Have you ever wondered how malware, spyware, scareware, crapware, or other undesirable software might get on a computer? First we’ll illustrate how easily your system can be infected, and then we’ll show you how to clean it up.
您是否曾经想过恶意软件,间谍软件,恐吓软件,垃圾软件或其他不良软件会如何在计算机上传播? 首先,我们将说明如何轻松感染您的系统,然后我们将向您展示如何清除它。
Our example system, running Windows 7, was set up from a worst case scenario point of view: Someone who was only interested in quickly getting to all the “fun stuff” on the internet with absolutely no concern for personal or computer security.
我们从最坏的情况来看,运行Windows 7的示例系统是由以下人员建立的:仅对快速访问Internet上的所有“有趣的东西”感兴趣的人,完全不关心个人或计算机的安全性。
Freshly Installed – Pre Malware
全新安装–恶意软件前
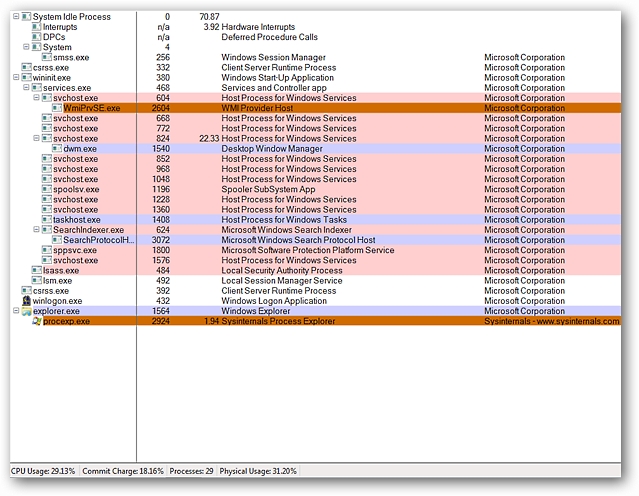
Here you can see the number of processes (and type) that were running on our freshly installed Windows 7 system. The install was so fresh that the only protection that this system had was the Windows Firewall and Windows Defender to keep the malware and virus hordes at bay.
在这里,您可以看到新安装的Windows 7系统上正在运行的进程数(和类型)。 安装是如此新鲜,以至于该系统唯一的保护是Windows防火墙和Windows Defender,以阻止恶意软件和病毒成群结队。
How Some Malware Gets On Your Computer
恶意软件如何在您的计算机上传播
Malware, spyware, and other junk software makes it onto your computer for a number of reasons:
恶意软件,间谍软件和其他垃圾软件会将其安装到您的计算机上有多种原因:
- You installed something you really shouldn’t have, from an untrustworthy source. Often these include screensavers, toolbars, or torrents that you didn’t scan for viruses. 您从不可靠的来源安装了您本不应该安装的东西。 通常,这些文件包括您没有扫描病毒的屏保,工具栏或种子。
- You didn’t pay attention when installing a “reputable” application that bundles “optional” crapware. 在安装捆绑了“可选”垃圾软件的“信誉良好”的应用程序时,您并没有注意。
- You’ve already managed to get yourself infected, and the malware installs even more malware. 您已经设法感染自己,并且该恶意软件还会安装更多恶意软件。
- You aren’t using a quality Anti-Virus or Anti-Spyware application. 您使用的不是优质的防病毒或防间谍软件应用程序。
Watch Out for Insidious Bundled Crapware
提防阴险的捆绑件
Editor’s Note: One of the biggest problems recently is that the makers of popular software keep selling out, and including “optional” crapware that nobody needs or wants. This way they profit off the unsuspecting users that aren’t tech-savvy enough to know any better. They should be ashamed.
编者注:最近最大的问题之一是流行软件的制造商不断售罄,其中包括没人需要或不需要的“可选”垃圾软件。 这样,他们就能从不懂技术的毫无戒心的用户中获利。 他们应该感到羞耻。
On our example system we installed Digsby Messenger, a very popular “reputable” application. This was the regular install version and as you can see in the following screenshots, there are attempts to get you to install undesirable software or make “not so good” changes on your computer. If a person is not careful, then their system becomes infected.
