ubuntu安装gmp+pbc+charm以及CP_ABE的两种实现方式
依赖以及基础密码学库安装
安装依赖项:m4,flex,bison。
在安装之前,我们要先进入root权限:
sudo su
然后我们使用如下命令安装:
sudo apt-get install m4
sudo apt-get install flex
sudo apt-get install bison
gmp安装
下载 https://gmplib.org/
安装zstd包用于解压gmp-6.2.1.tar.zst得到gmp源码文件
sudo apt install zstd
tar -I zstd -xvf gmp-6.2.1.tar.zst
然后打开文件夹,在文件夹中打开终端,输入如下命令进行安装:
./configure
make check
make
make install
pbc安装
下载:https://crypto.stanford.edu/pbc/download.html
右键将文件pbc-0.5.14.tar.gz提取出来,然后打开文件夹,在文件夹中打开终端,输入如下命令进行安装:
./configure
make
make install
CP-ABE 的实现方式一
libbswabe安装
下载 http://acsc.cs.utexas.edu/cpabe/index.html
使用下面命令安装libssl-dev:
sudo apt-get install libssl-dev
使用下面命令安装libglib2.0-dev
sudo apt-get install libglib2.0-dev
右键将libbswabe-0.9.tar.gz提取到此处,然后打开文件夹,在文件夹中打开终端,输入如下命令进行安装:
./configure
make
make install
cpabe安装
下载:http://acsc.cs.utexas.edu/cpabe/index.html
右键将文件cpabe-0.11.tar.gz提取到此处,然后打开文件夹,在文件夹中打开终端,输入如下命令进行安装:
./configure
执行完上面的命令,需要修改Makefile文件,在LDFLAGS最后再加一行,写:-lgmp (\和tab键不能忘记)详细见后面图片。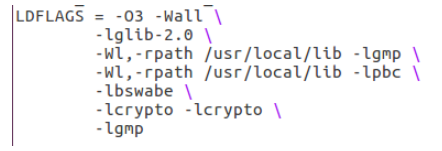
然后需要打开policy_lang.y文件在67行的 } 前面添加一个分号 ; 。
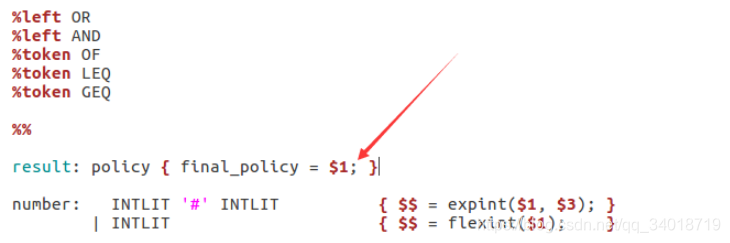
然后进行编译安装
make
make install
安装完成
调用测试
1、setup
通过setup步骤,我们可以生成公钥和主密钥。命令如下:
cpabe-setup
接下来,我们就可以使用master_key来生成各种与属性集关联的私钥。
2、keygen
当我们拥有了公钥和主密钥,就可以来生成用户的私钥,假设我们有两个用户A和B,假设我们生成对应的私钥为:sara_priv_key,kevin_priv_key。我们使用如下命令生成私钥:
cpabe-keygen -o sara_priv_key pub_key master_key sysadmin it_department 'office = 1431' 'hire_date = '`date +%s`
cpabe-keygen -o kevin_priv_key pub_key master_key business_staff strategy_team 'executive_level = 7' 'office = 2362' 'hire_date = '`date +%s`
通过这一步,我们生成了两个用户的私钥 。
注意:
我们只是为某些属性分配了值,另一些属性只是简单地具有了键,并未进行赋值限定。如hire_date。
3、encrypt
接下来就是我们的加密过程了。我们需要自己创建一个被加密文件(test.txt)代码如下:
cpabe-enc pub_key test.txt \\命令
//访问结构
(sysadmin and (hire_date < 946702800 or security_team)) or
(business_staff and 2 of (executive_level >= 5, audit_group, strategy_team))
然后以Ctrl + D结束。
注意:
三行代码必须输入一行,按一次回车,输入完第三行,按Ctrl + D。
运行结果如下图:
这样,我们就生成了一个加密文件test.txt.cpabe。根据其规则,我们知道,kevin可以解密而sara不能解密
4、decrypt
根据上一步我们知道kevin能解密,所以我们使用sara的密钥解密。
cpabe-dec pub_key sara_priv_key test.txt.cpabe
然后我们使用kevin的密钥解密:
cpabe-dec pub_key kevin_priv_key test.txt.cpabe
CP-ABE 的实现方式二
安装openSSL
下载 https://www.openssl.org/source/
tar -zxvf openssl-1.0.2s.tar.gz
cd openssl-1.0.2
./configure
make
sudo make install
安装 charm
下载:https://github.com/JHUISI/charm (github项目)
右键将charm-dev.zip提取到此处,然后打开文件夹,在文件夹中打开终端,输入如下命令进行安装:
./configure.sh
make
make install
利用charm编写CP_ABE的python代码
1、切换Pycharm的编译环境为system Interpreter
2、ABE BSW方案代码
from charm.toolbox.pairinggroup import PairingGroup,ZR,G1,G2,GT,pair
from charm.toolbox.secretutil import SecretUtil
from charm.toolbox.ABEnc import ABEnc, Input, Output
# type annotations
pk_t = { 'g':G1, 'g2':G2, 'h':G1, 'f':G1, 'e_gg_alpha':GT }
mk_t = {'beta':ZR, 'g2_alpha':G2 }
sk_t = { 'D':G2, 'Dj':G2, 'Djp':G1, 'S':str }
ct_t = { 'C_tilde':GT, 'C':G1, 'Cy':G1, 'Cyp':G2 }
debug = False
class CPabe_BSW07(ABEnc):
"""
>>> from charm.toolbox.pairinggroup import PairingGroup,ZR,G1,G2,GT,pair
