadProcessMemory(hProcess, (LPCVOID)ImageBase, header, sizeof(header), NULL)) {
cout << "获取文件内容失败";
CloseHandle(hProcess);
return 0;
}
PIMAGE_DOS_HEADER pDosHeader = (PIMAGE_DOS_HEADER)header;
if (pDosHeader->e_magic != 0x5a4d) {
cout << "不符合Dos文件头";
CloseHandle(hProcess);
return 0;
}
PIMAGE_NT_HEADERS pPeHeader = (PIMAGE_NT_HEADERS)(header + pDosHeader->e_lfanew);
if (pPeHeader->Signature != 0x4550) {
cout << "不是PE文件";
CloseHandle(hProcess);
return 0;
}
IMAGE_OPTIONAL_HEADER ImageOptionalHeader = (IMAGE_OPTIONAL_HEADER)pPeHeader->OptionalHeader;
IMAGE_DATA_DIRECTORY ImportTableDataDirectroy = ImageOptionalHeader.DataDirectory[1];
//这个是RVA
return ImportTableDataDirectroy.VirtualAddress;
}
int GetOriginalFuncAddress() {
DWORD IIDRVA = GetImageImportDescriptorRVA();
if (!IIDRVA) {
return 0;
}
IMAGE_IMPORT_DESCRIPTOR ImageImportDescriptor;
int sum = 0;
char DllName[100];
while (true) {
if (!ReadProcessMemory(hProcess, (LPVOID)(IIDRVA + ImageBase + sum * sizeof(ImageImportDescriptor)), &ImageImportDescriptor, sizeof(ImageImportDescriptor), NULL)) {
cout << "读取IID失败";
CloseHandle(hProcess);
return 0;
}
if (ImageImportDescriptor.FirstThunk == NULL) {
break;
}
sum++;
if (!ReadProcessMemory(hProcess, (LPVOID)(ImageImportDescriptor.Name + ImageBase), DllName, sizeof(DllName), NULL)) {
cout << "DllName读取失败";
CloseHandle(hProcess);
return 0;
}
if (!strcmp(DllName, WantToHookDllName)) {
IMAGE_THUNK_DATA INT;
int all = 0;
while (true) {
if (!ReadProcessMemory(hProcess, (LPVOID)(ImageImportDescriptor.OriginalFirstThunk + ImageBase + all * sizeof(INT)), &INT, sizeof(INT), NULL)) {
cout << "INT读取失败";
CloseHandle(hProcess);
return 0;
}
if (INT.u1.AddressOfData == NULL) {
break;
}
char INTContent[30];
if (!ReadProcessMemory(hProcess, (LPVOID)(INT.u1.AddressOfData + ImageBase), &INTContent, sizeof(INTContent), NULL)) {
cout << "funcName读取失败";
CloseHandle(hProcess);
return 0;
}
if (!strcmp(WantToHookFunName, INTContent + 2)) {
IMAGE_THUNK_DATA IAT;
if (!ReadProcessMemory(hProcess, (LPVOID)(ImageImportDescriptor.FirstThunk + ImageBase + all * sizeof(IAT)), &IAT, sizeof(IAT), NULL)) {
cout << "IAT读取失败";
CloseHandle(hProcess);
return 0;
}
if (IAT.u1.Function != (DWORD)GetProcAddress(LoadLibraryA(WantToHookDllName), WantToHookFunName))
{
cout << "已经被修改啦";
return 0;
}
OriginalHookedFunAddress = IAT.u1.Function;
HookedIATAddress = (LPVOID)(ImageImportDescriptor.FirstThunk + ImageBase + all * sizeof(IAT));
}
all++;
}
}
}
return 1;
}
int main() {
hProcess = GetProcessHandleByName(EXE_NAME);
if (!hProcess) {
cout << "没有该进程";
return 0;
}
if (!GetOriginalFuncAddress()) {
cout << "获取Func地址失败";
return 0;
}
BYTE SHELLCODE2[] = "\x6a\x00\x6a\x00\x6a\x00\x6a\x00\xb8\x70\x36\x76\x76\xff\xd0\xc2\x10\x00";
