很拉只做出来一道Re,任重而道远啊。。。
BabyMaze
pyc运行发现magic number错误,看看字节码
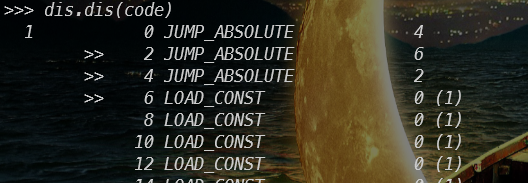
发现花指令
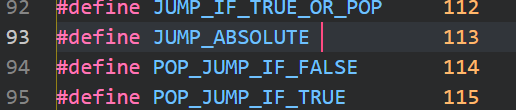
在Python\include\opcode.h里可以看到大小,学到了
JUMP_ABSOLUTE 0x71
发现为这六位
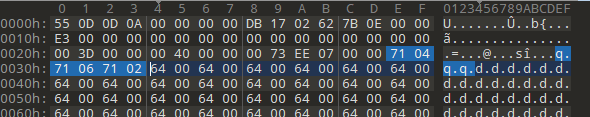
删除并在2A-2B 7EE的大小co_code 要减小为7E8
这用就可以反汇编了
_map = [
[1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1],
[1, 5, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1],
[1, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1],
[1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1],
[1, 0, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1],
[1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1],
[1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1],
[1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1],
[1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1],
[1, 0, 0, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1],
[1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1],
[1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1],
[1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1],
[1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1],
[1, 0, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1],
[1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1],
[1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1],
[1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 1],
[1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 1, 1],
[1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1],
[1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1],
[1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1],
[1, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1],
[1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1],
[1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1, 1, 1, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1],
[1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1],
[1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1],
[1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 1],
[1, 0, 1, 1, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 1, 1, 1, 0, 1],
[1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 0, 7, 1],
[1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1, 1]]
def maze():
x = 1
y = 1
step = input()
for i in range(len(step)):
x -= 1
if step[i] == 's':
x += 1
elif step[i] == 'a':
y -= 1
elif step[i] == 'd':
y += 1
else:
return False
if None[x][y] == 1:
return False
if None == 29 and y == 29:
return True
def main():
print('Welcome To VNCTF2022!!!')
print('Hello Mr. X, this time your mission is to get out of this maze this time.(FIND THAT 7!)')
print('you are still doing the mission alone, this tape will self-destruct in five seconds.')
if maze():
print('Congratulation! flag: VNCTF{md5(your input)}')
else:
print("Sorry, we won't acknowledge the existence of your squad.")
if __name__ == '__main__':
main()
# ssssddssaassddddwwwwddwwddddddwwddddddssddwwddddddddssssaawwaassaassaassddssaassaawwwwwwaaaaaaaassaassddddwwddssddssssaassddssssaaaaaawwddwwaawwwwaassssssssssssddddssddssddddddddwwaaaaaawwwwddssddwwwwwwwwddssddssssssssddddss
# VNCTF{801f190737434100e7d2790bd5b0732e}
时空飞行
一共两轮加密感觉不难,结果死活不出
第一轮加密,就逆向加密就好
#include <stdio.h>
#include <stdint.h>
#include <cstring>
unsigned int key2[4] = {0xa3b1bac6, 0x56aa3350, 0x677d9197, 0xb27022dc};
unsigned int key[32] = {0x00070e15, 0x1c232a31, 0x383f464d, 0x545b6269, 0x70777e85, 0x8c939aa1, 0xa8afb6bd, 0xc4cbd2d9, 0xe0e7eef5, 0xfc030a11, 0x181f262d, 0x343b4249, 0x50575e65, 0x6c737a81, 0x888f969d, 0xa4abb2b9, 0xc0c7ced5, 0xdce3eaf1, 0xf8ff060d, 0x141b2229, 0x30373e45, 0x4c535a61, 0x686f767d, 0x848b9299, 0xa0a7aeb5, 0xbcc3cad1, 0xd8dfe6ed, 0xf4fb0209, 0x10171e25, 0x2c333a41, 0x484f565d, 0x646b7279};
template <class T>
T __ROL__(T value, int count)
{
const unsigned int nbits = sizeof(T) * 8;
if (count > 0)
{
count %= nbits;
T high = value >> (nbits - count);
if (T(-1) < 0) // signed value
high &= ~((T(-1) << count));
value <<= count;
value |= high;
}
else
{
count = -count % nbits;
T low = value << (nbits - count);
value >>= count;
value |= low;
}
return value;
}
inline unsigned int __ROL4__(unsigned int value, int count) { return __ROL__((unsigned int)value, count); }
inline unsigned int __ROR4__(unsigned int value, int count) { return __ROL__((unsigned int)value, -count); }
int Rol(int a1)
{
return a1 ^ (unsigned int)(__ROL4__(a1, 13) ^ __ROR4__(a1, 9));
}
