╋━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━╋
┃DNS信息收集——DIG ┃
┃ dig @8.8.8.8 www.sina.com.mx ┃
┃ dig www.sina.com any ┃
┃ 反向查询:dig +noall +answer -x 8.8.8.8 ┃
┃ bind版本信息:dig +noall +answer txt chaos VERSION.BIND @ns3.dnsv4.com┃
┃ DNS追踪:dig +trace example.com ┃
┃ 抓包比较递归查询、迭代查询过程的区别 ┃
╋━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━╋
Dig是linux中的域名解析工具,功能比nslookup强很多,使用也很方便,不用象nslookup总是set不停。
Dig是domain information groper的缩写,知道了来源想必大家也就容易记住这条命令了。
Dig现在已经有人移植到了window上,可以在这里下载。
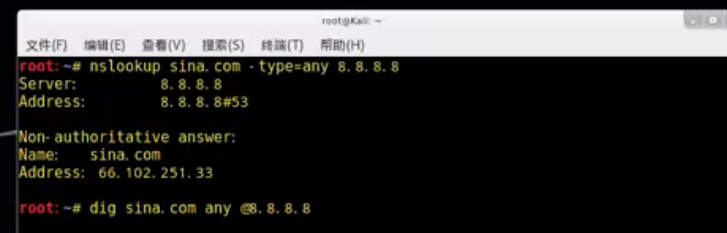
root@kali:~# nslookup sina.com -type=any 8.8.8.8
Server: 8.8.8.8
Address: 8.8.8.8#53
Non-authoritative answer:
Name: sina.com
Address: 66.102.251.33
root@kali:~# dig sina.com any @8.8.8.8
; <<>> DiG 9.9.5-9+deb8u3-Debian <<>> sina.com any @8.8.8.8
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 21943
;; flags: qr rd ra; QUERY: 1, ANSWER: 14, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 512
;; QUESTION SECTION:
;sina.com. IN ANY
;; ANSWER SECTION:
sina.com. 59 IN A 66.102.251.33
sina.com. 59 IN TXT "v=spf1 include:spf.sinamail.sina.com.cn -all"
sina.com. 299 IN SOA ns1.sina.com.cn. zhihao.staff.sina.com.cn. 2005042601 900 300 604800 300
sina.com. 21599 IN NS ns2.sina.com.
sina.com. 21599 IN NS ns4.sina.com.
sina.com. 21599 IN NS ns2.sina.com.cn.
sina.com. 21599 IN NS ns1.sina.com.cn.
sina.com. 21599 IN NS ns3.sina.com.
sina.com. 21599 IN NS ns4.sina.com.cn.
sina.com. 21599 IN NS ns3.sina.com.cn.
sina.com. 21599 IN NS ns1.sina.com.
sina.com. 59 IN MX 10 freemx2.sinamail.sina.com.cn.
sina.com. 59 IN MX 10 freemx3.sinamail.sina.com.cn.
sina.com. 59 IN MX 5 freemx1.sinamail.sina.com.cn.
;; Query time: 414 msec
;; SERVER: 8.8.8.8#53(8.8.8.8)
;; WHEN: Thu Sep 17 13:39:30 CST 2015
;; MSG SIZE rcvd: 395root@kali:~# dig sina.com any @202.106.0.20
; <<>> DiG 9.9.5-9+deb8u3-Debian <<>> sina.com any @202.106.0.20
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 25617
;; flags: qr rd ra; QUERY: 1, ANSWER: 12, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;sina.com. IN ANY
;; ANSWER SECTION:
sina.com. 26 IN MX 10 freemx2.sinamail.sina.com.cn.
sina.com. 26 IN MX 5 freemx1.sinamail.sina.com.cn.
sina.com. 26 IN MX 10 freemx3.sinamail.sina.com.cn.
sina.com. 46 IN A 66.102.251.33
sina.com. 69901 IN NS ns1.sina.com.cn.
sina.com. 69901 IN NS ns2.sina.com.cn.
sina.com. 69901 IN NS ns3.sina.com.
sina.com. 69901 IN NS ns3.sina.com.cn.
sina.com. 69901 IN NS ns1.sina.com.
sina.com. 69901 IN NS ns2.sina.com.
sina.com. 69901 IN NS ns4.sina.com.cn.
sina.com. 69901 IN NS ns4.sina.com.