LPVOID start_address = VirtualAllocEx(hProcess, 0, sizeof(SHELLCODE2), MEM_COMMIT, PAGE_EXECUTE_READWRITE);
if (!start_address) {
cout << "分配失败";
CloseHandle(hProcess);
return 0;
}
if (!WriteProcessMemory(hProcess, start_address, SHELLCODE2, sizeof(SHELLCODE2), NULL)) {
cout << "写入失败";
CloseHandle(hProcess);
return 0;
}
DWORD oldProtect;
if (!VirtualProtectEx(hProcess, HookedIATAddress, 4, PAGE_EXECUTE_READWRITE, &oldProtect)) {
cout << "IAT权限更改失败";
CloseHandle(hProcess);
return 0;
}
if (!WriteProcessMemory(hProcess, HookedIATAddress, &start_address, 4, NULL)) {
cout << "写入失败";
CloseHandle(hProcess);
return 0;
}
cout << "Hook成功";
CloseHandle(hProcess);
return 0;
}
这里面比较关键的就是SHELLCODE2,这里我就push了4个0,然后硬写了原函数的地址,因为kernel32.dll,user32.dll,ntdll这三个的函数地址都是固定不变的,如果你启用了aslr(Address space layout randomization), 他们会在每次重新启动系统的时候随机化一次,但对于所有进程来说,运行时地址一样
DLL IAT HOOK
测试代码
#include<windows.h>
#include<iostream>
using namespace std;
typedef DWORD (WINAPI*lpInstallIATHook)(LPVOID lpParameter);
int main() {
HMODULE hModule=LoadLibraryA("DllProject.dll");
int i = 0;
while (true) {
i++;
MessageBoxA(0, "ok", 0, 0);
if (i == 10) {
FreeLibrary(hModule);
}
}
return 0;
}
现在大概优化了代码,首先是主代码
#include "Process.h"
int main() {
hProcess = GetProcessHandleByName(EXE_NAME);
if (!hProcess) {
cout << "没有该进程";
return 0;
}
if (!GetOriginalFuncAddress()) {
return 0;
}
CHAR lpText[] = "hacked by bbs";
LPVOID TextAddress = VirtualAllocEx(hProcess, 0, sizeof(lpText), MEM_COMMIT, PAGE_READWRITE);
if (!TextAddress) {
CloseHandle(hProcess);
return 0;
}
if (!WriteProcessMemory(hProcess, TextAddress, lpText, sizeof(lpText), NULL)) {
CloseHandle(hProcess);
return 0;
}
CHAR lpTitle[] = "bbs nb";
LPVOID TitleAddress = VirtualAllocEx(hProcess, 0, sizeof(lpTitle), MEM_COMMIT, PAGE_READWRITE);
if (!TextAddress) {
CloseHandle(hProcess);
return 0;
}
if (!WriteProcessMemory(hProcess, TitleAddress, lpTitle, sizeof(lpTitle), NULL)) {
CloseHandle(hProcess);
return 0;
}
int i = 100;
SHELLCODE shellcode(100);
shellcode.push(MB_OKCANCEL);
shellcode.push((DWORD)TitleAddress);
shellcode.push((DWORD)TextAddress);
shellcode.push(0);
shellcode.moveax(OriginalHookedFunAddress);
shellcode.calleax();
shellcode.ret(0x10);
LPVOID start_address = VirtualAllocEx(hProcess, 0, shellcode.now_point, MEM_COMMIT, PAGE_EXECUTE_READWRITE);
if (!start_address) {
CloseHandle(hProcess);
return 0;
}
if (!WriteProcessMemory(hProcess, start_address, shellcode.shellcode, shellcode.now_point, NULL)) {
CloseHandle(hProcess);
return 0;
}
DWORD oldProtect;
if (!VirtualProtectEx(hProcess, HookedIATAddress, 4, PAGE_EXECUTE_READWRITE, &oldProtect)) {
CloseHandle(hProcess);
return 0;
}
if (!WriteProcessMemory(hProcess, HookedIATAddress, &start_address, 4, NULL)) {
CloseHandle(hProcess);
return 0;
}
cout << "Hook成功";
