DNS
DNS
英文全称是Domain Name System 域名名称系统
— 它的作用是进行域名解析的,把一个FQDN解析成IP地址,因为IP地址不易记,所以大多数的网页地址都是使用的域名,而DNS的作用就是用来解析这些域名的IP的。
DNS的操作流程如下
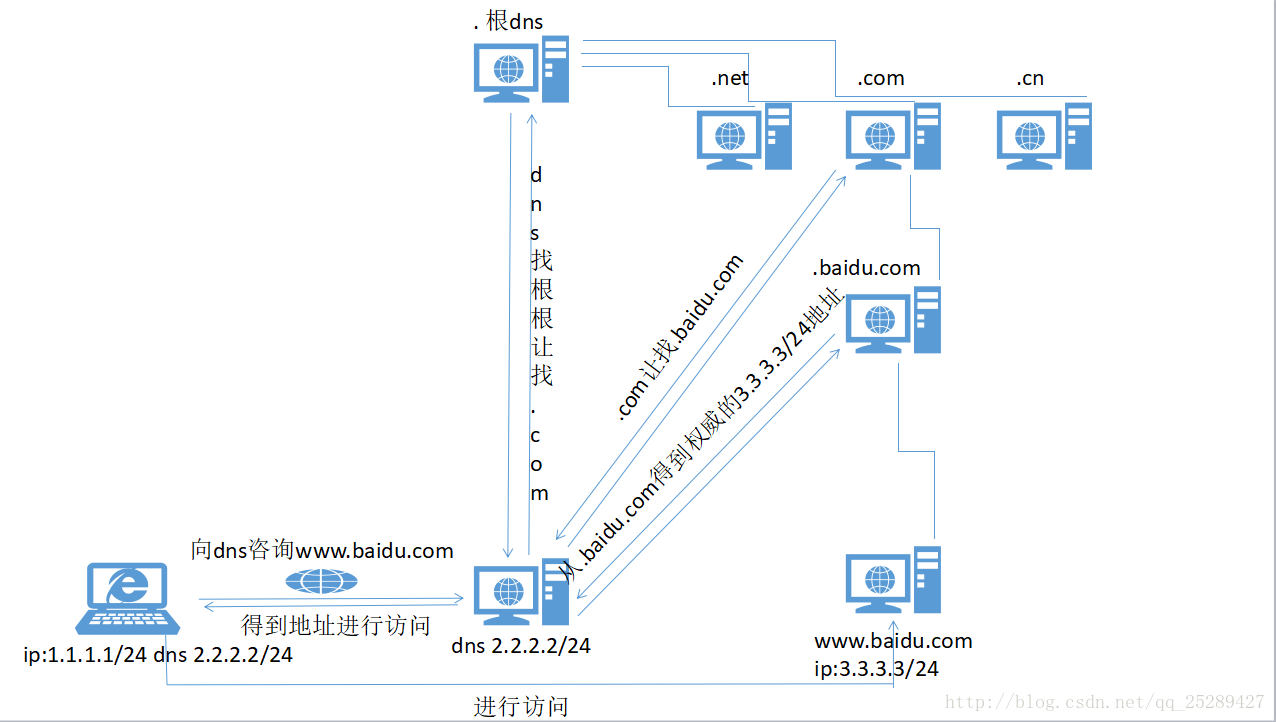
—当我们主机向dns发送请求时,如果dns没有缓存是直接去找根的,接着根会找自己的下级子域,然后子域继续找下级的子域进行层层迭代.
用户向dns服务器进行查询,我们称:递归查询
dns向根进行询问查询我们称:迭代查询
根服务器全球范围内一共有13个,主要分布在一些发达国家的手中,国内没有.