;; Query time: 52 msec
;; SERVER: 202.106.0.20#53(202.106.0.20)
;; WHEN: Thu Sep 17 13:42:55 CST 2015
;; MSG SIZE rcvd: 289
root@kali:~# dig mail.163.com any
; <<>> DiG 9.9.5-9+deb8u3-Debian <<>> mail.163.com any
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 35590
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 8, ADDITIONAL: 10
;; QUESTION SECTION:
;mail.163.com. IN ANY
;; ANSWER SECTION:
mail.163.com. 1190 IN CNAME mail163.yxgslb.netease.com.
;; AUTHORITY SECTION:
163.com. 40210 IN NS ns3.nease.net.
163.com. 40210 IN NS ns2.nease.net.
163.com. 40210 IN NS ns8.nease.net.
163.com. 40210 IN NS ns4.nease.net.
163.com. 40210 IN NS ns5.nease.net.
163.com. 40210 IN NS ns1.nease.net.
163.com. 40210 IN NS ns7.nease.net.
163.com. 40210 IN NS ns6.nease.net.
;; ADDITIONAL SECTION:
ns1.nease.net. 40210 IN A 123.58.173.177
ns2.nease.net. 40210 IN A 123.58.173.178
ns3.nease.net. 40211 IN A 220.181.28.4
ns4.nease.net. 70848 IN A 61.135.255.140
ns5.nease.net. 40211 IN A 121.195.179.18
ns6.nease.net. 40210 IN A 121.195.179.19
ns7.nease.net. 40210 IN A 111.13.84.10
ns7.nease.net. 40210 IN A 111.13.84.11
ns8.nease.net. 40212 IN A 54.86.137.107
ns8.nease.net. 40212 IN A 54.178.188.118
;; Query time: 229 msec
;; SERVER: 192.168.1.1#53(192.168.1.1)
;; WHEN: Thu Sep 17 13:44:29 CST 2015
;; MSG SIZE rcvd: 380这里的noall是什么也不输出的意思
root@kali:~# dig +noall mail.163.com所以我们需要再加一个answer指令
root@kali:~# dig +noall +answer mail.163.com any
mail.163.com. 1002 IN CNAME mail163.yxgslb.netease.com.我们也可以通过awk来对内容进行筛选;
比如只打印第五列的结果
root@kali:~# dig +noall +answer mail.163.com any | awk '{print $5}'
mail163.yxgslb.netease.com.dig也可以做反向查询;
我们先查一下cname记录对应的IP地址
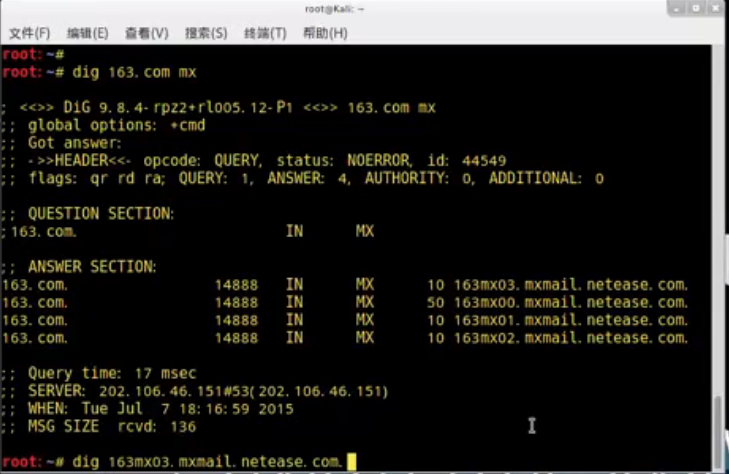
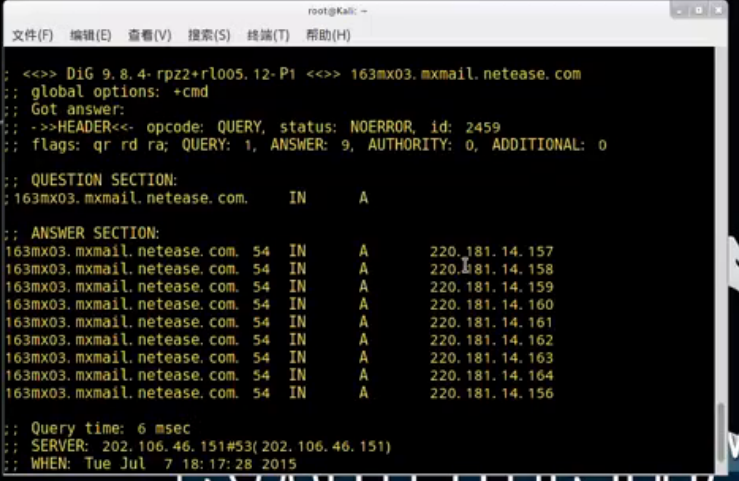
现在我们对这些地址做一个反查;
root@kali:~# dig -x 220.181.14.157
; <<>> DiG 9.9.5-9+deb8u3-Debian <<>> -x 220.181.14.157
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 37542
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 8, ADDITIONAL: 10
;; QUESTION SECTION:
;157.14.181.220.in-addr.arpa. IN PTR
;; ANSWER SECTION:
157.14.181.220.in-addr.arpa. 86400 IN PTR m14-157.188.com.