CloseHandle(hProcess);
return 0;
}
Process.h
#pragma once
#ifndef __Process_HEADER
#define __Process_HEADER
#include<windows.h>
#include<iostream>
#include<TlHelp32.h>
using namespace std;
extern WCHAR EXE_NAME[];
extern CHAR WantToHookDllName[];
extern CHAR WantToHookFunName[];
extern DWORD OriginalHookedFunAddress;
extern LPVOID HookedIATAddress;
extern HANDLE hProcess;
extern DWORD ImageBase;
DWORD GetProcessIdByName(WCHAR* FileName);
HANDLE GetProcessHandleById(DWORD ProcessId);
HANDLE GetProcessHandleByName(WCHAR* FileName);
BOOL GetOriginalFuncAddress();
class SHELLCODE {
public:
int size;
int now_point;
BYTE* shellcode;
SHELLCODE(int size);
void append(BYTE payload);
void append(WORD payload);
void append(DWORD payload);
void push(LONG payload);
void moveax(DWORD payload);
void jmpeax();
void jmp_eax_();
void jmp_address_(DWORD payload);
void calleax();
void call_eax_();
void call_address_(DWORD payload);
void ret(BYTE payload);
};
#endif
Process.c
#include "Process.h"
WCHAR EXE_NAME[] = L"1.exe";
CHAR WantToHookDllName[] = "USER32.dll";
CHAR WantToHookFunName[] = "MessageBoxA";
DWORD OriginalHookedFunAddress = 0;
LPVOID HookedIATAddress = 0;
HANDLE hProcess = NULL;
DWORD ImageBase = 0;
DWORD GetProcessIdByName(WCHAR* FileName) {
if (!FileName) {
return 0;
}
HANDLE hSnapShot = CreateToolhelp32Snapshot(TH32CS_SNAPPROCESS, NULL);
if (INVALID_HANDLE_VALUE == hSnapShot) {
return 0;
}
PROCESSENTRY32 p32;
p32.dwSize = sizeof(p32);
DWORD ProcessId = 0;
Process32First(hSnapShot, &p32);
do {
if (!wcscmp(p32.szExeFile, FileName)) {
ProcessId = p32.th32ProcessID;
break;
}
} while (Process32Next(hSnapShot, &p32));
CloseHandle(hSnapShot);
return ProcessId;
}
HANDLE GetProcessHandleById(DWORD ProcessId) {
if (!ProcessId) {
return 0;
}
return OpenProcess(PROCESS_ALL_ACCESS, FALSE, ProcessId);
}
HANDLE GetProcessHandleByName(WCHAR* FileName) {
return GetProcessHandleById(GetProcessIdByName(FileName));
}
VOID GetImageBase() {
BYTE SHELLCODE[] = "\x64\xA1\x30\x00\x00\x00\x8b\x40\x08\xc2\x04\x00";
LPVOID base_address = VirtualAllocEx(hProcess, NULL, sizeof(SHELLCODE), MEM_COMMIT, PAGE_EXECUTE_READWRITE);
if (!base_address) {
cout << "分配失败";
CloseHandle(hProcess);
}
if (!WriteProcessMemory(hProcess, base_address, SHELLCODE, sizeof(SHELLCODE), NULL)) {
cout << "写入失败";
CloseHandle(hProcess);
}
HANDLE hThread = CreateRemoteThread(hProcess, NULL, 0, (LPTHREAD_START_ROUTINE)base_address, NULL, 0, NULL);
if (!hThread) {
cout << "线程创建失败";
CloseHandle(hProcess);
}
WaitForSingleObject(hThread, INFINITE);
GetExitCodeThread(hThread, &ImageBase);
CloseHandle(hThread);
}
DWORD GetImageImportDescriptorRVA() {
GetImageBase();
if (!ImageBase) {
return 0;
}
char header[1000];
if (!ReadProcessMemory(hProcess, (LPCVOID)ImageBase, header, sizeof(header), NULL)) {
