免责声明:内容仅供学习参考,请合法利用知识,禁止进行违法犯罪活动!
如果看不懂、不知道现在做的什么,那就跟着做完看效果
内容参考于:如果看不懂、不知道现在做的什么,那就跟着做完看效果,代码看不懂是正常的,只要会抄就行,抄着抄着就能懂了
上一个内容:55.通知数据的分析与截取模拟
码云地址(master 分支):https://gitee.com/dye_your_fingers/titan
码云版本号:44b1aa9836d3077e5267051c18102d301b5a09ff
代码下载地址,在 titan 目录下,文件名为:titan-聊天数据的截取与模拟.zip
链接:https://pan.baidu.com/s/1W-JpUcGOWbSJmMdmtMzYZg
提取码:q9n5
--来自百度网盘超级会员V4的分享
HOOK引擎,文件名为:黑兔sdk升级版.zip
链接:https://pan.baidu.com/s/1IB-Zs6hi3yU8LC2f-8hIEw
提取码:78h8
--来自百度网盘超级会员V4的分享
以 55.通知数据的分析与截取模拟 它的代码为基础进行修改
本次完成了聊天数据的发送与拦截
聊天
附近
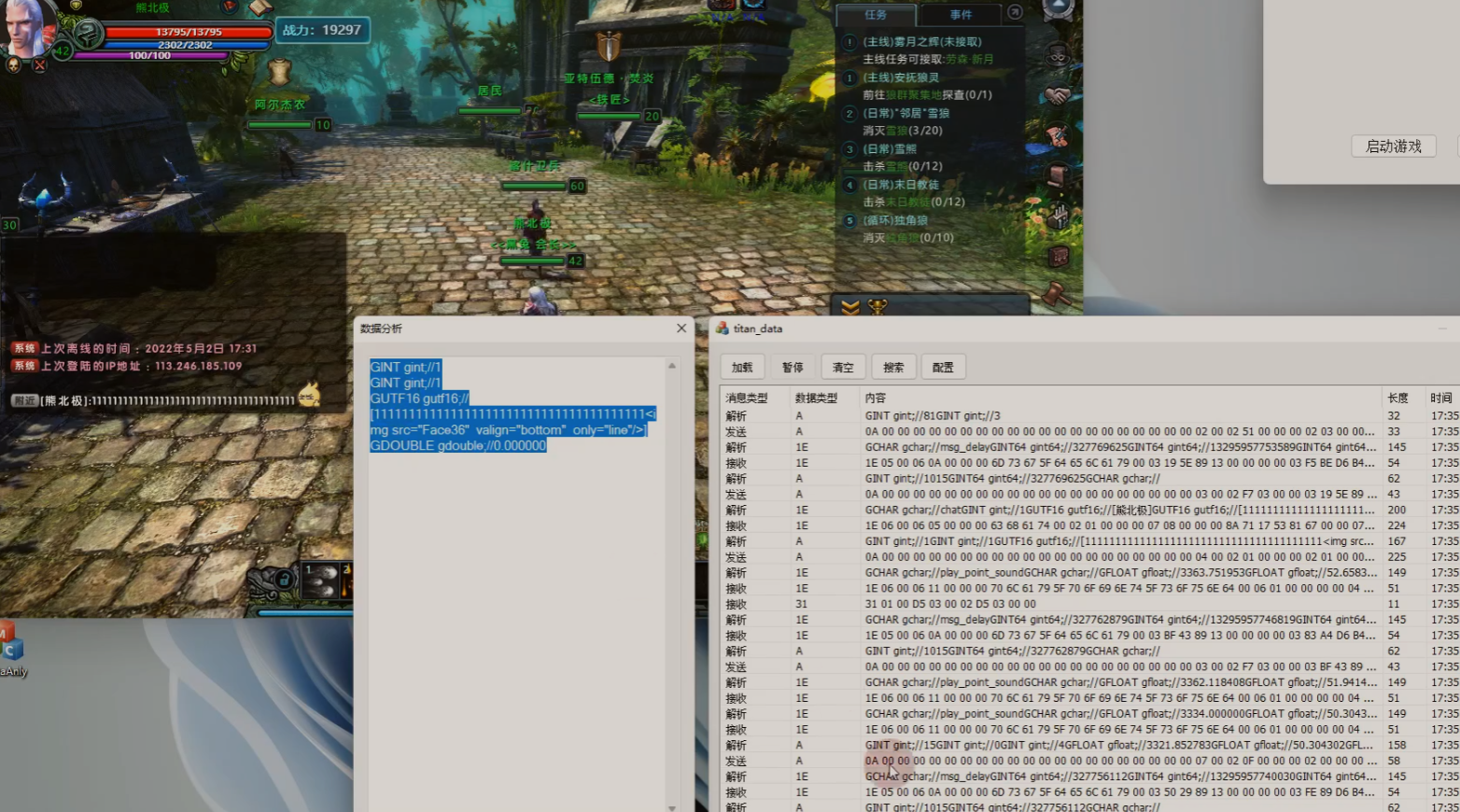
私聊
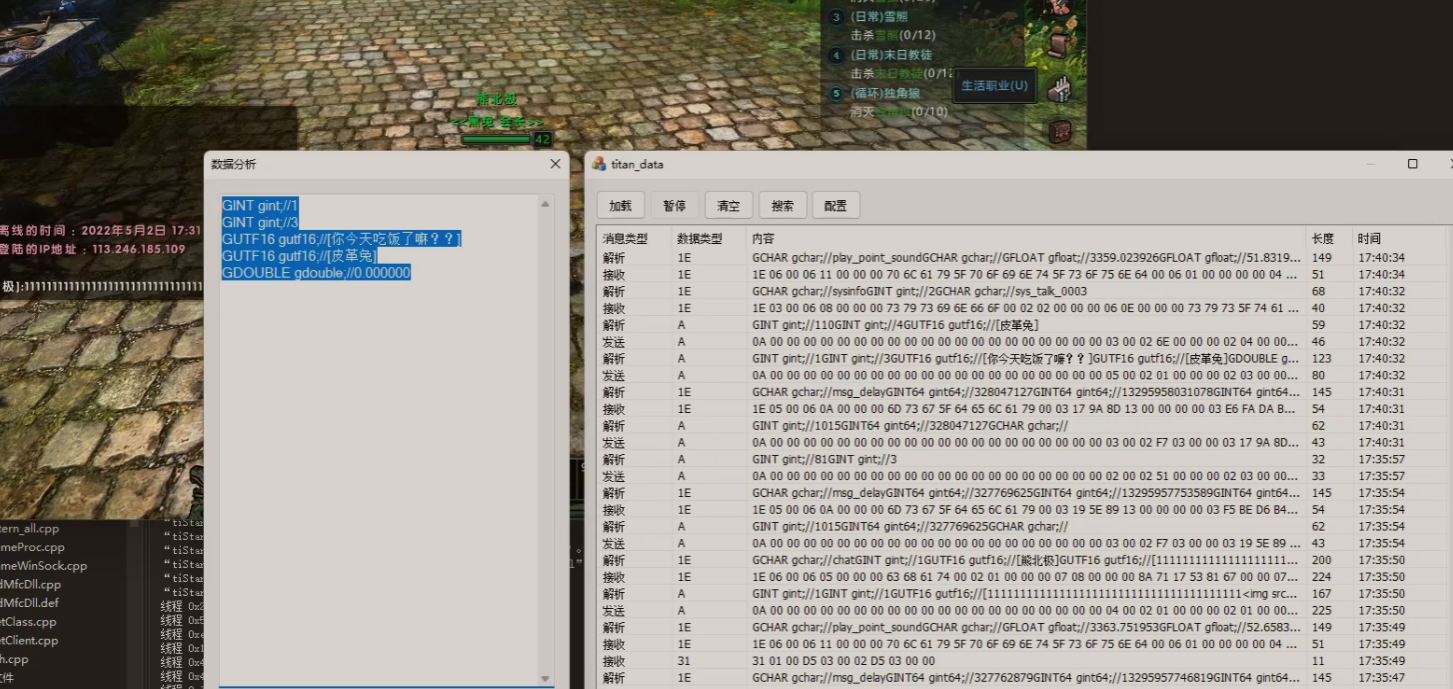
CUIWnd_0.cpp文件的修改:修改了 OnBnClickedButton1函数
// CUIWnd_0.cpp: 实现文件
//
#include "pch.h"
#include "htdMfcDll.h"
#include "CUIWnd_0.h"
#include "afxdialogex.h"
#include "extern_all.h"
// CUIWnd_0 对话框
IMPLEMENT_DYNAMIC(CUIWnd_0, CDialogEx)
CUIWnd_0::CUIWnd_0(CWnd* pParent /*=nullptr*/)
: CDialogEx(IDD_PAGE_0, pParent)
{
}
CUIWnd_0::~CUIWnd_0()
{
}
void CUIWnd_0::DoDataExchange(CDataExchange* pDX)
{
CDialogEx::DoDataExchange(pDX);
}
BEGIN_MESSAGE_MAP(CUIWnd_0, CDialogEx)
ON_BN_CLICKED(IDC_BUTTON1, &CUIWnd_0::OnBnClickedButton1)
END_MESSAGE_MAP()
// CUIWnd_0 消息处理程序
void CUIWnd_0::OnBnClickedButton1()
{
Client->TalkTo(L"t", L"打架吗?");
// Client->Talk(L"[欢迎来到麟科思]");
// Client->SelectRole(L"今晚打老虎");
/*Client->CreateRole(L"am4", 1.0, 2.0, 4.0, 8.0, "gui\BG_team\TeamRole\Teamrole_zq_humF_001.PNG",
"Face,0;Hat,0;Eyes,0;Beard,0;Ears,0;Tail,0;Finger,0;Cloth,0;Pants,0;Gloves,0;Shoes,0;Trait,0;HairColor,0;SkinColor,0;SkinMtl,0;Tattoo,0;TattooColor,16777215;",
"", 0.0);*/
//Client->SelectCamp("xuanrenZQ");
//Client->StartCreateRole();
//Client->DelRole(L"ranzhi11111");
/*
char buff[] = {
0xA, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x4, 0x00, 0x02, 0x01, 0x00, 0x00, 0x00, 0x02, 0x01, 00 ,0x00,
0x00, 0x07, 0x0E, 0x00, 0x00, 0x00, 0x31, 0x00, 0x32, 0x00, 0x33, 0x00, 0x31, 0x00, 0x32 ,0x00,
0x33, 0x00, 0x00, 0x00, 0x05, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00
};
WinSock->OnSend(buff, sizeof(buff));
*/
/*char buff[] = {
0x27, 0x46, 0x92, 0x02, 0x00, 0x00, 0x89, 0x02, 0x00, 0x00, 0x06, 0x00, 0x06, 0x05,
0x00, 0x00, 0x00, 0x63, 0x68, 0x61, 0x74, 0x00, 0x02, 0x01, 0x00, 0x00, 0x00, 0x07,
0x0A, 0x00, 0x00, 0x00, 0x34, 0x00, 0x33, 0x00, 0x39, 0x00, 0x39, 0x00, 0x00, 0x00,
0x07, 0x5A, 0x02, 0x00, 0x00, 0x31, 0x00, 0x32, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31,
0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31,
0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31,
