CtsMediaTestCases
android.media.cts.VideoDecoderPerfTest failed
failed 项:android.media.cts.VideoDecoderPerfTest#testHevcGoog0Perf1280x0720 fail
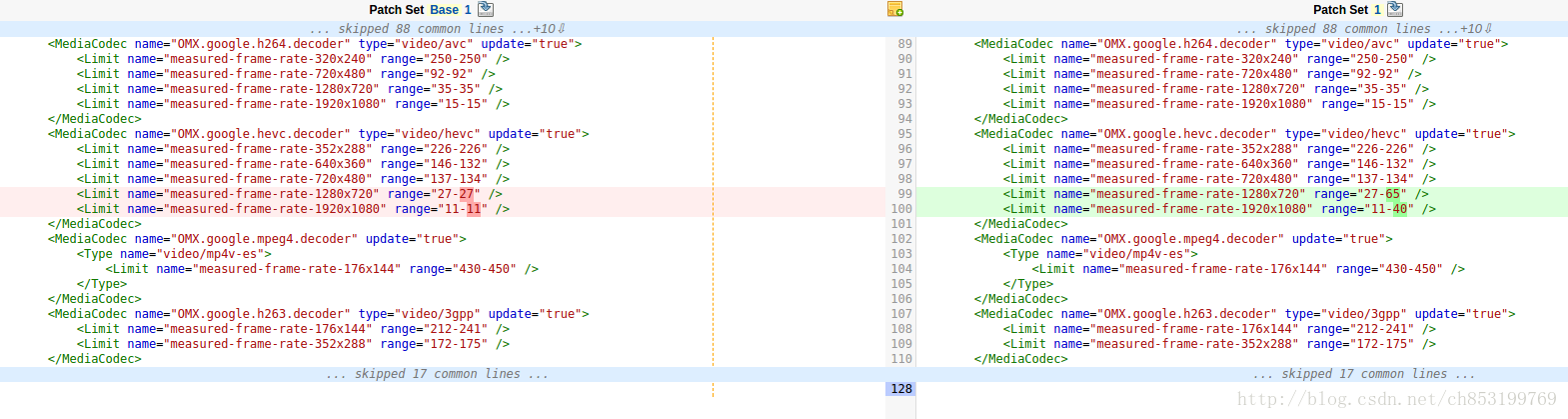
failed information:junit.framework.AssertionFailedError: Expected achievable frame rates for OMX.google.hevc.decoder video/hevc 1280x720: [27.0, 27.0].
failed 项:android.media.cts.VideoDecoderPerfTest#testHevcGoog0Perf1920x1080 fail
failed information:junit.framework.AssertionFailedError: Expected achievable frame rates for OMX.google.hevc.decoder video/hevc 1920x1080: [11.0, 11.0].
对于此类failed项需要多跑几次failed case,找到合适的codec performance limit 的范围.在测试的log中可以找到当时测试时的值
相应的文件media_codecs_performance.xml在android的system/vendor/etc目录下
项目代码中的路径是:
qcom/msm8937_32/media/media_codecs_performance_8937.xmlandroid.media.cts.AudioManagerTest#testAccessRingMode failed
Android 8.1
FAILED INFRAMATION:
01-02 01:45:09.530 7918 7935 I TestRunner: started: testAccessRingMode(android.media.cts.AudioManagerTest)
01-02 01:45:09.536 7918 7918 I MonitoringInstr: Activities that are still in CREATED to STOPPED: 0
01-02 01:45:09.537 7918 7935 D CtsTestRunListener: Total memory : 3734112
01-02 01:45:09.537 7918 7935 D CtsTestRunListener: Used memory : 2450256
01-02 01:45:09.537 7918 7935 D CtsTestRunListener: Free memory : 1283856
01-02 01:45:09.538 7918 7935 D CtsTestRunListener: java.io.tmpdir is:/data/user/0/android.media.cts/cache
01-02 01:45:09.538 7918 7935 D CtsTestRunListener: About to .exec df
01-02 01:45:09.541 7918 7935 D CtsTestRunListener: .exec returned
01-02 01:45:09.541 7918 7935 D CtsTestRunListener: Stream reader created
01-02 01:45:09.548 300 300 D AudioALSAStreamOut: dump()
01-02 01:45:09.552 300 300 D AudioALSAStreamOut: dump()
01-02 01:45:09.553 300 300 D AudioALSAHardware: dumpState()
01-02 01:45:09.557 7936 7936 W df : type=1400 audit(0.0:1207): avc: denied { getattr } for path="/vendor/protect_f" dev="mmcblk0p9" ino=2 scontext=u:r:untrusted_app:s0:c512,c768 tcontext=u:object_r:protect_f_data_file:s0 tclass=dir permissive=0
01-02 01:45:09.567 7936 7936 W df : type=1400 audit(0.0:1211): avc: denied { getattr } for path="/dev/block" dev="tmpfs" ino=49 scontext=u:r:untrusted_app:s0:c512,c768 tcontext=u:object_r:block_device:s0 tclass=dir permissive=0
01-02 01:45:09.574 7918 7935 D CtsTestRunListener: Filesystem 1K-blocks Used Available Use% Mounted on
01-02 01:45:09.575 7918 7935 D CtsTestRunListener: /dev/block/dm-0 5446228 3190812 2222648 59% /data
01-02 01:45:09.575 7918 7935 D CtsTestRunListener: In finally
01-02 01:45:09.575 7918 7935 D CtsTestRunListener: Now executing : android.media.cts.AudioManagerTest
01-02 01:45:09.848 828 1185 W WindowManager: removeWindowToken: Attempted to remove non-existing token: android.os.Binder@e5e85bf
01-02 01:45:09.855 828 3555 V SettingsProvider: name : accelerometer_rotation appId : 1000
01-02 01:45:09.957 828 3555 W WindowManager: removeWindowToken: Attempted to remove non-existing token: android.os.Binder@5f3d7d5
01-02 01:45:09.962 828 1185 V SettingsProvider: name : accelerometer_rotation appId : 1000
