1.State-space
components of state-space:
state variableds state state space operator set startd state goal state state space search graph(tree)

There are two kinds of state space representations, one is graph, another is tree.

2.Generate-and-test paradigm
A procedure for the generate-and-test paradigm would look like the following:
{While no solution is found and more candidates remain
[Generate a possible solution
Test if all problem constraints are satisfied]
End While}
If a solution has been found, announce success and output it.
Else announce no solution found.

Two method of the generate-and-test paradigm:
a.Backtracking
Exhaustive enumeration is a search methodology that looks everywhere for a solution to a problem. A partial solution is developed further even after it has been discovered that this set of steps cannot possibly lead to a successful problem solution.
Backtracking is an improvement to exhaustive enumeration.

b.The Greedy Algorithm
The greedy algorithm is another classic search method, which also operates by first dividing a problem into stages. A greedy algorithm always contains an objective function that must be optimized (i.e., either maximized or minimized).
3.Blind Search Algorithm
a.Depth First Search

b.Breadth First Search 
c.dfs with iterative deepening
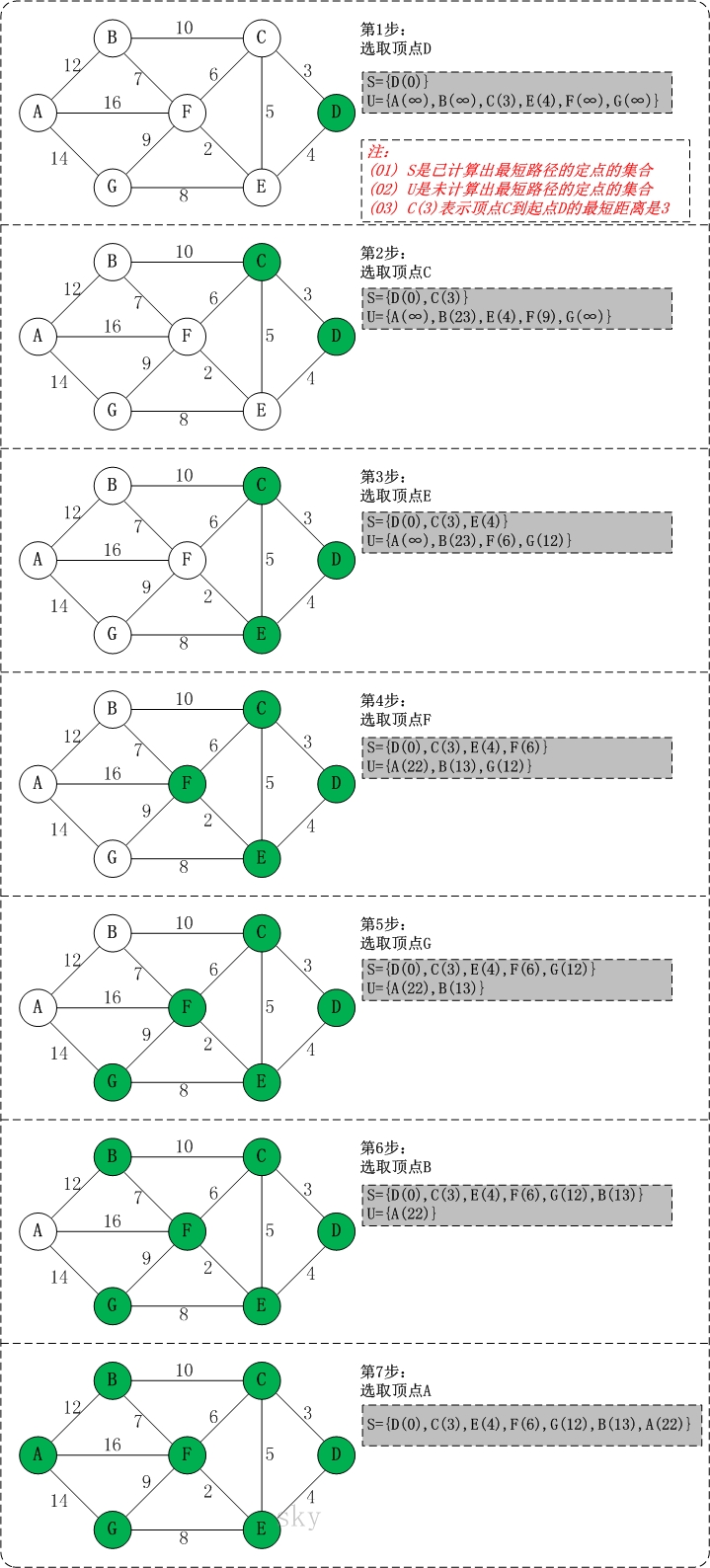
d. Dijkstra's Algorithm
4.Heuristics
Heuristic searches incorporate the use of domain-specific knowledge in the process of choosing which node to visit next in the search process. Search methods that include the use of domain knowledge in the form of heuristics are described as “weak” search methods. The knowledge used is “weak” in that it usually helps but does not always help to find a solution.
5.Admissible
A heuristic that never overestimates the cost to the goal is referred to as an admissible heuristic. Not all heuristics are necessarily admissible.
6.Hill Climbing
https://www.geeksforgeeks.org/introduction-hill-climbing-artificial-intelligence/