0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31,
0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31,
0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31,
0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31,
0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31,
0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31,
0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x31, 0x00, 0x32, 0x00, 0x32, 0x00, 0x32,
0x00, 0x32, 0x00, 0x32, 0x00, 0x32, 0x00, 0x32, 0x00, 0x32, 0x00, 0x32, 0x00, 0x32,
0x00, 0x32, 0x00, 0x32, 0x00, 0x32, 0x00, 0x32, 0x00, 0x32, 0x00, 0x32, 0x00, 0x32,
0x00, 0x32, 0x00, 0x32, 0x00, 0x32, 0x00, 0x32, 0x00, 0x32, 0x00, 0x32, 0x00, 0x32,
0x00, 0x32, 0x00, 0x32, 0x00, 0x32, 0x00, 0x32, 0x00, 0x32, 0x00, 0x32, 0x00, 0x32,
0x00, 0x32, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33,
0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33,
0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33,
0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33,
0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33,
0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33,
0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x33, 0x00, 0x35,
0x00, 0x35, 0x00, 0x35, 0x00, 0x35, 0x00, 0x35, 0x00, 0x35, 0x00, 0x35, 0x00, 0x35,
0x00, 0x35, 0x00, 0x35, 0x00, 0x35, 0x00, 0x35, 0x00, 0x35, 0x00, 0x35, 0x00, 0x35,
0x00, 0x35, 0x00, 0x35, 0x00, 0x35, 0x00, 0x35, 0x00, 0x35, 0x00, 0x35, 0x00, 0x35,
0x00, 0x35, 0x00, 0x35, 0x00, 0x35, 0x00, 0x35, 0x00, 0x35, 0x00, 0x35, 0x00, 0x35,
0x00, 0x35, 0x00, 0x35, 0x00, 0x35, 0x00, 0x35, 0x00, 0x35, 0x00, 0x35, 0x00, 0x35,
0x00, 0x35, 0x00, 0x35, 0x00, 0x35, 0x00, 0x35, 0x00, 0x35, 0x00, 0x35, 0x00, 0x34,
0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34,
0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34,
0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34,
0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34,
0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34,
0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x34, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36,
0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36,
0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36,
0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x36, 0x00, 0x37,
0x00, 0x37, 0x00, 0x37, 0x00, 0x37, 0x00, 0x37, 0x00, 0x37, 0x00, 0x37, 0x00, 0x37, 0x00, 0x37, 0x00, 0x37, 0x00, 0x37, 0x00, 0x37, 0x00, 0x37, 0x00, 0x37, 0x00, 0x37, 0x00, 0x37, 0x00, 0x37, 0x00,
