Harbor安装
1 安装docker
curl -fsSL https://get.docker.com | bash -s docker --mirror Aliyun
#配置镜像加速
mkdir -p /etc/docker
tee /etc/docker/daemon.json <<-'EOF'
{
"registry-mirrors": ["https://uyah70su.mirror.aliyuncs.com"]
}
EOF
#启动docker服务
systemctl enable --now docker
2 安装docker-compose
version=1.26.2
curl -L https://get.daocloud.io/docker/compose/releases/download/${version}/docker-compose-`uname -s`-`uname -m` -o /usr/local/bin/docker-compose
chmod +x /usr/local/bin/docker-compose
3 harbor安装
下载地址
https://github.com/goharbor/harbor/releases
https://mirrors.tuna.tsinghua.edu.cn/github-release/goharbor/harbor/
wget https://github.com/goharbor/harbor/releases/download/${version}/harbor-offline-installer-2.4.1.tgz
tar -zxvf harbor-offline-installer-v2.4.1.tgz -C /usr/local/
vim harbor.yml
修改hostname字段,并注释https部分然后执行部署
./install.sh
4 HTTPS配置
mkdir keys
cd keys
4.1 生成CA证书私钥
openssl genrsa -out ca.key 4096
4.2 生成CA证书
调整-subj选项中的值以反映您的组织。如果使用FQDN连接Harbor主机,则必须将其指定为通用名称(CN)属性
openssl req -x509 -new -nodes -sha512 -days 3650 \
-subj "/C=CN/ST=Beijing/L=Beijing/O=example/OU=Personal/CN=180.76.243.46" \
-key ca.key \
-out ca.crt
如果使用IP地址,需要在执行以上命令前执行以下操作:
cd /root
openssl rand -writerand .rnd
cd -
4.3 生成服务器证书
证书通常包含一个.crt文件和一个.key文件,例如yourdomain.com.crt和yourdomain.com.key。
4.3.1 生成私钥
openssl genrsa -out server.key 4096
4.3.2 生成证书签名请求(CSR)
调整-subj选项中的值以反映您的组织。如果使用FQDN连接Harbor主机,则必须将其指定为通用名称(CN)属性,并在密钥和CSR文件名中使用它。
openssl req -sha512 -new \
-subj "/C=CN/ST=Beijing/L=Beijing/O=example/OU=Personal/CN=180.76.243.46" \
-key server.key \
-out server.csr
4.3.3 生成一个x509 v3扩展文件
无论您使用FQDN还是IP地址连接到Harbor主机,都必须创建此文件,以便可以为您的Harbor主机生成符合主题备用名称(SAN)和x509 v3的证书扩展要求。替换DNS条目以反映您的域。
域名
cat > v3.ext <<-EOF
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth
subjectAltName = @alt_names
[alt_names]
DNS.1=registry.harbor.com
DNS.2=registry.harbor
DNS.3=harbor
EOF
IP
cat > v3.ext <<-EOF
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth
subjectAltName = IP:180.76.243.46
EOF
4.3.4 使用该v3.ext文件为您的Harbor主机生成证书
将yourdomain.comCRS和CRT文件名中的替换为Harbor主机名。
openssl x509 -req -sha512 -days 3650 \
-extfile v3.ext \
-CA ca.crt -CAkey ca.key -CAcreateserial \
-in server.csr \
-out server.crt
4.4 提供证书给Harbor和Docker
openssl x509 -inform PEM -in server.crt -out server.cert'