在我们的示例系统上,我们安装了Digsby Messenger,这是一个非常流行的“信誉良好”的应用程序。 这是常规安装版本,如下面的屏幕截图所示,有人试图使您安装不需要的软件或对计算机进行“不太好”的更改。 如果一个人不小心,那么他们的系统就会被感染。
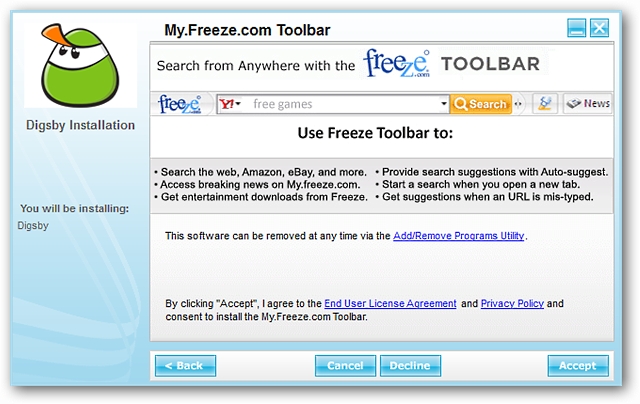
Here you can see the attempt to add the “My.Freeze.com Toolbar” to your browser(s)…definitely not good! Notice that while it does state that the software may be removed later, some people may 1.) Not notice it (lack of attention), 2.) Be in too much of a hurry to install the software to notice, or 3.) Not be familiar or comfortable with removing the software after it is already installed on their system.
在这里,您可以看到将“ My.Freeze.com工具栏”添加到浏览器的尝试……绝对不好! 请注意,尽管确实声明可能会在以后删除该软件,但某些人可能会1.)没注意到它(没有引起注意),2。)太急着安装该软件来引起注意,或者3.)在他们的系统上已经安装软件之后,对它不熟悉或不满意。
The real trick with Digsby (and other software that is set up with the same installation style) is that clicking on “Decline” still allows the installation of Digsby itself to proceed. But can you imagine how things can end up for those people who may think or believe that the only way to get Digsby or similar software installed is to click on “Accept”? It has a really deceptive style!
Digsby(以及其他具有相同安装风格的软件)的真正窍门是,单击“ Decline”(拒绝)仍允许继续进行Digsby的安装。 但是,您能想象那些认为或相信安装Digsby或类似软件的唯一方法是单击“接受”的人最终会如何? 它具有真正的欺骗性!
Note: For more, read our article on avoiding crapware when installing Digsby.
注意:有关更多信息,请阅读有关 在安装Digsby时避免使用垃圾软件 的文章 。
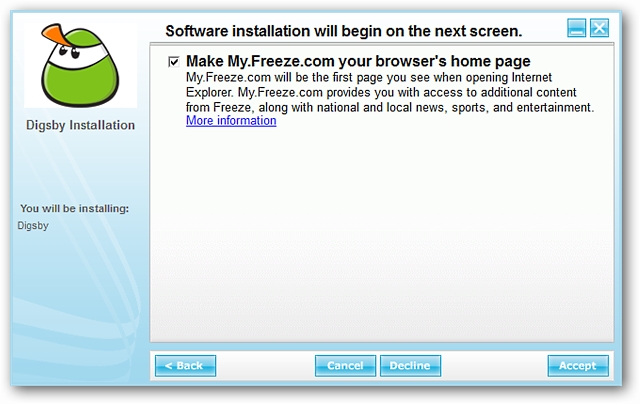
A very obvious attempt to make “My.Freeze.com” the new homepage for your browser(s). Once again the “Decline” versus “Accept” dilemma combined with a checkmark selection choice…
一种非常明显的尝试,使“ My.Freeze.com”成为您的浏览器的新主页。 再次出现“拒绝”与“接受”的困境,再加上对勾标记的选择……
If you have many programs that attempt to install “value-added” software like this on your system, you will quickly find that the majority (or all) of your operating system’s resources are being used up by malware (i.e. background processes). You are also likely to find that you will have unstable or very sluggish browser response, and are likely to have your personal and computer’s security compromised.