three circumstances in hill climbing:
a.The Foothills Problem

b.The Plateau Problem

c.The Ridge Problem

7.The best-first search
https://www.geeksforgeeks.org/best-first-search-informed-search/
The best-first search is described as a general search where the minimum cost nodes are expanded first. The best- first search is not guaranteed to find the shortest solution path.
The best-first search attempts to minimize the cost of finding a solution. It is a combination of the depth first-search and breadth-first search with heuristics. Two lists are maintained in the implementation of the best-first algorithm: OPEN and CLOSED. OPEN contains those nodes that have been evaluated by the heuristic function but have not been expanded into successors yet. CLOSED contains those nodes that have already been visited.

8.The beam search
In beam search, investigation spreads through the search tree level by level, but only the best W nodes are expanded. W is called the beam width.
9. Evaluation function
At this point in the search, one might wish to calculate f(n)—the exact cost of an S to G path that passes through n; f(n) has two components: g(n), the actual distance traveled from S to this node n, and h*(n), the remaining distance to G via a shortest path. In other words, f(n) = g(n) + h*(n).If this estimate is to be useful, then it must be an underestimate, or, h(n) ≤ h*(n) for all
nodes n. When this is so, h(n) is said to be an admissible heuristic.
10.Branch and bound
Branch and bound techniques are used to find the most optimal solution. Each solution path has a cost associated with it. Branch and bound techniques keep track of the solution and its cost and continue searching for a better solution further on. The entire search space is usually searched. Each path and hence each arc (rather than the node) has a cost associated with it. The assumption made is that the cost increases with path length. Paths that are estimated to have a higher cost than paths already found are not pursued. These techniques are used in conjunction with depth first and breadth first searches as well as iterative deepening.
11.The A* Search
https://www.geeksforgeeks.org/a-search-algorithm/
Search algorithms that are guaranteed to find the shortest path are called admissible algorithms. The breadth first search is an example of an admissible algorithm. The evaluation function we have considered with the best first algorithm is f(n) = g(n) + h(n), where g(n) - is an estimate of the cost of the distance from the start node to some node n, e.g. the depth at which the state is found in the graph h(n) - is the heuristic estimate of the distance from n to a goal.
An evaluation function used by admissible algorithms is: f*(n) = g*(n) + h*(n) where g*(n) - estimates the shortest path from the start node to the node n. h*(n) - estimates the actual cost from the start node to the goal node that passes through n.
f* does not exist in practice and we try to estimate f as closely as possible to f*. g(n) is a reasonable estimate of g*(n). Usually g(n) >= g*(n). It is not usually possible to compute h*(n). Instead we try to find a heuristic h(n) which is bounded from above by the actual cost of the shortest path to the goal, i.e. h(n) <= h*(n). The best first search used with f(n) is called the A algorithm. If h(n) <= h*(n) in the A algorithm then the A algorithm is called the A* algorithm.
There are generally three approximation heuristics to calculate h:
1) Manhattan Distance
h = abs (current_cell.x – goal.x) + abs (current_cell.y – goal.y)
2) Diagonal Distance
h = max { abs(current_cell.x – goal.x),abs(current_cell.y – goal.y) } 3) Euclidean Distance
h = sqrt ( (current_cell.x – goal.x)2 + (current_cell.y – goal.y)2 ) The example of A* algorithm:






Three basi factors effecting the efficiency of A*:
1.The cost of the path found
2.The number of nodes expanded in finding the path
3.The computational effort required to compute h.
The differences between best first search and A* search:
Best-first search algorithm visits next state based on heuristics function f(n) = h with lowest heuristic value (often called greedy). It doesn't consider cost of the path to that particular state. All it cares about is that which next state from the current state has lowest heuristics.
A* search algorithm visits next state based on heristics f(n) = h + g where h component is same heuristics applied as in Best-first search but g component is path from the initial state to the particular state. Therefore it doesn't chooses next state only with lowest heuristics value but one that gives lowest value when considering it's heuristics and cost of getting to that state.
12.Constraint Satisfaction Search
13.AND/OR Trees

14.The Bidirectional Search
The idea of bidirectional search is to find a solution path by searching forward for a goal state and searching backward
from a known goal state toward a start state.
15.Game tree
In a game tree, nodes represent game states and branches represent moves between these states.