将服务器证书,密钥和CA文件复制到Harbor主机上的Docker证书文件夹中。您必须首先创建适当的文件夹。
mkdir -p /etc/docker/certs.d/180.76.243.46/
cp server.cert /etc/docker/certs.d/180.76.243.46/
cp server.key /etc/docker/certs.d/180.76.243.46/
cp ca.crt /etc/docker/certs.d/180.76.243.46/
systemctl restart docker
yml
[root@harbor ~]# cd /root/harbor
[root@harbor harbor]# cp harbor.yml.tmpl harbor.yml
#只需修改hostname及https下的证书路径即可,其他保持默认
[root@harbor harbor]# more harbor.yml
# Configuration file of Harbor
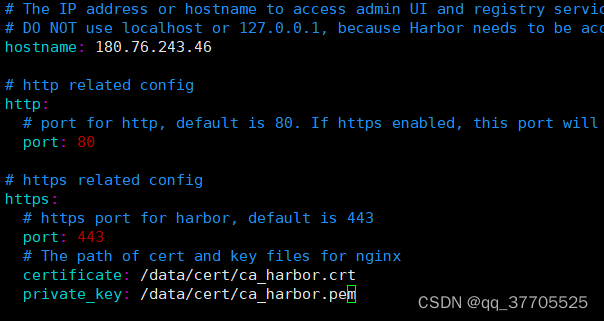
# The IP address or hostname to access admin UI and registry service.
# DO NOT use localhost or 127.0.0.1, because Harbor needs to be accessed by external clients.
hostname: registry.harbor.com
# http related config
http:
# port for http, default is 80. If https enabled, this port will redirect to https port
port: 80
# https related config
https:
# https port for harbor, default is 443
port: 443
# The path of cert and key files for nginx
certificate: /usr/local/harbor/keys/server.crt
private_key: /usr/local/harbor/keys/server.key
./install.sh
5 harbor.service
cat > /usr/lib/systemd/system/harbor.service << 'EOF'
[Unit]
Description=Harbor
After=docker.service systemd-networkd.service systemd-resolved.service
Requires=docker.service
Documentation=http://github.com/vmware/harbor
[Service]
Type=simple
Restart=on-failure
RestartSec=5
Environment=harbor_install_path=/usr/local
ExecStart=/usr/local/bin/docker-compose -f ${harbor_install_path}/harbor/docker-compose.yml up
ExecStop=/usr/local/bin/docker-compose -f ${harbor_install_path}/harbor/docker-compose.yml down
[Install]
WantedBy=multi-user.target
EOF
systemctl enable --now harbor
根证书
mkdir -p /data/cert
cd /data/cert
#生成跟密钥
openssl genrsa -out root.pem 2048
#生成跟请求文件,harbor安装足迹ip:192.168.56.108
openssl req -new -sha256 -out root.csr -key root.pem \
-subj "/C=CN/ST=guangdong/L=guangzhou/O=test/OU=Personal/CN=180.76.243.46"
#签发跟证书文件
openssl req -x509 -new -nodes -sha256 -days 365 \
-subj "/C=CN/ST=guangdong/L=guangzhou/O=test/OU=Personal/CN=180.76.243.46" \
-key root.pem \
-out root.crt
签发生成harbor服务端使用证书
#生成harbor密钥
openssl genrsa -out ca_harbor.pem 2048
#生成证书请求文件
openssl req -new -sha256 -out ca_harbor.csr -key ca_harbor.pem
生成一个x509 v3扩展文件
cat > v3.ext <<-EOF
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth
subjectAltName = IP:180.76.243.46
EOF
#签发证书
openssl x509 -req -sha512 -days 365 \
-extfile v3.ext \
-CA root.crt -CAkey root.pem -CAcreateserial \
-in ca_harbor.csr \
-out ca_harbor.crt
#转换ca_harbor.crt为harbor.cert,供Docker使用
openssl x509 -inform PEM -in ca_harbor.crt -out ca_harbor.cert
mkdir -p /etc/docker/certs.d/180.76.243.46/
cp /data/cert/ca_harbor.cert /etc/docker/certs.d/180.76.243.46/
cp /data/cert/ca_harbor.pem /etc/docker/certs.d/180.76.243.46/
cp /data/cert/ca_harbor.crt /etc/docker/certs.d/180.76.243.46/
vi /usr/local/harbor/harbor.yml
docker-compose down -v
systemctl restart docker
./install.sh
#查看443端口是否已启用
netstat -nplt
#若netstat未找到命令,可先执行安装工具类
yum -y install net-tools






















 990
990

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








