1、经常会遇到多端加解密的情况,因为我们要传一些参数,但是这些参数是要保密的,所以得加个密传输。
2、spring boot拿到加密的串,进行解密,然后进行一些列的操作(比如云端与第三方握手后返回数据,或者与微信端进行交互等)。
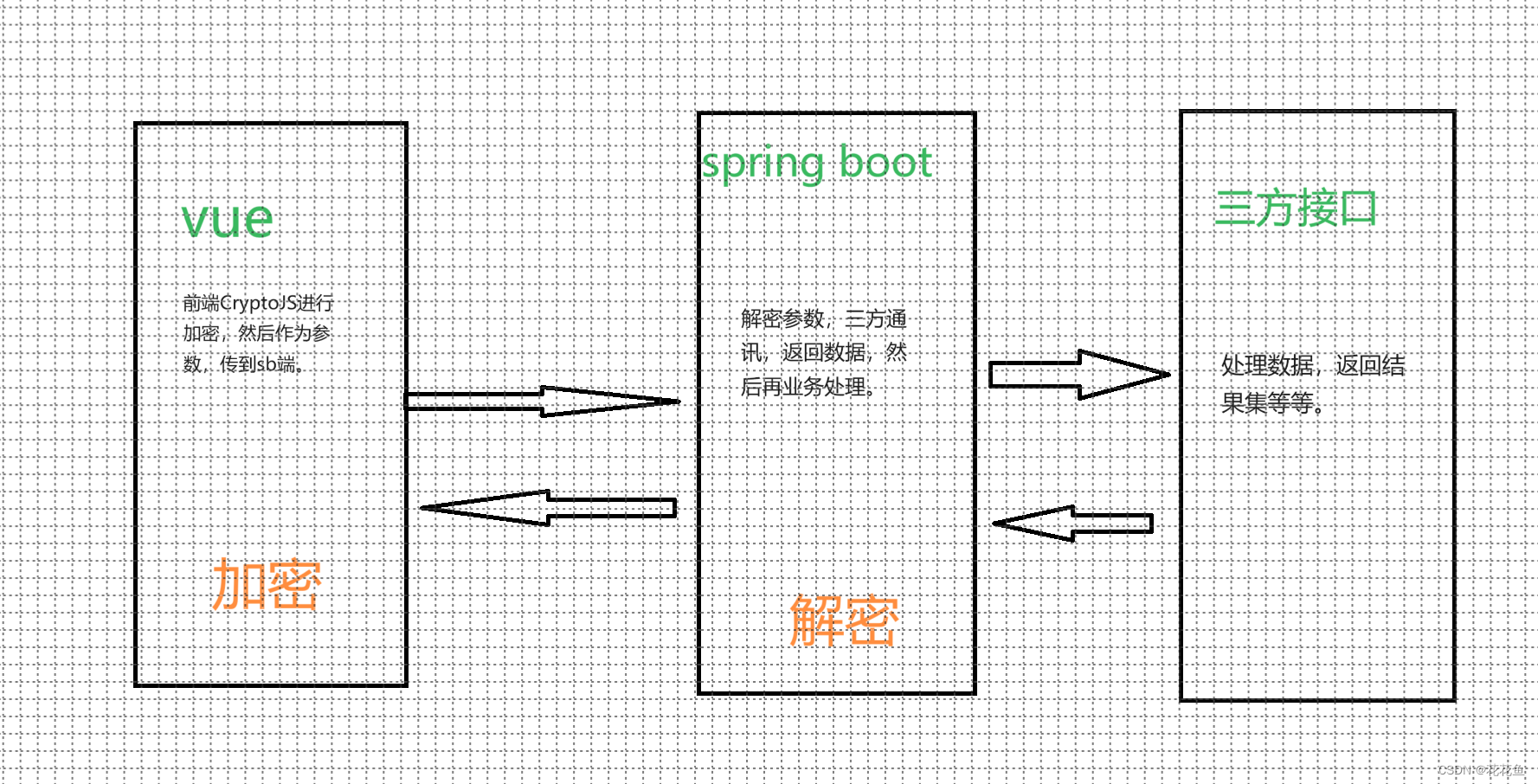
3、vue3 加密
crypto-js 这个库是一个 JavaScript 库,提供了一系列加密算法,可以用于 JavaScript 运行时环境。
pnpm add crypto-jsimport CryptoJS from 'crypto-js';let encrypted = CryptoJS.AES.encrypt('加密串', 'key').toString();
console.log('encrypted', encrypted);
let decrypted = CryptoJS.AES.decrypt(encrypted, 'key').toString(CryptoJS.enc.Utf8);
console.log('decrypted', decrypted);加密串:源字符串(待加密),key:密钥。
4、java(sb)解密:
package com.xxx.xxxx.util;
import javax.crypto.Cipher;
import javax.crypto.spec.IvParameterSpec;
import javax.crypto.spec.SecretKeySpec;
import java.nio.charset.StandardCharsets;
import java.security.DigestException;
import java.security.MessageDigest;
import java.util.Arrays;
import java.util.Base64;
/**
*
* 兼容node
*
*/
public class CryptoUtil {
public static String aesEncrypt(String datastr, String secret) {
try {
byte[] input = datastr.getBytes();
// 以下两个变量不可修改,否则java加密的,node无法解密
byte[] saltData = "DFބf$t:".getBytes();
byte[] preData = "Salted__".getBytes();
MessageDigest md5 = MessageDigest.getInstance("MD5");
final byte[][] keyAndIV = GenerateKeyAndIV(32, 16, 1, saltData, secret.getBytes(StandardCharsets.UTF_8),
md5);
SecretKeySpec key = new SecretKeySpec(keyAndIV[0], "AES");
IvParameterSpec iv = new IvParameterSpec(keyAndIV[1]);
Cipher aesCBC = Cipher.getInstance("AES/CBC/PKCS5Padding");
aesCBC.init(Cipher.ENCRYPT_MODE, key, iv);
byte[] encrypt = aesCBC.doFinal(input);
byte[] encryptedData = addBytes(saltData, encrypt);
byte[] encodedBytes = Base64.getEncoder().encode(addBytes(preData, encryptedData));