;; AUTHORITY SECTION:
14.181.220.in-addr.arpa. 477311 IN NS ns4.nease.net.
14.181.220.in-addr.arpa. 477311 IN NS ns5.nease.net.
14.181.220.in-addr.arpa. 477311 IN NS ns8.nease.net.
14.181.220.in-addr.arpa. 477311 IN NS ns2.nease.net.
14.181.220.in-addr.arpa. 477311 IN NS ns1.nease.net.
14.181.220.in-addr.arpa. 477311 IN NS ns6.nease.net.
14.181.220.in-addr.arpa. 477311 IN NS ns3.nease.net.
14.181.220.in-addr.arpa. 477311 IN NS ns7.nease.net.
;; ADDITIONAL SECTION:
ns1.nease.net. 34549 IN A 123.58.173.177
ns2.nease.net. 34549 IN A 123.58.173.178
ns3.nease.net. 34550 IN A 220.181.28.4
ns4.nease.net. 65187 IN A 61.135.255.140
ns5.nease.net. 34550 IN A 121.195.179.18
ns6.nease.net. 34549 IN A 121.195.179.19
ns7.nease.net. 34549 IN A 111.13.84.10
ns7.nease.net. 34549 IN A 111.13.84.11
ns8.nease.net. 34551 IN A 54.178.188.118
ns8.nease.net. 34551 IN A 54.86.137.107
;; Query time: 29 msec
;; SERVER: 192.168.1.1#53(192.168.1.1)
;; WHEN: Thu Sep 17 15:18:49 CST 2015
;; MSG SIZE rcvd: 387
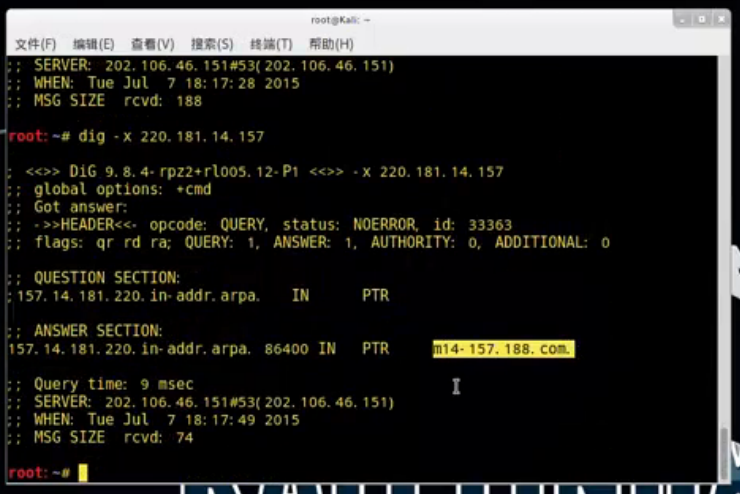
dig还可以查询服务器bind版本信息;
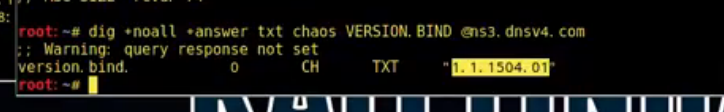
我们再查一个;
root@kali:~# dig sina.com ns
; <<>> DiG 9.9.5-9+deb8u3-Debian <<>> sina.com ns
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 17697
;; flags: qr rd ra; QUERY: 1, ANSWER: 8, AUTHORITY: 0, ADDITIONAL: 9
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;sina.com. IN NS
;; ANSWER SECTION:
sina.com. 31995 IN NS ns3.sina.com.cn.