0x38, 0x00, 0x00, 0x00, 0x02, 0x01, 0x00, 0x00, 0x00, 0x02, 0x01, 0x00, 0x00, 0x00
};
WinSock->OnRecv(buff, sizeof(buff));*/
}
NetClient.h文件的修改:新加 Talk函数、TalkTo函数、OnChat函数、OnChatPublic函数、OnChatPrivate函数
#pragma once
#include "NetClass.h"
#include "GameWinSock.h"
#define CAMP_NAME_QH "xuanrenQH"
#define CAMP_NAME_ZE "xuanrenZQ"
class NetClient // 监视客户端每一个操作
{
private:
GameWinSock* WinSock;
PROLEDATA roles;
unsigned rolecount;
bool logined = false;
bool DelRole(const wchar_t* rolename, unsigned _len);
public:
void Init(GameWinSock * _winSock);
/*
模拟登陆的方法
Id是账号
Pass是密码
它要基于发送的方法实现,因为我们没有连接socket的操作
*/
bool login(const char* Id, const char* Pass);
bool DelRole(const wchar_t* rolename);
bool StartCreateRole();// 用于创建角色
bool SelectCamp(const char* _campname);// 选择阵营
bool CreateRole(wchar_t* name,double sex, double camp, double face, double occu, const char* photo, const char*infos, const char* txt, double faceShape);// 角色创建
// 选择角色并且登录进游戏
bool SelectRole(const wchar_t* rolename);
// 根据角色名字获取一个登录成功数据包(选择角色列表里的一个数据)
PROLEDATA GetRoleByName(const wchar_t* rolename);
bool Talk(wchar_t* txt, int PdId = 1, double un = 0.0);
bool TalkTo(wchar_t* name, wchar_t* txt, double un = 0.0);
public:
// 用于拦截游戏删除角色功能
bool virtual OnDelRole(wchar_t* rolename, unsigned _len);
// 用于拦截游戏登录功能
void virtual Onlogin(const char* Id, const char*Pass);
// 用于拦截游戏创建角色功能
bool virtual OnStartCreateRole(int code);
// 拦截创建角色
bool virtual OnCreateRole(PNS_CREATEROLE _header, PCREATE_ROLE_DATAS _body);
// opcode意思是操作码,count意思是数量,buffStart意思是解码的内容开始,buffend意思是解码的内容结束,buffer是原始的数据,len是原始数据的长度
// char& buffer, int& len这俩参数带&的原因是,在 OnSendCustom 里进行修改之后,通过&的方式传递回去
bool virtual OnSendCustom(PNET_SEND_CHEAD _coder, char*& buffer, unsigned& len);
bool virtual OnSelectRole(wchar_t* rolename);
public:
bool virtual OnChooseCamp(PNS_CHOOSECAMP _coder);
bool virtual OnChat(PCHAT_DATA _coder);
bool virtual OnChatPublic(PCHAT_PUB _coder);
bool virtual OnChatPrivate(PCHAT_PRV _coder);
public:
// 处理失败,参数是错误码
bool virtual Tips(int code);
void virtual loginok(ROLE_DATA* _roles, int count);
bool virtual OnScrStartCreateRole(short code,wchar_t* _txt);
bool virtual OnSvrNotice(EnCode* _coder, int count, char*& buffer, unsigned& len);
};
NetClient.cpp文件的修改:新加 Talk函数、TalkTo函数、OnChat函数、OnChatPublic函数、OnChatPrivate函数,修改了 OnSendCustom函数、OnSvrNotice函数
#include "pch.h"
#include "NetClient.h"
#include "extern_all.h"
bool NetClient::login(const char* Id, const char* Pass)
{
const int bufflen = sizeof(DATA_LOGIN) + 1;