如果您有许多程序试图在系统上安装像这样的“增值”软件,您将很快发现操作系统的大部分(或全部)资源已被恶意软件(即后台进程)用尽。 您还可能会发现浏览器响应不稳定或非常缓慢,并且可能会损害您的个人和计算机的安全性。
Just How Quickly Can a System Become Infected?
感染系统有多快?
It only took 2.5 hours to reach the level described in our article…simply surfing wherever for “whatever looked interesting or different”, downloading things like screensavers, file-sharing applications, and installing questionable software from advertisements.
只需2.5小时即可达到我们的文章中描述的水平……只需在“任何有趣或不一样的地方”进行浏览,下载屏幕保护程序,文件共享应用程序以及从广告中安装可疑软件。
The possibilities for becoming infected with viruses or malware were rather high with little to no protection or forethought given concerning what was installed or for the websites visited. Searches for various “less than desirable” pictures, screensavers, clicking on ads, etc. made it very easy to find trouble…perhaps the better way to phrase that is that it was very easy for trouble to find our example system.
对于已安装的内容或所访问的网站,几乎没有或没有任何保护或预先考虑的感染病毒或恶意软件的可能性非常高。 搜索各种“不太理想的”图片,屏幕保护程序,点击广告等,很容易发现问题……也许更好的表达方式是,发现我们的示例系统很容易遇到麻烦。
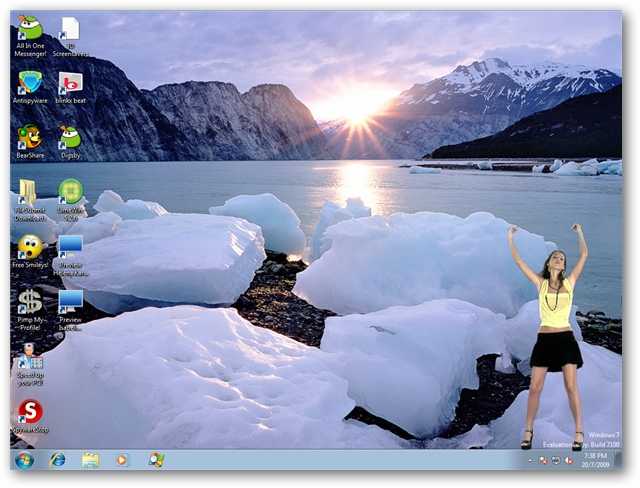
Here you can see a screenshot of the desktop of our example system. Notice that there are icons for file sharing programs, fake anti-malware programs, icons for various screensavers, less than nice websites (possible additional infection vectors), and a virtual dancing woman. Nothing good here!
在这里,您可以看到示例系统桌面的屏幕截图。 请注意,其中包含用于文件共享程序的图标,伪造的反恶意软件程序,用于各种屏幕保护程序的图标,比漂亮的网站还少(可能还有其他感染媒介)和虚拟舞女的图标。 这里没什么好!
Here is a look at the Start Menu…notice that some of the malware has obvious shortcuts in the Startup Folder, but there were plenty on our example system that were not shown in this folder.
这里是“开始”菜单的外观……请注意,某些恶意软件在“启动文件夹”中具有明显的快捷方式,但是示例系统中有很多未在此文件夹中显示。
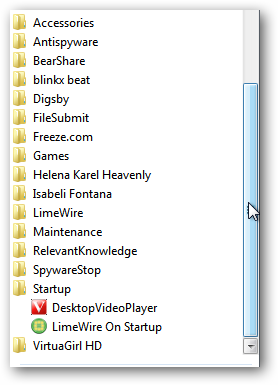
A quick look at an over abundance of toolbars plaguing Internet Explorer 8…by this point the browser was already having some problems starting properly (very slow), some episodes of crashing, and some browser hijacking had occurred.