01-02 01:45:09.971 7918 7935 I TestRunner: failed: testAccessRingMode(android.media.cts.AudioManagerTest)
01-02 01:45:09.971 7918 7935 I TestRunner: ----- begin exception -----
01-02 01:45:09.972 7918 7935 I TestRunner: junit.framework.AssertionFailedError: Wrote setting should be the same as the read one expected:<true> but was:<false>
01-02 01:45:09.972 7918 7935 I TestRunner: at junit.framework.Assert.fail(Assert.java:50)
01-02 01:45:09.972 7918 7935 I TestRunner: at junit.framework.Assert.failNotEquals(Assert.java:287)
01-02 01:45:09.972 7918 7935 I TestRunner: at junit.framework.Assert.assertEquals(Assert.java:67)
01-02 01:45:09.972 7918 7935 I TestRunner: at junit.framework.Assert.assertEquals(Assert.java:147)
01-02 01:45:09.972 7918 7935 I TestRunner: at android.media.cts.Utils.toggleNotificationPolicyAccess(Utils.java:112)
01-02 01:45:09.972 7918 7935 I TestRunner: at android.media.cts.AudioManagerTest.testAccessRingMode(AudioManagerTest.java:325)isNotificationPolicyAccessGranted())返回了false与期望不符合;
protected static void toggleNotificationPolicyAccess(String packageName,
Instrumentation instrumentation, boolean on) throws IOException {
......
NotificationManager nm = (NotificationManager) instrumentation.getContext()
.getSystemService(Context.NOTIFICATION_SERVICE);
Assert.assertEquals("Wrote setting should be the same as the read one", on,
nm.isNotificationPolicyAccessGranted());
}查看:isNotificationPolicyAccessGranted
最终发现:
private boolean checkPolicyAccess(String pkg) {
2582 try {
2583 int uid = getContext().getPackageManager().getPackageUidAsUser(
2584 pkg, UserHandle.getCallingUserId());
2585 if (PackageManager.PERMISSION_GRANTED == ActivityManager.checkComponentPermission(
2586 android.Manifest.permission.MANAGE_NOTIFICATIONS, uid,
2587 -1, true)) {
2588 return true;
2589 }
2590 } catch (NameNotFoundException e) {
2591 return false;
2592 }
2593 return checkPackagePolicyAccess(pkg) || mListeners.isComponentEnabledForPackage(pkg);
2594 }cts media测试没有android.Manifest.permission.MANAGE_NOTIFICATIONS的权限
最终确认是已知的google issue,向Google申请豁免
同样还有如下类似的failed项
failed项:
android.media.cts.AudioManagerTest#testAdjustVolumeInAlarmsOnlyMode fail
android.media.cts.AudioManagerTest#testAdjustVolumeInTotalSilenceMode fail
android.media.cts.AudioManagerTest#testSetStreamVolumeInAlarmsOnlyMode fail
android.media.cts.AudioManagerTest#testSetStreamVolumeInTotalSilenceMode fail
Information:
java.lang.SecurityException: Notification policy access denied
5604 5622 I TestRunner: failed: testAdjustVolumeInAlarmsOnlyMode(android.media.cts.AudioManagerTest)
01-02 01:30:29.822 5604 5622 I TestRunner: ----- begin exception -----
01-02 01:30:29.825 5604 5622 I TestRunner: java.lang.SecurityException: Notification policy access denied
01-02 01:30:29.825 5604 5622 I TestRunner: at android.os.Parcel.readException(Parcel.java:2004)
01-02 01:30:29.825 5604 5622 I TestRunner: at android.os.Parcel.readException(Parcel.java:1950)
01-02 01:30:29.825 5604 5622 I TestRunner: at android.app.INotificationManager$Stub$Proxy.setInterruptionFilter(INotificationManager.java:2247)