char buff[bufflen];
DATA_LOGIN data;
// 有些操作系统这样写会报错,因为内存不对齐,现在Windows下没事
//PDATALOGIN _data = (PDATALOGIN)(buff + 1);
// 这样写就能解决内存对齐问题
PDATALOGIN _data =&data;
int len = strlen(Id);
memcpy(_data->Id, Id, len);
len = strlen(Pass);
memcpy(_data->Pass, Pass, len);
memcpy(buff+1, _data, sizeof(DATA_LOGIN));
buff[0] = I_LOGIN;
return WinSock->OnSend(buff, sizeof(buff));
}
bool NetClient::DelRole(const wchar_t* rolename)
{
PROLEDATA _role = GetRoleByName(rolename);
if (_role == nullptr) {
return false;
}
else {
return DelRole(rolename, _role->name.lenth);
}
return false;
}
bool NetClient::StartCreateRole()
{
NET_CREATEROLE_START _data;
return WinSock->OnSend(&_data.op, _data.len);
}
bool NetClient::SelectCamp(const char* _campname)
{
NET_SEND_BUFF _buff;
NET_SEND_CHOOSECAMP _data;
_data.opcode.Set(SC_CHOOSECAMP);
_data.camps.Set(_campname);
/*
sizeof(_data) / sizeof(EnCode)的原因
NET_SEND_CHOOSECAMP结构体里面,没别 东西
全是 EnCode 这个结构
*/
short count = sizeof(_data) / sizeof(EnCode);
_buff.count = count;
/*
CodeMe函数给 _buff.buff里写数据参数的数据
也就是给0A开头数据包里写,数据参数个数后面的内容
然后返回值是写了多长的数据
也就是给0A开头数据包里的数据参数个数后面的数据写了多长
*/
int ilen = _data.CodeMe(count, _buff.buff);
ilen = ilen + sizeof(NET_SEND_HEAD) - 1;
return WinSock->OnSend(&_buff.op, ilen);
}
bool NetClient::CreateRole(wchar_t* name, double sex, double camp, double face, double occu, const char* photo, const char* infos, const char* txt, double faceShape)
{
// rolecount > 4说明角色的数量够了
if (rolecount > 4)return false;
int index = 0;
bool roleindex[5]{true, true, true, true, true };
for (int i = 0; i < rolecount; i++) {
roleindex[roles[i].index] = false;
}
for (int i = 0; i < 5; i++)
{
if (roleindex[i]) {
index = i;
break;
}
}
// wchar_t _name[] = L"am52111";
NS_CREATEROLE_HEAD_BUFF _buff;
CREATE_ROLE_DATAS _data;
_data.sex.Set(sex);
_data.camp.Set(camp);
_data.face.Set(face);
_data.occu.Set(occu);
_data.faceSahpe.Set(faceShape);
//_data.Photo.Set("gui\BG_team\TeamRole\Teamrole_zq_humF_001.PNG");
_data.Photo.Set(photo);
//_data.Infos.Set("Face,0;Hat,0;Eyes,0;Beard,0;Ears,0;Tail,0;Finger,0;Cloth,0;Pants,0;Gloves,0;Shoes,0;Trait,0;HairColor,0;SkinColor,0;SkinMtl,0;Tattoo,0;TattooColor,16777215;");
_data.Infos.Set(infos);
_data.Txt.Set(txt);
short count = sizeof(_data) / sizeof(EnCode);
_buff.count = count;
_buff.index = index;
int lenth = wcslen(name) + 1;
lenth = lenth * 2;
memcpy(_buff.name, name, lenth);
int ilen = _data.CodeMe(count, _buff.buff);
ilen = ilen + sizeof(NET_SEHD_CREATEROLE_HEAD) - 3;
return WinSock->OnSend(&_buff.op, ilen);