快速浏览困扰Internet Explorer 8的过多工具栏……到这一点为止,浏览器已经开始正常运行(非常慢),出现崩溃问题以及发生了一些浏览器劫持的问题。
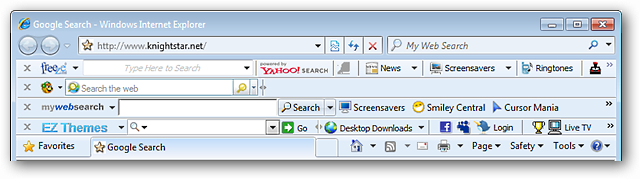
Taking a peek at the Program Uninstall Window shows a variety of malware and undesirable software types that were on our example system.
窥视“程序卸载窗口”,可以看到示例系统中存在多种恶意软件和不良软件类型。
Note: These are the ones that actually bothered with listing an entry in the Uninstall Registry.
注意:这些实际上是困扰于在“卸载注册表”中列出条目的选项。
A Good Look at Scareware
深入了解Scareware
What is scareware? It is software that once installed on your system will try to trick you into believing that you have a highly infected system with some very high “numbers of infections” found. These programs will constantly bother you to register and purchase the software in order to clean up your computer system.
什么是恐吓软件? 该软件一旦安装在您的系统上,就会试图欺骗您,使您相信您的系统感染严重,发现“感染次数”很高。 这些程序将不断困扰您注册和购买软件,以清理计算机系统。
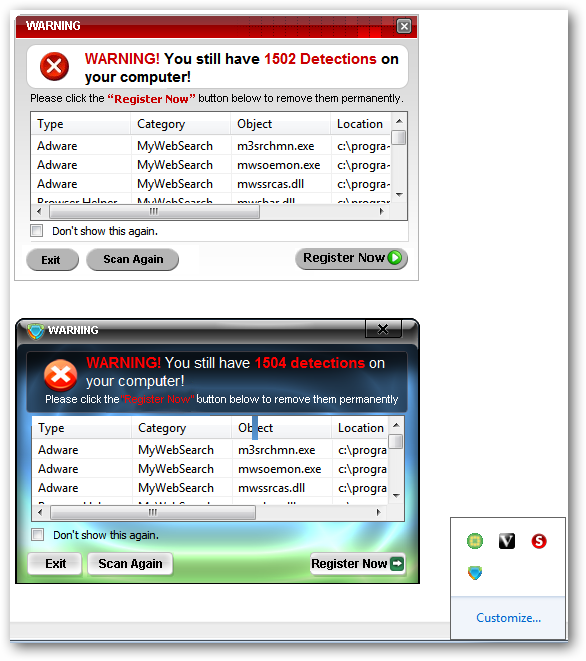
Here you can see two examples of well known scareware. SpywareStop and AntiSpyware 2009. Do not be surprised if you notice that these two “separate” softwares seem to be extremely alike in looks, style, and operation. They are exactly alike…the same wolf just different sheep skins. This is a common practice to stay ahead of legitimate anti-malware and anti-virus software and not be deleted before hopefully being purchased by unsuspecting computer users.
在这里,您可以看到两个众所周知的恐吓软件的例子。 SpywareStop和AntiSpyware2009。如果您发现这两个“分离的”软件在外观,样式和操作上极为相似,请不要感到惊讶。 它们完全一样……同一只狼只是不同的绵羊皮。 这是通常的作法,以领先于合法的反恶意软件和反病毒软件,并且在希望被毫无戒心的计算机用户购买之前不会被删除。
A good look at the two screens that appeared every time we started our example system…absolutely no hesitation to “remind us” how infected our computer was and that we should register the software now. Disgusting!!
仔细查看每次启动示例系统时出现的两个屏幕……绝对会毫不犹豫地“提醒我们”计算机感染了病毒,现在我们应该注册该软件。 真恶心!!
Note: The SpywareStop website was presented to us courtesy of a browser hijacking…and of course we were encouraged to install it.