int main(void)
{
unsigned int s[36];
s[35] = 0x96F64587;
s[34] = 0x68D33CD1;
s[33] = 0xEC90A488;
s[32] = 0xFD07C452;
unsigned int k[] = {0xFD07C452, 0xEC90A488, 0x68D33CD1, 0x96F64587};
int i, j, c;
for (i = 31; i >= 0; i--)
s[i] = s[i + 4] ^ Rol(s[i + 3] ^ s[i + 2] ^ s[i + 1] ^ key[i]);
for (i = 0; i < 4; i++)
s[i] ^= key2[i];
for (i = 0; i < 32; i++)
printf("%x ", s[i]);
return 0;
}
20211205
然后运行软件输入时间,接下来需要输入符来歌。
得到enflag
enflag dd 25h, 15h, 0DFh, 0A2h, 0C0h, 93h, 0ADh, 14h, 46h, 0C5h, 0Fh, 2Eh, 9Ah, 0EBh, 30h, 0F8h, 20h, 0E9h, 0CBh, 88h, 0C6h, 0BEh, 8Dh, 0E3h
scanf("%s", flag);
fun(flag1, flag);
for ( i = 0; i <= 5; ++i )
{
v4[4 * i] = (unsigned __int8)flag1[i + 60];
v4[4 * i + 1] = (unsigned __int8)BYTE1(flag1[i + 60]);
v4[4 * i + 2] = (unsigned __int8)BYTE2(flag1[i + 60]);
v4[4 * i + 3] = HIBYTE(flag1[i + 60]);
}
for ( i = 1; i <= 23; ++i )
v4[i - 1] ^= (v4[i - 1] % 0x12u + v4[i] + 5) ^ 0x41;
for ( i = 0; i <= 23; ++i )
{
if ( v4[i] != enflag[i] )
{
for ( i = 0; i <= 5; ++i )
{
for ( j = 0; j <= 5; ++j )
byte_4040E0[6 * i + j] = 14;
}
sub_40188E();
printf("什么东西??唱半天符来歌就这玩意,一定是门的问题!我们再唱会试试...");
exit(0);
}
}
sub_402193(flag);
加密等于enflag即可
但这算法好像爆破不出来,当时就傻了,angr应该可以,但没试
题解是DFS,牛
脚本就用官方的了,懒得写
#include <iostream>
#include <cstring>
static unsigned int Rcon[10] = {0x01000000, 0x02000000, 0x04000000, 0x08000000, 0x10000000,
0x20000000, 0x40000000, 0x80000000, 0x1b000000, 0x36000000};
int GetIntFromChar(char c);
int GetWordFromStr(char *str);
int MergeArrayToInt(int array[4]);
void SplitIntToArray(int num, int array[4]);
void LeftLoop4Int(int array[4], int step);
int T(int num, int round);
void DFS(unsigned char *flag, int deep);
unsigned char flags[30][24]; //已经控制数据在30个以内 你们多设点也可以
unsigned int enc[24] = {0x25, 0x15, 0xDF, 0xA2, 0xC0, 0x93, 0xAD, 0x14, 0x46, 0xC5, 0xF, 0x2E, 0x9A, 0xEB, 0x30, 0xF8, 0x20, 0xE9, 0xCB, 0x88, 0xC6, 0xBE, 0x8D, 0xE3};
int x;
int main(void)
{
int i, j, c;
unsigned int t[66];
unsigned char flag[24];
flag[23] = 0xE3;
DFS(flag, 23); //找到所有可能性放到flags
unsigned int *pi = (unsigned int *)flags; //已⽆符号整形来访问 宽度为24 于4字节访问⼀次 所以为6 //
// for (i = 0; i < 30 * 6; i++)
// {
// printf("0x%X, ", pi[i]);
// if ((i + 1) % 6 == 0)
// printf("\n");
// }
for (c = 0; c <= 30 * 6; c += 6)
{
for (i = 60; i < 66; i++) //填好数据
t[i] = pi[c + i - 60];
for (i = 59, j = 9; i >= 0; i--) //利⽤等式逆回去
{
if (i % 6 == 0)
{
t[i] = t[i + 6] ^ T(t[i + 5], j);
j--;
}
else
t[i] = t[i + 6] ^ t[i + 5];
}
unsigned char *p = (unsigned char *)t;
for (i = 0; i < 24; i += 4)
printf("%c%c%c%c", p[i + 3], p[i + 2], p[i + 1], p[i]); //注意⼩端序
printf("\n");
}
return 0;
}
void DFS(unsigned char *flag, int deep)
{
int i;
if (deep == 0)
{
for (i = 0; i < 24; i++)
{
flags[x][i] = flag[i];
}
x++;
}
else
{
for (i = 0; i < 0xFF; i++)
{
if (((i ^ 0x41) ^ (i % 0x12 + flag[deep] + 0x05)) == enc[deep - 1])
{
flag[deep - 1] = i; //
// printf("0x%X, ", flag[deep - 1]);
DFS(flag, deep - 1);
}
}
}
}
int GetIntFromChar(char c)
{
int result = (int)c;
return result & 0x000000FF;
}
int GetWordFromStr(char *str)
{
int one = GetIntFromChar(str[0]);
one = one << 24;
int two = GetIntFromChar(str[1]);
two = two << 16;
int three = GetIntFromChar(str[2]);
three = three << 8;
int four = GetIntFromChar(str[3]);
return one | two | three | four;
}
int MergeArrayToInt(int array[4])
{
int one = array[0] << 24;
int two = array[1] << 16;
int three = array[2] << 8;
int four = array[3];
return one | two | three | four;
}
void SplitIntToArray(int num, int array[4])
{
int one = num >> 24;
array[0] = one & 0x000000FF;
int two = num >> 16;
array[1] = two & 0x000000FF;
int three = num >> 8;
array[2] = three & 0x000000FF;
array[3] = num & 0x000000FF;
}
void LeftLoop4Int(int array[4], int step)
{
int tmp[4];
int i;
for (i = 0; i < 4; i++)
tmp[i] = array[i];
int index = step;
for (i = 0; i < 4; i++)
{
array[i] = tmp[index];
index++;
index = index % 4;
}
}
int T(int num, int round)
{
int NumArray[4];
SplitIntToArray(num, NumArray);
LeftLoop4Int(NumArray, 1);
int result = MergeArrayToInt(NumArray);
return result ^ Rcon[round];
}
VNCTF{TimeFlightMachine}
最后运行得flag

VNCTF{TimeFl20211205ightMachine}
cm1
在Main中发现check函数中存在loadDexClass
private Boolean check(String arg4) {
IHeihei v0 = this.loadDexClass();
if(v0 == null) {
Toast.makeText(this, "errrrrrrrorrrr what are you doing!!!!!", 0).show();
return Boolean.valueOf(false);
}
return v0.hcheck(arg4).booleanValue() ? Boolean.valueOf(true) : Boolean.valueOf(false);
}
