简介
Harbor 是 VMware 公司开源的企业级 Docker Registry 项目,其目标是帮助用户迅速搭建一个企业级的 Docker Registry 服务
Harbor以 Docker 公司开源的 Registry 为基础,提供了图形管理 UI 、基于角色的访问控制(Role Based AccessControl) 、AD/LDAP 集成、以及审计日志(Auditlogging) 等企业用户需求的功能,同时还原生支持中文
- helm安装harbor仓库
#创建harbor namespace
kubectl create ns harbor
helm repo add harbor https://helm.goharbor.io
helm fetch harbor/harbor --untar
##会在你路径目录下生成一个harbor目录
[root@k8s-master helm]# ll
total 0
drwxr-xr-x. 5 root root 135 Jan 16 18:15 harbor2. 修改harbor的配置文件
###主要修改四个地方(该方法适用于nodePort方式及没有存储卷的方式)
type: nodePort
commonName: "core.harbor.domain"
externalURL: https://34.150.64.0:30003
persistence:
enabled: false
第一个是类型选择使用nodePort方式
第二个是tls的域名(可自己定义)
第三个是https方式的web访问界面
第四个是不适用存储卷
###由于配置文件的内容过多,所以简单截取修改的一部分
###这一部分主要修改第一点和第二点
expose:
# Set how to expose the service. Set the type as "ingress", "clusterIP", "nodePort" or "loadBalancer"
# and fill the information in the corresponding section
type: nodePort
tls:
# Enable TLS or not.
# Delete the "ssl-redirect" annotations in "expose.ingress.annotations" when TLS is disabled and "expose.type" is "ingress"
# Note: if the "expose.type" is "ingress" and TLS is disabled,
# the port must be included in the command when pulling/pushing images.
# Refer to https://github.com/goharbor/harbor/issues/5291 for details.
enabled: true
# The source of the tls certificate. Set as "auto", "secret"
# or "none" and fill the information in the corresponding section
# 1) auto: generate the tls certificate automatically
# 2) secret: read the tls certificate from the specified secret.
# The tls certificate can be generated manually or by cert manager
# 3) none: configure no tls certificate for the ingress. If the default
# tls certificate is configured in the ingress controller, choose this option
certSource: auto
auto:
# The common name used to generate the certificate, it's necessary
# when the type isn't "ingress"
commonName: "core.harbor.domain"
secret:
# The name of secret which contains keys named:
# "tls.crt" - the certificate
# "tls.key" - the private key
secretName: ""
# The name of secret which contains keys named:
# "tls.crt" - the certificate
# "tls.key" - the private key
# Only needed when the "expose.type" is "ingress".
notarySecretName: ""