注意:SpywareStop网站是由于浏览器劫持而向我们提供的……当然,我们鼓励我们安装它。
The main window for SpywareStop…oh so quick to try and encourage you to remove the infections.
SpywareStop的主窗口…哦,这么快尝试一下,鼓励您消除感染。
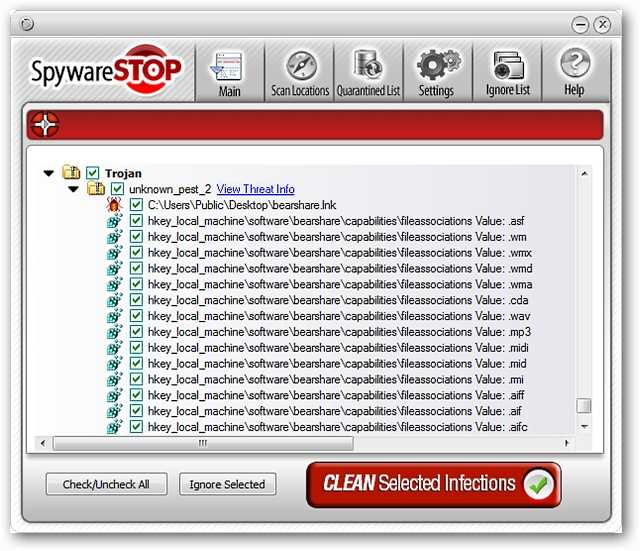
The System Tray pop up window for SpywareStop…
SpywareStop的系统托盘弹出窗口…
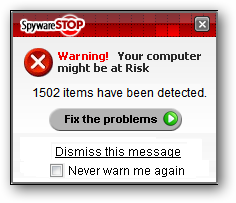
What do things look like if someone went to register the software and purchase it? The registration starts with a request for basic information including an e-mail address. Chances are the addresses harvested in this manner will be sold to spammers…the potential for a little extra income will definitely have an appeal.
如果有人去注册并购买软件,情况会怎样? 注册首先要求提供基本信息,包括电子邮件地址。 很有可能将以这种方式收集的地址出售给垃圾邮件发送者……增加一点收入的潜力肯定会吸引人。
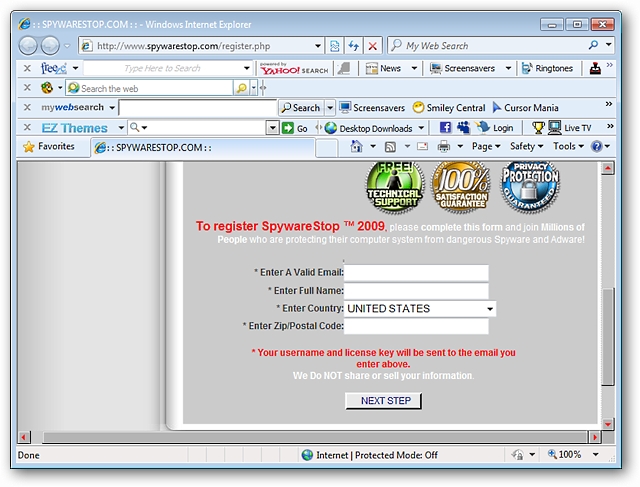
Notice that additional services and software are readily available! Nothing like an opportunity to make even more easy money once they have someone this far in…and of course you can use your credit card. How convenient for them…
请注意,随时可以使用其他服务和软件! 一旦他们有这么远的人,就没有机会赚更多的钱……当然,您可以使用您的信用卡。 对他们来说多么方便...
The ever wonderful cousin to SpywareStop…the infamous AntiSpyware 2009 (also very well known with the 2008 designation).
