1.命令查询补丁
systeminfo
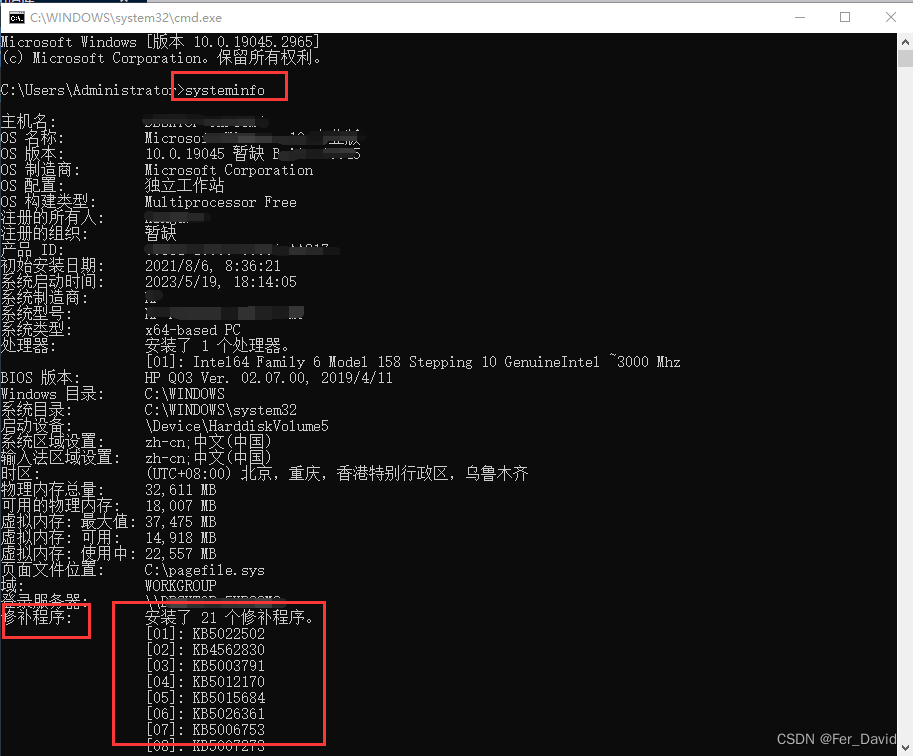
【需要将结果复制到】Windows提权辅助工具地址:
https://i.hacking8.com/tiquan
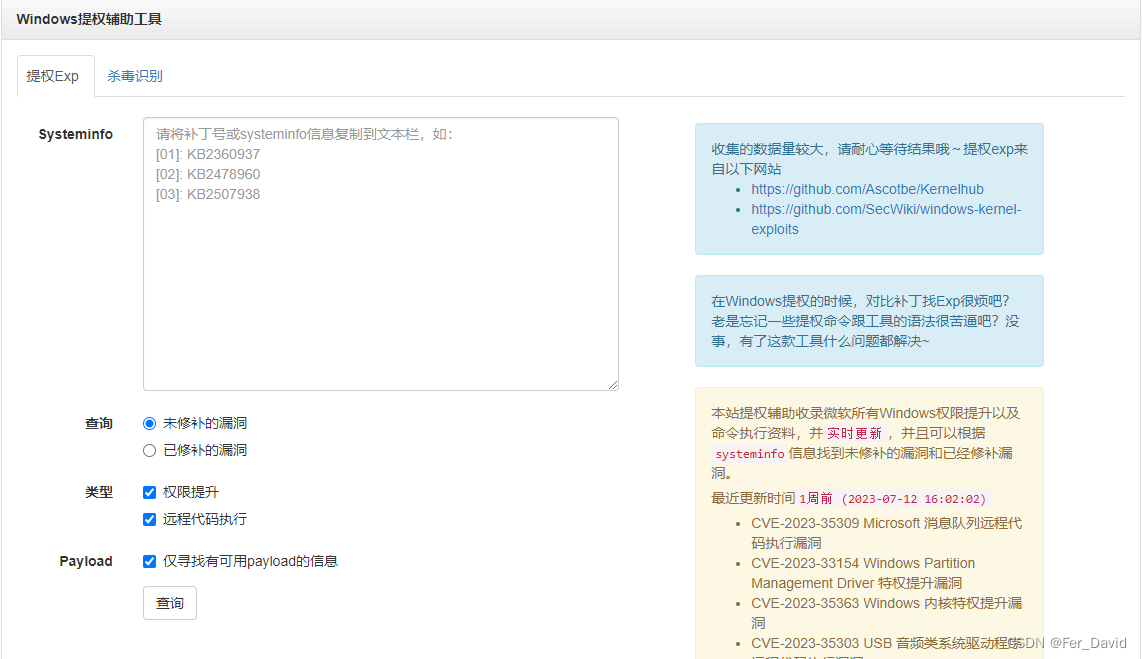
根据查询结果在这两个项目上寻找相关的编号的EXP进行提权:
- https://github.com/Ascotbe/Kernelhub
- https://github.com/SecWiki/windows-kernel-exploits
2.缺失补丁检测辅助工具
描述
该工具将目标补丁级别与 Microsoft 漏洞数据库进行比较,以检测目标上潜在的缺失补丁。它还会通知用户是否存在可用于缺失公告的公共漏洞和 Metasploit 模块。
它需要 Windows 主机的“systeminfo”命令输出,以便比较 Microsoft 安全公告数据库并确定主机的补丁级别。
它能够使用 --update 标志自动从 Microsoft 下载安全公告数据库,并将其保存为 Excel 电子表格。
查看命令输出时,需要注意的是,它假设了所有漏洞,然后根据修补程序数据有选择地删除它们。这可能会导致许多误报,了解目标主机上实际运行的软件至关重要。例如,如果存在已知的 IIS 漏洞,即使 IIS 未在目标主机上运行,它也会标记它们。
输出显示公共漏洞 (E) 或 Metasploit 模块 (M),如字符值所示。
它很大程度上受到 Pentura 的 Linux_Exploit_Suggester 的启发。
博客文章:“Windows 漏洞利用建议器简介”,https://blog.gdssecurity.com/labs/2014/7/11/introducing-windows-exploit-suggester.html
用法
更新数据库
$ ./windows-exploit-suggester.py --update
[*] initiating...
[*] successfully requested base url
[*] scraped ms download url
[+] writing to file 2014-06-06-mssb.xlsx
[*] done
安装依赖项
(安装 python-xlrd,$ pip install xlrd --upgrade)
向其提供“systeminfo”输入,并将其指向微软数据库
$ ./windows-exploit-suggester.py --database 2014-06-06-mssb.xlsx --systeminfo win7sp1-systeminfo.txt
[*] initiating...
[*] database file detected as xls or xlsx based on extension
[*] reading from the systeminfo input file
[*] querying database file for potential vulnerabilities
[*] comparing the 15 hotfix(es) against the 173 potential bulletins(s)
[*] there are now 168 remaining vulns
[+] windows version identified as 'Windows 7 SP1 32-bit'
[*]
[M] MS14-012: Cumulative Security Update for Internet Explorer (2925418) - Critical
[E] MS13-101: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (2880430) - Important
[M] MS13-090: Cumulative Security Update of ActiveX Kill Bits (2900986) - Critical
[M] MS13-080: Cumulative Security Update for Internet Explorer (2879017) - Critical
[M] MS13-069: Cumulative Security Update for Internet Explorer (2870699) - Critical