DNS的应用层端口: UDP:53 TCP:53
DNS的域名分层:根域--> 一级域名 --> 二级域名 --> 三级域名 ...等等,最多只能为127级域名
解析的类型有两种:
正向解析和反向解析即 FQDN --> IP 和 IP --> FQDN
正向和反向解析都有个解析库,正向区域库和反向区域库
区域解析库由众多RR(Resource Record)组成
解析库记录的类型:A AAAA PTR SOA NS CNAME MX
SOA :起始授权记录;此记录必须位于解析库的第一条记录,而且一个库只能只有一条此记录。
A :Internet Address 网络地址 即是 FQDN --> IP
AAAA : ipv6的解析 FQDN --> IP
PTR : 反向解析 IP --> FQDN
NS : 专用指向DNS服务器
CNAME: 用于记录域名的别名,如 www CNAME qqq
MX : 邮件交换器
DNS-bind
bind 是 Linux系统的dns包名,这里我们要讲的就是bind
1. 安装
配好yum源后用yum安装
yum -y install bind
2.包内文件
[root@CentOS6 ~]#rpm -ql bind
/etc/named <-- dns的配置文件目录
/etc/named.conf <-- dns的配置文件
/etc/named.rfc1912.zones <-- dns的zones配置文件,在这里定义区域名
/etc/rc.d/init.d/named <-- dns的服务名称,
/var/log/named.log <-- dns的日志文件
/var/named <-- dns运行目录
/var/named/named.ca <-- dns定义的13个根服务器文件
/var/named/named.empty <-- dns定义的模块文件
/var/named/slaves <-- 从dns服务器的目录
3.文件作用
– /etc/named.conf 这是dns的全局配置文件
[root@CentOS6 ~]#cat /etc/named.conf // // named.conf // // Provided by Red Hat bind package to configure the ISC BIND named(8) DNS // server as a caching only nameserver (as a localhost DNS resolver only). // // See /usr/share/doc/bind*/sample/ for example named configuration files. // options { listen-on port 53 { 192.168.3.2;127.0.0.1; }; <-- 这里是指向监听哪些IP的端口 // listen-on-v6 port 53 { ::1; }; <-- 这里监听IPV6的,注释掉了。(// 是注释) directory "/var/named"; dump-file "/var/named/data/cache_dump.db"; statistics-file "/var/named/data/named_stats.txt"; memstatistics-file "/var/named/data/named_mem_stats.txt"; // allow-query { any; }; <-- 这里是允许谁进行访问,any是所有 recursion yes; <-- 这里是定义开启和关闭递归查询的 // dnssec-enable yes; <-- 这两项是dns安全策略的 // dnssec-validation yes; /* Path to ISC DLV key */ // bindkeys-file "/etc/named.iscdlv.key"; // managed-keys-directory "/var/named/dynamic"; }; logging { channel default_debug { file "data/named.run"; severity dynamic; }; }; zone "." IN { <-- 这里定义的根的zone信息及文件 type hint; file "named.ca"; }; include "/etc/named.rfc1912.zones"; <-- 这里调用了zones的文件,(建议zone信息都放致这个文件) include "/etc/named.root.key";/etc/named.rfc1912.zones
[root@CentOS6 ~]#cat /etc/named.rfc1912.zones // named.rfc1912.zones: // // Provided by Red Hat caching-nameserver package // // ISC BIND named zone configuration for zones recommended by // RFC 1912 section 4.1 : localhost TLDs and address zones // and http://www.ietf.org/internet-drafts/draft-ietf-dnsop-default-local-zones-02.txt // (c)2007 R W Franks // // See /usr/share/doc/bind*/sample/ for example named configuration files. // zone "localhost.localdomain" IN { type master; file "named.localhost"; allow-update { none; }; }; zone "localhost" IN { type master; file "named.localhost"; allow-update { none; }; }; zone "1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.ip6.arpa" IN { type master; file "named.loopback"; allow-update { none; }; }; zone "1.0.0.127.in-addr.arpa" IN { type master; file "named.loopback"; allow-update { none; }; }; zone "0.in-addr.arpa" IN { type master; file "named.empty"; allow-update { none; }; }; zone "benben.com" IN { <-- 这里我们自己定义了一个benben.com的zone type master; <-- 他它类型是主 file "benben.com.zone;" <-- 文件指向的路径是/var/named/benben.com.zone
3./var/named/named.empty
[root@CentOS6 named]#cat named.empty <-- 这是范例文件
$TTL 3H <-- TTL是全局继续的
@ IN SOA @ rname.invalid. ( <-- @ 是引用当前区域的名称
0 ; serial <-- 版本号对比 有要求的长度
1D ; refresh <--从主服务DNS进行同步更新时间
1H ; retry <--重载与主服务器DNS同步数据库信息
1W ; expire <--过期时间 (从DNS服务器)
3H ) ; minimum <--否定结果的缓存有效期
NS @ <-- 此处的NS记录得加上从DNS记录
A 127.0.0.1 <-- FQDN - IP 正向解析
AAAA ::1 <-- FQDN - IPV6 正向解析
语法: name [TTL] IN rr_type value
示例 1
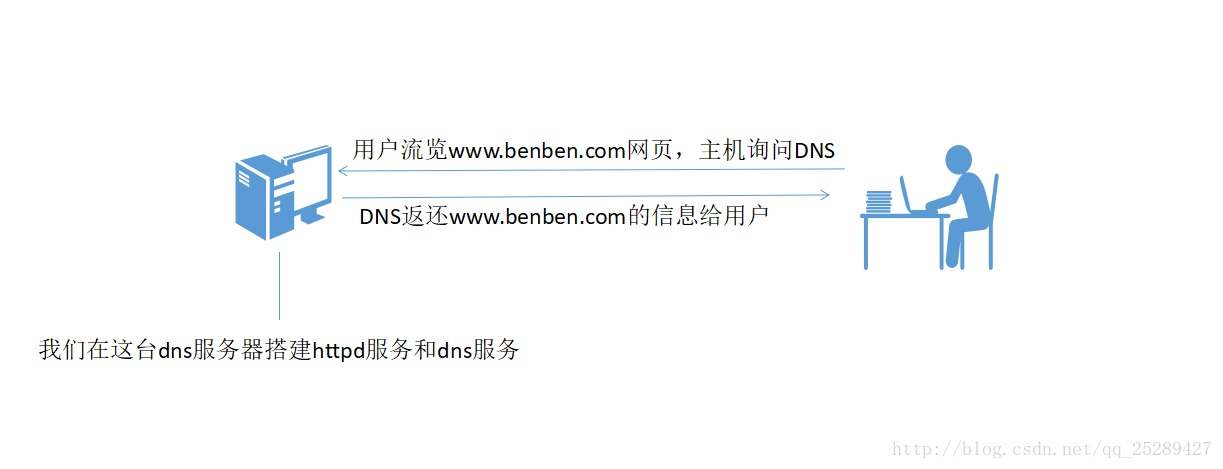
(1). 首选修改dns的配置文件,放开端口,在修改前事先做好备份 cp /etc/named.conf{,.bak}
10 options {
11 listen-on port 53 { 192.168.3.2;127.0.0.1; }; --> 将IP的监听端口打开默认只打开了本地127
12 // listen-on-v6 port 53 { ::1; };
13 directory "/var/named";
14 dump-file "/var/named/data/cache_dump.db";
15 statistics-file "/var/named/data/named_stats.txt";
16 memstatistics-file "/var/named/data/named_mem_stats.txt";
17 allow-query { any; }; -->允许所有人访问
18 recursion yes;
(2). 编辑vim /etc/named.rfc1912.zones
在这里我们添加一条zone记录
42 zone "benben.com" IN {
43 type master;
44 file "benben.com.zone;"
45 }
(3). 在/var/named/目录下创建benben.com.zone的区域文件,并编辑
在创建文件后把文件的属主于属组改成对应的named chown named:named benben.com.zone
-rw-r----- 1 named named 196 Sep 1 21:40 benben.com.zone
[root@CentOS6 named]#vim benben.com.zone
1 $TTL 1D
2 @ IN SOA dns1.magedu.com. root.mail.com (
3 0 ; serial
4 1D ; refresh
5 1H ; retry
6 1W ; expire
7 3H ) ; minimum
8 NS dns1
9 dns1 A 192.168.3.2
10www CNAME dns1
(4)测试
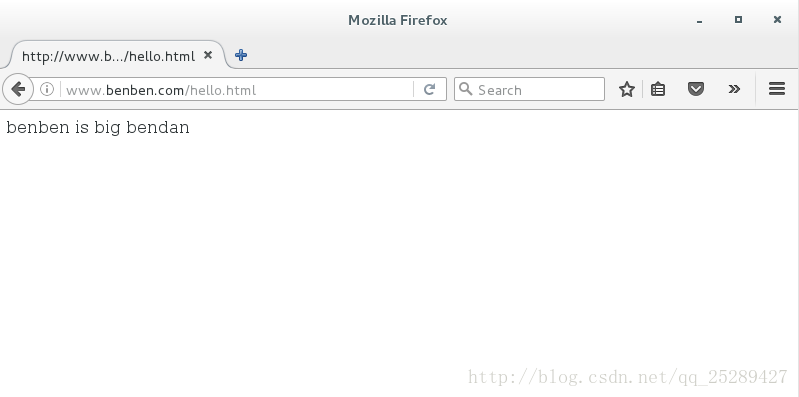
我们把ip属性配置好自搭的dns指向,然后进行访问,也可以使用dig命令
[root@CentOS6 /]#cat /var/www/html/hello.html
benben is big bendan
示例 2
继续使用上面的例子来制作反向解析和上述例子操作没多大区别
(1)创建反向解析的zone记录 /etc/named.rfc1912.zones
zone "3.168.192.in-addr.arpa" IN {
type master;
file "192.168.3.zone";
};
( 2 ) 创建192.168.3.zone的文档数据库 /var/named/192.168.3.zone
[root@CentOS6 ~]#cat /var/named/192.168.3.zone
$TTL 1D
@ IN SOA dns1.benben.com. root.mail.com. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS dns1
dns1 A 192.168.3.2
PTR dns1.benben.com.
