1. 关于iOS砸壳的介绍
https://mp.weixin.qq.com/s/xFHA2tlc6HCLti_ihlrsZA
2. 准备工作:使用Cydia安装Filza
直接在Cydia里搜索filza,安装“Filza File Manager”

3. FlexDecrypt砸壳
3.1 使用Filza安装flexdecrypt
参考:
https://github.com/JohnCoates/flexdecrypt

下载flexdecrypt.deb到手机:
https://github.com/JohnCoates/flexdecrypt/releases/tag/1.1
使用filza打开flexdecrypt.deb,点击flexdecrypt.deb,点击右上角的安装

安装成功:
3.2 使用flexdecrypt砸壳
参考:https://www.jianshu.com/p/c3305067fd94
借助Filza找到app程序的路径
一般是在/var/containers/Bundle/Application/下面:
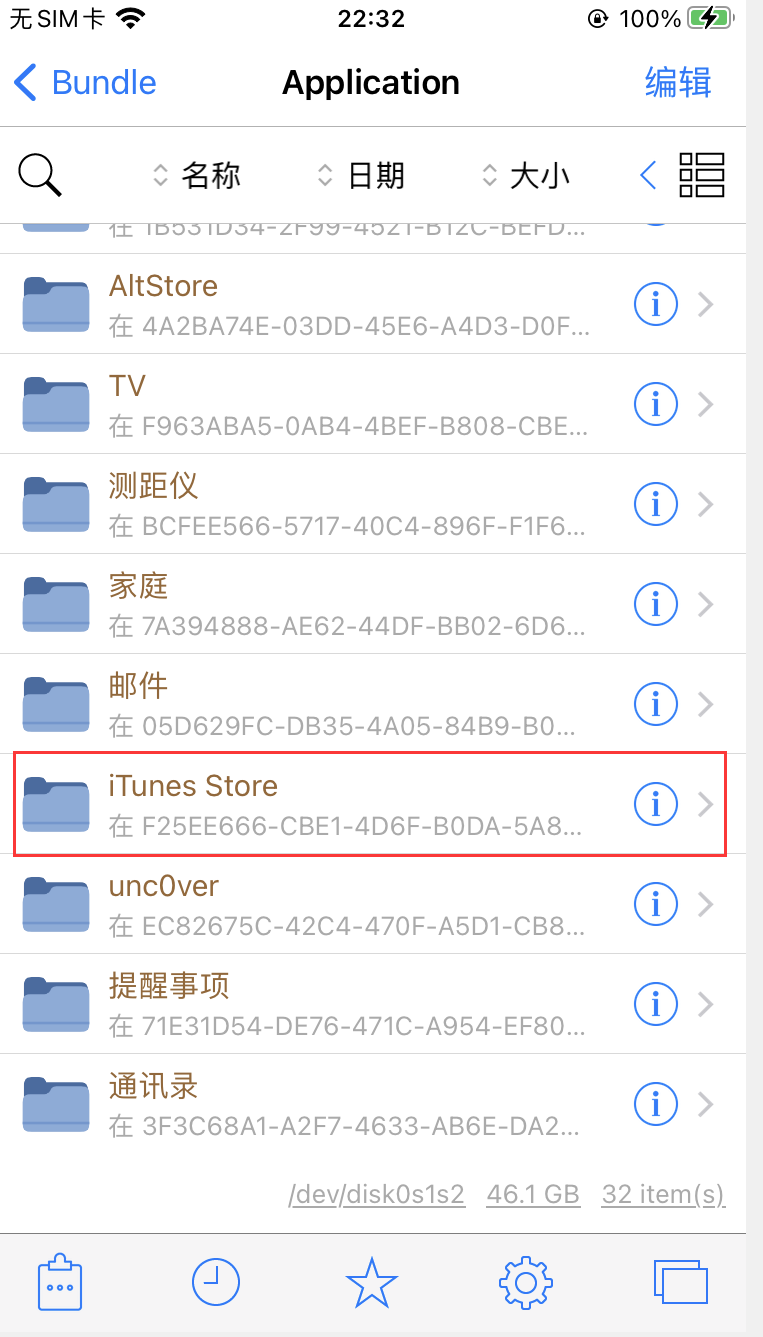
比如iTunes Store位于:
/var/containers/Bundle/Application/F25EE666-CBE1-4D6F-B0DA-5A8AB41BB364/MobileStore.app/MobileStore
使用flexdecrypt
flexdecrypt /var/containers/Bundle/Application/F25EE666-CBE1-4D6F-B0DA-5A8AB41BB364/MobileStore.app/MobileStore
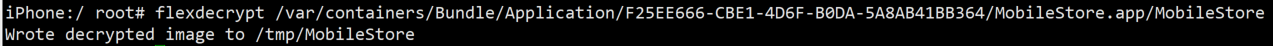
将 /private/var/tmp/ 路径下的 MobileStore 拷贝到PC