cout << "获取文件内容失败";
CloseHandle(hProcess);
return 0;
}
PIMAGE_DOS_HEADER pDosHeader = (PIMAGE_DOS_HEADER)header;
if (pDosHeader->e_magic != 0x5a4d) {
cout << "不符合Dos文件头";
CloseHandle(hProcess);
return 0;
}
PIMAGE_NT_HEADERS pPeHeader = (PIMAGE_NT_HEADERS)(header + pDosHeader->e_lfanew);
if (pPeHeader->Signature != 0x4550) {
cout << "不是PE文件";
CloseHandle(hProcess);
return 0;
}
IMAGE_OPTIONAL_HEADER ImageOptionalHeader = (IMAGE_OPTIONAL_HEADER)pPeHeader->OptionalHeader;
IMAGE_DATA_DIRECTORY ImportTableDataDirectroy = ImageOptionalHeader.DataDirectory[1];
//这个是RVA
return ImportTableDataDirectroy.VirtualAddress;
}
BOOL GetOriginalFuncAddress() {
BOOL flag = 0;
DWORD IIDRVA=GetImageImportDescriptorRVA();
if (!IIDRVA) {
return 0;
}
IMAGE_IMPORT_DESCRIPTOR ImageImportDescriptor;
int sum = 0;
while (true) {
if (!ReadProcessMemory(hProcess, (LPVOID)(IIDRVA + ImageBase + sum * sizeof(ImageImportDescriptor)), &ImageImportDescriptor, sizeof(ImageImportDescriptor), NULL)) {
cout << "读取IID失败";
CloseHandle(hProcess);
return 0;
}
if (ImageImportDescriptor.FirstThunk == NULL) {
break;
}
sum++;
char DllName[100];
if (!ReadProcessMemory(hProcess, (LPVOID)(ImageImportDescriptor.Name + ImageBase), DllName, sizeof(DllName), NULL)) {
cout << "DllName读取失败";
CloseHandle(hProcess);
return 0;
}
if (!strcmp(DllName, WantToHookDllName)) {
IMAGE_THUNK_DATA INT;
int all = 0;
while (true) {
if (!ReadProcessMemory(hProcess, (LPVOID)(ImageImportDescriptor.OriginalFirstThunk + ImageBase + all * sizeof(INT)), &INT, sizeof(INT), NULL)) {
cout << "INT读取失败";
CloseHandle(hProcess);
return 0;
}
if (INT.u1.AddressOfData == NULL) {
break;
}
char INTContent[30];
if (!ReadProcessMemory(hProcess, (LPVOID)(INT.u1.AddressOfData + ImageBase), &INTContent, sizeof(INTContent), NULL)) {
cout << "funcName读取失败";
CloseHandle(hProcess);
return 0;
}
if (!strcmp(WantToHookFunName, INTContent + 2)) {
IMAGE_THUNK_DATA IAT;
if (!ReadProcessMemory(hProcess, (LPVOID)(ImageImportDescriptor.FirstThunk + ImageBase + all * sizeof(IAT)), &IAT, sizeof(IAT), NULL)) {
cout << "IAT读取失败";
CloseHandle(hProcess);
return 0;
}
if (IAT.u1.Function != (DWORD)GetProcAddress(LoadLibraryA(WantToHookDllName), WantToHookFunName))
{
cout << "已经被修改啦";
break;
}
flag = 1;
OriginalHookedFunAddress = IAT.u1.Function;
HookedIATAddress = (LPVOID)(ImageImportDescriptor.FirstThunk + ImageBase + all * sizeof(IAT));
break;
}
all++;
}
}
if (flag) {
break;
}
}
return flag;
}
SHELLCODE::SHELLCODE(int size) {
this->size = size;
this->now_point = 0;
this->shellcode = (BYTE*)malloc(sizeof(BYTE)*size);
}
void SHELLCODE::append(BYTE payload) {
this->shellcode[now_point] = payload;
this->now_point++;
}
void SHELLCODE::append(WORD payload) {
this->append(*((BYTE*)&payload));