}
bool NetClient::SelectRole(const wchar_t* rolename)
{
PROLEDATA roles = GetRoleByName(rolename);
if (roles == nullptr)return false;
NS_SELECTROLE _data;
memcpy(_data.buff, roles->name.value(), roles->name.lenth);
return WinSock->OnSend((char*)&_data, sizeof(_data));
}
PROLEDATA NetClient::GetRoleByName(const wchar_t* rolename)
{
//PROLEDATA result = nullptr;
for (int i = 0; i < rolecount; i++)
{
// StrCmpW判断两个字符串是否相同
// 比较时区分大小写,如果字符串相同返回0
if (StrCmpW(roles[i].name.value(), rolename) == 0) {
return &roles[i];
}
}
return nullptr;
}
bool NetClient::Talk(wchar_t* txt, int PdId, double un)
{
NET_SEND_BUFF _buff;
CHAT_PUBLIC _data;
_data.opcode.Set(SC_CHAT);
_data.ChartId.Set(PdId);
_data.txt.Set(txt);
_data.un.Set(un);
/*
sizeof(_data) / sizeof(EnCode)的原因
NET_SEND_CHOOSECAMP结构体里面,没别 东西
全是 EnCode 这个结构
*/
short count = sizeof(_data) / sizeof(EnCode);
_buff.count = count;
/*
CodeMe函数给 _buff.buff里写数据参数的数据
也就是给0A开头数据包里写,数据参数个数后面的内容
然后返回值是写了多长的数据
也就是给0A开头数据包里的数据参数个数后面的数据写了多长
*/
int ilen = _data.CodeMe(count, _buff.buff);
ilen = ilen + sizeof(NET_SEND_HEAD) - 1;
return WinSock->OnSend(&_buff.op, ilen);
}
bool NetClient::TalkTo(wchar_t* name, wchar_t* txt, double un)
{
NET_SEND_BUFF _buff;
CHAT_PRIVATE _data;
_data.opcode.Set(SC_CHAT);
_data.ChartId.Set(3);
_data.txt.Set(txt);
_data.name.Set(name);
_data.un.Set(un);
/*
sizeof(_data) / sizeof(EnCode)的原因
NET_SEND_CHOOSECAMP结构体里面,没别 东西
全是 EnCode 这个结构
*/
short count = sizeof(_data) / sizeof(EnCode);
_buff.count = count;
/*
CodeMe函数给 _buff.buff里写数据参数的数据
也就是给0A开头数据包里写,数据参数个数后面的内容
然后返回值是写了多长的数据
也就是给0A开头数据包里的数据参数个数后面的数据写了多长
*/
int ilen = _data.CodeMe(count, _buff.buff);
ilen = ilen + sizeof(NET_SEND_HEAD) - 1;
return WinSock->OnSend(&_buff.op, ilen);
}
bool NetClient::DelRole(const wchar_t* rolename, unsigned _len)
{
DATA_DELROLE _data;
_data.op = 0x06;
_data.len = _len;
memcpy(_data.buff, rolename, _len);
return WinSock->OnSend((char*)&_data, sizeof(DATA_DELROLE) - 1);
}
void NetClient::Init(GameWinSock* _winSock)
{
this->WinSock = _winSock;
}
bool NetClient::OnDelRole(wchar_t* rolename, unsigned _len)
{
// AfxMessageBox(rolename);
return true;
}
void NetClient::Onlogin(const char* Id, const char* Pass)
{
/*
const int bufflen = sizeof(DATA_LOGIN) + 1;
char buff[bufflen];
DATA_LOGIN data;
// 有些操作系统这样写会报错,因为内存不对齐,现在Windows下没事
//PDATALOGIN _data = (PDATALOGIN)(buff + 1);
// 这样写就能解决内存对齐问题
PDATALOGIN _data =&data;
int len = strlen(Id);
memcpy(_data->Id, Id, len);
len = strlen(Pass);
memcpy(_data->Pass, Pass, len);
