1.[广东强网杯 2021 团队组]RSA and BASE
题目: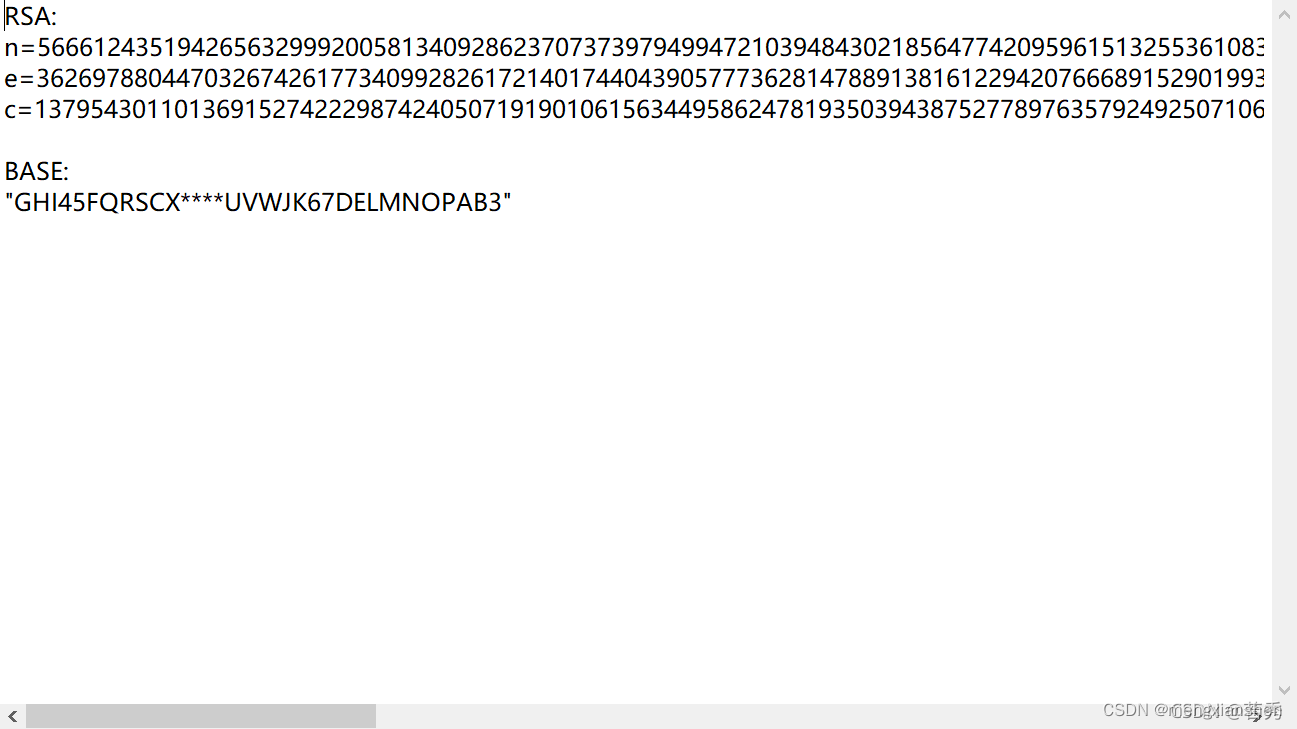
这里发现e特别大,猜测为维纳攻击,解出flag{CMDIEOH2MJFBLKHT2J7BLYZ2WUE5NYR2HNG====},观察数字为2-7,不妨猜测为base32,下面又给了一串意义不明的字母表,但字母表总数为32,因此应该为base32的变种,先得出缺少的字母,再通过排列组合得到24种情况,分别解码找到有意义的字符串,得到flag
脚本:
n=56661243519426563299920058134092862370737397949947210394843021856477420959615132553610830104961645574615005956183703191006421508461009698780382360943562001485153455401650697532951591191737164547520951628336941289873198979641173541232117518791706826699650307105202062429672725308809988269372149027026719779368169
e=36269788044703267426177340992826172140174404390577736281478891381612294207666891529019937732720246602062358244751177942289155662197410594434293004130952671354973700999803850153697545606312859272554835232089533366743867361181786472126124169787094837977468259794816050397735724313560434944684790818009385459207329
c=137954301101369152742229874240507191901061563449586247819350394387527789763579249250710679911626270895090455502283455665178389917777053863730286065809459077858674885530015624798882224173066151402222862023045940035652321621761390317038440821354117827990307003831352154618952447402389360183594248381165728338233
import gmpy2
import libnum
def continuedFra(x, y):
"""计算连分数
:param x: 分子
:param y: 分母
:return: 连分数列表
"""
cf = []
while y:
cf.append(x // y)
x, y = y, x % y
return cf
def gradualFra(cf):
"""计算传入列表最后的渐进分数
:param cf: 连分数列表
:return: 该列表最后的渐近分数
"""
numerator = 0
denominator = 1
for x in cf[::-1]:
# 这里的渐进分数分子分母要分开
numerator, denominator = denominator, x * denominator + numerator
return numerator, denominator
def solve_pq(a, b, c):
"""使用韦达定理解出pq,x^2−(p+q)∗x+pq=0
:param a:x^2的系数
:param b:x的系数
:param c:pq
:return:p,q
"""
par = gmpy2.isqrt(b * b - 4 * a * c)
return (-b + par) // (2 * a), (-b - par) // (2 * a)
def getGradualFra(cf):
"""计算列表所有的渐近分数
:param cf: 连分数列表
:return: 该列表所有的渐近分数
"""
gf = []
for i in range(1, len(cf) + 1):
