elrond32
丢进exeInfoPe,32位无壳,IDA分析
主函数很简约
int __cdecl main(int a1, char **a2)
{
if ( a1 > 1 && sub_8048414(a2[1], 0) )
{
puts("Access granted"); //进入if语句可以get flag
sub_8048538((int)a2[1]);
}
else
{
puts("Access denied");
}
return 0;
}
额,简约到没得说,需要满足sub_8048414()函数为真才有机会get_flag,跟踪sub_8048414()函数
signed int __cdecl sub_8048414(_BYTE *a1, int a2)
{
signed int result; // eax
switch ( a2 )
{
case 0:
if ( *a1 == 105 )
goto LABEL_19;
result = 0;
break;
case 1:
if ( *a1 == 101 )
goto LABEL_19;
result = 0;
break;
case 3:
if ( *a1 == 110 )
goto LABEL_19;
result = 0;
break;
case 4:
if ( *a1 == 100 )
goto LABEL_19;
result = 0;
break;
case 5:
if ( *a1 == 97 )
goto LABEL_19;
result = 0;
break;
case 6:
if ( *a1 == 103 )
goto LABEL_19;
result = 0;
break;
case 7:
if ( *a1 == 115 )
goto LABEL_19;
result = 0;
break;
case 9:
if ( *a1 == 114 )
LABEL_19:
result = sub_8048414(a1 + 1, 7 * (a2 + 1) % 11);
else
result = 0;
break;
default:
result = 1;
break;
}
return result;
}
恒为真,直接进sub_8048538()函数
int __cdecl sub_8048538(int a1)
{
int v2[33]; // [esp+18h] [ebp-A0h]
int i; // [esp+9Ch] [ebp-1Ch]
qmemcpy(v2, &dword_8048760, sizeof(v2));
for ( i = 0; i <= 32; ++i )
putchar(v2[i] ^ *(char *)(a1 + i % 8));
return putchar(10);
}
异或两组数组,输出字符串,猜测是flag,需要知道sub_8048538()函数形参来源,发现和sub_8048414()是同一个数组,回到sub_8048414()函数求a1数组的值,根据函数内的递归过程跑出a1数组:
#coding:utf-8
a = [105,101,0,110,100,97,103,115,0,114,0,0]
i = 0
k = 0
while((i!=2)&(i!=8)&(i!=10)):
b = [0]*20
b[k] = a[i]
i = 7*(i+1)%11
print(b[k])
k += 1
得到数组值

另一组异或的数组v2是从内存中复制而来的
qmemcpy(v2, &dword_8048760, sizeof(v2));
进到dword_8048760 .rodata区,v2数组是int型,一个int型4个内存字节

得到v2数组
v2 = [0x0F,0x1F,0x04,0x09,0x1C,0x12,0x42,0x09,0x0C,0x44,0x0D,0x07,0x09,0x06,0x2D,0x37,0x59,0x1E,0x00,0x59,0x0F,0x08,0x1C,0x23,0x36,0x07,0x55,0x02,0x0C,0x08,0x41,0x0A,0x14]
进行异或拿到flag
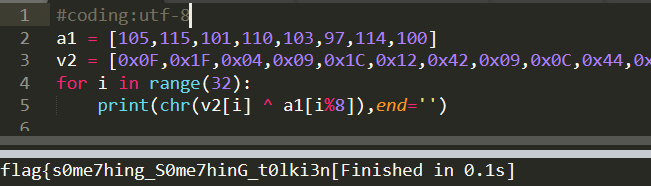
#coding:utf-8
a1 = [105,115,101,110,103,97,114,100]
v2 = [0x0F,0x1F,0x04,0x09,0x1C,0x12,0x42,0x09,0x0C,0x44,0x0D,0x07,0x09,0x06,0x2D,0x37,0x59,0x1E,0x00,0x59,0x0F,0x08,0x1C,0x23,0x36,0x07,0x55,0x02,0x0C,0x08,0x41,0x0A,0x14]
for i in range(32):
print(chr(v2[i] ^ a1[i%8]),end='')
PS:刚才写py才发现,不光是题不刷会丢技能,连语言用的少了都开始生疏
PSS: 其实这里跑a1数组用C会更好理解吧,py有一种凑出来的感觉






















 3万+
3万+











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