01-02 01:30:29.825 5604 5622 I TestRunner: at android.app.NotificationManager.setInterruptionFilter(NotificationManager.java:1194)
01-02 01:30:29.825 5604 5622 I TestRunner: at android.media.cts.AudioManagerTest.setInterruptionFilter(AudioManagerTest.java:919)
01-02 01:30:29.825 5604 5622 I TestRunner: at android.media.cts.AudioManagerTest.testAdjustVolumeInAlarmsOnlyMode(AudioManagerTest.java:858)
01-02 01:30:29.825 5604 5622 I TestRunner: at java.lang.reflect.Method.invoke(Native Method)
01-02 01:30:29.825 5604 5622 I TestRunner: at android.test.InstrumentationTestCase.runMethod(InstrumentationTestCase.java:220)
01-02 01:30:29.825 5604 5622 I TestRunner: at android.test.InstrumentationTestCase.runTest(InstrumentationTestCase.java:205)
01-02 01:30:29.825 5604 5622 I TestRunner: at junit.framework.TestCase.runBare(TestCase.java:134)
01-02 01:30:29.825 5604 5622 I TestRunner: at junit.framework.TestResult$1.protect(TestResult.java:115)原因: 已知的google issue,向Google申请豁免
[STS] CtsSecurityTestCases
android.security.cts.StagefrightTest#testStagefright_bug_34896431
Test failed to run to completion. Reason: ‘Instrumentation run failed due to ‘Process crashed.”. Check device logcat for details
08-02 23:30:12.572 6812 6829 I StagefrightTest: no input buffer
08-02 23:30:12.572 895 7081 F DEBUG : *** *** *** *** *** *** *** *** *** *** *** *** *** *** *** ***
08-02 23:30:12.572 895 7081 F DEBUG : Build fingerprint: 'WIKO/W-P220-OPE/W-P220:8.1.0/OPM1.171019.019/androi08021339:userdebug/release-keys'
08-02 23:30:12.572 895 7081 F DEBUG : Revision: '0'
08-02 23:30:12.572 895 7081 F DEBUG : ABI: 'arm'
08-02 23:30:12.572 895 7081 F DEBUG : pid: 895, tid: 7081, name: media.codec >>> omx@1.0-service <<<
08-02 23:30:12.573 895 7081 F DEBUG : signal 11 (SIGSEGV), code 1 (SEGV_MAPERR), fault addr 0x8
08-02 23:30:12.573 895 7081 F DEBUG : Cause: null pointer dereference
08-02 23:30:12.577 6812 6829 I StagefrightTest: no output buffer
08-02 23:30:12.583 6812 6829 I StagefrightTest: no input buffer
08-02 23:30:12.587 895 7081 F DEBUG : r0 00000000 r1 00000000 r2 f09830a0 r3 efc04014
08-02 23:30:12.587 895 7081 F DEBUG : r4 ffffc000 r5 efc05014 r6 00000000 r7 f0983378
08-02 23:30:12.587 895 7081 F DEBUG : r8 f0983000 r9 00000000 sl f09830a1 fp f0583000
08-02 23:30:12.587 895 7081 F DEBUG : ip 00000001 sp ef5633b0 lr efc00000 pc eff9aa6c cpsr 600f0010
08-02 23:30:12.588 6812 6829 I StagefrightTest: no output buffer
08-02 23:30:12.593 6812 6829 I StagefrightTest: no input buffer
08-02 23:30:12.599 6812 6829 I StagefrightTest: no output buffer
08-02 23:30:12.604 6812 6829 I StagefrightTest: no input buffer
08-02 23:30:12.609 895 7081 F DEBUG :
08-02 23:30:12.609 895 7081 F DEBUG : backtrace:
08-02 23:30:12.609 895 7081 F DEBUG : #00 pc 00019a6c /system/lib/libstagefright_soft_hevcdec.so (ihevcd_parse_slice_data+544)
08-02 23:30:12.609 6812 6829 I StagefrightTest: no output buffer
08-02 23:30:12.610 895 7081 F DEBUG : #01 pc 0000f160 /system/lib/libstagefright_soft_hevcdec.so (ihevcd_decode+1596)
08-02 23:30:12.610 895 7081 F DEBUG : #02 pc 0000a619 /system/lib/libstagefright_soft_hevcdec.so (android::SoftHEVC::onQueueFilled(unsigned int)+252)