private IHeihei loadDexClass() {
File v0 = this.getDir("dex", 0);
String v1 = v0.getAbsolutePath() + File.separator + "classes.dex";
File v2 = new File(v1);
try {
if(!v2.exists()) {
v2.createNewFile();
FileUtils.copyFiles(this, "ooo", v2);
}
}
catch(IOException v2_1) {
v2_1.printStackTrace();
}
DexClassLoader v2_2 = new DexClassLoader(v1, v0.getAbsolutePath(), null, this.getClassLoader());
try {
IHeihei v0_2 = (IHeihei)v2_2.loadClass("com.vnctf2022.cm1.Haha").newInstance();
if(v0_2 != null) {
return v0_2;
}
Log.e("Mz1", " --- loaderr");
}
catch(Exception v0_1) {
v0_1.printStackTrace();
}
return null;
}
使用了copyFiles加载ooo,(打开发现是乱码)
public static void copyFiles(Context arg6, String arg7, File arg8) {
InputStream v6 = null;
FileOutputStream v7 = null;
byte[] v0 = "vn2022".getBytes();
InputStream v1 = null;
try {
v6 = arg6.getApplicationContext().getAssets().open(arg7);
goto label_16;
}
catch(IOException v8) {
}
catch(Throwable v8_1) {
goto label_63;
}
v7 = null;
goto label_54;
try {
label_16:
v7 = new FileOutputStream(arg8.getAbsolutePath());
byte[] v8_2 = new byte[0x400];
while(true) {
int v1_1 = v6.read(v8_2);
if(v1_1 == -1) {
break;
}
int v3;
for(v3 = 0; v3 < v1_1; ++v3) {
v8_2[v3] = (byte)((v8_2[v3] ^ v0[v3 % v0.length]) & 0xFF);
}
v7.write(v8_2, 0, v1_1);
}
对ooo进行异或操作
key = "vn2022"
with open('ooo', 'rb') as f:
content = f.read()
with open('ooo.out', 'wb') as f:
for i in range(len(content)):
f.write((content[i] ^ ord(key[i % 1024 % len(key)])).to_bytes(
1, byteorder='little', signed=False))
print('ok')
将ooo dex转化jar进行分析可以发现hcheck是xxtea算法
package com.vnctf2022.cm1;
import android.content.Context;
import android.widget.Toast;
public class Haha implements IHeihei {
public String flag;
public Haha() {
this.flag = "flag{fake_flag_again}";
}
public static byte[] bencrypt(byte[] arg3, byte[] arg4) {
return arg3.length == 0 ? arg3 : Haha.toByteArray(Haha.encrypt(Haha.toIntArray(arg3, false), Haha.toIntArray(arg4, false)), false);
}
public static int[] encrypt(int[] arg13, int[] arg14) {
int v3 = 52 / arg13.length + 6;
int v0 = arg13[arg13.length - 1];
int v1 = 0;
do {
v1 -= 1640531527;
int v6 = v1 >>> 2 & 3;
int v4;
for(v4 = 0; v4 < arg13.length - 1; ++v4) {
v0 = ((v0 ^ arg14[v4 & 3 ^ v6]) + (arg13[v4 + 1] ^ v1) ^ (v0 >>> 5 ^ arg13[v4 + 1] << 2) + (arg13[v4 + 1] >>> 3 ^ v0 << 4)) + arg13[v4];
arg13[v4] = v0;
}
int v7 = arg13[0];
int v8 = arg13.length - 1;
v0 = ((v0 ^ arg14[v4 & 3 ^ v6]) + (v7 ^ v1) ^ (v0 >>> 5 ^ v7 << 2) + (v7 >>> 3 ^ v0 << 4)) + arg13[v8];
arg13[v8] = v0;
--v3;
}
while(v3 > 0);
return arg13;
}
public Boolean hcheck(String arg9) {
int v0 = 0;
byte[] v2 = new byte[]{68, 39, -92, 108, -82, -18, 72, -55, 74, -56, 38, 11, 60, 84, 97, -40, 87, 71, 99, -82, 120, 104, 0x2F, -71, -58, -57, 0, 33, 42, 38, -44, -39, -60, 0x71, -2, 92, -75, 0x76, -77, 50, 0x87, 43, 0x20, -106};
byte[] v3 = Haha.bencrypt(arg9.getBytes(), "H4pPY_VNCTF!!OvO".getBytes());
if(v3.length != v2.length) {
return Boolean.valueOf(false);
}
while(v0 < v3.length) {
if(v3[v0] != v2[v0]) {
return Boolean.valueOf(false);
}
++v0;
}
return Boolean.valueOf(true);
}
public void hi(Context arg3) {
Toast.makeText(arg3, "anothor dex", 1).show();
}
private static byte[] toByteArray(int[] arg5, boolean arg6) {
int v0;
int v1 = arg5.length << 2;
if(arg6) {
v0 = arg5[arg5.length - 1];
if(v0 > v1) {
return null;
}
}
else {
v0 = v1;
}
byte[] v1_1 = new byte[v0];
int v2;
for(v2 = 0; v2 < v0; ++v2) {
v1_1[v2] = (byte)(arg5[v2 >>> 2] >>> ((v2 & 3) << 3) & 0xFF);
}
return v1_1;
}
private static int[] toIntArray(byte[] arg7, boolean arg8) {
int[] v0;
int v1 = (arg7.length & 3) == 0 ? arg7.length >>> 2 : (arg7.length >>> 2) + 1;
if(arg8) {
v0 = new int[v1 + 1];
v0[v1] = arg7.length;
}
else {
v0 = new int[v1];
}
int v1_1;
for(v1_1 = 0; v1_1 < arg7.length; ++v1_1) {
int v3 = v1_1 >>> 2;
v0[v3] |= (arg7[v1_1] & 0xFF) << ((v1_1 & 3) << 3);
}
return v0;
}
}
xxtea
写出exp
public class xxtea {
public static byte[] bdecrypt(byte[] data, byte[] key) {
if (data.length == 0) {
return data;
}
return toByteArray(decrypt(toIntArray(data, false), toIntArray(key, false)), false);
}
public static int[] decrypt(int[] v, int[] k) {
int y, z, sum;
int p, rounds, e;
int n = v.length;
rounds = 6 + 52 / n;
sum = rounds * 0x9E3779B9;
y = v[0];
z = v[n - 1];
do {
e = (sum >> 2) & 3;
for (p = n - 1; p > 0; p--) {
z = v[p - 1];
y = v[p] -= (((z >>> 5 ^ y << 2) + (y >>> 3 ^ z << 4)) ^ ((sum ^ y) + (k[(p & 3) ^ e] ^ z)));