memcpy(buff+1, _data, sizeof(DATA_LOGIN));
buff[0] = I_LOGIN;
return WinSock->OnSend(buff, sizeof(buff));
*/
}
bool NetClient::OnStartCreateRole(int code)
{
return true;
}
bool NetClient::OnCreateRole(PNS_CREATEROLE _header, PCREATE_ROLE_DATAS _body)
{
return true;
}
bool NetClient::OnSendCustom(PNET_SEND_CHEAD _coder, char*& buffer, unsigned& len)
{
switch (_coder->opcode.value())
{
case SC_CHOOSECAMP:
return OnChooseCamp((PNS_CHOOSECAMP)_coder);
break;
case SC_CHAT:
return OnChat((PCHAT_DATA)_coder);
break;
default:
break;
}
return true;
}
bool NetClient::OnSelectRole(wchar_t* rolename)
{
AfxMessageBox(rolename);
return true;
}
bool NetClient::OnChooseCamp(PNS_CHOOSECAMP _coder)
{
PNS_CHOOSECAMP _p = (PNS_CHOOSECAMP)_coder;
return true;
}
bool NetClient::OnChat(PCHAT_DATA _coder)
{
switch (_coder->ChartId)
{
case 3:// 私聊
return OnChatPrivate((PCHAT_PRV)_coder);
case 1:// 附近频道
case 2:// 区域频道
case 6:// 公会频道
case 9:// 阵营频道
case 21:// 喊话频道
return OnChatPublic((PCHAT_PUB)_coder);
break;
}
}
bool NetClient::OnChatPublic(PCHAT_PUB _coder)
{
return true;
}
bool NetClient::OnChatPrivate(PCHAT_PRV _coder)
{
return true;
}
bool NetClient::Tips(int code)
{
#ifdef Anly
CString txt;
if (code == 51001) {
txt = L"登陆失败,易道云通行证不存在!";
}else if (code == 51002) {
txt = L"登录失败,密码错误!";
}else if (code == 21101) {
txt = L"人物重名!";
}else if (code == 21109) {
txt = L"名字过长或包含非法字符!";
}
else {
txt.Format(L"未知登录错误:%d", code);
}
anly->SendData(TTYPE::I_LOG, 0, txt.GetBuffer(), (txt.GetLength() + 1)*2);
#endif
return true;
}
void NetClient::loginok(ROLE_DATA* _roles, int count)
{
logined = true;
if(roles) delete[] roles;
roles = _roles;
rolecount = count;
}
bool NetClient::OnScrStartCreateRole(short code, wchar_t* _txt)
{
return true;
}
bool NetClient::OnSvrNotice(EnCode* _coder, int count, char*& buffer, unsigned& len)
{
GCHAR* _msgHead = (GCHAR*)_coder;
if (_msgHead->Safe()) {// 如果是0x06说明当前数据是字符串
}
else {
AfxMessageBox(L"异常!");
}
return true;
}
EnCode.cpp文件的修改:新加 Safe函数
#include "pch.h"
#include "EnCode.h"
#include "extern_all.h"
void EnCode::Init(char*& buff, char EnIndex)
{
index = EnIndex;
op = buff[0];
int len = data_desc[index][op].lenth;
/*
比如 07 0A 00 00 00 34 00 33 00 39 00 39 00 00 00
buff + 1 的结果是 0A 00 00 00 34 00 33 00 39 00 39 00 00 00
len是 07 所代表的类型的长度,也就是0A 00 00 00 这个东西
memcpy(dataPool, buff + 1, len);也就是把 0A 00 00 00 复制到 dataPool里
然后从下方的if ((op == 0x7))得到它的字符串
*/
memcpy(dataPool, buff + 1, len);
buff = buff + 1 + len;// 下一个结构
if (index == 0) {
if ((op == 0x7)) {
