KEY FINDINGS
- The responsibility for the MGM Resorts cyberattack has been claimed ALPHV ransomware group.
- The attackers apparently gained access to the company’s systems through a social engineering attack.
- The attack affected some of the company’s systems, including its website, reservation systems, and hotel electronic key card systems.
- MGM Resorts is working to restore its systems and improve its cybersecurity.
- The FBI is investigating the incident.
Las Vegas-based MGM Resorts International, a global entertainment and hospitality giant, has been hit by a cyber attack. The attack, which was first reported on September 11, 2023, affected some of the company’s systems, including its website, reservation systems, and hotel electronic key card systems.
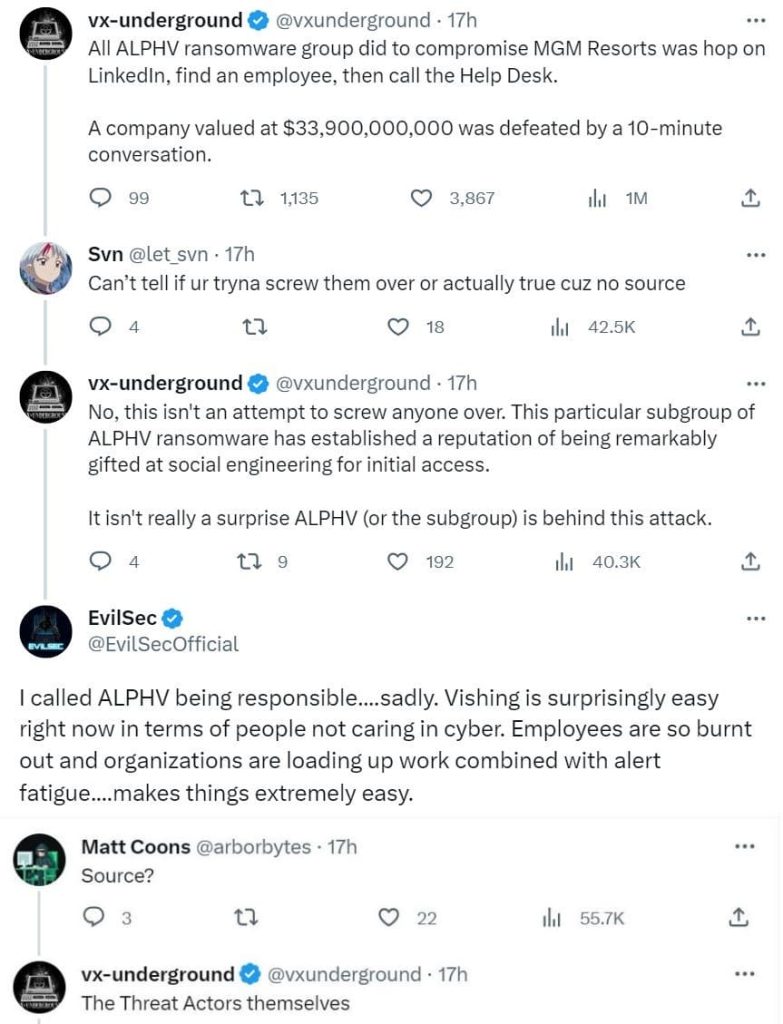
The FBI has been notified of the incident and is investigating. The agency has characterized the event as ongoing. However, according to a tweet by the malware repository vx-underground, the culprits behind the attack are the ALPHV ransomware group. The ransomware gang was able to breach the company through a social engineering attack.
“All ALPHV ransomware group did to compromise MGM Resorts was hop on LinkedIn, find an employee, then call the Help Desk,” vx-underground posted on Twitter. “A company valued at $33,900,000,000 was defeated by a 10-minute conversation.”
The social engineering attack is a common tactic used by ransomware gangs and cyber criminals. In this type of attack, the attackers trick the victim into clicking on a malicious link or opening a malicious attachment either through phishing or Vishing or Smishing (SMS Phishing). Once the victim does this, the attackers gain access to the victim’s computer system and can then install the ransomware.
In this case, according to researchers, the technique that was used to target MGM Resorts was vishing. Vishing is a type of social engineering attack that uses voice calls to trick victims into giving up their personal information or clicking on a malicious link. The name is a portmanteau of “voice” and “phishing.”
The ALPHV ransomware group is a relatively new ransomware group, but it has quickly become one of the most active ransomware groups. The group has been responsible for a number of high-profile attacks, including attacks on the Costa Rican government, the Norwegian Ministry of Health and Care Services and reportedly Reddit.
Nevertheless, this is not the first time that MGM Resorts has suffered a cyber attack. In fact, in February 2020, private information of over 10.7 million MGM Hotel guests was being sold on Dark Web. In July 2020, the personal details of more than 142 million MGM customers were sold on a dark web marketplace.
In response to the news, Ryan McConechy, CTO of Barrier Networks told Hackread.com, “In response to this incident, it looks like MGM decided to take all their systems offline, which is a routine move when organisations run such large and complex networks.”
“Until MGM provides more information on the breach, it’s not clear the exact reason why they decided to take this action, but it is very costly move.” McConechy added. “For every minute the gaming floor was down, MGM was losing money. Likewise, with reservations and their websites still being down, the company continues to suffer massive financial losses.”
“Understandably, this may be to prevent active attackers pivoting or malware spreading, but when organisations segment their networks effectively, this scale of downtime can usually be avoided,” McConechy added.
“Organisations must work to segment their assets, so no attacker can ever reach everything at once. This stops the risks of malware spreading and means when incidents do occur, they can be more easily identified and contained without impacting other network areas, which saves significant financial losses caused by downtime,” he advised.
The MGM Resorts cyberattack is a reminder of the importance of cybersecurity for all businesses. Businesses should have strong cybersecurity measures in place to protect their data and systems from attack. These measures should include:
- Having a backup plan in case of a cyberattack.
- Training employees on cybersecurity best practices.
- Using strong passwords and changing them regularly.
- Keeping software up to date to avoid attacks through 0day flaws
- Using a firewall to protect the network from unauthorized access.
In the wake of the attack, MGM Resorts has said that it is working to restore its systems and that it is taking steps to improve its cybersecurity. The company has also said that it is not aware of any customer data being compromised in the attack.






















 5271
5271











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