sina.com. 31995 IN NS ns2.sina.com.cn.
sina.com. 31995 IN NS ns4.sina.com.
sina.com. 31995 IN NS ns1.sina.com.cn.
sina.com. 31995 IN NS ns2.sina.com.
sina.com. 31995 IN NS ns3.sina.com.
sina.com. 31995 IN NS ns4.sina.com.cn.
sina.com. 31995 IN NS ns1.sina.com.
;; ADDITIONAL SECTION:
ns1.sina.com. 31995 IN A 114.134.80.144
ns1.sina.com.cn. 23569 IN A 202.106.184.166
ns2.sina.com. 22584 IN A 114.134.80.145
ns2.sina.com.cn. 25771 IN A 61.172.201.254
ns3.sina.com. 21335 IN A 61.172.201.254
ns3.sina.com.cn. 23569 IN A 123.125.29.99
ns4.sina.com. 23573 IN A 123.125.29.99
ns4.sina.com.cn. 23569 IN A 121.14.1.22
;; Query time: 227 msec
;; SERVER: 192.168.1.1#53(192.168.1.1)
;; WHEN: Thu Sep 17 19:16:43 CST 2015
;; MSG SIZE rcvd: 320这里我们就选用ns的ns2.sina.com这个网站;
root@kali:~# dig +noall +answer txt chaos VERSION.BIND @ns2.sina.com
VERSION.BIND. 0 CH TXT 看以看到bind版本的信息被隐藏了。。。
其实大家都知道,如果我们知道了版本后,我们可以利用这个版本的一些漏洞进行查找。所以,不要把DNS透露到公网上!
下面我们再讲一下。dig的+trace选项追踪DNS解析过程;
root@bogon:~# dig +trace www.sina.com
; <<>> DiG 9.10.3-P4-Debian <<>> +trace www.sina.com
;; global options: +cmd
. 410232 IN NS m.root-servers.net.
. 410232 IN NS c.root-servers.net.
. 410232 IN NS h.root-servers.net.
. 410232 IN NS e.root-servers.net.
. 410232 IN NS j.root-servers.net.
. 410232 IN NS l.root-servers.net.
. 410232 IN NS i.root-servers.net.
. 410232 IN NS f.root-servers.net.
. 410232 IN NS b.root-servers.net.
. 410232 IN NS a.root-servers.net.
. 410232 IN NS d.root-servers.net.
. 410232 IN NS g.root-servers.net.
. 410232 IN NS k.root-servers.net.
. 410232 IN RRSIG NS 8 0 518400 20160525050000 20160515040000 60615 . QJgP3BIx2zDSGdjaNmlRmIBkPeK66yZog51dvLT9jXbaJ7nrkbZNfPLp NI5KE6dv1d0sK8dwDakoM/0B9J4jSckkOzQnT2jStsfG+UmswVqhW/Wf b1cZlu0S88PFB/ciJ7WaPva+dycxVS/8+xzJNiala/5aDc8dtwOCuCZ1 iQw=
;; Received 397 bytes from 202.99.160.68#53(202.99.160.68) in 20 ms
com. 172800 IN NS m.gtld-servers.net.
com. 172800 IN NS e.gtld-servers.net.
com. 172800 IN NS g.gtld-servers.net.
com. 172800 IN NS c.gtld-servers.net.
com. 172800 IN NS h.gtld-servers.net.
com. 172800 IN NS l.gtld-servers.net.
com. 172800 IN NS i.gtld-servers.net.
com. 172800 IN NS b.gtld-servers.net.
com. 172800 IN NS j.gtld-servers.net.
com. 172800 IN NS a.gtld-servers.net.
