
Microsoft Teams作为一款国际化公司会议软件,在2024年7月1日起不再支持经典版本,提示升级New Teams。

由于New Teams官网提供的Windows系统安装包并不是传统的可执行文件MSI,EXE等,而是新型封装的MSIX格式,无法直接双击安装完成升级的。
小编为大家分享New Teams的几种安装方法。
方法一:如果您的电脑系统是Win10 21H2版本及以上,且登录微软账号和系统带有Microsoft Store,那么可以直接打开Microsoft Store搜索Teams,下载并安装新版本的Teams即可。
方法二:如果您的电脑系统是Windows企业版,LTSC版,且不带有Microsoft Store和系统版本在21H2及以上。
1.复制网址Your request has been blocked. This could be due to several reasons.到浏览器打开,下载安转包。

2.打开安装包所在目录,鼠标放在该目录的空白位置,同时按下键盘Shift键和鼠标右键,选择在此打开powershell窗口。

3.输入add-appxpackage ./MSTeams-x64.msix回车执行安装。

4.打开开始菜单,即可看到New Teams的图标,打开运行即可

方法三:如果在方法二执行安装命令提示已有更高版本存在,无法继续安装,可以按照这个方法直接运行。

1.复制网址下载 - voidtools到浏览器打开,下载并安装everything搜索软件打开,搜索Teams。选中C盘-Program Files-WindowsApps目录下的ms-teams.exe右键选择打开文件所在位置。

2.选中ms-teams右键选择发送到桌面快捷方式,后打开即可运行New Teams。

方法四:如果您的电脑系统是Win10 21H2及以下版本,且不是使用微软账号和不带有microsoft Store,或者安装中提示错误,无法继续安装的,可以使用此终极方法。

1. .复制网址Your request has been blocked. This could be due to several reasons.到浏览器打开,下载安转包。

2.打开安装包所在目录,将安装包的msix拓展名改为zip,后使用解压软件解压。
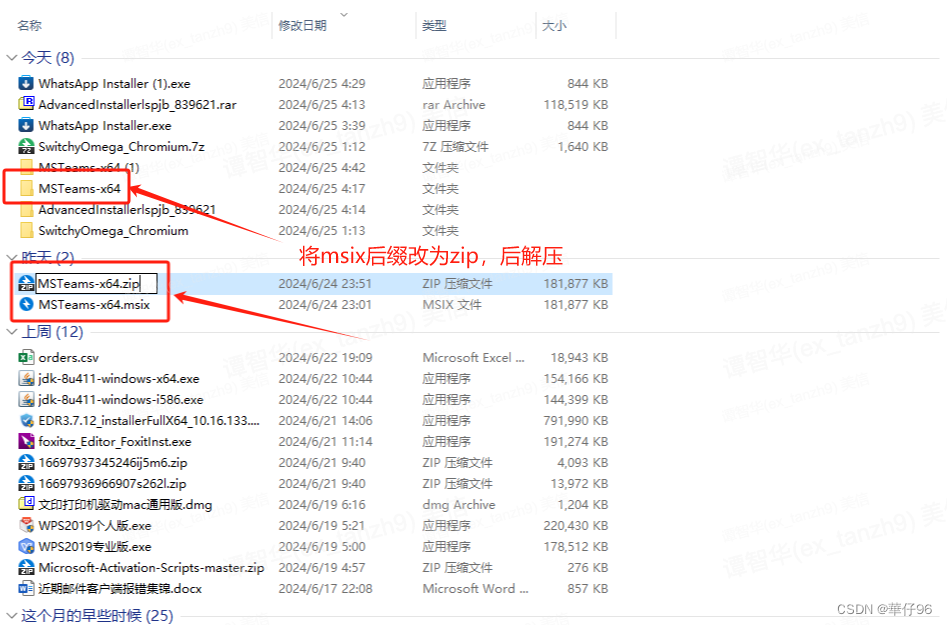
3.打开解压的目录,选中ms-teams右键选择发送到桌面快捷方式,后打开即可运行New Teams。

以上就是小编测试出来New Teams的安装方式,当然微软官方也给出了适合专业IT人员的升级安装方法,请参考网站批量部署新的 Microsoft Teams 桌面客户端 - Microsoft Teams | Microsoft Learn


























 955
955

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