###这一部分主要修改的是第三点
# The external URL for Harbor core service. It is used to
# 1) populate the docker/helm commands showed on portal
# 2) populate the token service URL returned to docker/notary client
#
# Format: protocol://domain[:port]. Usually:
# 1) if "expose.type" is "ingress", the "domain" should be
# the value of "expose.ingress.hosts.core"
# 2) if "expose.type" is "clusterIP", the "domain" should be
# the value of "expose.clusterIP.name"
# 3) if "expose.type" is "nodePort", the "domain" should be
# the IP address of k8s node
#
# If Harbor is deployed behind the proxy, set it as the URL of proxy
externalURL: https://34.150.64.0:30003
###这一部分主要修改第四点
# The persistence is enabled by default and a default StorageClass
# is needed in the k8s cluster to provision volumes dynamically.
# Specify another StorageClass in the "storageClass" or set "existingClaim"
# if you already have existing persistent volumes to use
#
# For storing images and charts, you can also use "azure", "gcs", "s3",
# "swift" or "oss". Set it in the "imageChartStorage" section
persistence:
enabled: false
# Setting it to "keep" to avoid removing PVCs during a helm delete
# operation. Leaving it empty will delete PVCs after the chart deleted
# (this does not apply for PVCs that are created for internal database
# and redis components, i.e. they are never deleted automatically)
resourcePolicy: "keep"
persistentVolumeClaim:
registry:
3.启动harbor
helm install harbor ./harbor -n harbor查找pod
[root@k8s-master helm]# kubectl get pod -n harbor
NAME READY STATUS RESTARTS AGE
harbor-chartmuseum-5fffc5b687-mjhmm 1/1 Running 1 15h
harbor-core-7585f98869-9lxt6 1/1 Running 1 15h
harbor-database-0 1/1 Running 1 15h
harbor-jobservice-67958b97f5-sw2lk 1/1 Running 3 15h
harbor-nginx-7dc9667c7b-rnvdz 1/1 Running 1 15h
harbor-notary-server-78d95d9d85-v297n 1/1 Running 3 15h
harbor-notary-signer-645bd5b8cf-lkhw6 1/1 Running 3 15h
harbor-portal-6489d955c5-l48zq 1/1 Running 1 15h
harbor-redis-0 1/1 Running 1 15h
harbor-registry-7b677467b4-99g77 2/2 Running 2 15h
harbor-trivy-0 1/1 Running 1 15h4.访问harbor的web页面
https://IP:30003
admin
Harbor12345
5.使用harbor证书
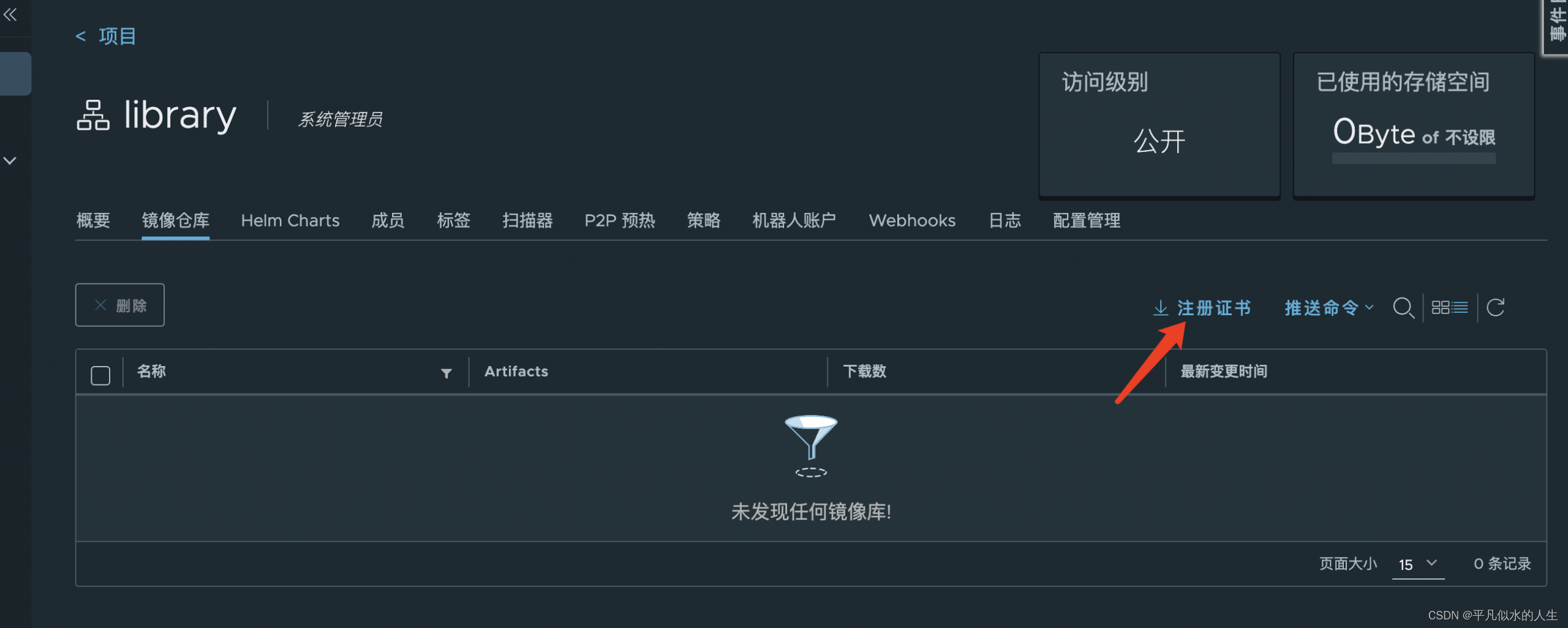
将下载的ca.crt复制到docker certs配置文件夹
mkdir -p /etc/docker/certs.d/core.harbor.domain
mv ca.crt /etc/docker/certs.d/core.harbor.domain
systemctl restart docker配置hosts(可以给每个node节点都配置,方便其他node登录harbor)
[root@k8s-master helm]# kubectl get svc -n harbor
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
harbor NodePort 10.1.215.186 <none> 80:30002/TCP,443:30003/TCP,4443:30004/TCP 15h
###将harbor的culster-ip写入到hosts解析中
vim /etc/hosts
10.1.215.186 core.harbor.domain配置不安全认证
机器登录harbor时可能会出现报错,这个时候需要配置insecure-registries,文件名称是daemon.json,路径在/etc/docker目录下
[root@k8s-master helm]# cat /etc/docker/daemon.json
{
"registry-mirrors": ["https://registry.cn-hangzhou.aliyuncs.com"],
"exec-opts": ["native.cgroupdriver=systemd"],
"insecure-registries": ["https://core.harbor.domain"]
}
这一步建议所有node节点都配置好,方便其他node节点登录harbor测试节点登录harbor仓库
[root@k8s-node01 ~]# docker login core.harbor.domain
Authenticating with existing credentials...