com. 172800 IN NS k.gtld-servers.net.
com. 172800 IN NS d.gtld-servers.net.
com. 172800 IN NS f.gtld-servers.net.
com. 86400 IN DS 30909 8 2 E2D3C916F6DEEAC73294E8268FB5885044A833FC5459588F4A9184CF C41A5766
com. 86400 IN RRSIG DS 8 1 86400 20160526050000 20160516040000 60615 . paIUqaDEAUXsH3Nuu2+45ZN1KIVKLFPGjb/DZFhgwu1NW/2+9BoW5/bh djCnEWBdnmP4mw5PZuoN3sRdSH/RzBXLX+gcoHYRq7+HqOyU7AjuyLj6 viniPv8C7iTNK/GwUbVBeM8neJ7egAGUXFmjI/s4/3WBt4lww6ypYm91 u9E=
;; Received 736 bytes from 202.12.27.33#53(m.root-servers.net) in 151 ms
sina.com. 172800 IN NS ns1.sina.com.cn.
sina.com. 172800 IN NS ns2.sina.com.cn.
sina.com. 172800 IN NS ns3.sina.com.cn.
sina.com. 172800 IN NS ns1.sina.com.
sina.com. 172800 IN NS ns2.sina.com.
sina.com. 172800 IN NS ns4.sina.com.
sina.com. 172800 IN NS ns3.sina.com.
CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN NSEC3 1 1 0 - CK0Q1GIN43N1ARRC9OSM6QPQR81H5M9A NS SOA RRSIG DNSKEY NSEC3PARAM
CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN RRSIG NSEC3 8 2 86400 20160522050725 20160515035725 34745 com. Og2nR0w6gJppWGoguvWKWs1ckF70tAhGyMOfzy4n+ihqvEtVB8DtBsqj GyLPnDA1DOtjiWsBq/qLa1DVsQ9Z6G74yj6n4GnXtfFcKl13rEX2NMAL C6RADMyoyh2N7yGqQYNAnT8l2ZWRE03m48+6cbz/C3ejFiCe9KyhlrZX 6/Y=
TGAFTKK08BOUSKO3P3B8A4U84C84DTHM.com. 86400 IN NSEC3 1 1 0 - TGAIGAA7UE2B06LAN5KC5MT51RE8U42A NS DS RRSIG
TGAFTKK08BOUSKO3P3B8A4U84C84DTHM.com. 86400 IN RRSIG NSEC3 8 2 86400 20160521043955 20160514032955 34745 com. GHjaw9XewFzB70wH9kkVDmqULpgm2vapYenP10NDqSh5cftVBU+ww9T+ suTIcSImmB3Q9LrO+IDedNDKi0iFpleTK2iCQVFNtPC7DHwuoR7cFL4h +7OPBNhDWKYPoYWQPcFKcwq++A0Vrj0kTbi23VYUR2cnfCHmim9MB0zB fdg=
;; Received 727 bytes from 192.43.172.30#53(i.gtld-servers.net) in 155 ms
www.sina.com. 60 IN CNAME us.sina.com.cn.
us.sina.com.cn. 60 IN CNAME wwwus.sina.com.
wwwus.sina.com. 60 IN A 66.102.251.33
sina.com. 86400 IN NS ns2.sina.com.
sina.com. 86400 IN NS ns1.sina.com.
sina.com. 86400 IN NS ns4.sina.com.
sina.com. 86400 IN NS ns3.sina.com.cn.
sina.com. 86400 IN NS ns2.sina.com.cn.
sina.com. 86400 IN NS ns1.sina.com.cn.
sina.com. 86400 IN NS ns4.sina.com.cn.
sina.com. 86400 IN NS ns3.sina.com.