return new String(encodedBytes);
} catch (Exception e) {
System.out.println(e.getMessage());
return null;
}
}
public static String aesDecrypt(String encryptedText, String secret) {
// 参考文章:https://www.pianshen.com/question/31931314701/
try {
byte[] cipherData = Base64.getDecoder().decode(encryptedText);
byte[] saltData = Arrays.copyOfRange(cipherData, 8, 16);
MessageDigest md5 = MessageDigest.getInstance("MD5");
final byte[][] keyAndIV = GenerateKeyAndIV(32, 16, 1, saltData, secret.getBytes(StandardCharsets.UTF_8),
md5);
SecretKeySpec key = new SecretKeySpec(keyAndIV[0], "AES");
IvParameterSpec iv = new IvParameterSpec(keyAndIV[1]);
byte[] encrypted = Arrays.copyOfRange(cipherData, 16, cipherData.length);
Cipher aesCBC = Cipher.getInstance("AES/CBC/PKCS5Padding");
aesCBC.init(Cipher.DECRYPT_MODE, key, iv);
byte[] decryptedData = aesCBC.doFinal(encrypted);
return new String(decryptedData, StandardCharsets.UTF_8);
} catch (Exception e) {
System.out.println(e.getMessage());
return null;
}
}
public static byte[][] GenerateKeyAndIV(int keyLength, int ivLength, int iterations, byte[] salt, byte[] password,
MessageDigest md) {
int digestLength = md.getDigestLength();
int requiredLength = (keyLength + ivLength + digestLength - 1) / digestLength * digestLength;
byte[] generatedData = new byte[requiredLength];
int generatedLength = 0;
try {
md.reset();
// Repeat process until sufficient data has been generated
while (generatedLength < keyLength + ivLength) {
// Digest data (last digest if available, password data, salt if available)
if (generatedLength > 0)