>>> group = PairingGroup('SS512')
>>> cpabe = CPabe_BSW07(group)
>>> msg = group.random(GT)
>>> attributes = ['ONE', 'TWO', 'THREE']
>>> access_policy = '((four or three) and (three or one))'
>>> (master_public_key, master_key) = cpabe.setup()
>>> secret_key = cpabe.keygen(master_public_key, master_key, attributes)
>>> cipher_text = cpabe.encrypt(master_public_key, msg, access_policy)
>>> decrypted_msg = cpabe.decrypt(master_public_key, secret_key, cipher_text)
>>> msg == decrypted_msg
True
"""
def __init__(self, groupObj):
ABEnc.__init__(self)
global util, group
util = SecretUtil(groupObj, verbose=False)
group = groupObj
@Output(pk_t, mk_t)
def setup(self):
g, gp = group.random(G1), group.random(G2)
alpha, beta = group.random(ZR), group.random(ZR)
# initialize pre-processing for generators
g.initPP(); gp.initPP()
h = g ** beta; f = g ** ~beta
e_gg_alpha = pair(g, gp ** alpha)
pk = { 'g':g, 'g2':gp, 'h':h, 'f':f, 'e_gg_alpha':e_gg_alpha }
mk = {'beta':beta, 'g2_alpha':gp ** alpha }
return (pk, mk)
@Input(pk_t, mk_t, [str])
@Output(sk_t)
def keygen(self, pk, mk, S):
r = group.random()
g_r = (pk['g2'] ** r)
D = (mk['g2_alpha'] * g_r) ** (1 / mk['beta'])
D_j, D_j_pr = {}, {}
for j in S:
r_j = group.random()
D_j[j] = g_r * (group.hash(j, G2) ** r_j)
D_j_pr[j] = pk['g'] ** r_j
return { 'D':D, 'Dj':D_j, 'Djp':D_j_pr, 'S':S }
@Input(pk_t, GT, str)
@Output(ct_t)
def encrypt(self, pk, M, policy_str):
policy = util.createPolicy(policy_str)
a_list = util.getAttributeList(policy)
s = group.random(ZR)
shares = util.calculateSharesDict(s, policy)
C = pk['h'] ** s
C_y, C_y_pr = {}, {}
for i in shares.keys():
j = util.strip_index(i)
C_y[i] = pk['g'] ** shares[i]
C_y_pr[i] = group.hash(j, G2) ** shares[i]
return { 'C_tilde':(pk['e_gg_alpha'] ** s) * M,
'C':C, 'Cy':C_y, 'Cyp':C_y_pr, 'policy':policy_str, 'attributes':a_list }
@Input(pk_t, sk_t, ct_t)
@Output(GT)
def decrypt(self, pk, sk, ct):
policy = util.createPolicy(ct['policy'])
pruned_list = util.prune(policy, sk['S'])
if pruned_list == False:
return False
z = util.getCoefficients(policy)
A = 1
for i in pruned_list:
j = i.getAttributeAndIndex(); k = i.getAttribute()
A *= ( pair(ct['Cy'][j], sk['Dj'][k]) / pair(sk['Djp'][k], ct['Cyp'][j]) ) ** z[j]
return ct['C_tilde'] / (pair(ct['C'], sk['D']) / A)
def main():
groupObj = PairingGroup('SS512')
cpabe = CPabe_BSW07(groupObj)
attrs = ['ONE', 'TWO', 'THREE']
access_policy = '((four or three) and (three or one))'
if debug:
print("Attributes =>", attrs); print("Policy =>", access_policy)
(pk, mk) = cpabe.setup()
sk = cpabe.keygen(pk, mk, attrs)
print("sk :=>", sk)
rand_msg = groupObj.random(GT)
if debug: print("msg =>", rand_msg)
ct = cpabe.encrypt(pk, rand_msg, access_policy)
if debug: print("\n\nCiphertext...\n")
groupObj.debug(ct)
rec_msg = cpabe.decrypt(pk, sk, ct)
if debug: print("\n\nDecrypt...\n")
if debug: print("Rec msg =>", rec_msg)
assert rand_msg == rec_msg, "FAILED Decryption: message is incorrect"
if debug: print("Successful Decryption!!!")