SpywareStop的绝妙表亲…臭名昭著的AntiSpyware 2009(也以2008标识而闻名)。
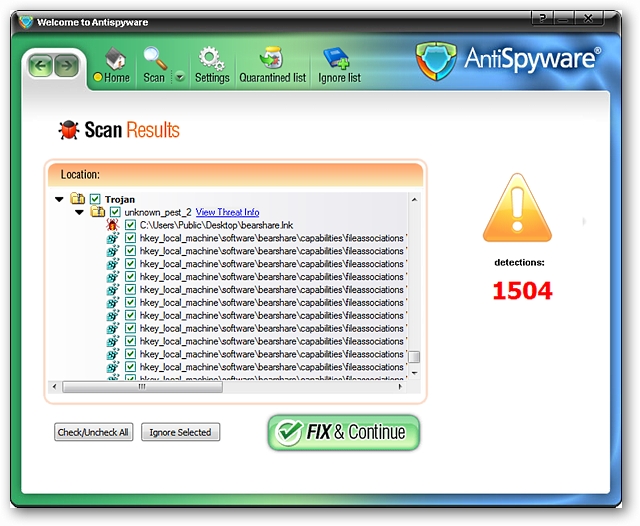
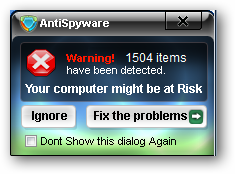
And the wonderful System Tray pop up window for AntiSpyware 2009…the fun never stops!
并为AntiSpyware 2009弹出了漂亮的“系统任务栏”窗口……乐趣永不止息!
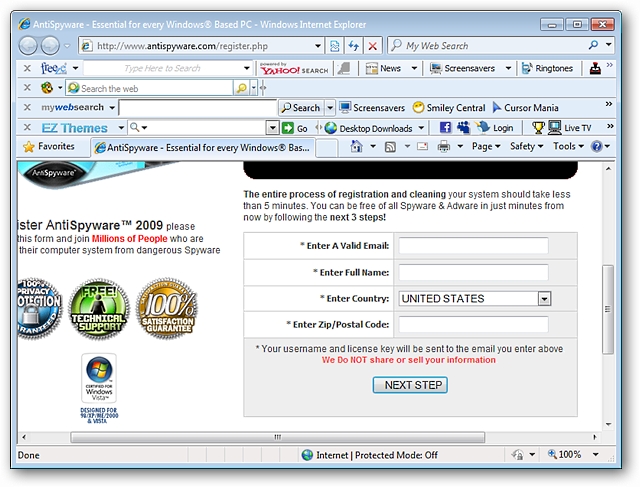
What about registration for this one? Take a good look at these two screenshots and compare them with the two shown above. There is so little difference…yet another sign that these are identical scareware programs with altered user interfaces and alternate websites.
那这个的注册呢? 好好看一下这两个屏幕截图,并将它们与上面显示的两个屏幕截图进行比较。 差别不大……但又有迹象表明,这些是相同的恐吓软件程序,但用户界面和备用网站已更改。
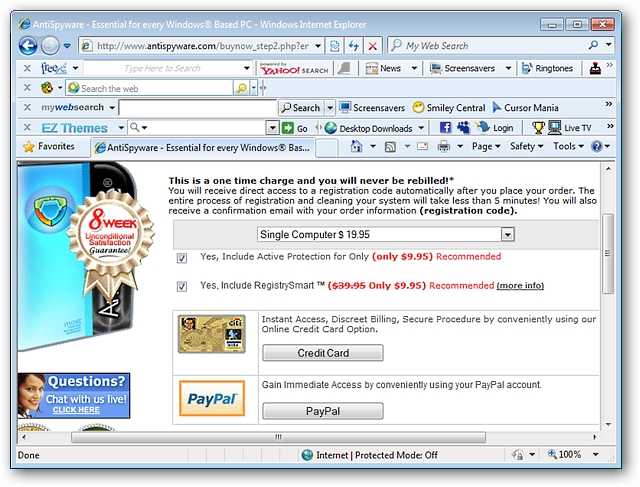
How nice! More additional software available for you to buy and the ability to use that credit card and PayPal!
多好! 您可以购买更多其他软件,以及使用该信用卡和PayPal的功能!
Some Other Things That Come with Malware
恶意软件随附的其他一些内容
Here is another irritating feature of some malware. Nice pop up windows harassing you to take surveys or do other things. This was an additional “gift” from one of the programs installed on our example system.