md.update(generatedData, generatedLength - digestLength, digestLength);
md.update(password);
if (salt != null)
md.update(salt, 0, 8);
md.digest(generatedData, generatedLength, digestLength);
// additional rounds
for (int i = 1; i < iterations; i++) {
md.update(generatedData, generatedLength, digestLength);
md.digest(generatedData, generatedLength, digestLength);
}
generatedLength += digestLength;
}
// Copy key and IV into separate byte arrays
byte[][] result = new byte[2][];
result[0] = Arrays.copyOfRange(generatedData, 0, keyLength);
if (ivLength > 0)
result[1] = Arrays.copyOfRange(generatedData, keyLength, keyLength + ivLength);
return result;
} catch (DigestException e) {
throw new RuntimeException(e);
} finally {
// Clean out temporary data
Arrays.fill(generatedData, (byte) 0);
}
}
public static byte[] addBytes(byte[] data1, byte[] data2) {
byte[] data3 = new byte[data1.length + data2.length];
System.arraycopy(data1, 0, data3, 0, data1.length);
System.arraycopy(data2, 0, data3, data1.length, data2.length);
return data3;
}
public static void main(String[] args) {
String secret = "key"; //与前端一致。
String datastr = "{\"m\":\"images\",\"u\":\"0\",\"t\":\"20230322\",\"f\":\"16794597950146230.png\"}";
String t = aesEncrypt(datastr, secret);
System.out.println(t);
System.out.println(aesDecrypt(t, secret));
}
}
参考:解决cryptoJS.AES默认参数加密,java无法解密的问题_cryptojs.aes.encrypt java-CSDN博客
这里我将Base64加解密的调整为import java.util.Base64; 就不用引入hutool包了,如果项目中原来就有hutool引入,也可以直接使用上面的。
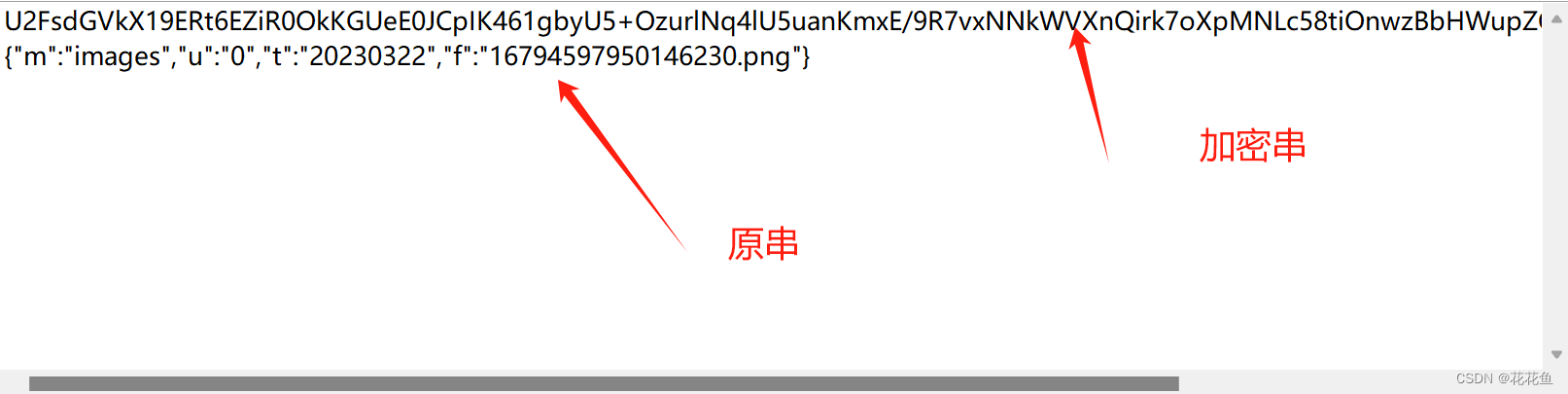
这样简单的前端加密,后端解密的逻辑就可以了。
























 6377
6377











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