08-02 23:30:12.610 895 7081 F DEBUG : #03 pc 0003d9e7 /system/lib/libstagefright_omx.so (android::SimpleSoftOMXComponent::onMessageReceived(android::sp<android::AMessage> const&)+254)
08-02 23:30:12.610 895 7081 F DEBUG : #04 pc 0003e9e1 /system/lib/libstagefright_omx.so
08-02 23:30:12.610 895 7081 F DEBUG : #05 pc 00010909 /system/lib/libstagefright_foundation.so (android::AHandler::deliverMessage(android::sp<android::AMessage> const&)+24)
08-02 23:30:12.610 895 7081 F DEBUG : #06 pc 00012ba9 /system/lib/libstagefright_foundation.so (android::AMessage::deliver()+48)
08-02 23:30:12.610 895 7081 F DEBUG : #07 pc 000114c1 /system/lib/libstagefright_foundation.so (android::ALooper::loop()+468)
08-02 23:30:12.610 895 7081 F DEBUG : #08 pc 0000d2a9 /system/lib/vndk-sp/libutils.so (android::Thread::_threadLoop(void*)+180)
08-02 23:30:12.611 895 7081 F DEBUG : #09 pc 0004706b /system/lib/libc.so (__pthread_start(void*)+22)
08-02 23:30:12.611 895 7081 F DEBUG : #10 pc 0001af31 /system/lib/libc.so (__start_thread+32)
08-02 23:30:12.615 6812 6829 I StagefrightTest: no input buffer类似的failed项需要查看Google bug_34896431 相关的security patch有没有合入,这种failed case,一般是因为少合入的一部分security patch,或者就是是 平台有关的库的bug了,需平台提供支持
解决的patch是:
diff --git a/drivers/media/platform/msm/vidc/msm_vdec.c b/drivers/media/platform/msm/vidc/msm_vdec.c
index 86b7b1b..579f032 100644
--- a/drivers/media/platform/msm/vidc/msm_vdec.c
+++ b/drivers/media/platform/msm/vidc/msm_vdec.c
@@ -1,4 +1,4 @@
-/* Copyright (c) 2012-2017, The Linux Foundation. All rights reserved.
+/* Copyright (c) 2012-2018, The Linux Foundation. All rights reserved.
*
* This program is free software; you can redistribute it and/or modify
* it under the terms of the GNU General Public License version 2 and
@@ -22,6 +22,7 @@
#define MSM_VDEC_DVC_NAME "msm_vdec_8974"
#define MIN_NUM_OUTPUT_BUFFERS 4
#define MIN_NUM_OUTPUT_BUFFERS_VP9 6
+#define MIN_NUM_OUTPUT_BUFFERS_HEVC 5
#define MIN_NUM_CAPTURE_BUFFERS 6
#define MIN_NUM_THUMBNAIL_MODE_CAPTURE_BUFFERS 1
#define MAX_NUM_OUTPUT_BUFFERS VB2_MAX_FRAME
@@ -1494,6 +1495,10 @@ static int msm_vdec_queue_setup(struct vb2_queue *q,
V4L2_PIX_FMT_VP9 &&
*num_buffers < MIN_NUM_OUTPUT_BUFFERS_VP9)
*num_buffers = MIN_NUM_OUTPUT_BUFFERS_VP9;
+ else if (inst->fmts[OUTPUT_PORT].fourcc ==
+ V4L2_PIX_FMT_HEVC &&
+ *num_buffers < MIN_NUM_OUTPUT_BUFFERS_HEVC)
+ *num_buffers = MIN_NUM_OUTPUT_BUFFERS_HEVC;
for (i = 0; i < *num_planes; i++) {
sizes[i] = get_frame_size(inst,android.security.cts.StagefrightTest#testStagefright_bug_63522067
FAILED INFORMATION:
junit.framework.AssertionFailedError: Device *IS* vulnerable to BUG-63522067-3-HEVC
at junit.framework.Assert.fail(Assert.java:50)
at junit.framework.Assert.assertTrue(Assert.java:20)
at junit.framework.Assert.assertFalse(Assert.java:34)
at android.security.cts.StagefrightTest.doStagefrightTestRawBlob(StagefrightTest.java:1511)
at android.security.cts.StagefrightTest.testStagefright_bug_63522067(StagefrightTest.java:532) at java.lang.reflect.Method.invoke(Native Method)