16.Minimax evaluation
https://www.geeksforgeeks.org/minimax-algorithm-in-game-theory-set-1-introduction/
Minimax evaluation is an algorithm used to evaluate game trees. It examines the state of the game and returns a value indicating whether the state is a win, loss, or draw for the current player.
The value of the Max node is the maximum of the values in either of its immediate successor nodes;The Min player always
makes the move with the minimum value attached to it, because the Min player is trying to minimize the value that accrues to Max.


17.Alpha-beta pruning
http://web.cs.ucla.edu/~rosen/161/notes/alphabeta.html
It will return the same values as minimax alone, but by examining only about one-half as many nodes in a game tree as
minimax. This allows a deeper inspection of a game tree, resulting in more trustworthy and accurate evaluations.
The basic tenet of alpha-beta pruning is that after a move has been discovered to be bad, it is abandoned, and additional resources are not expended to discover how truly bad it is.
18.Progressive deepening
For example, you can explore the game tree to a depth of one, and then return the best move found. If more time remains, you proceed to depth two. If still more time remains, you go down to depth three, and so on. Because the number of leaf nodes in a search tree grows exponentially with respect to the branching factor of the tree, re-inspecting the tree from scratch but exploring one level deeper at each iteration does not involve much overhead.
19.Games of chance
Games of chance are called nondeterministic games because you cannot predict the next state of the game based upon
its present state.
To analyze nondeterministic games, you use the expectiminimax algorithm. E(X) = Σ xi * P (xi)

20.Prisoner’s Dilemma

21.Propositional logic
a.Basics
A statement (or logical expression) is a sentence that can be categorized with a truth-value of true or false.
Theorems in the propositional logic can be used to prove additional theorems through a process known as deduction.
We have seen that an expression whose value is always true is referred to as a tautology. An expression whose value is always false is called a contradiction.Finally, an expression in the propositional logic is said to be satisfiable when there is at least one truth assignment for the variables that makes the expression true.







b.Arguments

c.Proving Arguments in the Propositional Logic Valid – A Second Approach
A second approach to proving validity of propositional logic arguments is known as resolution. This strategy is also referred to as resolution-refutation.This approach assumes that the premises are true and that the conclusion is false. If you can thereby arrive at a contradiction, then the original conclusion must follow logically from the premises and hence the original argument is valid. Resolution proofs require that the premises and conclusion of the argument be in a special form referred to as clause form.


22.Predicate logic
A predicate logic expression consists of a predicate name followed by a list (possibly empty) of arguments.
As with the propositional logic, predicate logic expressions can be combined with the operators: ~ , ˄ , ˅, ⇒, ⇔. Furthermore, two quantifiers can be applied to predicate variables. The first (∃) is an existential quantifier. ∃x is
read as: “there exists an x” this means that one or more values of x are guaranteed to exist. The second quantifier, (∀) is a universal quantifier. ∀x reads as: “for all x”, this means that the predicate expression is stating something for all values that x can assume.
23.Unification in the Predicate Logic
24.Resolution in the Predicate Logic
25. Converting a Predicate Expression to Clause Form
Step 1: Eliminate implication. Recall that p ⇒ q ≡ ~ p ˅ q.
Step 2: Reduce the scope of negation by using the following logical equivalences:
i) ~ (~a) ≡ a
ii) ~ (∃x) P(x) ≡ (∀x) ~P (x)
iii) ~ (∀x) P(x) ≡ (∃x) ~ P(x)
iv) ~ (a ˄ b) ≡ ~ a ˅ ~b De Morgan’s theorems
~ (a ˅ b) ≡ ~ a ˄ ~b
Step 3: Standardize variable names. All variables bound by different quantifiers must have unique names. It is therefore necessary to rename some variables.
Step 4: Move all quantifiers to the left, being certain to preserve their order.
Step 5: All existential quantifiers are now removed.
Step 6: Drop all universal quantifiers.
Step 7: Convert to conjunctive normal form (CNF), in other words, every expression is a conjunction of disjunctive terms.
Step 8: Each term being AND’ed will become a separate clause.
Step 9: Standardize the variable names one more time.