gf.append(gradualFra(cf[:i]))
return gf
def wienerAttack(e, n):
"""
:param e:
:param n:
:return: 私钥d
"""
cf = continuedFra(e, n)
gf = getGradualFra(cf)
for d, k in gf:
if k == 0: continue
if (e * d - 1) % k != 0:
continue
phi = (e * d - 1) // k
p, q = solve_pq(1, n - phi + 1, n)
if p * q == n:
return d
d=wienerAttack(e, n)
m=pow(c, d, n)
print(libnum.n2s(m).decode())
import itertools
str1='TCMDIEOH2MJFBLKHT2J7BLYZ2WUE5NYR2HNG===='
str2='ABCDEFGHIJKLMNOPQRSTUVWXYZ234567'
str3='GHI45FQRSCX****UVWJK67DELMNOPAB3'
missstr=''
for i in str2:
if i not in str3:
missstr+=i
missstrs=[]
for i in itertools.permutations(missstr, 4):
missstrs.append(''.join(i))
print(missstrs)
from base64 import b32decode
for g in missstrs:
str4='GHI45FQRSCX'+g+'UVWJK67DELMNOPAB3'
flag=str(b32decode(str1.translate(str.maketrans(str4,str2))))
print(flag)
2. [安洵杯 2020]密码学?爆破就行了
题目:
import hashlib
from secret import SECRET
from broken_flag import BROKEN_FLAG
flag = 'd0g3{' + hashlib.md5(SECRET).hexdigest() + '}'
broken_flag = 'd0g3{71b2b5616**2a4639**7d979**de964c}'
assert flag[:14] == broken_flag[:14]
assert flag[16:22] == broken_flag[16:22]
assert flag[24:29] == broken_flag[24:29]
ciphier = hashlib.sha256(flag).hexdigest()
print(ciphier)
'''
ciphier = '0596d989a2938e16bcc5d6f89ce709ad9f64d36316ab80408cb6b89b3d7f064a'
题解:没事那么好说的,sha256直接爆破
脚本:
import hashlib
broken_flag= '71b2b5616**2a4639**7d979**de964c'
str1="d0g3{71b2b5616"
str2="2a4639"
str3="7d979"
str4="de964c}"
cipher='0596d989a2938e16bcc5d6f89ce709ad9f64d36316ab80408cb6b89b3d7f064a'
def getdigest(string):
return hashlib.sha256((string.encode("utf-8"))).hexdigest()
alphabet="1234567890abcdef"
for a in alphabet:
for b in alphabet:
for c in alphabet:
for d in alphabet:
for e in alphabet:
for f in alphabet:
string=str1+a+b+str2+c+d+str3+e+f+str4
if getdigest(string)==cipher:
print (string)
得到flag





















 947
947

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