if __name__ == "__main__":
debug = True
main()
3、运行结果
/usr/bin/python3.4 /usr/local/lib/python3.4/dist-packages/Charm_Crypto-0.43-py3.4-linux-x86_64.egg/charm/schemes/abenc/abenc_bsw07.py
Attributes => ['ONE', 'TWO', 'THREE']
Policy => ((four or three) and (three or one))
sk :=> {'S': ['ONE', 'TWO', 'THREE'], 'Djp': {'ONE': [1656857131215580264510078454299990414175887444678436008332324360542735469179258124011404238217955081837786880138276570000997765310267143522376372323309070, 1020194252724993196593649866987385298542229853736046389300946124764947292401317558598634510350270226065183391641191344619648147673544771643861630244765930], 'TWO': [225317086650852053633971364384383011442618726962646456024839071109721775185973951992657058985833938226532065546643912474416823013889167466674625211542802, 5171211596342072937178509212242286325440319641530025777266992858662275312246353637368148221983474614209038517463417566890813420921040676994561999520751694], 'THREE': [3983328040050770385311661300958091739579156540917924891518947554398379535551315171256600054477162049224364382953582613187356721808236819041319638721047478, 7371267254746006440330119766353676015392228094735514424960465434771080152140386620007509569124264385016600460194218599155681078129987768944069589914239490]}, 'Dj': {'ONE': [1962627967356264304383273587974053565229154214703878240673183565251443678722539149280500080933156652747279940708819879106578786491620869965264661670349793, 738193107865147017138645734354784104728498756789693536386607463562358238023526996038934101133403879620520839670828705709045353274354995694025847243868564], 'TWO': [1733449180497253489761536512695142611941443126530136551522811723599825036941159083481783331690337863390556617893052369395870679686857873242817006664546558, 4558192993466863776692961804292316005634595519974374968695047717435431525272260433088523824208861644574753961533266595792172253018276618231053179769214467], 'THREE': [4409166116875522861349761633571530284175930541585875153977922931849362909800042310349838677159816941927756692334132282340748816972707154754404328168903324, 2144808269640752698084538531728733988657901478917609226246584412293784079675261515400344586913995169491739540527739968312682161005255677193767451989055897]}, 'D': [1635759058468099881703061645255879266664659870999373105240059945250388805865040227776529160859856210338558920903610269519132715827453619802041055435170321, 1091949721784882674875614682399727036457780605367860600157506109557720430784451962510054242801908289120338069045205395273838892330783136286666760942800974]}
msg => [4742011490917596458046505841387905176015968001608409912648099524254019771579532713401953289693580600713620411755823914152995309168774382204143043451006805, 956341419444095659848657352585671568036617096998621143045273563005069499664753599491731504482690115733852065040073109064757188053144907431510452742805115]
Ciphertext...
Decrypt...
Rec msg => [4742011490917596458046505841387905176015968001608409912648099524254019771579532713401953289693580600713620411755823914152995309168774382204143043451006805, 956341419444095659848657352585671568036617096998621143045273563005069499664753599491731504482690115733852065040073109064757188053144907431510452742805115]
Successful Decryption!!!
Process finished with exit code 0
注:本文使用ubuntu20.04系统,借鉴以下三篇文章完成,并一一验证过了。
CP-ABE库安装及调用借鉴:https://blog.csdn.net/shuiyixin/article/details/104490091
charm安装和使用借鉴:https://blog.csdn.net/qq_37272891/article/details/99631319
charm安装借鉴:https://blog.csdn.net/qq_34823530/article/details/96605662





















 985
985











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