}
z = v[n - 1];
y = v[0] -= (((z >>> 5 ^ y << 2) + (y >>> 3 ^ z << 4)) ^ ((sum ^ y) + (k[(p & 3) ^ e] ^ z)));
} while ((sum -= 0x9E3779B9) != 0);
return v;
}
private static int[] toIntArray(byte[] data, boolean includeLength) {
int n = (((data.length & 3) == 0) ? (data.length >>> 2) : ((data.length >>> 2) + 1));
int[] result;
if (includeLength) {
result = new int[n + 1];
result[n] = data.length;
} else {
result = new int[n];
}
n = data.length;
for (int i = 0; i < n; i++) {
result[i >>> 2] |= (0x000000ff & data[i]) << ((i & 3) << 3);
}
return result;
}
private static byte[] toByteArray(int[] data, boolean includeLength) {
int n = data.length << 2;
;
if (includeLength) {
int m = data[data.length - 1];
if (m > n) {
return null;
} else {
n = m;
}
}
byte[] result = new byte[n];
for (int i = 0; i < n; i++) {
result[i] = (byte) ((data[i >>> 2] >>> ((i & 3) << 3)) & 0xff);
}
return result;
}
public static void main(String[] args) {
byte[] aim = { 68, 39, -92, 108, -82, -18, 72, -55, 74, -56, 38, 11, 60, 84, 97, -40, 87, 71, 99, -82, 120, 104,
47, -71, -58, -57, 0, 33, 42, 38, -44, -39, -60, 113, -2, 92, -75, 118, -77, 50, -121, 43, 32, -106 };
byte[] flag = bdecrypt(aim, "H4pPY_VNCTF!!OvO".getBytes());
String f = new String(flag);
System.out.println(f);
// VNCTF{93ee7688-f216-42cb-a5c2-191ff4e412ba}
}
}
这里有个坑,就是在复制c++代码到java,会有>> 到这个的变化 >>>
>>是算术右移,>>>是逻辑右移。
在算术移位中,符号位被扩展以保持数字的符号性。
例如:-2 表示为 8 位11111110(因为最高有效位具有负权重)。使用算术移位将其右移一位会给你11111111,或 -1。然而,逻辑右移并不关心该值是否可能表示一个有符号数。它只是将所有内容向右移动并从左侧填充 0。使用逻辑移位将我们的 -2 右移一位将给出01111111.(127)
还有一点就是DELTA 用的是0x9e3779b9,而不是题中出现的1640531527。
cm狗
vm,go,都没怎么见过 之前一直用的是7.5,听说7.6对go有支持,自动恢复,又下了一个。
main___ptr_MzVm__init函数,虚拟机的初始化函数

然后是opcode,好长
0,0,0;0
0,0,0;3
1,0,87;6
98,0,0;9
1,0,101;12
98,0,0;15
1,0,108;18
98,0,0;21
1,0,99;24
98,0,0;27
1,0,111;30
98,0,0;33
1,0,109;36
98,0,0;39
1,0,101;42
98,0,0;45
1,0,32;48
98,0,0;51
1,0,116;54
98,0,0;57
1,0,111;60
98,0,0;63
1,0,32;66
98,0,0;69
1,0,86;72
98,0,0;75
1,0,78;78
98,0,0;81
1,0,67;84
98,0,0;87
1,0,84;90
98,0,0;93
1,0,70;96
98,0,0;99
1,0,50;102
98,0,0;105
1,0,48;108
98,0,0;111
1,0,50;114
98,0,0;117
1,0,50;120
98,0,0;123
1,0,33;126
98,0,0;129
1,0,10;132
98,0,0;135
1,0,105;138
98,0,0;141
1,0,110;144
98,0,0;147
1,0,112;150
98,0,0;153
1,0,117;156
98,0,0;159
1,0,116;162
98,0,0;165
1,0,32;168
98,0,0;171
1,0,102;174
98,0,0;177
1,0,108;180
98,0,0;183
1,0,97;186
98,0,0;189
1,0,103;192
98,0,0;195
1,0,58;198
98,0,0;201
1,0,10;204
98,0,0;207
1,19,73;210
1,3,0;213
1,1,43;216
1,2,1;219
97,0,0;222
5,0,0;225
8,1,2;228
14,1,3;231
1,0,0;234
5,0,0;237
0,0,0;240
0,0,0;243
6,0,0;246
1,5,256;249
10,0,5;252
2,6,0;255
6,0,0;258
7,6,0;261
2,0,6;264
10,0,5;267
2,6,0;270
6,0,0;273
7,6,0;276
2,0,6;279
10,0,5;282
2,6,0;285
6,0,0;288
7,6,0;291
0,0,0;294
6,0,0;297
1,5,256;300
10,0,5;303
2,7,0;306
6,0,0;309
7,7,0;312
2,0,7;315
10,0,5;318
2,7,0;321
6,0,0;324
7,7,0;327
2,0,7;330
10,0,5;333
2,7,0;336
6,0,0;339
7,7,0;342
0,0,0;345
6,0,0;348
1,5,256;351
10,0,5;354
2,8,0;357
6,0,0;360
7,8,0;363
2,0,8;366
10,0,5;369
2,8,0;372
6,0,0;375
7,8,0;378
2,0,8;381
10,0,5;384
2,8,0;387
6,0,0;390
7,8,0;393
0,0,0;396
6,0,0;399
1,5,256;402
10,0,5;405
2,9,0;408
6,0,0;411
7,9,0;414
2,0,9;417
10,0,5;420
2,9,0;423
6,0,0;426
7,9,0;429
2,0,9;432
10,0,5;435
2,9,0;438
6,0,0;441
7,9,0;444
0,0,0;447
6,0,0;450
1,5,256;453
10,0,5;456
2,10,0;459
6,0,0;462
7,10,0;465
2,0,10;468
10,0,5;471
2,10,0;474
6,0,0;477
7,10,0;480
2,0,10;483
10,0,5;486
2,10,0;489
6,0,0;492
7,10,0;495
0,0,0;498
6,0,0;501
1,5,256;504
10,0,5;507
2,11,0;510
6,0,0;513
7,11,0;516
2,0,11;519
10,0,5;522
2,11,0;525
6,0,0;528
7,11,0;531
2,0,11;534
10,0,5;537
2,11,0;540
6,0,0;543
7,11,0;546
0,0,0;549
6,0,0;552
1,5,256;555
10,0,5;558
2,12,0;561
6,0,0;564
7,12,0;567
2,0,12;570
10,0,5;573
2,12,0;576
6,0,0;579
7,12,0;582
2,0,12;585
10,0,5;588
2,12,0;591
6,0,0;594
7,12,0;597
0,0,0;600
6,0,0;603
1,5,256;606
10,0,5;609
2,13,0;612
6,0,0;615
7,13,0;618
2,0,13;621
10,0,5;624
2,13,0;627
6,0,0;630
7,13,0;633
2,0,13;636
10,0,5;639
2,13,0;642
6,0,0;645
7,13,0;648
0,0,0;651
6,0,0;654
1,5,256;657
10,0,5;660
2,14,0;663
6,0,0;666
7,14,0;669
2,0,14;672
10,0,5;675
2,14,0;678
6,0,0;681
7,14,0;684
2,0,14;687
10,0,5;690
2,14,0;693
6,0,0;696
7,14,0;699
0,0,0;702
6,0,0;705
1,5,256;708
10,0,5;711
2,15,0;714
6,0,0;717
7,15,0;720
2,0,15;723
10,0,5;726
2,15,0;729
6,0,0;732
7,15,0;735
2,0,15;738
10,0,5;741
2,15,0;744
6,0,0;747
7,15,0;750
0,0,0;753
6,0,0;756
1,5,256;759
10,0,5;762
2,16,0;765
6,0,0;768