this->append(*((BYTE*)&payload + 1));
}
void SHELLCODE::append(DWORD payload) {
this->append(*((WORD*)&payload));
this->append(*((WORD*)&payload + 1));
}
void SHELLCODE::push(LONG payload) {
if (payload >= -128 && payload <= 127) {
this->append((BYTE)0x6a);
this->append((BYTE)payload);
}
else {
this->append((BYTE)0x68);
this->append((DWORD)payload);
};
}
void SHELLCODE::moveax(DWORD payload) {
this->append((BYTE)0xb8);
this->append(payload);
}
void SHELLCODE::jmpeax() {
this->append((WORD)0xe0ff);
}
void SHELLCODE::jmp_eax_() {
this->append((WORD)0x20ff);
}
void SHELLCODE::jmp_address_(DWORD payload) {
this->append((WORD)0x25ff);
this->append(payload);
}
void SHELLCODE::calleax() {
this->append((WORD)0xd0ff);
}
void SHELLCODE::call_eax_() {
this->append((WORD)0x10ff);
}
void SHELLCODE::call_address_(DWORD payload) {
this->append((WORD)0x15ff);
this->append(payload);
}
void SHELLCODE::ret(BYTE payload) {
this->append((BYTE)0xc2);
this->append(payload);
this->append((BYTE)0x00);
}
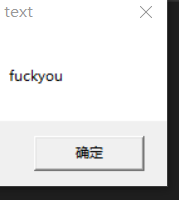
hook之前
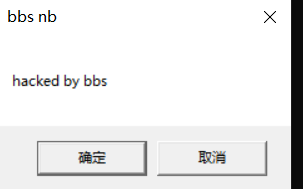
hook之后
运行环境
dll代码
dll生命周期 是LoadLibrary和FreeLibrary之间,一般就是下图的结构,一定要注意break break break vs2022默认没有break不知道为啥,不然你每个状态都会卸载,我当时看了半天不知道为啥

dllmain.h
#pragma once
#include<windows.h>
#include<iostream>
#include<TlHelp32.h>
using namespace std;
WCHAR EXE_NAME[] = L"1.exe";
CHAR WantToHookDllName[] = "USER32.dll";
CHAR WantToHookFunName[] = "MessageBoxA";
DWORD OriginalHookedFunAddress = 0;
LPVOID HookedIATAddress = 0;
HANDLE hProcess = NULL;
DWORD ImageBase = 0;
DWORD oldProtect = 0;
int WINAPI MyMessageBoxA(
_In_opt_ HWND hWnd,
_In_opt_ LPCSTR lpText,
_In_opt_ LPCSTR lpCaption,
_In_ UINT uType);
typedef int (WINAPI *lpMessageBoxA)(
_In_opt_ HWND hWnd,
_In_opt_ LPCSTR lpText,
_In_opt_ LPCSTR lpCaption,
_In_ UINT uType);
BOOL GetOriginalFuncAddress(DWORD IIDRVA);
DWORD WINAPI InstallIATHook(LPVOID lpParameter);
DWORD WINAPI UnInstallIATHook(LPVOID lpParameter);
#include "pch.h"
#include <stdio.h>
#include "dllmain.h"
int WINAPI MyMessageBoxA(
_In_opt_ HWND hWnd,
_In_opt_ LPCSTR lpText,
_In_opt_ LPCSTR lpCaption,
_In_ UINT uType) {
lpMessageBoxA OldmessageBox = (lpMessageBoxA )OriginalHookedFunAddress;
OldmessageBox(0, "bbs真可爱", "哈哈", MB_OKCANCEL);
return 0;
}
BOOL GetOriginalFuncAddress(DWORD IIDRVA) {
BOOL flag = 0;
if (!IIDRVA) {
return 0;
}
int sum = 0;
while (true) {
PIMAGE_IMPORT_DESCRIPTOR pImageImportDescriptor = (PIMAGE_IMPORT_DESCRIPTOR)(IIDRVA + ImageBase + sum * sizeof(IMAGE_IMPORT_DESCRIPTOR));
if (pImageImportDescriptor->FirstThunk == NULL || flag) {
break;
}
sum++;
char* DllName = (char*)(pImageImportDescriptor->Name + ImageBase);
if (!strcmp(DllName, WantToHookDllName)) {
int all = 0;
while (true) {