at android.test.InstrumentationTestCase.runMethod(InstrumentationTestCase.java:220)
at android.test.InstrumentationTestCase.runTest(InstrumentationTestCase.java:205)
at junit.framework.TestCase.runBare(TestCase.java:134)
at junit.framework.TestResult$1.protect(TestResult.java:115)
at android.support.test.internal.runner.junit3.AndroidTestResult.runProtected(AndroidTestResult.java:77) at junit.framework.TestResult.run(TestResult.java:118)
at android.support.test.internal.runner.junit3.AndroidTestResult.run(AndroidTestResult.java:55) at junit.framework.TestCase.run(TestCase.java:124)
at android.support.test.internal.runner.junit3.NonLeakyTestSuite$NonLeakyTest.run(NonLeakyTestSuite.java:63)
at android.support.test.internal.runner.junit3.AndroidTestSuite$2.run(AndroidTestSuite.java:111) at java.util.concurrent.Executors$RunnableAdapter.call(Executors.java:457)
at java.util.concurrent.FutureTask.run(FutureTask.java:266)
at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1162)
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:636)
at java.lang.Thread.run(Thread.java:764)同上分析,检查security 相关的patch全部合入,考虑使用的decoder是qcom hevc decoder,结合log看可能是平台相关的hevc的解码的库的问题, 合入下面的patch验证OK
diff --git a/decoder/ihevcd_decode.c b/decoder/ihevcd_decode.c
index 83f9b42..d2ea7a5 100755
--- a/decoder/ihevcd_decode.c
+++ b/decoder/ihevcd_decode.c
@@ -670,7 +670,6 @@ WORD32 ihevcd_decode(iv_obj_t *ps_codec_obj, void *pv_api_ip, void *pv_api_op)
if(IHEVCD_IGNORE_SLICE == ret)
{
- ps_codec->s_parse.i4_cur_slice_idx = MAX(0, (ps_codec->s_parse.i4_cur_slice_idx - 1));
ps_codec->pu1_inp_bitsbuf += (nal_ofst + nal_len);
ps_codec->i4_bytes_remaining -= (nal_ofst + nal_len);
diff --git a/decoder/ihevcd_parse_headers.c b/decoder/ihevcd_parse_headers.c
index b8ed252..fd8712b 100755
--- a/decoder/ihevcd_parse_headers.c
+++ b/decoder/ihevcd_parse_headers.c
@@ -2623,20 +2621,8 @@ void ihevcd_parse_sei_payload(codec_t *ps_codec,
case SEI_USER_DATA_REGISTERED_ITU_T_T35:
ps_parse->s_sei_params.i1_sei_parameters_present_flag = 1;
- if(ps_parse->s_sei_params.i4_sei_user_data_cnt >= USER_DATA_MAX)
- {
- for(i = 0; i < u4_payload_size / 4; i++)
- {
- ihevcd_bits_flush(ps_bitstrm, 4 * 8);
- }
-
- ihevcd_bits_flush(ps_bitstrm, (u4_payload_size - i * 4) * 8);
- }
- else
- {
- ihevcd_parse_user_data_registered_itu_t_t35(ps_codec,
- u4_payload_size);
- }
+ ihevcd_parse_user_data_registered_itu_t_t35(ps_codec,
+ u4_payload_size);
break;
default:
@@ -2653,20 +2639,8 @@ void ihevcd_parse_sei_payload(codec_t *ps_codec,
{
case SEI_USER_DATA_REGISTERED_ITU_T_T35:
ps_parse->s_sei_params.i1_sei_parameters_present_flag = 1;
- if(ps_parse->s_sei_params.i4_sei_user_data_cnt >= USER_DATA_MAX)
- {
- for(i = 0; i < u4_payload_size / 4; i++)
- {
- ihevcd_bits_flush(ps_bitstrm, 4 * 8);
- }
-
- ihevcd_bits_flush(ps_bitstrm, (u4_payload_size - i * 4) * 8);
- }
- else
- {
- ihevcd_parse_user_data_registered_itu_t_t35(ps_codec,
- u4_payload_size);
- }
+ ihevcd_parse_user_data_registered_itu_t_t35(ps_codec,
+ u4_payload_size);
break; 






















 1万+
1万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