4. Dumpdecrypted砸壳
参考:https://juejin.cn/post/7198210198644129851
有些app使用FlexDecrypt砸壳时会报错,可以用Dumpdecrypted试一下
4.1 生成dumpdecrypted.dylib
下载Dumpdecrypted
https://github.com/stefanesser/dumpdecrypted
在macbook上进入dumpdecrypted-master
make
ldid -S dumpdecrypted.dylib
4.2 使用dumpdecrypted.dylib
找到macho文件的路径(用Filza)
/var/containers/Bundle/Application/6BAB0A28-8DD4-4C30-ABBD-FD37791A75A9/Taobao4iPhone.app/Taobao4iPhone
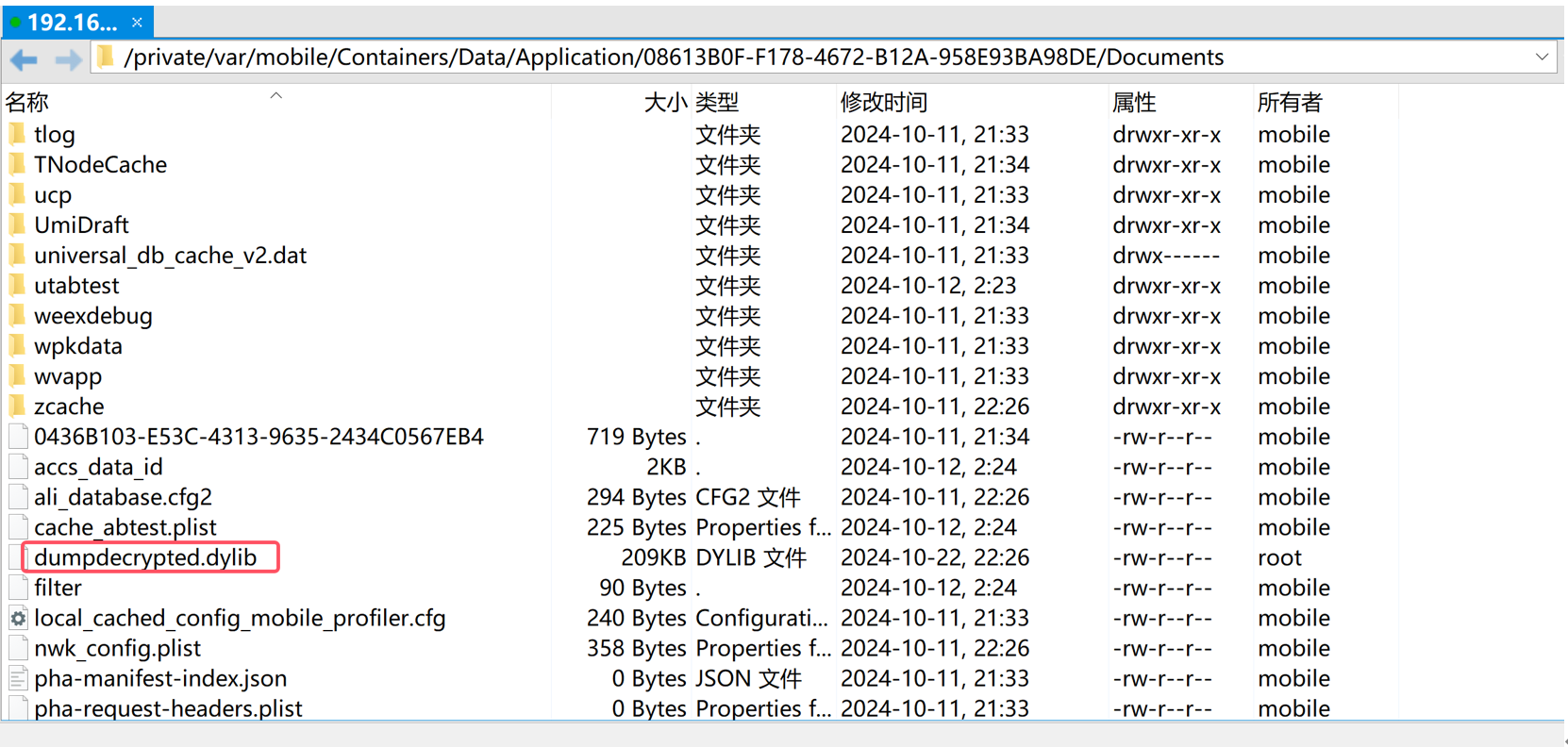
找到app document对应的路径(用Filza)
/var/mobile/Containers/Data/Application/08613B0F-F178-4672-B12A-958E93BA98DE/Documents
将dumpdecrypted.dylib拷贝至app document对应的目录
/var/mobile/Containers/Data/Application/08613B0F-F178-4672-B12A-958E93BA98DE/Documents
SSH连接手机,root权限执行
DYLD_INSERT_LIBRARIES=/var/mobile/Containers/Data/Application/08613B0F-F178-4672-B12A-958E93BA98DE/Documents/dumpdecrypted.dylib /var/containers/Bundle/Application/6BAB0A28-8DD4-4C30-ABBD-FD37791A75A9/Taobao4iPhone.app/Taobao4iPhone
其中第一个path是dumpdecrypted.dylib路径,第二个path是app macho文件的路径
就可以得到砸壳出来的文件了:Taobao4iPhone.decrypted