www CNAME dns1
( 3 ) 测试
[root@localhost ~]#nslookup
> www.benben.com
Server: 192.168.3.2
Address: 192.168.3.2#53
www.benben.com canonical name = dns1.benben.com.
Name: dns1.benben.com
Address: 192.168.3.2
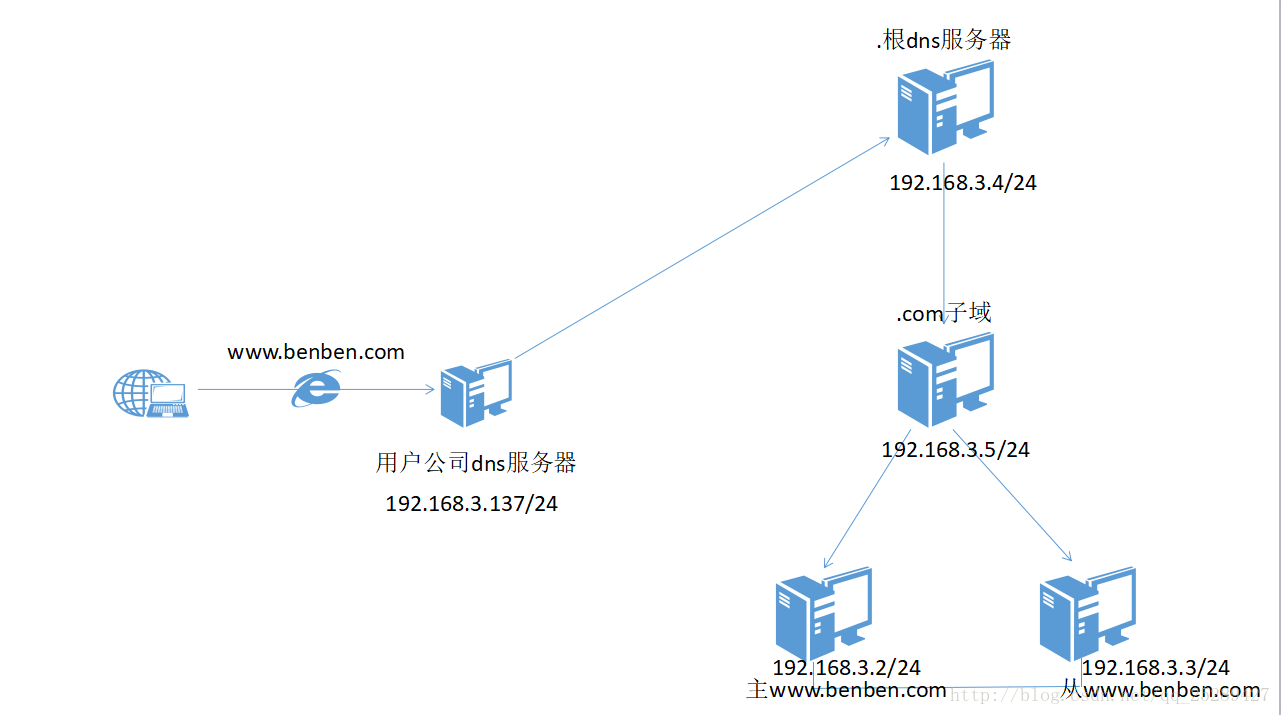
示例 3
主www.benben.com 192.168.3.2配置
/etc/named.conf
options {
listen-on port 53 { 192.168.3.3;127.0.0.1; };
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
allow-query { any; };
/etc/named.rfc1912.zones
zone "benben.com" IN {
type master;
file "benben.com.zone";
allow-update { none;};
};
zone "3.168.192.in-addr.arpa" IN {
type master;
file "192.168.3.zone";
};
/var/named/benben.com.zone
$TTL 1D
@ IN SOA dns1.benben.com. root.mail.com. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS dns1
NS dns2
dns1 A 192.168.3.2
dns2 A 192.168.3.3
www CNAME dns1
从 www.benben.com 192.168.3.3 配置
/etc/named.conf
options {
listen-on port 53 { 192.168.3.3;127.0.0.1; };
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
allow-query { any; };
/etc/named.rfc1912.zones
zone "benben.com" IN {
type slave;
masters {192.168.3.2;};
file "slaves/benben.com.zone";
};
zone "3.168.192.in-addr.arpa" IN {
type slave;
masters {192.168.3.2;};
file "slaves/192.168.3.zone";
};
/var/named/slave/benben.com.zone
因为是从DNS所以这个配置文件是继承192.168.3.2的,也因为是CentOS7 所以这个文件内容格式不易读,就不贴出来了.com子域 192.168.3.5配置
/etc/named.rfc1912.zones
zone "com" IN {
type master;
file "com.zone";
};
/var/named/com.zone
$TTL 1D
@ IN SOA dns1 rname.invalid. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS dns1
benben.com. NS dns2
benben.com. NS dns3
dns1 A 192.168.3.5
dns2 A 192.168.3.2
dns3 A 192.168.3.3
benben.com. A 192.168.3.3
benben.com. A 192.168.3.2根的192.168.3.4配置
/etc/named.conf
options {
listen-on port 53 { 192.168.3.4;127.0.0.1; };
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
allow-query { any; };
recursion yes;
dnssec-enable no;
dnssec-validation no;
/* Path to ISC DLV key */