AllocPointer(lenth);
// if (pointer)delete[]pointer;
/*
dataPool 与 lenth是一个联合体,联合体的特性就是
所有变量共用一个内存,所以 dataPool 的值就是lenth的值
从上方的注释得知现在dataPool的值是0A 00 00 00
然后通过 lenth去读 0A 00 00 00结果就是十进制的 10
然后创建一个10字节的空间给pointer
然后在通过 memcpy(pointer, buff, lenth); 把字符串赋值给pointer
*/
// pointer = new char[lenth];
memcpy(pointer, buff, lenth);
buff = buff + lenth;// 指向下一个字符串
}
}
if (index == 1) {
if ((op == 0x06) || (op == 0x7)) {
AllocPointer(lenth);
memcpy(pointer, buff, lenth);
buff = buff + lenth;
}
}
}
/*
buff是数据包
_len暂时没用
ExIndex是解析方式,因为分析的时候发现6有时是char类型有时是char*类型
看懂此方法需要分析手动分析一次数据包(数据解析约定的数据包)
然后带着数据包去看这个函数
*/
EnCode::EnCode(char*& buff,char EnIndex)
{
Init(buff,EnIndex);
}
EnCode::~EnCode()
{
if(pointer)
delete[] pointer;
}
void EnCode::AllocPointer(int size)
{
if (size > AllocCount) {
if (pointer) delete[]pointer;
pointer = new char[size];
AllocCount = size;
}
}
EnCode::EnCode()
{
}
EnCode& EnCode::operator=(char*& buff)
{
Init(buff);
return *this;
}
GBYTE::operator char()
{
return this->byte;
}
char GBYTE::value()
{
return this->byte;
}
GSHORT::operator short()
{
return this->stval;
}
short GSHORT::value()
{
return this->stval;
}
GINT::operator int()
{
return this->val;
}
int GINT::value()
{
return this->val;
}
/*
GINT::Set函数得到的数据是
02 03 00 00 00
02是数据类型,表示int类型
03 00 00 00 int类型的值
*/
void GINT::Set(int _invalue, char EnIndex)
{
index = EnIndex;// 处理类型
op = 2; // 数据解析约定的数据02表示int
val = _invalue; // 数据
}
GFLOAT::operator float()
{
return this->fval;
}
float GFLOAT::value()
{
return this->fval;
}
void GFLOAT::Set(float invalue, char EnIndex)
{
index = EnIndex;
op = 0x04 ;
fval = invalue;
}
GINT64::operator long long()
{
return this->lval;
}
long long GINT64::value()
{
return this->lval;
}
void GINT64::Set(long long invalue, char EnIndex)
{
index = EnIndex;
op = 0x03;
lval = invalue;
}
GDOUBLE::operator double()
{
return this->dbval;
}
double GDOUBLE::value()
{
return this->dbval;
}
void GDOUBLE::Set(double invalue, char EnIndex)
{
index = EnIndex;
op = 0x05;
dbval = invalue;
}
GCHAR::operator const char*()
{
return this->pointer;
}
const char* GCHAR::value()
{
return this->pointer;
}
/*
GCHAR::Set函数得到的数据是
06 03 00 00 00 77 65 72 00
06是数据类型,表示char*类型
03 00 00 00 表示字符串长度
77 65 72 00 是字符串
*/
void GCHAR::Set(const char* _txt, char EnIndex)
{
index = EnIndex;
op = 6;
lenth = strlen(_txt) + 1;
AllocPointer(lenth);
memcpy(pointer, _txt, lenth);
}
bool GCHAR::Safe()
{
return op == 0x06;
}
GUTF16::operator const wchar_t*()
{
return (wchar_t*)this->pointer;
}
const wchar_t* GUTF16::value()