zzz256:/var/mobile/Containers root# DYLD_INSERT_LIBRARIES=/var/mobile/Containers/Data/Application/08613B0F-F178-4672-B12A-958E93BA98DE/Documents/dumpdecrypted.dylib /var/containers/Bundle/Application/6BAB0A28-8DD4-4C30-ABBD-FD37791A75A9/Taobao4iPhone.app/Taobao4iPhone
mach-o decryption dumper
DISCLAIMER: This tool is only meant for security research purposes, not for application crackers.
[+] detected 64bit ARM binary in memory.
[+] offset to cryptid found: @0x102c49f78(from 0x102c48000) = 1f78
[+] Found encrypted data at address 0044c000 of length 4096 bytes - type 1.
[+] Opening /private/var/containers/Bundle/Application/6BAB0A28-8DD4-4C30-ABBD-FD37791A75A9/Taobao4iPhone.app/Taobao4iPhone for reading.
[+] Reading header
[+] Detecting header type
[+] Executable is a plain MACH-O image
[+] Opening Taobao4iPhone.decrypted for writing.
[+] Copying the not encrypted start of the file
[+] Dumping the decrypted data into the file
[+] Copying the not encrypted remainder of the file
[+] Setting the LC_ENCRYPTION_INFO->cryptid to 0 at offset 1f78
[+] Closing original file
[+] Closing dump file
4.3 报错:could not load inserted library ‘/xxx/dumpdecrypted.dylib’ into hardened process because no suitable image found
执行DYLD_INSERT_LIBRARIES=时报错:

zzz256:/var/mobile/Containers root# DYLD_INSERT_LIBRARIES=/var/mobile/Containers/Data/Application/08613B0F-F178-4672-B12A-958E93BA98DE/Documents/dumpdecrypted.dylib /var/containers/Bundle/Application/6BAB0A28-8DD4-4C30-ABBD-FD37791A75A9/Taobao4iPhone.app/Taobao4iPhone
dyld: warning: could not load inserted library '/var/mobile/Containers/Data/Application/08613B0F-F178-4672-B12A-958E93BA98DE/Documents/dumpdecrypted.dylib' into hardened process because no suitable image found. Did find:
/var/mobile/Containers/Data/Application/08613B0F-F178-4672-B12A-958E93BA98DE/Documents/dumpdecrypted.dylib: code signature in (/var/mobile/Containers/Data/Application/08613B0F-F178-4672-B12A-958E93BA98DE/Documents/dumpdecrypted.dylib) not valid for use in process using Library Validation: mapped file has no cdhash, completely unsigned? Code has to be at least ad-hoc signed.
[TBSideWayRecovery] Run before launch tasks with count: 0
Abort trap: 6
解决办法:
生成dumpdecrypted.dylib时不要忘记ldid -S dumpdecrypted.dylib
参考:https://github.com/stefanesser/dumpdecrypted/issues/28
5. FoulDecrypt砸壳
https://github.com/Lessica/fouldecrypt
直接使用工具:Iridium
Iridium 是基于静态砸壳命令行工具 fouldecrypt 做砸壳开发的图形化工具
使用教程:https://www.jianshu.com/p/b60a494c24d3
直接Cydia安装即可
























 1万+
1万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