;; Received 377 bytes from 123.125.29.99#53(ns4.sina.com) in 33 ms
本机先会去访问13个根域的服务器,然后会去查.com的服务器,也是13个,再随机挑选一个.com的ip地址,去查ns的记录,再随机挑选由ns的记录去查name的记录,一个迭代的查询。然后再由CNAME记录去解析A,得到了IP。在这个过程中,我们进行了抓包,现在来看一下抓包信息。
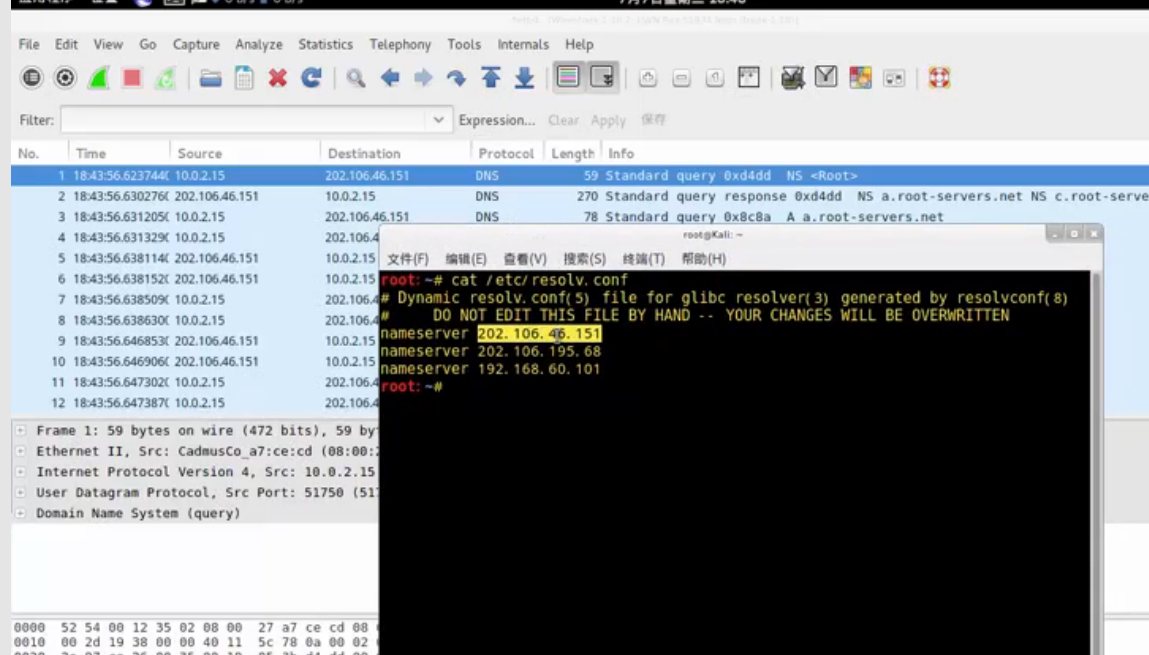
首先是由本机的DNS服务器进行查询的
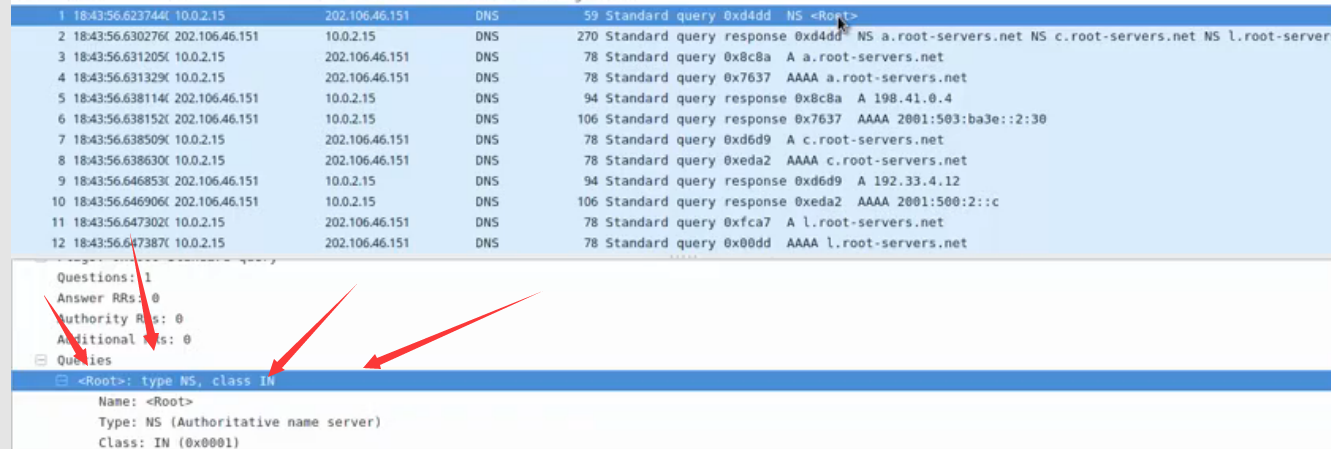
可以看到显示查询ns的13个根域的域名服务器名称以及对称关系。
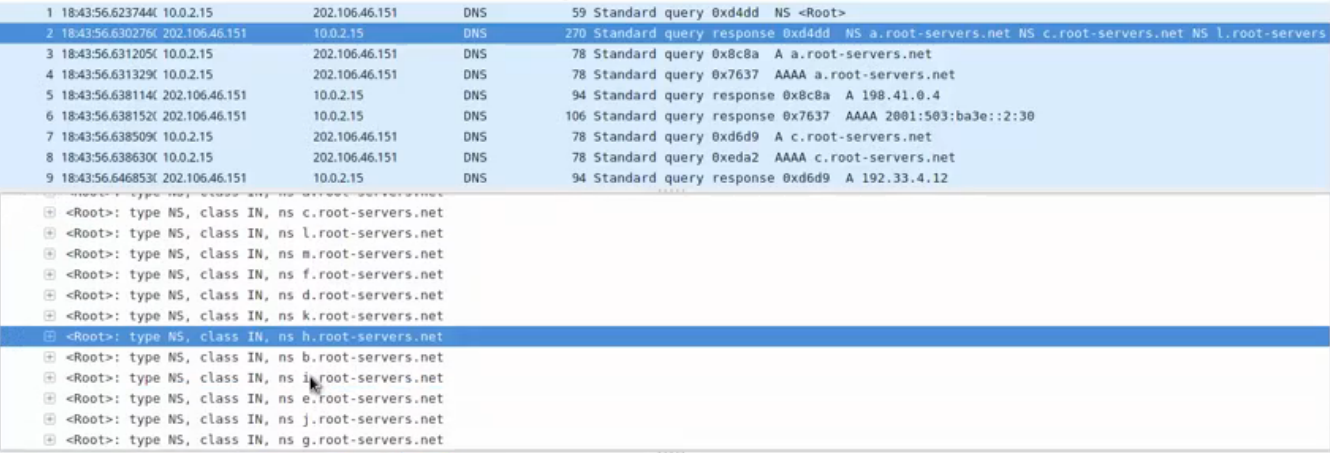
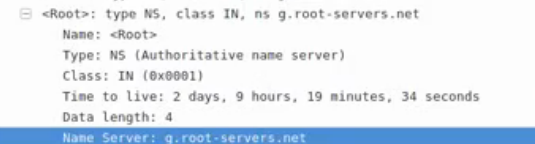
这里可以看到answer,拿到13个域名服务器的名称后,但是不知道IP地址是什么,所以,客户端的DNS服务器将再会向本地的A记录,AAAA记录(相当于IPV6的域名解析地址)