7,16,0;771
2,0,16;774
10,0,5;777
2,16,0;780
6,0,0;783
7,16,0;786
2,0,16;789
10,0,5;792
2,16,0;795
6,0,0;798
7,16,0;801
0,0,0;804
5,6,0;807
5,7,0;810
5,8,0;813
5,9,0;816
5,10,0;819
5,11,0;822
5,12,0;825
5,13,0;828
5,14,0;831
5,15,0;834
5,16,0;837
6,1,0;840
6,2,0;843
1,20,284;846
1,0,340;849
12,0,0;852
1,0,-388901409;855
1,19,387;858
1,20,339;861
14,1,0;864
1,0,-169623276;867
14,2,0;870
6,1,0;873
6,2,0;876
1,20,295;879
1,0,340;882
12,0,0;885
1,0,579781142;888
1,19,387;891
1,20,339;894
14,1,0;897
1,0,-1982571935;900
14,2,0;903
6,1,0;906
6,2,0;909
1,20,306;912
1,0,340;915
12,0,0;918
1,0,1700499305;921
1,19,387;924
1,20,339;927
14,1,0;930
1,0,612671610;933
14,2,0;936
6,1,0;939
6,2,0;942
1,20,317;945
1,0,340;948
12,0,0;951
1,0,-639244296;954
1,19,387;957
1,20,339;960
14,1,0;963
1,0,977540402;966
14,2,0;969
6,1,0;972
6,2,0;975
1,20,328;978
1,0,340;981
12,0,0;984
1,0,-1851031928;987
1,19,387;990
1,20,339;993
14,1,0;996
1,0,1778148540;999
14,2,0;1002
6,1,0;1005
1,0,8206181;1008
14,1,0;1011
1,0,393;1014
12,0,0;1017
99,0,0;1020
1,3,-1640531527;1023
1,4,613452;1026
1,5,34589;1029
1,6,108471;1032
1,7,1230791;1035
1,8,0;1038
1,17,16;1041
1,18,32;1044
1,19,352;1047
1,10,0;1050
1,11,32;1053
1,12,1;1056
7,8,3;1059
2,0,2;1062
10,0,17;1065
7,0,4;1068
2,14,0;1071
2,0,2;1074
7,0,8;1077
2,15,0;1080
2,0,2;1083
9,0,18;1086
7,0,5;1089
2,16,0;1092
2,0,14;1095
11,0,15;1098
11,0,16;1101
7,1,0;1104
2,0,1;1107
10,0,17;1110
7,0,6;1113
2,14,0;1116
2,0,1;1119
7,0,8;1122
2,15,0;1125
2,0,1;1128
9,0,18;1131
7,0,7;1134
2,16,0;1137
2,0,14;1140
11,0,15;1143
11,0,16;1146
7,2,0;1149
8,11,12;1152
14,11,10;1155
12,20,0;1158
0,0,0;1161
1,0,110;1164
98,0,0;1167
1,0,111;1170
98,0,0;1173
12,20,0;1176
0,0,0;1179
1,0,121;1182
98,0,0;1185
1,0,101;1188
98,0,0;1191
1,0,115;1194
98,0,0;1197
12,20,0;1200
0,0,0;1203
不知道该怎么办了,官方文档写的不详细
参考这个VNCTF2022的wp
code=[0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x57, 0x62, 0x00, 0x00, 0x01, 0x00, 0x65, 0x62, 0x00, 0x00, 0x01, 0x00, 0x6C, 0x62, 0x00, 0x00, 0x01, 0x00, 0x63, 0x62, 0x00, 0x00, 0x01, 0x00, 0x6F, 0x62, 0x00, 0x00, 0x01, 0x00, 0x6D, 0x62, 0x00, 0x00, 0x01, 0x00, 0x65, 0x62, 0x00, 0x00, 0x01, 0x00, 0x20, 0x62, 0x00, 0x00, 0x01, 0x00, 0x74, 0x62, 0x00, 0x00, 0x01, 0x00, 0x6F, 0x62, 0x00, 0x00, 0x01, 0x00, 0x20, 0x62, 0x00, 0x00, 0x01, 0x00, 0x56, 0x62, 0x00, 0x00, 0x01, 0x00, 0x4E, 0x62, 0x00, 0x00, 0x01, 0x00, 0x43, 0x62, 0x00, 0x00, 0x01, 0x00, 0x54, 0x62, 0x00, 0x00, 0x01, 0x00, 0x46, 0x62, 0x00, 0x00, 0x01, 0x00, 0x32, 0x62, 0x00, 0x00, 0x01, 0x00, 0x30, 0x62, 0x00, 0x00, 0x01, 0x00, 0x32, 0x62, 0x00, 0x00, 0x01, 0x00, 0x32, 0x62, 0x00, 0x00, 0x01, 0x00, 0x21, 0x62, 0x00, 0x00, 0x01, 0x00, 0x0A, 0x62, 0x00, 0x00, 0x01, 0x00, 0x69, 0x62, 0x00, 0x00, 0x01, 0x00, 0x6E, 0x62, 0x00, 0x00, 0x01, 0x00, 0x70, 0x62, 0x00, 0x00, 0x01, 0x00, 0x75, 0x62, 0x00, 0x00, 0x01, 0x00, 0x74, 0x62, 0x00, 0x00, 0x01, 0x00, 0x20, 0x62, 0x00, 0x00, 0x01, 0x00, 0x66, 0x62, 0x00, 0x00, 0x01, 0x00, 0x6C, 0x62, 0x00, 0x00, 0x01, 0x00, 0x61, 0x62, 0x00, 0x00, 0x01, 0x00, 0x67, 0x62, 0x00, 0x00, 0x01, 0x00, 0x3A, 0x62, 0x00, 0x00, 0x01, 0x00, 0x0A, 0x62, 0x00, 0x00, 0x01, 0x13, 0x49, 0x01, 0x03, 0x00, 0x01, 0x01, 0x2B, 0x01, 0x02, 0x01, 0x61, 0x00, 0x00, 0x05, 0x00, 0x00, 0x08, 0x01, 0x02, 0x0E, 0x01, 0x03, 0x01, 0x00, 0x00, 0x05, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x06, 0x00, 0x00, 0x01, 0x05, 0x00000100, 0x0A, 0x00, 0x05, 0x02, 0x06, 0x00, 0x06, 0x00, 0x00, 0x07, 0x06, 0x00, 0x02, 0x00, 0x06, 0x0A, 0x00, 0x05, 0x02, 0x06, 0x00, 0x06, 0x00, 0x00, 0x07, 0x06, 0x00, 0x02, 0x00, 0x06, 0x0A, 0x00, 0x05, 0x02, 0x06, 0x00, 0x06, 0x00, 0x00, 0x07, 0x06, 0x00, 0x00, 0x00, 0x00, 0x06, 0x00, 0x00, 0x01, 0x05, 0x00000100, 0x0A, 0x00, 0x05, 0x02, 0x07, 0x00, 0x06, 0x00, 0x00, 0x07, 0x07, 0x00, 0x02, 0x00, 0x07, 0x0A, 0x00, 0x05, 0x02, 0x07, 0x00, 0x06, 0x00, 0x00, 0x07, 0x07, 0x00, 0x02, 0x00, 0x07, 0x0A, 0x00, 0x05, 0x02, 0x07, 0x00, 0x06, 0x00, 0x00, 0x07, 0x07, 0x00, 0x00, 0x00, 0x00, 0x06, 0x00, 0x00, 0x01, 0x05, 0x00000100, 0x0A, 0x00, 0x05, 0x02, 0x08, 0x00, 0x06, 0x00, 0x00, 0x07, 0x08, 0x00, 0x02, 0x00, 0x08, 0x0A, 0x00, 0x05, 0x02, 0x08, 0x00, 0x06, 0x00, 0x00, 0x07, 0x08, 0x00, 0x02, 0x00, 0x08, 0x0A, 0x00, 0x05, 0x02, 0x08, 0x00, 0x06, 0x00, 0x00, 0x07, 0x08, 0x00, 0x00, 0x00, 0x00, 0x06, 0x00, 0x00, 0x01, 0x05, 0x00000100, 0x0A, 0x00, 0x05, 0x02, 0x09, 0x00, 0x06, 0x00, 0x00, 0x07, 0x09, 0x00, 0x02, 0x00, 0x09, 0x0A, 0x00, 0x05, 0x02, 0x09, 0x00, 