PIMAGE_THUNK_DATA pINT =(PIMAGE_THUNK_DATA) (pImageImportDescriptor->OriginalFirstThunk + ImageBase + all * sizeof(IMAGE_THUNK_DATA));
if (pINT->u1.AddressOfData == NULL) {
break;
}
char* INTContent = (char*)(pINT->u1.AddressOfData + ImageBase+2);
if (!strcmp(WantToHookFunName, INTContent)) {
PIMAGE_THUNK_DATA pIAT = (PIMAGE_THUNK_DATA)(pImageImportDescriptor->FirstThunk + ImageBase + all * sizeof(IMAGE_THUNK_DATA));
if (pIAT->u1.Function != (DWORD)GetProcAddress(LoadLibraryA(WantToHookDllName), WantToHookFunName))
{
cout << "已经被修改啦";
break;
}
flag = 1;
OriginalHookedFunAddress = pIAT->u1.Function;
HookedIATAddress = (LPVOID)(pImageImportDescriptor->FirstThunk + ImageBase + all * sizeof(IMAGE_THUNK_DATA));
break;
}
all++;
}
}
}
return flag;
}
DWORD WINAPI InstallIATHook(LPVOID lpParameter){
__asm {
mov eax, fs: [0x30]
mov eax, [eax + 0x8]
mov ImageBase, eax
}
PIMAGE_DOS_HEADER pDosHeader = (PIMAGE_DOS_HEADER)ImageBase;
if (pDosHeader->e_magic != 0x5a4d) {
cout << "不符合Dos文件头";
return 0;
}
PIMAGE_NT_HEADERS pPeHeader = (PIMAGE_NT_HEADERS)(ImageBase + pDosHeader->e_lfanew);
if (pPeHeader->Signature != 0x4550) {
cout << "不是PE文件";
return 0;
}
PIMAGE_OPTIONAL_HEADER pImageOptionalHeader = &pPeHeader->OptionalHeader;
PIMAGE_DATA_DIRECTORY pImportTableDataDirectroy =& pImageOptionalHeader->DataDirectory[1];
if (!GetOriginalFuncAddress(pImportTableDataDirectroy->VirtualAddress)) {
cout << "获取函数地址失败";
return 0;
}
hProcess = GetCurrentProcess();
if (!hProcess) {
cout << "打开失败";
return 0;
}
if (!VirtualProtect( HookedIATAddress, 4, PAGE_EXECUTE_READWRITE, &oldProtect)) {
cout << "IAT权限更改失败";
CloseHandle(hProcess);
return 0;
}
DWORD tmp = (DWORD) & MyMessageBoxA;
if (!WriteProcessMemory(hProcess, HookedIATAddress,&tmp, 4, NULL)) {
cout << "IAT写入失败";
CloseHandle(hProcess);
return 0;
}
cout << "Hook成功";
CloseHandle(hProcess);
return 0;
}
DWORD WINAPI UnInstallIATHook(LPVOID lpParameter) {
hProcess = GetCurrentProcess();
if (!hProcess) {
cout << "打开失败";
return 0;
}
if (!WriteProcessMemory(hProcess, HookedIATAddress, &OriginalHookedFunAddress, 4, NULL)) {
cout << "ok";
cout << "IAT写入失败";
CloseHandle(hProcess);
return 0;
}
if (!VirtualProtectEx(hProcess, HookedIATAddress, 4, oldProtect, &oldProtect)) {
cout << "IAT权限更改失败";
CloseHandle(hProcess);
return 0;
}
cout << "Hook结束";
CloseHandle(hProcess);
return 0;
}
BOOL APIENTRY DllMain(HMODULE hModule,
DWORD ul_reason_for_call,
LPVOID lpReserved
)
{
switch (ul_reason_for_call)
{
case DLL_PROCESS_ATTACH:
InstallIATHook(0);
break;
case DLL_THREAD_ATTACH:
break;
case DLL_THREAD_DETACH:
break;
case DLL_PROCESS_DETACH:
UnInstallIATHook(0);
break;
}
return TRUE;
}
可以看出dll舒服很多不用担心进程之间内存问题,当然可以通过进程共享内存解决,这个我之后试试看






















 1803
1803











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