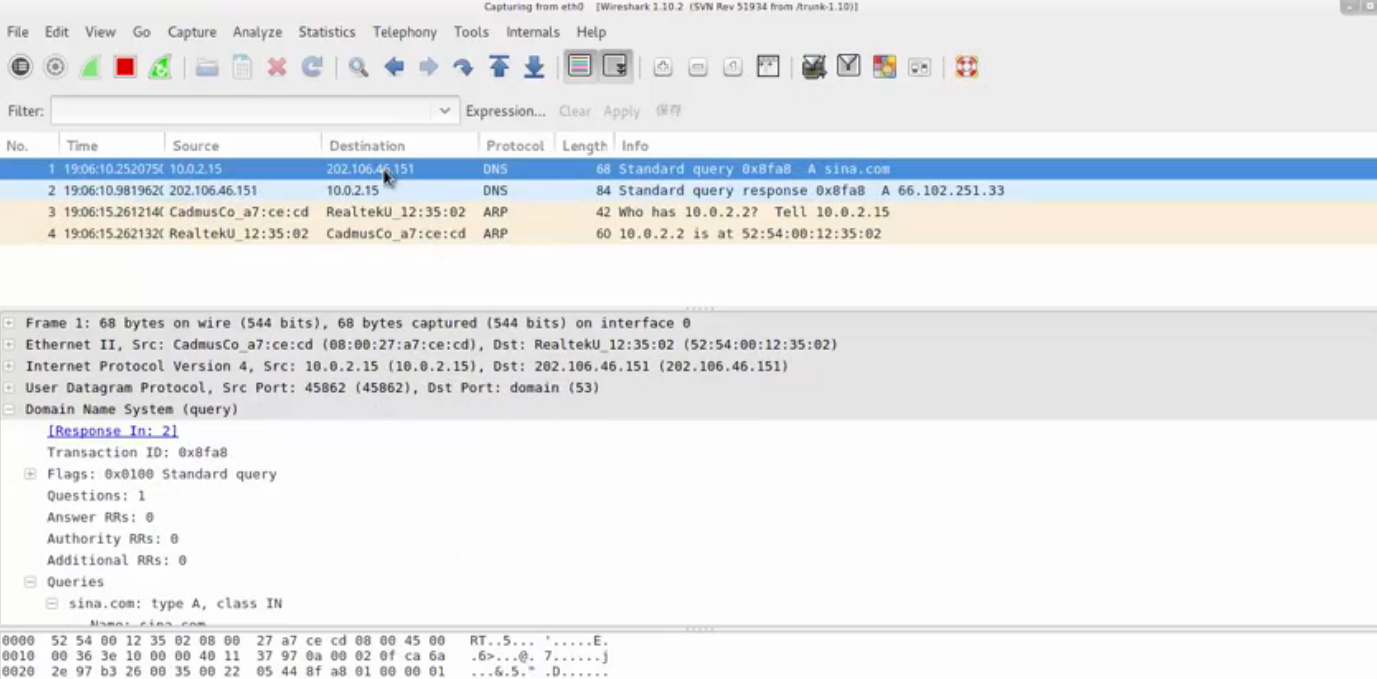
我们再来看一下递归的查询结果;
root@bogon:~# dig sina.com
; <<>> DiG 9.10.3-P4-Debian <<>> sina.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 33896
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;sina.com. IN A
;; ANSWER SECTION:
sina.com. 13 IN A 66.102.251.33
;; Query time: 113 msec
;; SERVER: 202.99.160.68#53(202.99.160.68)
;; WHEN: Mon May 16 22:18:36 CST 2016
;; MSG SIZE rcvd: 53
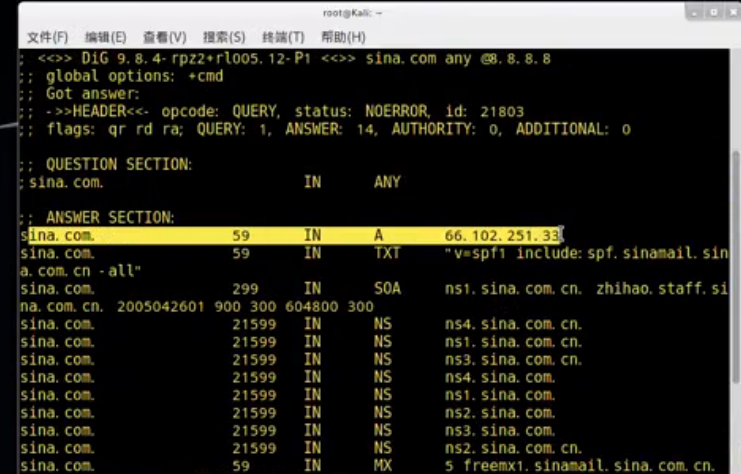
个人理解:
root@bogon:~# dig sina.com
; <<>> DiG 9.10.3-P4-Debian <<>> sina.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 33896
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;sina.com. IN A
;; ANSWER SECTION:
sina.com. 13 IN A 66.102.251.33
;; Query time: 113 msec
;; SERVER: 202.99.160.68#53(202.99.160.68)
;; WHEN: Mon May 16 22:18:36 CST 2016
;; MSG SIZE rcvd: 53






















 554
554











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