0x06, 0x00, 0x00, 0x07, 0x09, 0x00, 0x02, 0x00, 0x09, 0x0A, 0x00, 0x05, 0x02, 0x09, 0x00, 0x06, 0x00, 0x00, 0x07, 0x09, 0x00, 0x00, 0x00, 0x00, 0x06, 0x00, 0x00, 0x01, 0x05, 0x00000100, 0x0A, 0x00, 0x05, 0x02, 0x0A, 0x00, 0x06, 0x00, 0x00, 0x07, 0x0A, 0x00, 0x02, 0x00, 0x0A, 0x0A, 0x00, 0x05, 0x02, 0x0A, 0x00, 0x06, 0x00, 0x00, 0x07, 0x0A, 0x00, 0x02, 0x00, 0x0A, 0x0A, 0x00, 0x05, 0x02, 0x0A, 0x00, 0x06, 0x00, 0x00, 0x07, 0x0A, 0x00, 0x00, 0x00, 0x00, 0x06, 0x00, 0x00, 0x01, 0x05, 0x00000100, 0x0A, 0x00, 0x05, 0x02, 0x0B, 0x00, 0x06, 0x00, 0x00, 0x07, 0x0B, 0x00, 0x02, 0x00, 0x0B, 0x0A, 0x00, 0x05, 0x02, 0x0B, 0x00, 0x06, 0x00, 0x00, 0x07, 0x0B, 0x00, 0x02, 0x00, 0x0B, 0x0A, 0x00, 0x05, 0x02, 0x0B, 0x00, 0x06, 0x00, 0x00, 0x07, 0x0B, 0x00, 0x00, 0x00, 0x00, 0x06, 0x00, 0x00, 0x01, 0x05, 0x00000100, 0x0A, 0x00, 0x05, 0x02, 0x0C, 0x00, 0x06, 0x00, 0x00, 0x07, 0x0C, 0x00, 0x02, 0x00, 0x0C, 0x0A, 0x00, 0x05, 0x02, 0x0C, 0x00, 0x06, 0x00, 0x00, 0x07, 0x0C, 0x00, 0x02, 0x00, 0x0C, 0x0A, 0x00, 0x05, 0x02, 0x0C, 0x00, 0x06, 0x00, 0x00, 0x07, 0x0C, 0x00, 0x00, 0x00, 0x00, 0x06, 0x00, 0x00, 0x01, 0x05, 0x00000100, 0x0A, 0x00, 0x05, 0x02, 0x0D, 0x00, 0x06, 0x00, 0x00, 0x07, 0x0D, 0x00, 0x02, 0x00, 0x0D, 0x0A, 0x00, 0x05, 0x02, 0x0D, 0x00, 0x06, 0x00, 0x00, 0x07, 0x0D, 0x00, 0x02, 0x00, 0x0D, 0x0A, 0x00, 0x05, 0x02, 0x0D, 0x00, 0x06, 0x00, 0x00, 0x07, 0x0D, 0x00, 0x00, 0x00, 0x00, 0x06, 0x00, 0x00, 0x01, 0x05, 0x00000100, 0x0A, 0x00, 0x05, 0x02, 0x0E, 0x00, 0x06, 0x00, 0x00, 0x07, 0x0E, 0x00, 0x02, 0x00, 0x0E, 0x0A, 0x00, 0x05, 0x02, 0x0E, 0x00, 0x06, 0x00, 0x00, 0x07, 0x0E, 0x00, 0x02, 0x00, 0x0E, 0x0A, 0x00, 0x05, 0x02, 0x0E, 0x00, 0x06, 0x00, 0x00, 0x07, 0x0E, 0x00, 0x00, 0x00, 0x00, 0x06, 0x00, 0x00, 0x01, 0x05, 0x00000100, 0x0A, 0x00, 0x05, 0x02, 0x0F, 0x00, 0x06, 0x00, 0x00, 0x07, 0x0F, 0x00, 0x02, 0x00, 0x0F, 0x0A, 0x00, 0x05, 0x02, 0x0F, 0x00, 0x06, 0x00, 0x00, 0x07, 0x0F, 0x00, 0x02, 0x00, 0x0F, 0x0A, 0x00, 0x05, 0x02, 0x0F, 0x00, 0x06, 0x00, 0x00, 0x07, 0x0F, 0x00, 0x00, 0x00, 0x00, 0x06, 0x00, 0x00, 0x01, 0x05, 0x00000100, 0x0A, 0x00, 0x05, 0x02, 0x10, 0x00, 0x06, 0x00, 0x00, 0x07, 0x10, 0x00, 0x02, 0x00, 0x10, 0x0A, 0x00, 0x05, 0x02, 0x10, 0x00, 0x06, 0x00, 0x00, 0x07, 0x10, 0x00, 0x02, 0x00, 0x10, 0x0A, 0x00, 0x05, 0x02, 0x10, 0x00, 0x06, 0x00, 0x00, 0x07, 0x10, 0x00, 0x00, 0x00, 0x00, 0x05, 0x06, 0x00, 0x05, 0x07, 0x00, 0x05, 0x08, 0x00, 0x05, 0x09, 0x00, 0x05, 0x0A, 0x00, 0x05, 0x0B, 0x00, 0x05, 0x0C, 0x00, 0x05, 0x0D, 0x00, 0x05, 0x0E, 0x00, 0x05, 0x0F, 0x00, 0x05, 0x10, 0x00, 0x06, 0x01, 0x00, 0x06, 0x02, 0x00, 0x01, 0x14, 0x0000011C, 0x01, 0x00, 0x00000154, 0x0C, 0x00, 0x00, 0x01, 0x00, 0xE8D1D5DF, 0x01, 0x13, 0x00000183, 0x01, 0x14, 0x00000153, 0x0E, 0x01, 0x00, 0x01, 0x00, 0xF5E3C114, 0x0E, 0x02, 0x00, 0x06, 0x01, 0x00, 0x06, 0x02, 0x00, 0x01, 0x14, 0x00000127, 0x01, 0x00, 0x00000154, 0x0C, 0x00, 0x00, 0x01, 0x00, 0x228EC216, 0x01, 0x13, 0x00000183, 0x01, 0x14, 0x00000153, 0x0E, 0x01, 0x00, 0x01, 0x00, 0x89D45A61, 0x0E, 0x02, 0x00, 0x06, 0x01, 0x00, 0x06, 0x02, 0x00, 0x01, 0x14, 0x00000132, 0x01, 0x00, 0x00000154, 0x0C, 0x00, 0x00, 0x01, 0x00, 0x655B8F69, 0x01, 0x13, 0x00000183, 0x01, 0x14, 0x00000153, 0x0E, 0x01, 0x00, 0x01, 0x00, 0x2484A07A, 0x0E, 0x02, 0x00, 0x06, 0x01, 0x00, 0x06, 0x02, 0x00, 0x01, 0x14, 0x0000013D, 0x01, 0x00, 0x00000154, 0x0C, 0x00, 0x00, 0x01, 0x00, 0xD9E5E7F8, 0x01, 0x13, 0x00000183, 0x01, 0x14, 0x00000153, 0x0E, 0x01, 0x00, 0x01, 0x00, 0x3A441532, 0x0E, 0x02, 0x00, 0x06, 0x01, 0x00, 0x06, 0x02, 0x00, 0x01, 0x14, 0x00000148, 0x01, 0x00, 0x00000154, 0x0C, 0x00, 0x00, 0x01, 0x00, 0x91AB7E88, 0x01, 0x13, 0x00000183, 0x01, 0x14, 0x00000153, 0x0E, 0x01, 0x00, 0x01, 0x00, 0x69FC64BC, 0x0E, 0x02, 0x00, 0x06, 0x01, 0x00, 0x01, 0x00, 0x007D3765, 0x0E, 0x01, 0x00, 0x01, 0x00, 0x00000189, 0x0C, 0x00, 0x00, 0x63, 0x00, 0x00, 0x01, 0x03, 0x9E3779B9, 0x01, 0x04, 0x00095C4C, 0x01, 0x05, 0x0000871D, 0x01, 0x06, 0x0001A7B7, 0x01, 0x07, 0x0012C7C7, 0x01, 0x08, 0x00, 0x01, 0x11, 0x10, 0x01, 0x12, 0x20, 0x01, 0x13, 0x00000160, 0x01, 0x0A, 0x00, 0x01, 0x0B, 0x20, 0x01, 0x0C, 0x01, 0x07, 0x08, 0x03, 0x02, 0x00, 0x02, 0x0A, 0x00, 0x11, 0x07, 0x00, 0x04, 0x02, 0x0E, 0x00, 0x02, 0x00, 0x02, 0x07, 0x00, 0x08, 0x02, 0x0F, 0x00, 0x02, 0x00, 0x02, 0x09, 0x00, 0x12, 0x07, 0x00, 0x05, 0x02, 0x10, 0x00, 0x02, 0x00, 0x0E, 0x0B, 0x00, 0x0F, 0x0B, 0x00, 0x10, 0x07, 0x01, 0x00, 0x02, 0x00, 0x01, 0x0A, 0x00, 0x11, 0x07, 0x00, 0x06, 0x02, 0x0E, 0x00, 0x02, 0x00, 0x01, 0x07, 0x00, 0x08, 0x02, 0x0F, 0x00, 0x02, 0x00, 0x01, 0x09, 0x00, 0x12, 0x07, 0x00, 0x07, 0x02, 0x10, 0x00, 0x02, 0x00, 0x0E, 0x0B, 0x00, 0x0F, 0x0B, 0x00, 0x10, 0x07, 0x02, 0x00, 0x08, 0x0B, 0x0C, 0x0E, 0x0B, 0x0A, 0x0C, 0x14, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x6E, 0x62, 0x00, 0x00, 0x01, 0x00, 0x6F, 0x62, 0x00, 0x00, 0x0C, 0x14, 0x00, 0x00, 0x00, 0x00, 0x01, 0x00, 0x79, 0x62, 0x00, 0x00, 0x01, 0x00, 0x65, 0x62, 0x00, 0x00, 0x01, 0x00, 0x73, 0x62, 0x00, 0x00, 0x0C, 0x14, 0x00]