[M] MS13-059: Cumulative Security Update for Internet Explorer (2862772) - Critical
[M] MS13-055: Cumulative Security Update for Internet Explorer (2846071) - Critical
[M] MS13-053: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Remote Code Execution (2850851) - Critical
[M] MS13-009: Cumulative Security Update for Internet Explorer (2792100) - Critical
[M] MS13-005: Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege (2778930) - Important
[*] done
无需修补程序数据即可利用操作系统的可能漏洞
$ ./windows-exploit-suggester.py --database 2014-06-06-mssb.xlsx --ostext 'windows server 2008 r2'
[*] initiating...
[*] database file detected as xls or xlsx based on extension
[*] getting OS information from command line text
[*] querying database file for potential vulnerabilities
[*] comparing the 0 hotfix(es) against the 196 potential bulletins(s)
[*] there are now 196 remaining vulns
[+] windows version identified as 'Windows 2008 R2 64-bit'
[*]
[M] MS13-009: Cumulative Security Update for Internet Explorer (2792100) - Critical
[M] MS13-005: Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege (2778930) - Important
[E] MS11-011: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2393802) - Important
[M] MS10-073: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (981957) - Important
[M] MS10-061: Vulnerability in Print Spooler Service Could Allow Remote Code Execution (2347290) - Critical
[E] MS10-059: Vulnerabilities in the Tracing Feature for Services Could Allow Elevation of Privilege (982799) - Important
[E] MS10-047: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (981852) - Important
[M] MS10-002: Cumulative Security Update for Internet Explorer (978207) - Critical
[M] MS09-072: Cumulative Security Update for Internet Explorer (976325) - Critical
项目地址:
- https://github.com/SecWiki/windows-kernel-exploits/tree/master/win-exp-suggester























 628
628











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