{
return (wchar_t*)this->pointer;
}
/*
GUTF16::Set函数得到的数据是
07 03 00 00 00 77 00 65 00 72 00
07是数据类型,表示wchar_t*类型
03 00 00 00 表示字符串长度
77 00 65 00 72 00 是字符串
*/
void GUTF16::Set(const wchar_t* _txt, char EnIndex)
{
index = EnIndex;
op = 7;
lenth = wcslen(_txt) + 1;
lenth = lenth * 2;
AllocPointer(lenth);
memcpy(pointer, _txt, lenth);
}
EnCode.h文件的修改:修改了 GCHAR类
#pragma once
/*
EnCode结构体
un[6]、index、op是8字节
union里也是8字节
pointer、back它俩虽然是char类型,但它俩是指针类型,所以它们一共是8字节
EnCode结构体一共是24字节
*/
class EnCode// 用于表示数据解析约定的数据
{
private:
char un[6]{};//
public:
char index = 0;
// op + un[3]是四字节,op与buffer是6字节,如果自动内存对齐op与buffer可能不会挨在一起
char op = 0;
/*
这个位置会导致编译器代码生成出现问题
就是在当前文件一个类里写一个新的函数声明
这个时候会因为下方的 union 导致编译器无法
通过函数声明在cpp实现函数,这是因为编译器
不知道下方的 union 是什么东西导致的
*/
union
{
char dataPool[0x8];
int lenth;
char byte;
short stval;
int val;
float fval;
double dbval;
long long lval = 0;
};
char* pointer = 0;
int AllocCount = 0;// 记录内存大小
protected:
void AllocPointer(int size);
public:
EnCode();
EnCode(char*& buff, char ExIndex = 1);
EnCode& operator=(char*& buff);
void Init(char*& buff, char EnIndex = 1);
~EnCode();
};
class GBYTE :public EnCode {
public:
using EnCode::EnCode;
using EnCode::operator=;
public:
operator char();
char value();
};
class GSHORT :public EnCode {
public:
using EnCode::EnCode;
using EnCode::operator=;
public:
operator short();
short value();
};
class GINT :public EnCode {
public:
using EnCode::EnCode;
using EnCode::operator=;
public:
operator int();
int value();
void Set(int _invalue, char EnIndex = 1);
};
class GFLOAT :public EnCode {
public:
using EnCode::EnCode;
using EnCode::operator=;
operator float();
float value();
void Set(float invalue, char EnIndex = 1);
};
class GINT64 :public EnCode {
public:
using EnCode::EnCode;
using EnCode::operator=;
operator long long();
long long value();
void Set(long long invalue, char EnIndex = 1);
};
class GDOUBLE :public EnCode {
public:
using EnCode::EnCode;
using EnCode::operator=;
operator double();
double value();
void Set(double invalue, char EnIndex = 1);
};
class GCHAR :public EnCode {
public:
using EnCode::EnCode;
using EnCode::operator=;
operator const char*();
const char* value();
void Set(const char* _txt, char EnIndex = 1);
bool Safe();
};
class GUTF16 :public EnCode {
public:
using EnCode::EnCode;
using EnCode::operator=;
operator const wchar_t*();
const wchar_t* value();
void Set(const wchar_t* _txt, char EnIndex = 1);
};

























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