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
显示登录成功测试打包上传
docker tag registry.aliyuncs.com/google_containers/etcd:3.4.3-0 core.harbor.domain/library/etcd:laster
docker push core.harbor.domain/library/etcd:laster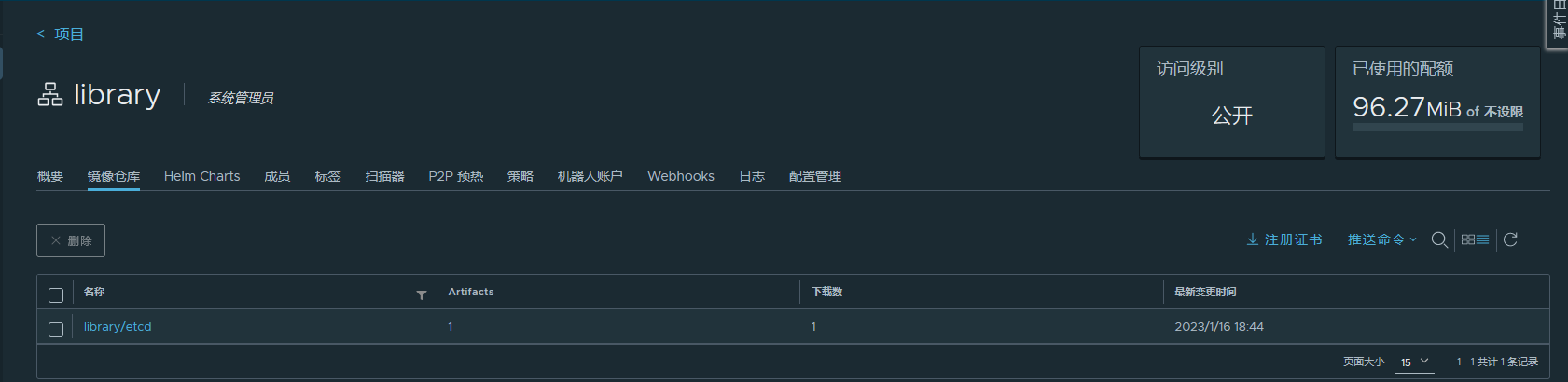
显示上传成功
测试下载
[root@k8s-node01 ~]# docker pull core.harbor.domain/library/etcd@sha256:4198ba6f82f642dfd18ecf840ee37afb9df4b596f06eef20e44d0ae1kc47fstr
sha256:4198ba6f82f642dfd18ecf840ee37afb9df4b596f06eef20e44d0ae1kc47fstr: Pulling from library/etcd
39fafc05754f: Pull complete
3736e1e115b8: Pull complete
79de61f59f2e: Pull complete
Digest: sha256:4198ba6f82f642dfd18ecf840ee37afb9df4b596f06eef20e44d0ae1kc47fstr
Status: Downloaded newer image for core.harbor.domain/library/etcd@sha256:4198ba6f82f642dfd18ecf840ee37afb9df4b596f06eef20e44d0ae1kc47fstr
显示下载成功
到这一步就表示harbor仓库的基本使用已经完成啦
参考于博主平凡似水的人生, 按照本机当时环境做了小部分修改及补充。





















 993
993











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