calllist=['nop','load','copy','returnN','enterN','push','pop','add','sub','divide','multiply','xor','jump','ifequ','ifneq','iflt','ifgt']
funlist={}
for i,e in enumerate(calllist):
funlist[i]=e
funlist[0x61]='getinput'
funlist[0x62]='output'
funlist[0x63]='quit'
rip=0
while(rip<len(code)-1):
instr=code[rip]
print(hex(rip//3),funlist[instr],hex(code[rip+1]),hex(code[rip+2]))
rip+=3
运行结果如下
0x0 nop 0x0 0x0
0x1 nop 0x0 0x0
0x2 load 0x0 0x57
0x3 output 0x0 0x0
0x4 load 0x0 0x65
0x5 output 0x0 0x0
0x6 load 0x0 0x6c
0x7 output 0x0 0x0
0x8 load 0x0 0x63
0x9 output 0x0 0x0
0xa load 0x0 0x6f
0xb output 0x0 0x0
0xc load 0x0 0x6d
0xd output 0x0 0x0
0xe load 0x0 0x65
0xf output 0x0 0x0
0x10 load 0x0 0x20
0x11 output 0x0 0x0
0x12 load 0x0 0x74
0x13 output 0x0 0x0
0x14 load 0x0 0x6f
0x15 output 0x0 0x0
0x16 load 0x0 0x20
0x17 output 0x0 0x0
0x18 load 0x0 0x56
0x19 output 0x0 0x0
0x1a load 0x0 0x4e
0x1b output 0x0 0x0
0x1c load 0x0 0x43
0x1d output 0x0 0x0
0x1e load 0x0 0x54
0x1f output 0x0 0x0
0x20 load 0x0 0x46
0x21 output 0x0 0x0
0x22 load 0x0 0x32
0x23 output 0x0 0x0
0x24 load 0x0 0x30
0x25 output 0x0 0x0
0x26 load 0x0 0x32
0x27 output 0x0 0x0
0x28 load 0x0 0x32
0x29 output 0x0 0x0
0x2a load 0x0 0x21
0x2b output 0x0 0x0
0x2c load 0x0 0xa
0x2d output 0x0 0x0
0x2e load 0x0 0x69
0x2f output 0x0 0x0
0x30 load 0x0 0x6e
0x31 output 0x0 0x0
0x32 load 0x0 0x70
0x33 output 0x0 0x0
0x34 load 0x0 0x75
0x35 output 0x0 0x0
0x36 load 0x0 0x74
0x37 output 0x0 0x0
0x38 load 0x0 0x20
0x39 output 0x0 0x0
0x3a load 0x0 0x66
0x3b output 0x0 0x0
0x3c load 0x0 0x6c
0x3d output 0x0 0x0
0x3e load 0x0 0x61
0x3f output 0x0 0x0
0x40 load 0x0 0x67
0x41 output 0x0 0x0
0x42 load 0x0 0x3a
0x43 output 0x0 0x0
0x44 load 0x0 0xa
0x45 output 0x0 0x0
0x46 load 0x13 0x49
0x47 load 0x3 0x0
0x48 load 0x1 0x2b
0x49 load 0x2 0x1
0x4a getinput 0x0 0x0
0x4b push 0x0 0x0
0x4c sub 0x1 0x2
0x4d ifneq 0x1 0x3
0x4e load 0x0 0x0
0x4f push 0x0 0x0
0x50 nop 0x0 0x0
0x51 nop 0x0 0x0
0x52 pop 0x0 0x0
0x53 load 0x5 0x100
0x54 multiply 0x0 0x5
0x55 copy 0x6 0x0
0x56 pop 0x0 0x0
0x57 add 0x6 0x0
0x58 copy 0x0 0x6
0x59 multiply 0x0 0x5
0x5a copy 0x6 0x0
0x5b pop 0x0 0x0
0x5c add 0x6 0x0
0x5d copy 0x0 0x6
0x5e multiply 0x0 0x5
0x5f copy 0x6 0x0
0x60 pop 0x0 0x0
0x61 add 0x6 0x0
0x62 nop 0x0 0x0
0x63 pop 0x0 0x0
0x64 load 0x5 0x100
0x65 multiply 0x0 0x5
0x66 copy 0x7 0x0
0x67 pop 0x0 0x0
0x68 add 0x7 0x0
0x69 copy 0x0 0x7
0x6a multiply 0x0 0x5
0x6b copy 0x7 0x0
0x6c pop 0x0 0x0
0x6d add 0x7 0x0
0x6e copy 0x0 0x7
0x6f multiply 0x0 0x5
0x70 copy 0x7 0x0
0x71 pop 0x0 0x0
0x72 add 0x7 0x0
0x73 nop 0x0 0x0
0x74 pop 0x0 0x0
0x75 load 0x5 0x100
0x76 multiply 0x0 0x5
0x77 copy 0x8 0x0
0x78 pop 0x0 0x0
0x79 add 0x8 0x0
0x7a copy 0x0 0x8
0x7b multiply 0x0 0x5
0x7c copy 0x8 0x0
0x7d pop 0x0 0x0
0x7e add 0x8 0x0
0x7f copy 0x0 0x8
0x80 multiply 0x0 0x5
0x81 copy 0x8 0x0
0x82 pop 0x0 0x0
0x83 add 0x8 0x0
0x84 nop 0x0 0x0
0x85 pop 0x0 0x0
0x86 load 0x5 0x100
0x87 multiply 0x0 0x5
0x88 copy 0x9 0x0
0x89 pop 0x0 0x0
0x8a add 0x9 0x0
0x8b copy 0x0 0x9
0x8c multiply 0x0 0x5
0x8d copy 0x9 0x0
0x8e pop 0x0 0x0
0x8f add 0x9 0x0
0x90 copy 0x0 0x9
0x91 multiply 0x0 0x5
0x92 copy 0x9 0x0
0x93 pop 0x0 0x0
0x94 add 0x9 0x0
0x95 nop 0x0 0x0
0x96 pop 0x0 0x0
0x97 load 0x5 0x100
0x98 multiply 0x0 0x5
0x99 copy 0xa 0x0
0x9a pop 0x0 0x0
0x9b add 0xa 0x0
0x9c copy 0x0 0xa
0x9d multiply 0x0 0x5
0x9e copy 0xa 0x0
0x9f pop 0x0 0x0
0xa0 add 0xa 0x0
0xa1 copy 0x0 0xa
0xa2 multiply 0x0 0x5
0xa3 copy 0xa 0x0
0xa4 pop 0x0 0x0
0xa5 add 0xa 0x0
0xa6 nop 0x0 0x0
0xa7 pop 0x0 0x0
0xa8 load 0x5 0x100
0xa9 multiply 0x0 0x5
0xaa copy 0xb 0x0
0xab pop 0x0 0x0
0xac add 0xb 0x0
0xad copy 0x0 0xb
0xae multiply 0x0 0x5
0xaf copy 0xb 0x0
0xb0 pop 0x0 0x0
0xb1 add 0xb 0x0
0xb2 copy 0x0 0xb
0xb3 multiply 0x0 0x5
0xb4 copy 0xb 0x0
0xb5 pop 0x0 0x0
0xb6 add 0xb 0x0
0xb7 nop 0x0 0x0
0xb8 pop 0x0 0x0
0xb9 load 0x5 0x100
0xba multiply 0x0 0x5