bindkeys-file "/etc/named.iscdlv.key";
managed-keys-directory "/var/named/dynamic";
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";
/etc/named.rfc1912.zones
zone "." IN {
type master;
file "root.zone";
};
/var/named/root.zone
$TTL 3H
@ IN SOA dns1 rname.invalid. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS dns1
com NS dns2
dns1 A 192.168.3.4
dns2 A 192.168.3.5
[root@localhost ~]# cat /var/named/named.ca
; This file holds the information on root name servers needed to
; initialize cache of Internet domain name servers
; (e.g. reference this file in the "cache . <file>"
; configuration file of BIND domain name servers).
;
; This file is made available by InterNIC
; under anonymous FTP as
; file /domain/named.cache
; on server FTP.INTERNIC.NET
; -OR- RS.INTERNIC.NET
;
; last update: December 01, 2015
; related version of root zone: 2015120100
;
; formerly NS.INTERNIC.NET
;
. 3600000 NS A.ROOT-SERVERS.NET.
A.ROOT-SERVERS.NET. 3600000 A 198.41.0.4
A.ROOT-SERVERS.NET. 3600000 AAAA 2001:503:ba3e::2:30
;
; FORMERLY NS1.ISI.EDU
;
. 3600000 NS B.ROOT-SERVERS.NET.
B.ROOT-SERVERS.NET. 3600000 A 192.228.79.201
B.ROOT-SERVERS.NET. 3600000 AAAA 2001:500:84::b
;
; FORMERLY C.PSI.NET
;
. 3600000 NS C.ROOT-SERVERS.NET.
C.ROOT-SERVERS.NET. 3600000 A 192.33.4.12
C.ROOT-SERVERS.NET. 3600000 AAAA 2001:500:2::c
;
; FORMERLY TERP.UMD.EDU
;
. 3600000 NS D.ROOT-SERVERS.NET.
D.ROOT-SERVERS.NET. 3600000 A 199.7.91.13
D.ROOT-SERVERS.NET. 3600000 AAAA 2001:500:2d::d
;
; FORMERLY NS.NASA.GOV
;
. 3600000 NS E.ROOT-SERVERS.NET.
E.ROOT-SERVERS.NET. 3600000 A 192.203.230.10
;
; FORMERLY NS.ISC.ORG
;
. 3600000 NS F.ROOT-SERVERS.NET.
F.ROOT-SERVERS.NET. 3600000 A 192.5.5.241
F.ROOT-SERVERS.NET. 3600000 AAAA 2001:500:2f::f
;
; FORMERLY NS.NIC.DDN.MIL
;
. 3600000 NS G.ROOT-SERVERS.NET.
G.ROOT-SERVERS.NET. 3600000 A 192.112.36.4
;
; FORMERLY AOS.ARL.ARMY.MIL
;
. 3600000 NS H.ROOT-SERVERS.NET.