这是某些恶意软件的另一个令人讨厌的功能。 漂亮的弹出式窗口会骚扰您进行调查或做其他事情。 这是示例系统中安装的程序之一的额外“礼物”。
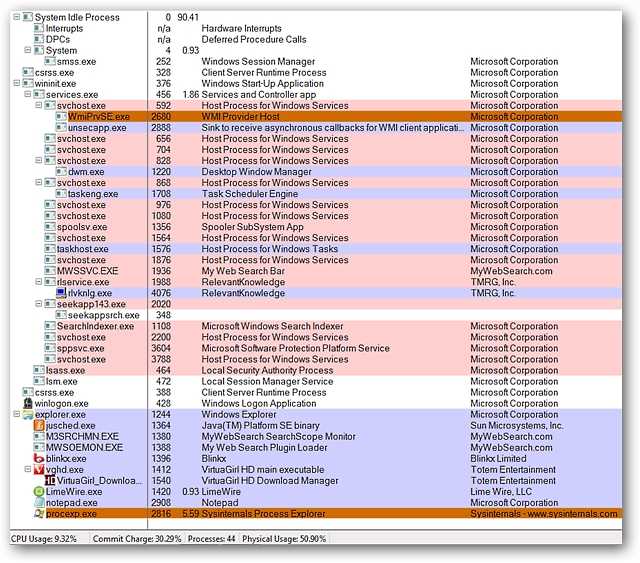
A Look at the Processes Running After Infection
看一下感染后运行的过程
Compare the screenshot of running processes shown at the beginning of the article and then the running processes shown here. You can already see a significant increase. Not good for you or your computer!
比较本文开头显示的正在运行的进程的屏幕截图,然后比较此处显示的正在运行的进程。 您已经可以看到大幅增加。 对您或您的计算机不利!
Conclusion
结论
While nothing super horrible got onto our example system within those 2.5 hours, it is still easy to see just how quickly a system can start to become a mess. Imagine a system that has been exposed for a much longer period of time and is heavily infected! The best approach is to avoid trouble from the beginning. But if you find yourself or someone you know with an infected system then take a look at our upcoming series on removing malware from an infected computer.
在这2.5个小时之内,虽然没有什么可怕的东西进入我们的示例系统,但是仍然很容易看到一个系统能很快变得混乱。 想象一下一个暴露了很长时间并且被严重感染的系统! 最好的方法是从一开始就避免麻烦。 但是,如果您发现自己或认识的某个人带有受感染的系统,请查看我们即将推出的有关从受感染的计算机中删除恶意软件的系列文章。
Note: By the time the short “infestation period” was finished on our example system, the Windows Firewall, Windows Defender, and the Security Settings for Internet Explorer had all been either 1.) Turned off or 2.) Set to the lowest possible settings. In addition, no legitimate anti-virus or anti-malware software was installed. This system was totally unprotected in exchange for so-called “speed and convenience”.
注意:在我们的示例系统上,短暂的“感染期”结束时,Windows防火墙,Windows Defender和Internet Explorer的安全设置全部为1.)关闭或2.)设置为最低设置。 此外,未安装任何合法的防病毒或防恶意软件。 该系统完全不受保护,以换取所谓的“速度和便利性”。
Next Up: Removing the Spyware
下一步:删除间谍软件
Stay tuned, as tomorrow we will show you how we cleaned up the crapware-filled computer with Spybot Search & Destroy. And then later this week, we’ll show how well Ad-Aware and MalwareBytes performed against the same set of spyware.
请继续关注,明天我们将向您展示如何使用Spybot Search&Destroy清理装有垃圾软件的计算机。 然后在本周晚些时候,我们将展示Ad-Aware和MalwareBytes对同一套间谍软件的性能。
翻译自: https://www.howtogeek.com/howto/2998/how-does-spyware-malware-or-crapware-get-on-my-computer/





















 1482
1482











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