0xbb copy 0xc 0x0
0xbc pop 0x0 0x0
0xbd add 0xc 0x0
0xbe copy 0x0 0xc
0xbf multiply 0x0 0x5
0xc0 copy 0xc 0x0
0xc1 pop 0x0 0x0
0xc2 add 0xc 0x0
0xc3 copy 0x0 0xc
0xc4 multiply 0x0 0x5
0xc5 copy 0xc 0x0
0xc6 pop 0x0 0x0
0xc7 add 0xc 0x0
0xc8 nop 0x0 0x0
0xc9 pop 0x0 0x0
0xca load 0x5 0x100
0xcb multiply 0x0 0x5
0xcc copy 0xd 0x0
0xcd pop 0x0 0x0
0xce add 0xd 0x0
0xcf copy 0x0 0xd
0xd0 multiply 0x0 0x5
0xd1 copy 0xd 0x0
0xd2 pop 0x0 0x0
0xd3 add 0xd 0x0
0xd4 copy 0x0 0xd
0xd5 multiply 0x0 0x5
0xd6 copy 0xd 0x0
0xd7 pop 0x0 0x0
0xd8 add 0xd 0x0
0xd9 nop 0x0 0x0
0xda pop 0x0 0x0
0xdb load 0x5 0x100
0xdc multiply 0x0 0x5
0xdd copy 0xe 0x0
0xde pop 0x0 0x0
0xdf add 0xe 0x0
0xe0 copy 0x0 0xe
0xe1 multiply 0x0 0x5
0xe2 copy 0xe 0x0
0xe3 pop 0x0 0x0
0xe4 add 0xe 0x0
0xe5 copy 0x0 0xe
0xe6 multiply 0x0 0x5
0xe7 copy 0xe 0x0
0xe8 pop 0x0 0x0
0xe9 add 0xe 0x0
0xea nop 0x0 0x0
0xeb pop 0x0 0x0
0xec load 0x5 0x100
0xed multiply 0x0 0x5
0xee copy 0xf 0x0
0xef pop 0x0 0x0
0xf0 add 0xf 0x0
0xf1 copy 0x0 0xf
0xf2 multiply 0x0 0x5
0xf3 copy 0xf 0x0
0xf4 pop 0x0 0x0
0xf5 add 0xf 0x0
0xf6 copy 0x0 0xf
0xf7 multiply 0x0 0x5
0xf8 copy 0xf 0x0
0xf9 pop 0x0 0x0
0xfa add 0xf 0x0
0xfb nop 0x0 0x0
0xfc pop 0x0 0x0
0xfd load 0x5 0x100
0xfe multiply 0x0 0x5
0xff copy 0x10 0x0
0x100 pop 0x0 0x0
0x101 add 0x10 0x0
0x102 copy 0x0 0x10
0x103 multiply 0x0 0x5
0x104 copy 0x10 0x0
0x105 pop 0x0 0x0
0x106 add 0x10 0x0
0x107 copy 0x0 0x10
0x108 multiply 0x0 0x5
0x109 copy 0x10 0x0
0x10a pop 0x0 0x0
0x10b add 0x10 0x0
0x10c nop 0x0 0x0
0x10d push 0x6 0x0
0x10e push 0x7 0x0
0x10f push 0x8 0x0
0x110 push 0x9 0x0
0x111 push 0xa 0x0
0x112 push 0xb 0x0
0x113 push 0xc 0x0
0x114 push 0xd 0x0
0x115 push 0xe 0x0
0x116 push 0xf 0x0
0x117 push 0x10 0x0
0x118 pop 0x1 0x0
0x119 pop 0x2 0x0
0x11a load 0x14 0x11c
0x11b load 0x0 0x154
0x11c jump 0x0 0x0
0x11d load 0x0 0xe8d1d5df
0x11e load 0x13 0x183
0x11f load 0x14 0x153
0x120 ifneq 0x1 0x0
0x121 load 0x0 0xf5e3c114
0x122 ifneq 0x2 0x0
0x123 pop 0x1 0x0
0x124 pop 0x2 0x0
0x125 load 0x14 0x127
0x126 load 0x0 0x154
0x127 jump 0x0 0x0
0x128 load 0x0 0x228ec216
0x129 load 0x13 0x183
0x12a load 0x14 0x153
0x12b ifneq 0x1 0x0
0x12c load 0x0 0x89d45a61
0x12d ifneq 0x2 0x0
0x12e pop 0x1 0x0
0x12f pop 0x2 0x0
0x130 load 0x14 0x132
0x131 load 0x0 0x154
0x132 jump 0x0 0x0
0x133 load 0x0 0x655b8f69
0x134 load 0x13 0x183
0x135 load 0x14 0x153
0x136 ifneq 0x1 0x0
0x137 load 0x0 0x2484a07a
0x138 ifneq 0x2 0x0
0x139 pop 0x1 0x0
0x13a pop 0x2 0x0
0x13b load 0x14 0x13d
0x13c load 0x0 0x154
0x13d jump 0x0 0x0
0x13e load 0x0 0xd9e5e7f8
0x13f load 0x13 0x183
0x140 load 0x14 0x153
0x141 ifneq 0x1 0x0
0x142 load 0x0 0x3a441532
0x143 ifneq 0x2 0x0
0x144 pop 0x1 0x0
0x145 pop 0x2 0x0
0x146 load 0x14 0x148
0x147 load 0x0 0x154
0x148 jump 0x0 0x0
0x149 load 0x0 0x91ab7e88
0x14a load 0x13 0x183
0x14b load 0x14 0x153
0x14c ifneq 0x1 0x0
0x14d load 0x0 0x69fc64bc
0x14e ifneq 0x2 0x0
0x14f pop 0x1 0x0
0x150 load 0x0 0x7d3765
0x151 ifneq 0x1 0x0
0x152 load 0x0 0x189
0x153 jump 0x0 0x0
0x154 quit 0x0 0x0
0x155 load 0x3 0x9e3779b9
0x156 load 0x4 0x95c4c
0x157 load 0x5 0x871d
0x158 load 0x6 0x1a7b7
0x159 load 0x7 0x12c7c7
0x15a load 0x8 0x0
0x15b load 0x11 0x10
0x15c load 0x12 0x20
0x15d load 0x13 0x160
0x15e load 0xa 0x0
0x15f load 0xb 0x20
0x160 load 0xc 0x1
0x161 add 0x8 0x3
0x162 copy 0x0 0x2
0x163 multiply 0x0 0x11
0x164 add 0x0 0x4
0x165 copy 0xe 0x0
0x166 copy 0x0 0x2
0x167 add 0x0 0x8
0x168 copy 0xf 0x0
0x169 copy 0x0 0x2
0x16a divide 0x0 0x12
0x16b add 0x0 0x5
0x16c copy 0x10 0x0
0x16d copy 0x0 0xe
0x16e xor 0x0 0xf
0x16f xor 0x0 0x10
0x170 add 0x1 0x0
0x171 copy 0x0 0x1
0x172 multiply 0x0 0x11
0x173 add 0x0 0x6
0x174 copy 0xe 0x0
0x175 copy 0x0 0x1
0x176 add 0x0 0x8
0x177 copy 0xf 0x0
0x178 copy 0x0 0x1
0x179 divide 0x0 0x12
0x17a add 0x0 0x7
0x17b copy 0x10 0x0
0x17c copy 0x0 0xe
0x17d xor 0x0 0xf
0x17e xor 0x0 0x10
0x17f add 0x2 0x0
0x180 sub 0xb 0xc
0x181 ifneq 0xb 0xa
0x182 jump 0x14 0x0
0x183 nop 0x0 0x0
0x184 load 0x0 0x6e
0x185 output 0x0 0x0
0x186 load 0x0 0x6f
0x187 output 0x0 0x0
0x188 jump 0x14 0x0
0x189 nop 0x0 0x0
0x18a load 0x0 0x79
0x18b output 0x0 0x0
0x18c load 0x0 0x65
0x18d output 0x0 0x0
0x18e load 0x0 0x73
0x18f output 0x0 0x0
0x190 jump 0x14 0x0
然后看到 0x155 load 0x3 0x9e3779b9 tea加密的特征值,
对里面的值一一对比即可
VNCTF{ecd63ae5-8945-4ac4-b5a5-34fc3ade81e7}





















 29万+
29万+











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