H.ROOT-SERVERS.NET. 3600000 A 198.97.190.53
H.ROOT-SERVERS.NET. 3600000 AAAA 2001:500:1::53
;
; FORMERLY NIC.NORDU.NET
;
. 3600000 NS I.ROOT-SERVERS.NET.
I.ROOT-SERVERS.NET. 3600000 A 192.36.148.17
I.ROOT-SERVERS.NET. 3600000 AAAA 2001:7fe::53
;
; OPERATED BY VERISIGN, INC.
;
. 3600000 NS J.ROOT-SERVERS.NET.
J.ROOT-SERVERS.NET. 3600000 A 192.58.128.30
J.ROOT-SERVERS.NET. 3600000 AAAA 2001:503:c27::2:30
;
; OPERATED BY RIPE NCC
;
. 3600000 NS K.ROOT-SERVERS.NET.
K.ROOT-SERVERS.NET. 3600000 A 193.0.14.129
K.ROOT-SERVERS.NET. 3600000 AAAA 2001:7fd::1
;
; OPERATED BY ICANN
;
. 3600000 NS L.ROOT-SERVERS.NET.
L.ROOT-SERVERS.NET. 3600000 A 199.7.83.42
L.ROOT-SERVERS.NET. 3600000 AAAA 2001:500:3::42
;
; OPERATED BY WIDE
;
. 3600000 NS M.ROOT-SERVERS.NET.
M.ROOT-SERVERS.NET. 3600000 A 202.12.27.33
M.ROOT-SERVERS.NET. 3600000 AAAA 2001:dc3::35
; End of file用户DNS 192.168.3.137 配置
/etc/named.conf
options {
listen-on port 53 { 192.168.3.137;127.0.0.1; };
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
allow-query { any; };
/*
- If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.
- If you are building a RECURSIVE (caching) DNS server, you need to enable
recursion.
- If your recursive DNS server has a public IP address, you MUST enable access
control to limit queries to your legitimate users. Failing to do so will
cause your server to become part of large scale DNS amplification
attacks. Implementing BCP38 within your network would greatly
reduce such attack surface
*/
recursion yes;
dnssec-enable no;
dnssec-validation no;
/* Path to ISC DLV key */
bindkeys-file "/etc/named.iscdlv.key";
managed-keys-directory "/var/named/dynamic";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
zone "." IN {
type hint;
file "named.ca";
};
include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";
/var/named/named.ca
; This file holds the information on root name servers needed to
; initialize cache of Internet domain name servers
; (e.g. reference this file in the "cache . <file>"
; configuration file of BIND domain name servers).
;
; This file is made available by InterNIC
; under anonymous FTP as
; file /domain/named.cache
; on server FTP.INTERNIC.NET
; -OR- RS.INTERNIC.NET
;
; last update: December 01, 2015
; related version of root zone: 2015120100
;
; formerly NS.INTERNIC.NET
;
. 3600000 NS A.ROOT-SERVERS.NET.
A.ROOT-SERVERS.NET. 3600000 A 192.168.3.4
除开根,其它所有配置的named.ca里的内容更变为:
. 3600000 NS A.ROOT-SERVERS.NET.
A.ROOT-SERVERS.NET. 3600000 A 192.168.3.4
测试: 使用 192.168.3.137 dig下 www.benben.com
[root@localhost ~]# dig www.benben.com @192.168.3.137
; <<>> DiG 9.9.4-RedHat-9.9.4-51.el7 <<>> www.benben.com @192.168.3.137
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 26393
;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 2, ADDITIONAL: 2
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;www.benben.com. IN A
;; ANSWER SECTION:
www.benben.com. 85402 IN CNAME dns1.benben.com.
dns1.benben.com. 85402 IN A 192.168.3.2
;; AUTHORITY SECTION:
benben.com. 85402 IN NS dns2.benben.com.
benben.com. 85402 IN NS dns1.benben.com.
;; ADDITIONAL SECTION:
dns2.benben.com. 85402 IN A 192.168.3.3
;; Query time: 1 msec
;; SERVER: 192.168.3.137#53(192.168.3.137)
;; WHEN: Fri Sep 22 20:16:11 CST 2017
;; MSG SIZE rcvd: 127




















 7298
7298











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