Proof Tree
26. Logics
a.First Order Predicate Logic (FOPL)
b.Second Order Logic
c.Non-Monotonic Logic
d.Fuzzy Logic
Fuzzy logic permits this latitude in truth-values. A logical expression can vary anywhere from false (0.0 degree of truth) to certainty (1.0 degree of truth).
e.Modal Logic

27.Graphical sketch
. A graphical sketch is an informal drawing or outline of a setting, a process, a mood, or system.
28.Human Window
The Human Window is a region constrained by human memory capabilities and computational limitations.
29.Graph
A graph consists of a finite set of vertices (nodes) together with a finite set of edges. Each edge consists of a distinct pair of vertices. If the edge e consists of the vertices {u, v} we often write e = (u, v) and say that u is joined to v (also that v is joined to u) and that u and v are adjacent. We also say that u and v are incident with the edge e. Graphs can be directed or undirected, together with labels and weights. A famous problem is The Bridges of Königsberg Problem.
30. Search tree
31.Decision Tree
A decision tree is a special type of a search tree that can be used to find a solution to a problem by choosing from alternatives starting from a root node. A decision tree will logically split a problem space into separate paths, which can be independently followed in the search for a solution, or for the answer to a question.
32.Production systems
Production systems are often represented by a set of rules of the form,IF [condition] THEN [action], together with a control system, which acts as rule interpreter and a sequencer and a database.
33.Object orientation
Object orientation is a programming paradigm that
is designed to be an intuitive and natural reflection of the
human experience. It is based on the concepts of inheritance, polymorphism, and encapsulation.
Procedural and data abstraction are combined into the notion of classes. Classes describe the data
and behavior common to a collection of objects. Objects are instances of classes.
34.Frames

35.Scripts
36.Semantic networks

37.Associations
38.Concept Maps

39.Conceptual Graphs
40.Baecker’s Work
41.Agents
Common notions of the word “agent” are (1) one who acts or who can act, and (2) one who acts in place of another with permission.
Agents have four qualities: situated, autonomous,flexible,social.
42.Random Search
a.Strategy
The strategy of Random Search is to sample solutions from across the entire search space using a uniform probability distribution. Each future sample is independent of the samples that come before it.
b.Procedure

43.Tabu Search
a.Strategy
The objective for the Tabu Search algorithm is to constrain an embedded heuristic from returning to recently visited areas of the search space, referred to as cycling. The strategy of the approach is to maintain a short term memory of the specific changes of recent moves within the search space and preventing future moves from undoing those changes.
b.Procedure

44.Stochastic Hill Climbing
a.Strategy
The strategy of the Stochastic Hill Climbing algorithm is iterate the process of randomly selecting a neighbor for a candidate solution and only accept it if it results in an improvement. The strategy was proposed to address the limitations of deterministic hill climbing techniques that were likely to get stuck in local optima due to their greedy acceptance of neighboring moves.
b.Procedure

45. Genetic Algorithm
a.Strategy
The strategy for the Genetic Algorithm is to repeatedly employ surrogates or the recombination and mutation genetic mechanisms on the population of candidate solutions, where the cost function (also known as objective or fitness function) applied to a decoded representation of a candidate governs the probabilistic contributions a given candidate solution can make to the subsequent generation of candidate solutions.
b.Procedure

46.Simulated Annealing
a.Strategy
The information processing objective of the technique is to locate the minimum cost configuration in the search space. The algorithms plan of action is to probabilistically re-sample the problem space where the acceptance of new samples into the currently held sample is managed by a probabilistic function that becomes more discerning of the cost of samples it accepts over the execution time of the algorithm. This probabilistic decision is based on the Metropolis-Hastings algorithm for simulating samples from a thermodynamic system.
b.Procedure

47.Prolog
Prolog has several basic features:
a.A uniform database.Data is given in clausal form.
b.Prolog provides logic variables as opposed to "normal variables".
c.Resolution is executed via depth first search within the knowledge base.
d.Prolog can support the processing of structure data such as lists.
48.Evolutionary Computation techniques
basic procedure:
a. Initialize the population
b.Calculate the fitness for each individual in the population
c.Reproduce selected individuals to form a new population
d.Perform evolutionary operations, such as crossover and mutation on the population
e.Loop to step b until some conditions is met.
49.Predicate Calculus
https://www.zweigmedia.com/RealWorld/logic/logic7.html
For all x, if x is a man then x is mortal. ∀x[Px→Qx].
All men are mortal. ∀x[Px → Qx]
Socrates is a man. Ps
Therefore, Socrates is mortal.  Qs
Qs
For all x, if x is a number and x is greater than 1, then x is greater than 0.
∀x[(Nx (x>1)) → (x>0)].
(x>1)) → (x>0)].
For every person x, there is a person y such that x is better off than y.
∀x[Px→(∃y[Py B(x,y)])]
B(x,y)])]
For every integer n, if n is divisible by 6 then it is divisible by 3 and by 2.
∀n[(∃m[n = 6m])→(∃m[n = 3m]) (∃m[n = 2m])].
(∃m[n = 2m])].

























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








